
How To: Stack poker chips with one hand
Take some ordinary poker chips and make two piles of four. Put three fingers on the side of one pile, and the thumb on the side of the other pile. Gently squeeze the chips together.


Take some ordinary poker chips and make two piles of four. Put three fingers on the side of one pile, and the thumb on the side of the other pile. Gently squeeze the chips together.

You don’t have to take your circular saw to the shop for a tune-up; we’ve brought the shop to you. Learn how to extend the life of your saw with simple cleaning and general maintenance. There's no 3,000 mile rule here, but if your saw starts running slower than normal, or you see sparks coming from the back of the housing, it’s time for a tune-up. Tune up a circular-saw.

Aharon Rabinowitz shows you how to make ''Horror Movie'' style text appear on a wall in part one of this After Effect tutorial. In part two you'll make it actually run down the wall and look like it's really on the wall, not just over it. Take this bloody text idea and get creative with your own rendition! Create "horror movie" text in After Effects - Part 1 of 2.

Buddy Mason demonstrates how to play the pull shot for the game cricket. You play the pull shot to play short deliveries on the leg side in an attacking way. You have to swing down and roll your wrists upon contact with the ball. The pull shot can be a great attacking weapon in your batting arsenal, here's how to play it! A show that can make big runs quickly. Play the pull shot.

Jade Johnson has risen from virtual obscurity to become Britain's number one long jumper. She domonstrates how to jump further. Make sure you warm up properly - it's vital to make sure you perform to your best and lower the risk of getting injured. Increase your run-up speed as you approach the board - but remember to stay in control. Don't forget your arms! Keep them under control - whatever they do, your legs will follow. Jump further in the long jump.

Wood can be refinished by sanding off the old stain or paint but sanding runs the risk of removing fine details on the wood. Chemical strippers are the best to remove paint, varnish and shellac. Prepare the area on and around the project, strip, scrape and scrub. You might encounter some tricky situations like finding it hard to clean details on the wood. After project is stripped and cleaned, let it dry over night. It is time to refinish the wood. Bleach wood if needed, stain or leave natura...

Richard McEvoy shows how he hits the chip and run shot. The chip and run shot is very similar to a putt but obviously you play it from just off the green. Use a nine iron so the ball can pitch onto the green and roll towards the hole. Hit a pitch and run shot.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

There are a million tutorials on the Internet for how to transmit redstone power up and down, but that's because vertical power transfers are both really important and very counterintuitive. This quick and easy guide should help clear it up!

Hey, hackers! Now that you've hacked/owned your first "box" in my last article, let's look a little closer at another great feature of Metasploit, the Meterpreter, and then let’s move on to hacking a Linux system and using the Meterpreter to control and own it.
Sage Workshops are a series of student run poetry workshops. The workshops are inspired and modeled after the Pen In The Classroom program. The Downtown's Central Library is hosting our workshops. The workshops are in their Teen'Scape department. These workshops will eventually branch out to other organizations or schools. We are currently sponsored by PEN In The Classroom. Part of Sage Workshops is maintaining this world in the wonderhowto website. Please support our project and visit our Fa...

As you may have seen in your city or town, red light cameras are on the rise in the United States. In many instances in my area, these cameras have sprung up seemingly out of no-where, and mostly without any reason. Over use of these systems can make privacy (even on the road) a fleeting possibility.

Just last week, the Flashback trojan scared a lot of Mac users. Now, there's yet another trojan spreading across Mac computers—SabPub. The same Java vulnerability that allowed Flashback in seems to be how this SabPub malware snuck in, along with an Office vulnerability, which was just identified this weekend.
Anyone who follows the TSA blog, run by “Bob”, will know that from time to time the agency attempts to offset the ballooning negative public opinion directed towards it, and the openly criminal behaviour of its employees, by bragging about “dangerous” items that it has discovered and confiscated from the luggage and persons of those traveling through the nation’s airports.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Purple Hyacinth Look that Purple Hyacinth will soon bloom

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

What can I say—it's amazing. Loaded with over 350 LEDs in a matrix, this Daft Punk helmet simply radiates awesomeness. Made by Harrison Krix of Volpin Props, this DIY project took four months to build (much shorter than his last helmet of 17 months).

Snapshot: 12w08a brings us a few nice things a few things I'm not so sure about and a few things I just hope Mojang doesn't incorporate into the next official update.

BebopVox filmed this great run-through of the new 12w07a and 12w07b Snapshots. He goes over what's changed, and some of the current glitches.

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel today's lesson.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

With the purchase of my latest computer, installing Linux turned into a nightmare from Hell. The graphics drivers are probably the biggest issue that anyone with a newer computer will run into when installing Linux. AMD and NVIDIA are the dominant ones on the market, both of which have awful support.
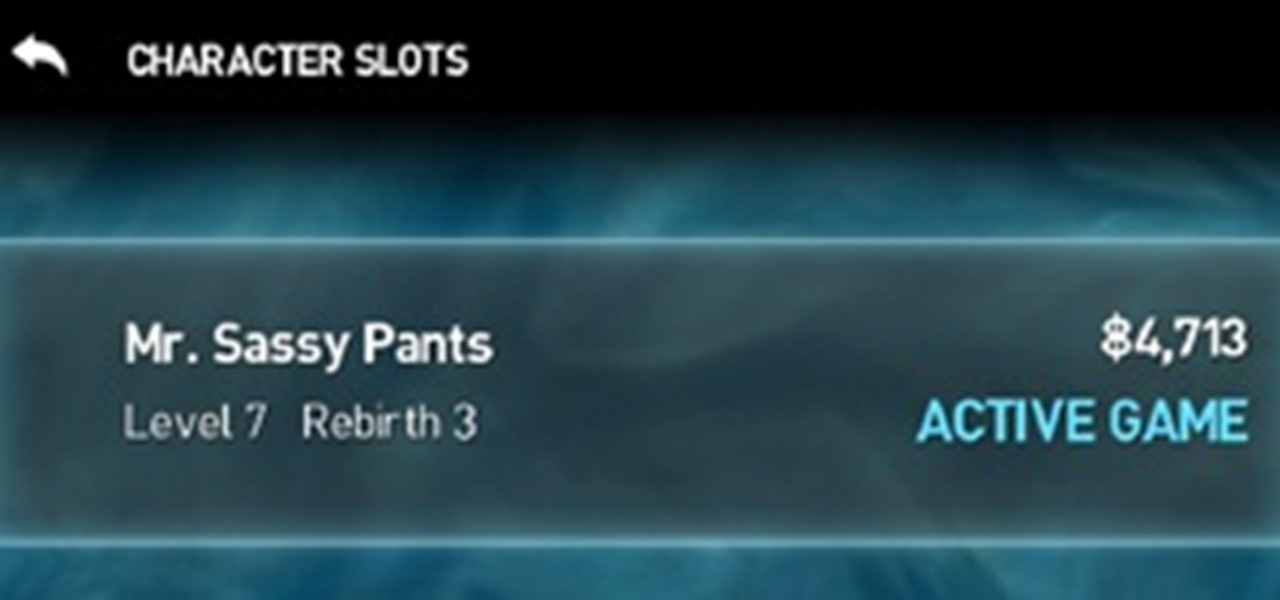
Just removed an important gem from your weapon? Totally screw yourself over by restarting a bloodline instead of the battle you just lost? It sure would be great if you could backup your character so you can always have a safe copy ready to go at a moment's notice. Well, those smart folks over at the Infinity Blade forums have devised a clever way to do this.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. So you have a deep mine, an epic home, a bountiful farm, and mob traps galore, but have you ever considered linking them together into one cohesive unit? With the use of a minecart train station you can turn your disjointed Minecraft manor into a well oiled machine and cut travel times in half.

Edit on a Dime has made it through its first week, dear readers. As the collection of links and blog posts below make apparent, we’re entering into an exciting, dare I say fecund, time for low cost and free editing solutions. We'll have no shortage of apps to try out, argue over and utilize to make some, hopefully great, movies.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Every Modern Warfare game has had bits of enemy intel for you to recover, and they're always hidden within the level. The few pieces I've uncovered across the series has always been through dumb luck. But if you want that 'Scout Leader' achievement, you'll have to find all 46 pieces of intel throughout the entire single player campaign.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

In the level "Going Hunting", you take control of the co-pilot of an F-18 Hornet tasked with shooting down enemy planes. To get the 'You Can Be My Wingman Anytime' achievement, you'll need a perfect playthrough of the level. That means you don't get hit, and all the enemy planes are shot down without running out of ammo. Do this, and you'll get 30G on Xbox 360, or a bronze trophy on PlayStation 3. If you need some guidance, check out the video below.

Here's a tougher achievement for you guys to get in Battlefield 3. In the level "Thunder Run", you take control of a big friggin' tank. Use it to take down six enemy tanks before you reach the fort, and you'll get 25G on Xbox 360, or a bronze trophy on PlayStation 3.

Now, I know what you're thinking... "I need an extra sexy coffee table that is like no other."

Minecraft World user Xhoes is building an epic "Capture the Flag" arena. While still a work in progress, this epic arena boasts two fortresses with flags, obstacles and objects to hide behind in the battle field, and an underground passageway.

Having an SSH or Secure SHell to tunnel your traffic through is something we have talked about many times at Null Byte. As we know, it allows us to securely route and encrypt our traffic through a remote server, effectively anonymizing us and protecting our traffic from all forms of analysis—simultaneously. We have gone over how to make a home SSH tunnel. However, the question has come up, "How can I get an SSH tunnel to somewhere other than my computer?" This would be useful in a situation w...