This video shows you how to easily remove the tracking Cookies from your web browser. Normally, if you use AVG Free, it will detect the tracking cookies but not delete them. This video will show you how to manually remove that tracking cookies without using any software. The first thing you have to do is click Start menu, then search for Run. In the Run windows, paste the following: C:\Users\YOUR PC NAME\AppData\Roaming\Microsoft\Windows\Cookies , and hit Ok button. Delete all the files that ...
Now your computer is running slowly while opening the multiple programs, and for checking mails. The following steps easy to get faster the computer.

This is a directional video of how to increase the speed of a Windows Vista PC. The first step is to uninstall programs that you do not use. Then you want to go into MSCONFIG and remove unnecessary start up entries. You can also configure the performance options of your computer in the computer's properties. The next step is to go to the system tools and run Disk Cleanup. It is also important to run the Defragmentor from the system tools.

This video is a quick overview for installing the "Google Chrome Frame" to speed up applications in your internet explorer.

Are you aware of your water usage? Are you really doing all you can to conserve water, our most precious resource? Here are some simple ways you may not have thought of and some facts about the amount of water wasted on a daily basis in America.

Get some tips and tricks to helping your dog become a well-obedient and well-trained dog. Watch this video tutorial to see how to teach your dog to "come".

The tarbuck knot is a non-jamming knot, great for when the rope will be bearing a heavy load, and shocked with sudden weight. Form the loop around the winch then make a serises of turns around the standing part in a clockwise direction. Bring the running end down to the base of the runs and make another clockwise turn finishing off with a figure eight through the exiting strand from the top turn. Watch this video knot-tying tutorial and learn how to tie a tarbuck knot.

In this tutorial video, we show you how to jailbreak Apple's latest device the iPhone 3G to start the process you need to do the following:

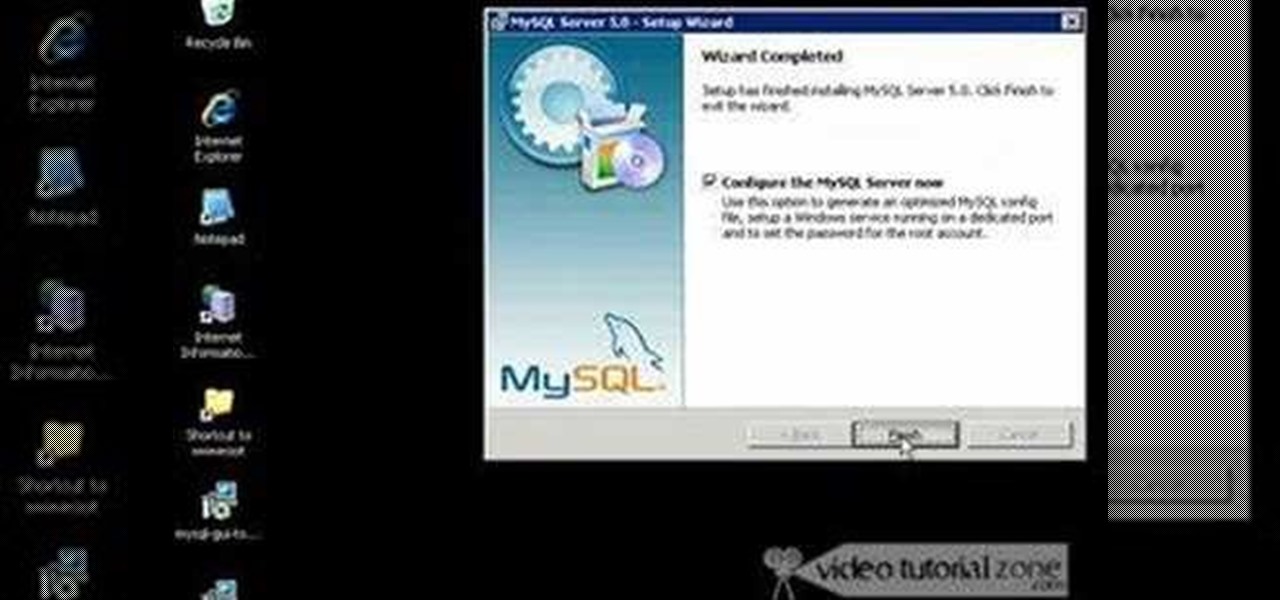
MySQL is a multithreaded, multi-user SQL database management system which has over 10 million installations. It runs as a server providing multi-user access to databases. It is by far the most popular and common database used in web applications throughout the world, and almost all hosting companies provide it free of charge to their users. MySQL AB makes MySQL Server available as free software under the GNU General Public License (GPL). For this tutorial we are going to download and install ...

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

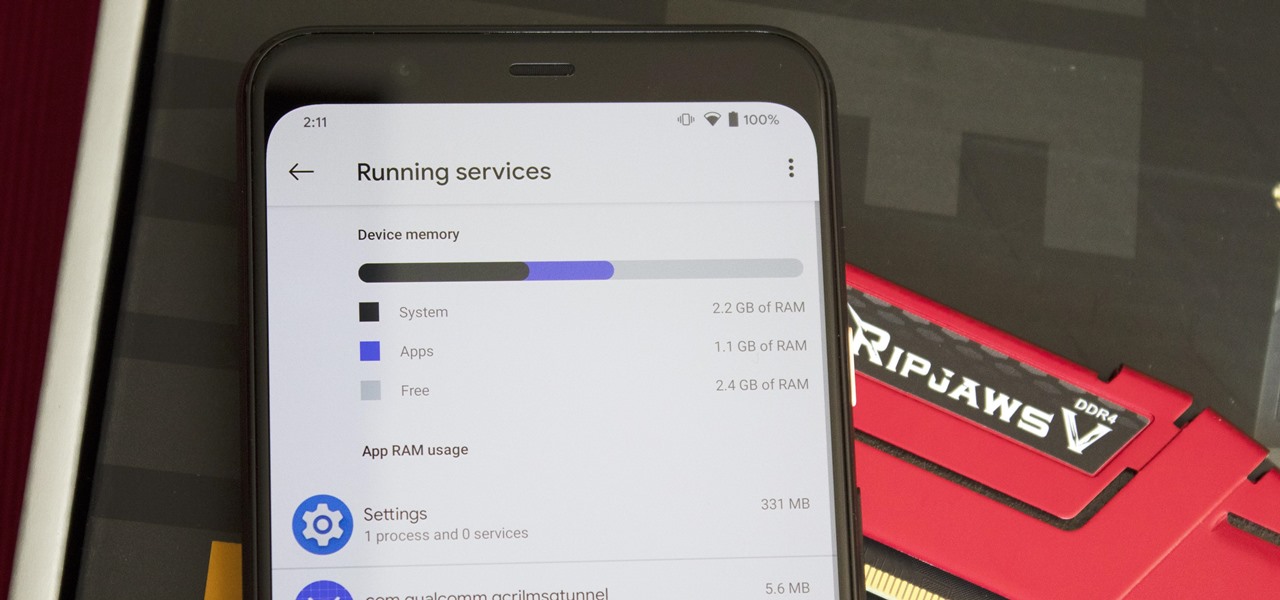
Not every app is designed well. With nearly 3 million apps on the Play Store and countless more that you can sideload from other sources, there are bound to be a few stinkers. And many of them do a terrible job using RAM.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

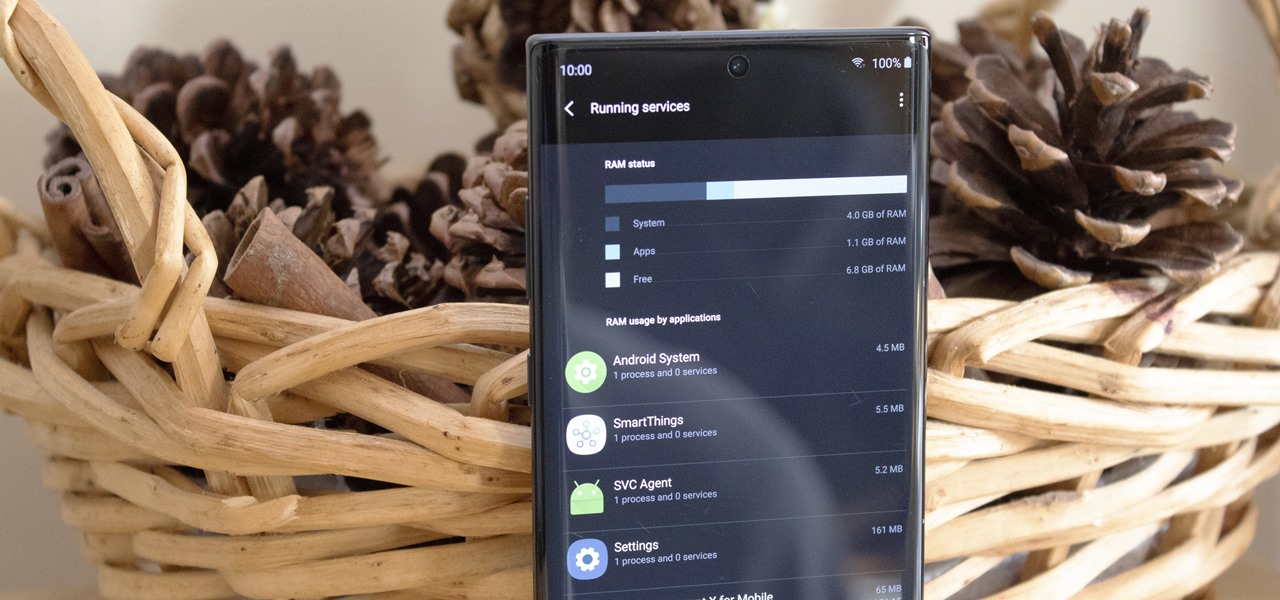
Every 5G model of the Galaxy S20 comes with 12 GB of memory. This amount of RAM is overkill, but Samsung's been putting similar amounts in its flagships for years. Since you have it, why not put it to use? With One UI 2, you can.

It's pretty much a given at this point that Facebook has a lot of data on us. While you might be conscious of the data you share with Facebook when you post, upload photos, or chat with friends on Messenger, you might not be thinking about all the data it receives from websites and apps you use outside the social media giant. Now, you can actually do something about it.

There are phones nowadays with 12 gigs of RAM, but they'll cost you well over a grand. The majority of Android devices have much less memory — I'd wager most have less than 4 GB. And with the system taking up around 2 GB, that leaves user-installed apps little room to breathe.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

The newly enhanced focus from Magic Leap on enterprise, announced on Tuesday, also came with a few companies opting to weigh in with their experiences developing for the platform.

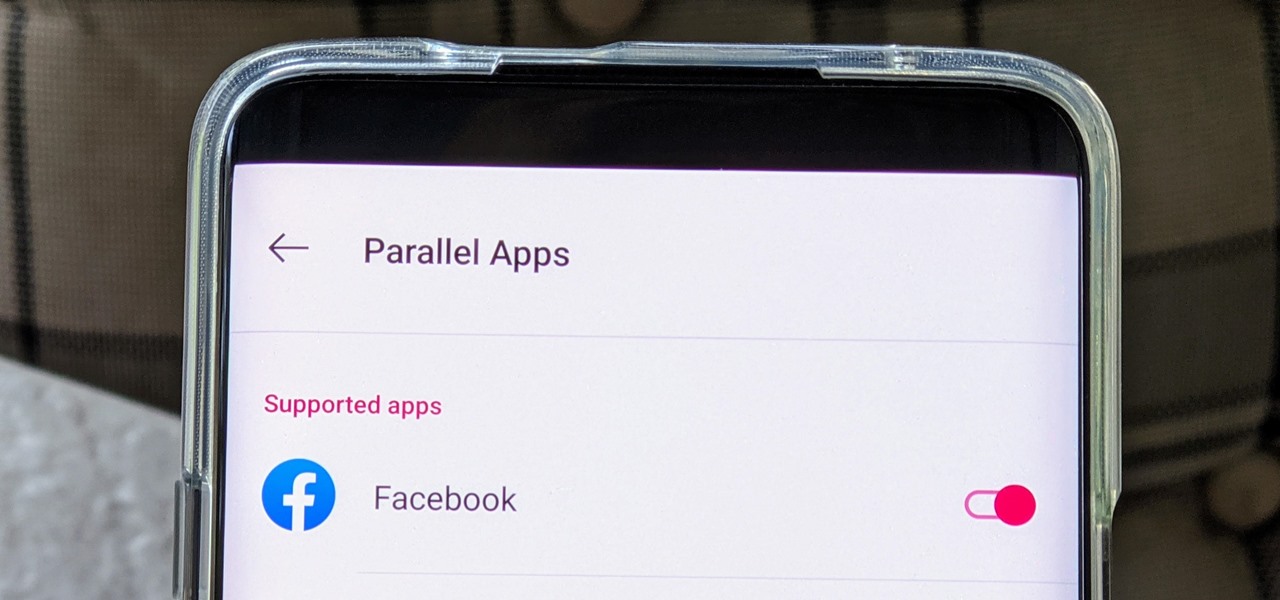
The Facebook app only supports one account being logged in at a time — but what if you need one for work and one for your personal life? That would normally involve logging out and logging in every time you need to switch accounts, but your OnePlus device offers a much better solution.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Google's strategy for updating its apps with dark mode options is apparently "one at a time" and "as slow as possible." Even after the company added a dark theme to many of its apps for Android and iOS, such as Calendar, Chrome, Keep, and Photos, Gmail seemed to remain "light" for the longest time. However, the app now supports dark mode on both mobile OSs. Here's how to enable it.

Apple slowly rolled out its new credit card, Apple Card, throughout August, but announced on Aug. 20 that it's now available to all qualified users in the US. Here's the problem: it's not totally obvious how to apply. Without any notification, directions, or clear settings, how do you even fill out an Apple Card application? Luckily for you, we're here to show exactly how to find it.

Right now, Apple is testing two versions of iOS. On the one hand, you have iOS 13, buggy but feature-filled. On the other, iOS 12.4. The latter just got an update to the fifth developer and public beta versions, 13 days after the release of iOS 12.4 developer beta 4.

With iOS 13's developer beta in full swing, it can be easy to forget that there's an entirely separate iOS beta cycle still running right now. Yes, iOS 12.4 is still in beta, and unlike iOS 13, it's available to the public for testing.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Talking Tom has long been mesmerizing children of all ages with his ability to repeat words and phrases and encourage touch interactions. Now, the lovable cat and his band of cuddly friends have ventured into the endless runner genre as heroes bent on saving Angela and their city from a band of mischievous raccoons.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

While AT&T is gradually showing off the powers of its 5G technology in the US via the Magic Leap One, another major wireless company is doing the same in the UK using the world of fashion.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

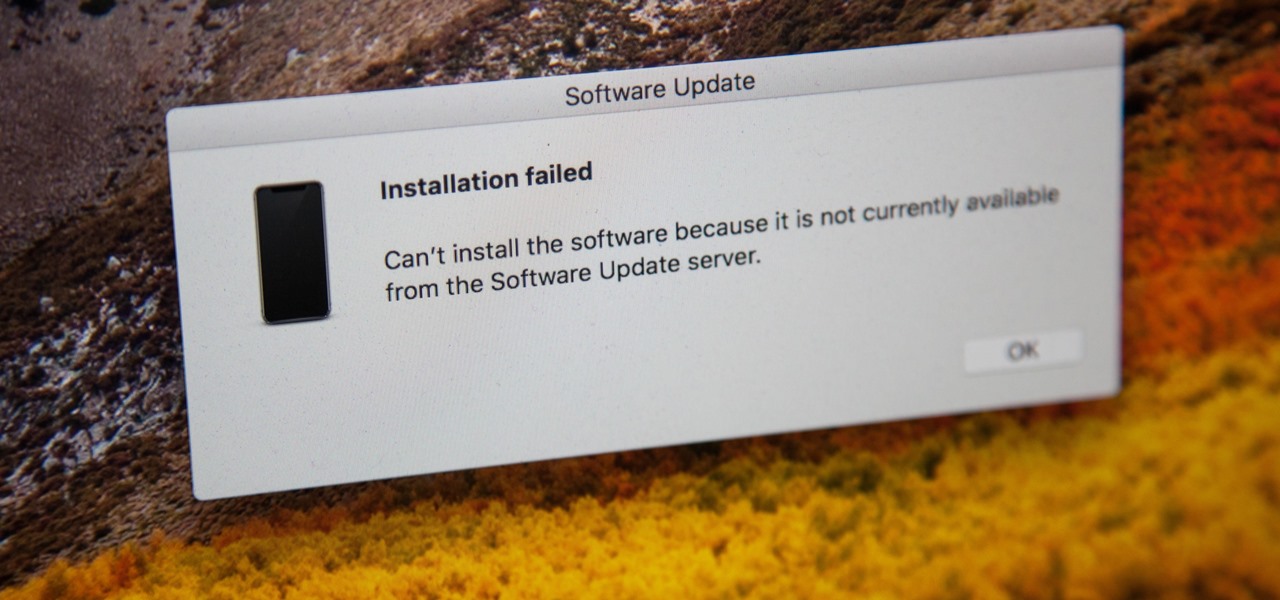
If you're currently running macOS 10.11 or higher on your Mac and connect your iPhone to sync with iTunes, you may get an alert saying that "a software update is required to connect to your iPhone." Here's everything you need to know about what that means, how to update your system, and what to do if updating doesn't work.

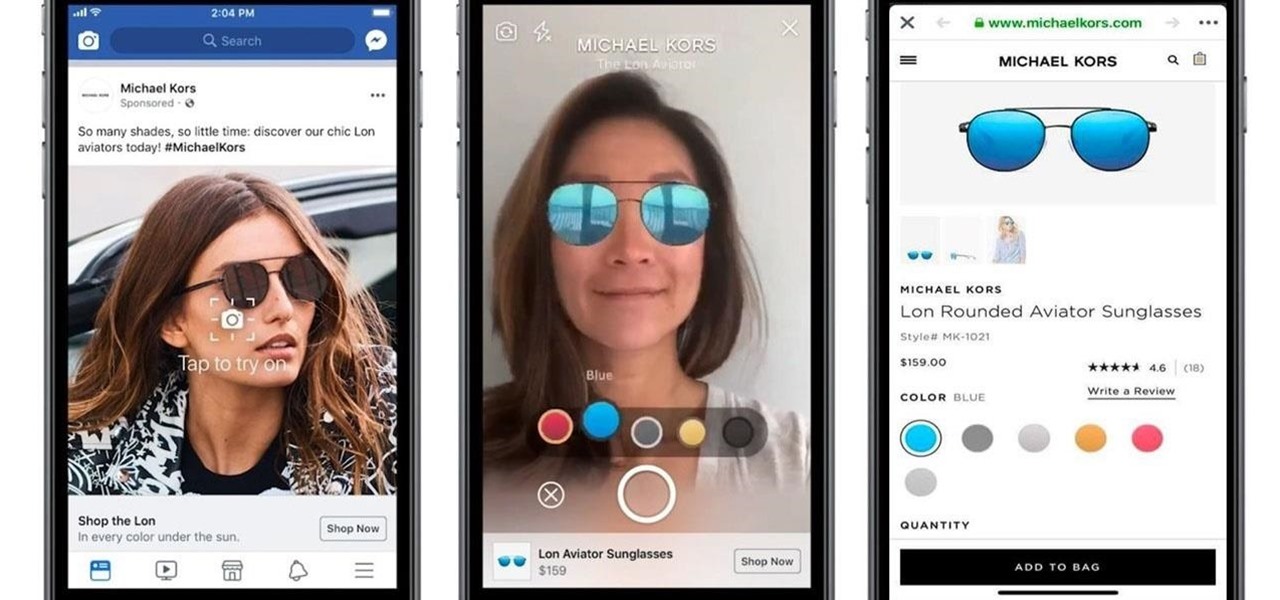
Facebook is preparing to make augmented reality experiences for brands more visible in its mobile app with Tuesday's introduction of augmented reality ads in its News Feed.

With tons of titles to choose from on the iOS App Store, you'll never be lacking when it comes zombie shooters. Unfortunately, the same can't be said if you're more interested in base-building and defending against the undead. PlayStack aims to change this, and they've soft-launched Survival City in the Philippines for further development. With a simple hack, you can try the game yourself right now.

Even in augmented reality, Wile E. Coyote still can't catch the Road Runner. The latest AR experiment from developer Abhishek Singh brings the classic Looney Tunes duo into the real world.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

When Google first announced Android Oreo (Go edition), many believed these devices would be focused more on developing countries. However, thanks to ZTE, we'll be getting Android Go stateside, so US customers on even the tightest of budgets can still enjoy the convenience of a smartphone.

From its official launch back in September, iOS 11 has been equal parts revered as it has been criticized. Even with all the great, new features we've come to expect from a major iOS update, plenty of bugs and glitches have forced users to overlook the positives. Perhaps that is why, four months later, 25% of iPhone owners are still running iOS 10.3 or earlier.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

To commemorate the rollout of the AR+ update for Pokémon Go, Apple CEO Tim Cook took to Twitter to promote and celebrate the moment his company's ARKit platform made possible.

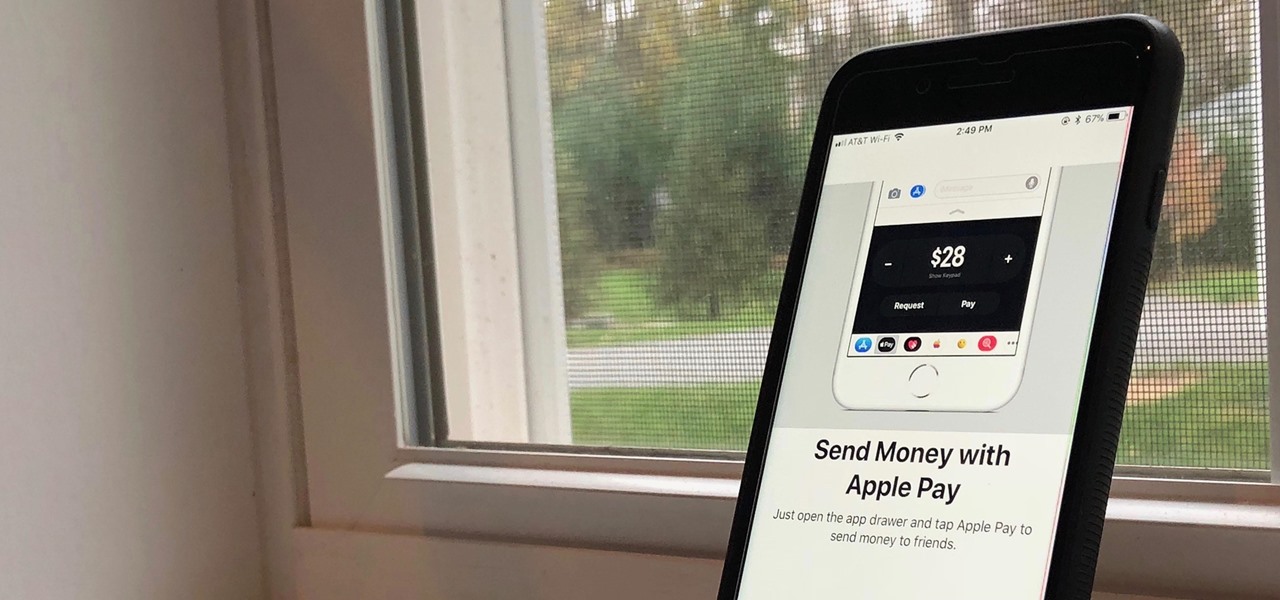
First showcased back in June at WWDC, Apple Pay Cash is Apple's answer to Venmo. Although iOS 11 has been out in the wild since September, this new iMessage feature has been mysteriously absent. That's finally changed with the second beta of iOS 11.2 — Apple Pay Cash is here.