Update 10/14: Developer paphonb has added rootless Google Now integration to the leaked Pixel 2 launcher, so now, anyone running Android Nougat or Oreo can get the full Pixel 2 home screen experience. For those running Lollipop or Marshmallow, we've left the unaltered leaked version linked out below, but we've added a new link for the tweaked version with Google Now integration.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

As a long-distance runner off and on for the past, I absolutely detests hills. While there are many apps that can measure elevation and slope for certain routes, understanding spatial data on a line graph or even an elevation map can be difficult.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Sports gaming company ePlay Digital, Inc. is looking to capitalize on the fall launch of iOS 11 and ARKit with an augmented reality fantasy sports app.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Netmarble's Lineage 2 Revolution has finally soft launched in the Philippines, giving mobile gamers hope that a worldwide release isn't too far off. What many don't realize, however, is that this game can be had for free right now — with a little digital elbow grease, that is.

If you find this update from Pinterest more than a little creepy, I agree. If you don't, then keep reading about how Pinterest's updated "Lens" feature is your next must-have tool!

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

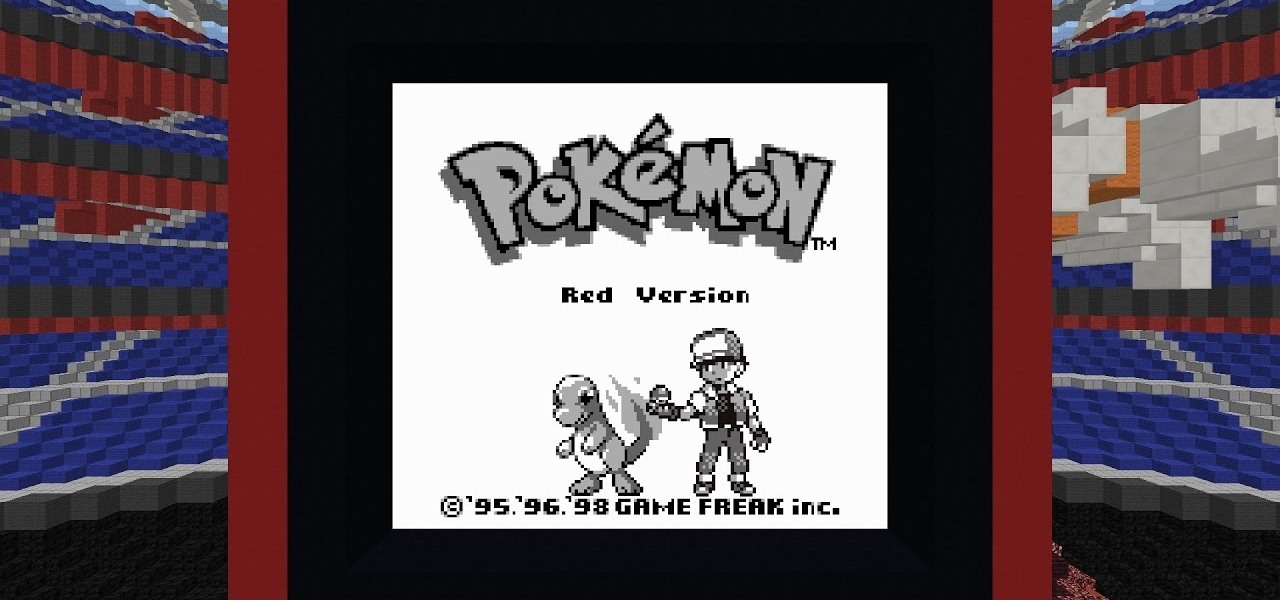
Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How long did it take him? Almost two years.

Tom Clancy games, like Rainbow Six and Ghost Recon: Wildlands, are famous for their realistic and immersive gameplay that focuses on covert, low-intensity warfare. Ubisoft now appears to be testing the overcrowded waters of mobile gaming with the release of ShadowBreak, and has soft released the game for both iOS and Android in Canada for further development, which means that with a little tinkering, you can play ShadowBreak in any country.

Netmarble's ChronoBlade, a mobile role-playing game, has made its way to iOS and Android by way of a soft launch that will make it exclusive to users in Canada and Singapore for a couple of months. Its console-quality graphics and extra features will surely make it a hit when it's released worldwide, but if you've got a little gumption, you can skip the wait and install it today.

Blizzard's Hearthstone was a rousing success with more than 10 million downloads on the Google Play Store. Not taking things lying down, Bethesda, the creator of The Elder Scrolls, has come up with a card game based off its popular fantasy franchise. The Elder Scrolls: Legends is now out in the wild, though, officially only available for select Android tablets. But with a little creativity, there's a way to game the system and play Legends on any Android device. The Elder Scrolls: Legends is ...

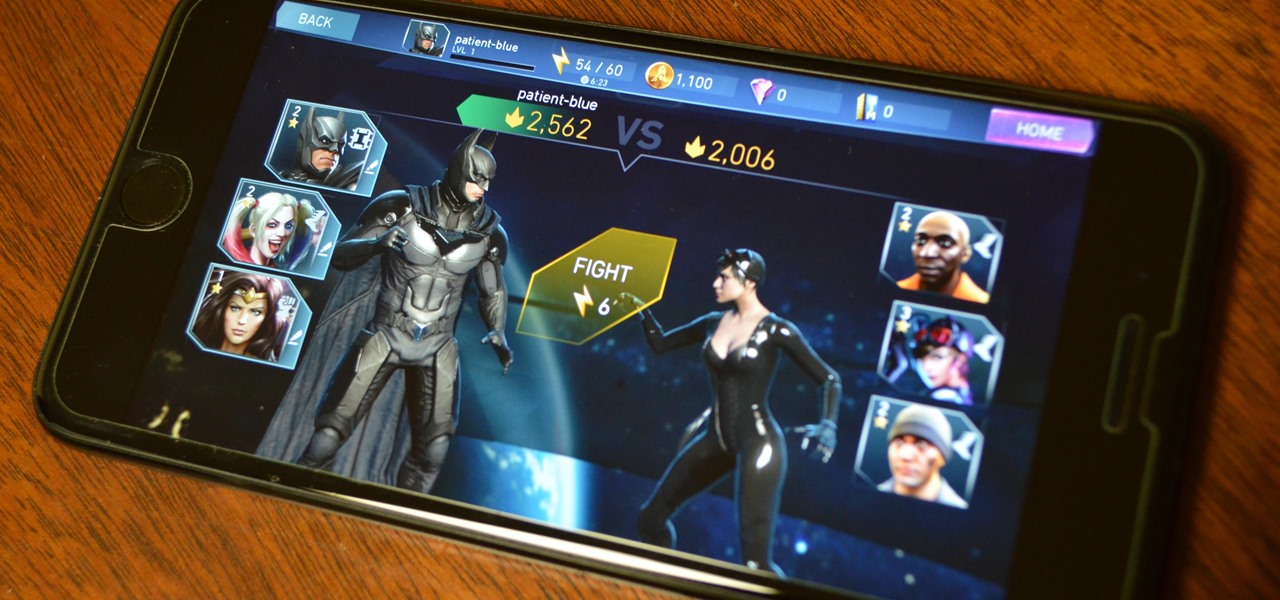
Based in the DC Universe, Injustice: Gods Among Us was a runaway success on the iOS App Store, generating enough downloads to rival its console-based iteration in terms of popularity. But now, the sequel to this long-running game, Injustice 2, is finally out in the wild, as it was soft-launched in the Philippines this past February.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Bats are an important part of the US economy. They devour metric tons of bugs every night that would otherwise ravage crops and also be generally disgusting-looking and make you itchy. But they're in danger from a nasty fungal infection called white-nose syndrome, which has just popped up in Texas and has been spreading across the country.

With the Game Developers Conference (GDC) in San Fransisco just a few weeks away, Microsoft Senior Program Manager Vlad Kolesnikov has announced via Channel9 (Microsoft's developer news outlet) that not only will new low-cost virtual reality headsets be coming in March to developers, but that they will be at GDC, too.

Being able to take screenshots on Android isn't something we were always able to do. It was added to stock Android in Ice Cream Sandwich 4.0 (Gingerbread 2.3, if you were a Samsung TouchWiz user) as a simple full screen screenshot, and that's the way it's remained ever since—until now.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

Emojis, for better or for worse, have essentially taken over online forms of communication. And now, thanks to a recently discovered feature in iOS, they are going to change the way you search for nearby places.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

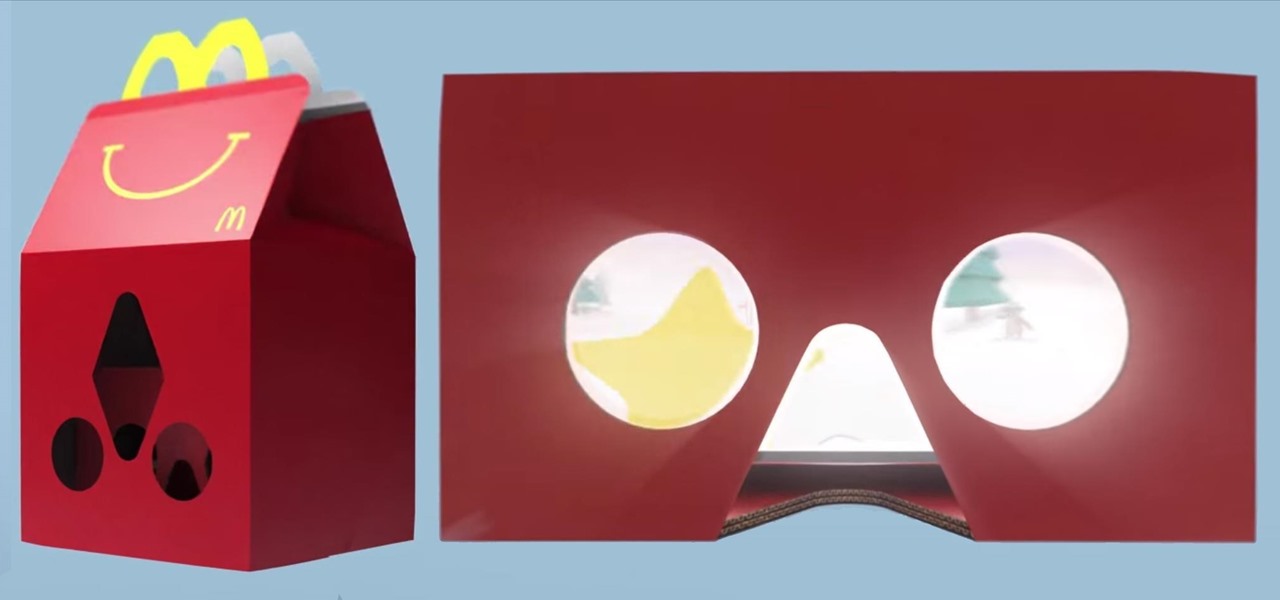
Another day, another company hopping on the virtual reality bandwagon. Today, it's fast food behemoth McDonald's, which is testing limited edition Happy Meal boxes that you can turn into a VR headset by punching out a couple holes and tearing along a few perforated seams. The resulting headset is a lot like Google Cardboard, with the lingering scent of fry grease.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

The digital pen on the Surface Pro 4 and Surface Book is an indispensable tool for serious note-takers and artists alike.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

Hello friends. This is actually my first how to.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.