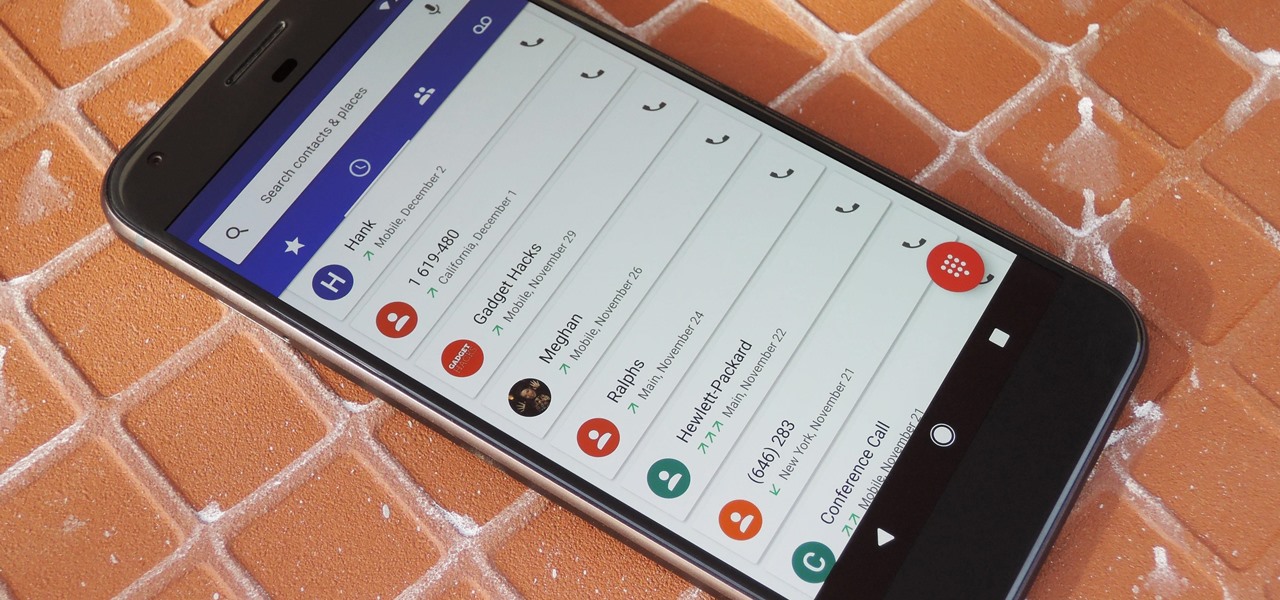
By default, Android limits your call history to the last 500 incoming, outgoing, or missed calls. When you reach this limit, older entries get trimmed off the bottom of the list and deleted forever. This isn't an issue with storage space, because even the biggest call logs only occupy mere kilobytes, so it's really just an artificial limit.

Ready to finally play some Pokémon on your HoloLens? Here is your chance! KennyWdev has released a video showing off his newest build of PokéLens, a Pokémon clone for the HoloLens similar to Pokémon GO. In the video, you get to see two Pokémon battle it out on what appears to be an office floor. Apparently, Pikachu is "super effective." This coincidentally appeared online the same day that another developer, Sky Zhou, showed off his Smash Brothers-style Pokémon game.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Google's new Pixel and Pixel XL smartphones are available for pre-order right now, but the general public won't start to get their hands on these devices for another week or two. Tech reporters got some hands-on time at Google's launch event on October 4th, but camera testing wasn't allowed, and the Wi-Fi coverage at the event was too flooded for real-world performance reviews.

People fear virtual reality will isolate us, but the right experience can prove it does the opposite.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

If not the future of computing in general, augmented, virtual, and mixed reality certainly will change the world of gaming. If you want to try your hand at shaping this evolved medium, the Unite Europe conference posted a talk that explains the first things you need to learn to develop holographic games.

The latest beta of the popular open-source media player VLC just hit the Windows Store, which means it not only runs on Windows 10 and Xbox One, but the HoloLens as well.

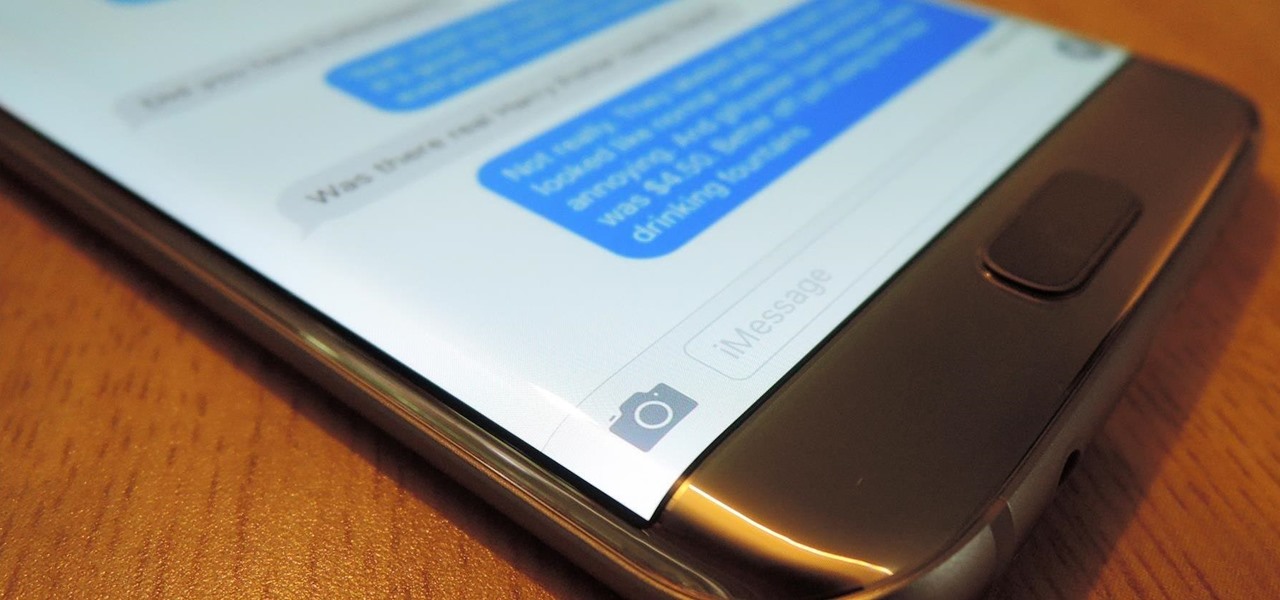
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

The world's first cloud-oriented smartphone, Nextbit Robin, is now available to the masses via Amazon with free one-day shipping for Prime members.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

If you've been around computers long enough, you've probably heard the phrase "have you tried turning it off and on again?" This trick usually works because it forces your computer to empty out the contents of its RAM and disk caches when you restart.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

There was lots of new tech to check out at CES 2016, but you could argue that the majority of the big-ticket items weren't the most unique things in the world. Thankfully, there were a few innovative, unconventional ideas on display, and here are some of our favorites.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

When it's frigid outside, all you can think about is getting inside and shutting out the cold. But sometimes even the largest house can get a bit, well, stuffy.

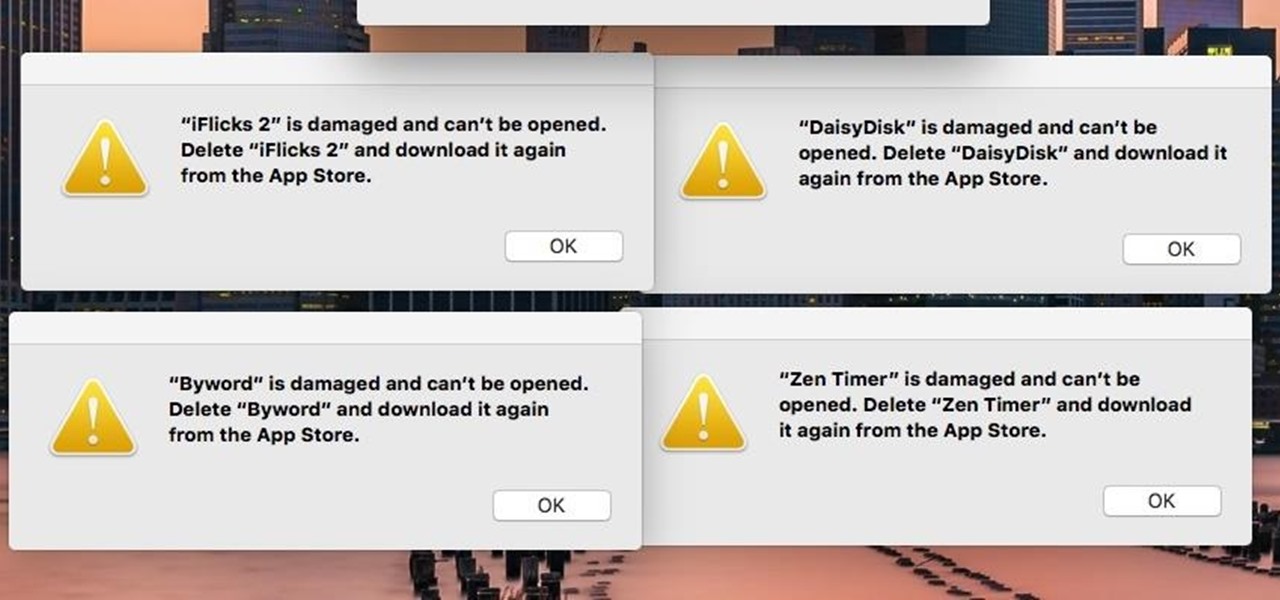
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed:

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

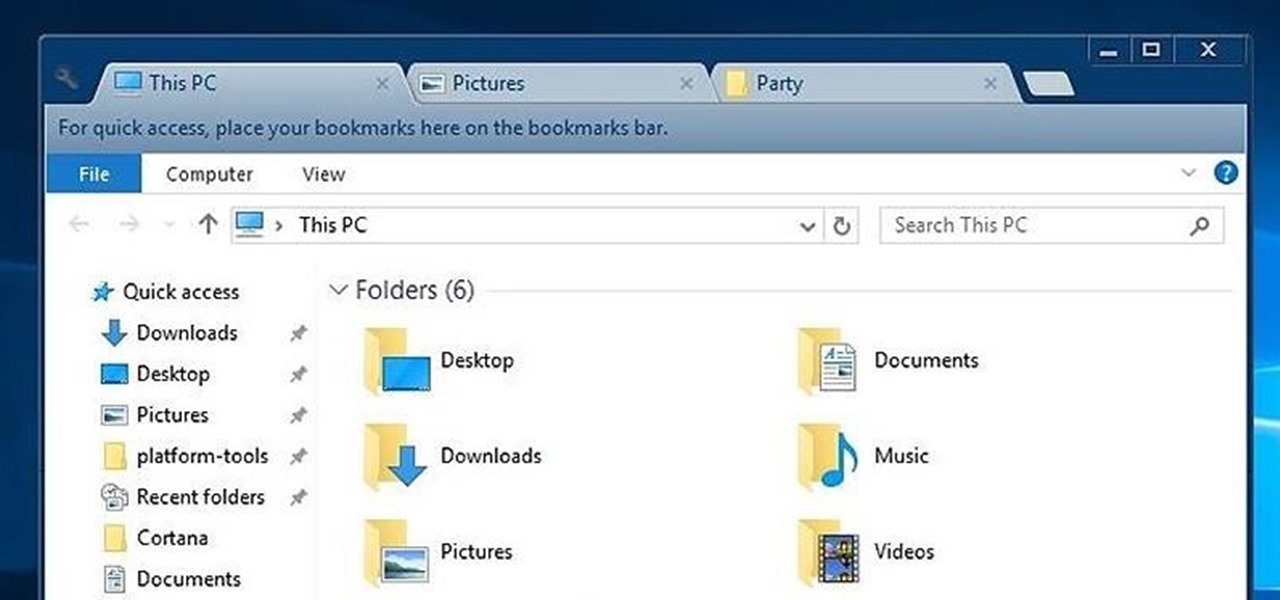
While Windows 10's new File Explorer is just as, if not more, useful as it was in previous iterations of Windows, it could definitely still be better. Two features that would greatly improve File Explorer are tabbed results and a customizable user interface, similar to how they are in Google Chrome.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started

Work, school, and everything in between keeps us pretty busy—so much so, that sometimes we run out of the house with our shirts on backwards, our headphones misplaced, and our computers running all day long.

This tutorial is for those who've purchased an account with Private Internet Access to hide your VPN and would like to set it up in Kali. Please note, you can chose to run your PIA service from your Windows computer without configuring it in linux as long as you'll be using a NAT connection. Using a NAT connection will allow your Windows machine and Kali Virtual Machine to use the same IP address, hence if your IP is hidden on one, it will be hidden on the other.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

One of the biggest gripes I initially had with the LG G3 was the lack of options for the Shortcut keys, which are the volume keys that allow you to launch the camera or the QuickMemo+ app directly from the lock screen. I never use QuickMemo+, so having it as a shortcut was a complete waste of functionality.

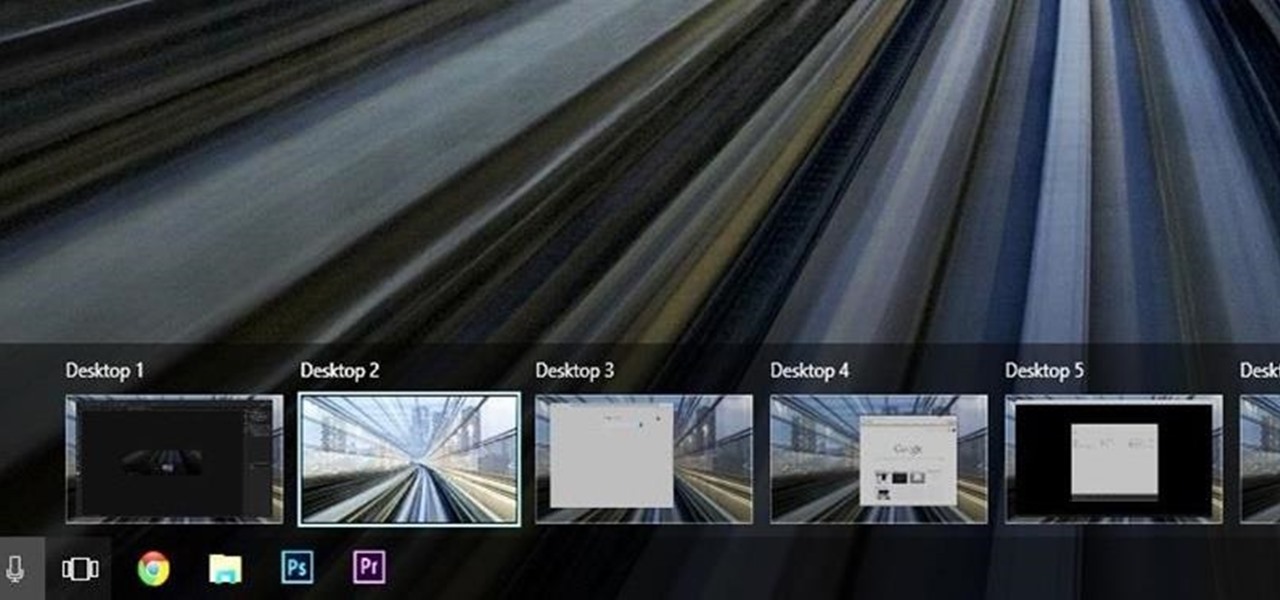
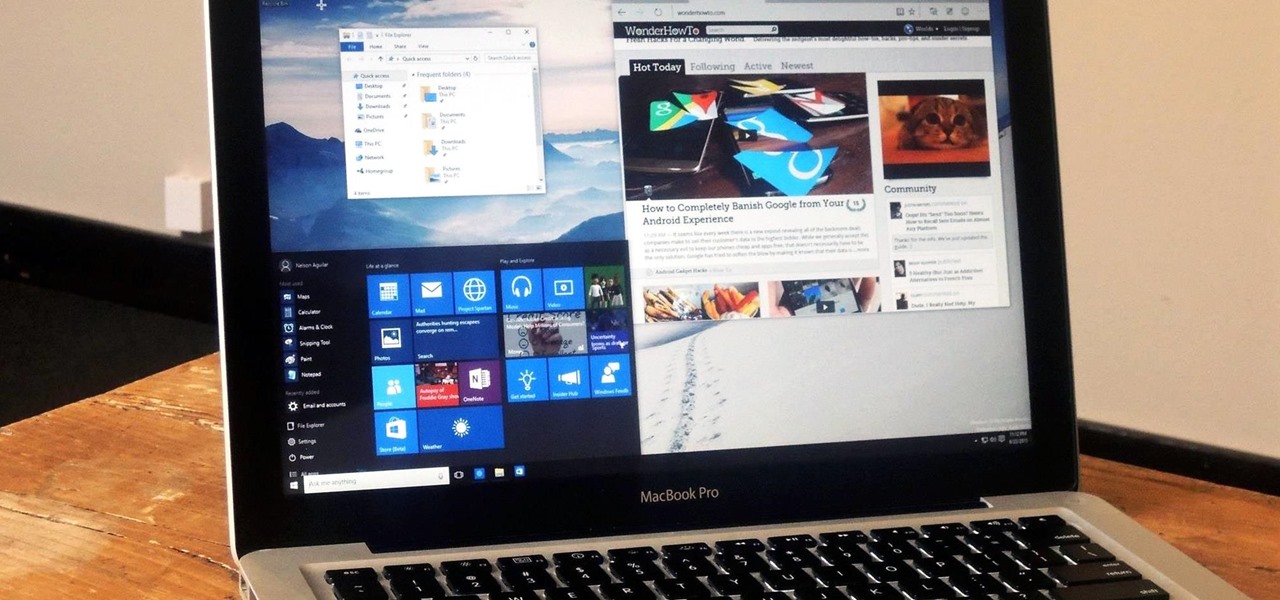
Linux and Mac users have long enjoyed the use of multiple virtual desktops to free up clutter on their home screen and keep individual workflow environments separated, but Windows users have always been stuck with one solitary desktop.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.