Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

In its goal to push the visual quality of real-time rendering to a new level, Unity is starting the new year off right by releasing a sneak peek at its upcoming interactive rendering improvements via a short, three-minute first-person interactive demo called "Book of the Dead."

Cyber Week 2017 is still upon us. If you're looking for an iPhone X deal, you might still have time to score one. But maybe you already have — a reported six million people purchased the newest iPhone over the Black Friday weekend. If you're one of those lucky millions, there's a slight learning curve to using the X over other iPhone models.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.

Zika is a threat to unborn babies — the virus can cause neurological damage if it infects a mother during pregnancy. But as with many things, our solutions to the problem aren't always all that much better than the problem itself.

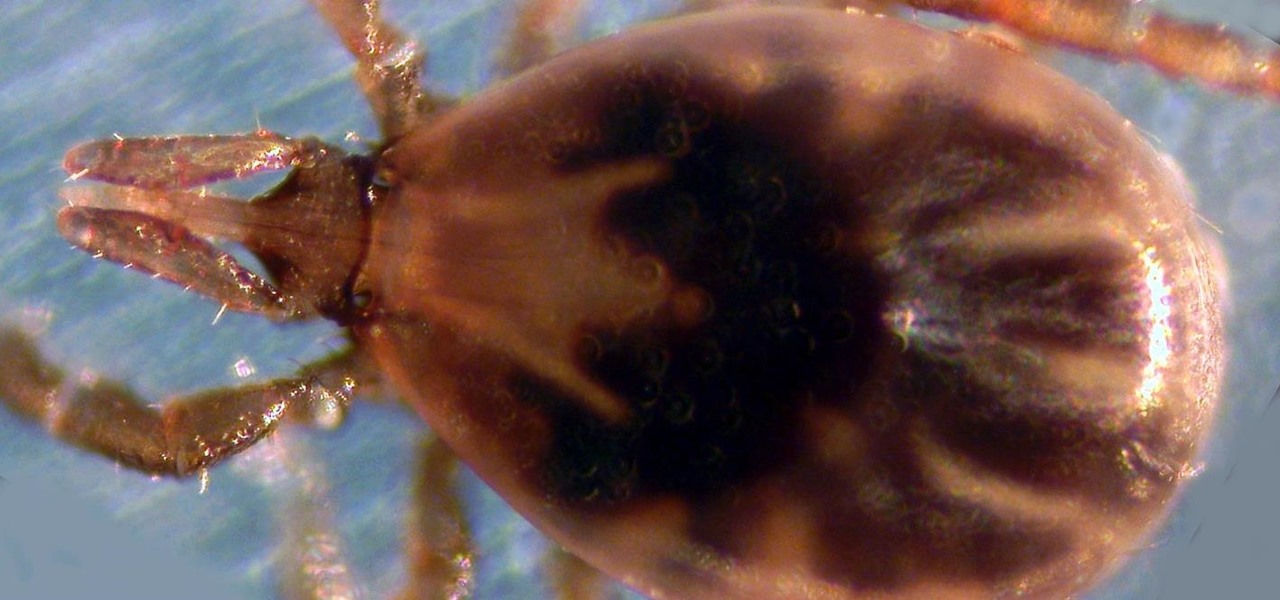
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

Now that we've got all of our software installed, we're going to proceed with the next step in our HoloLens Dev 101 series—starting a fresh project and building it into a Holographic application. Then we will output the application to the HoloLens Emulator so we can see it in action.

We're almost there to completing the setup of your Mac for hacking! Now that we have Git and Homebrew under our belts, it's time to take on something fairly easy, but very important for our hacking needs.

Before the iPhone 7 was launched and all the unrealized reports about the phone's features were tucked back into their annual rumor mill, there was some speculation about wireless charging. Specifically, whether or not the iPhone 7 and 7 Plus would support it. We now know they don't, and here's why.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

2 + 2 = 4. That's about as much math as I can handle without a calculator on a daily basis. I literally hate doing math more than anything in life, mostly because I'm not good at it—and I hate doing things I'm not good at.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Try adding some weighted bar exercises to your workout routine to not only strengthen you arms but to increase your core and back strength as well. Use heavier weights to build larger muscles and more reps at a lighter weight for lean strong muscle.

In this series of art instruction videos, our expert painter shows you how to mix primary and secondary colors as well as how to effectively use these colors in your own work of art. Start with six colors and quickly turn those six into twenty four using tips from our experienced artist. Begin with a solid grasp of the basics from Expert Village, then let your imagination do the rest. You will be creating your own masterpieces in no time!

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Primarily caused by the bacteria Borrelia burgdorferi, Lyme disease is the most common tickborne disease in the US. By all predictions, 2017 is expected to be a banner tick year in several regions. If you have children, it is important to know what to expect.

Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. When a smaller component like a proximity sensor fails, you're often left with no other choice but to take it to a professional.

Joe McKenna died when he was 30 years old. A young married man with his future ahead of him, he was cleaning up the station where he worked as a fireman. Struck by a piece of equipment fallen from a shelf, Joe complained of a sore shoulder. Over the next week, Joe worsened and ended up in the hospital. Chilled, feverish, and delirious, his organs shut down from an infection we'd now call septic shock.

I'm starting to wonder if the people at Boston Dynamics have ever watched a Terminator movie. Not just because the robotics company with the oxymoronic name develops machines that are able to move around environments with animal- and human-like agility, but because the people testing them seem to take such joy in openly antagonizing their creations. It's one thing to tempt fate by creating superhuman robots that could potentially end mankind. You've reached a whole new level of hubris when yo...

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Instead of suffering through long, dull meetings with your supervisors and coworkers, you can turn those office table sessions into your very own psychological experiment.

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

With only a few days until Apple Watch preorders begin, and just a couple of weeks until its official release, the biggest question in Apple Land seems to be: "Are you going to get an Apple Watch?"

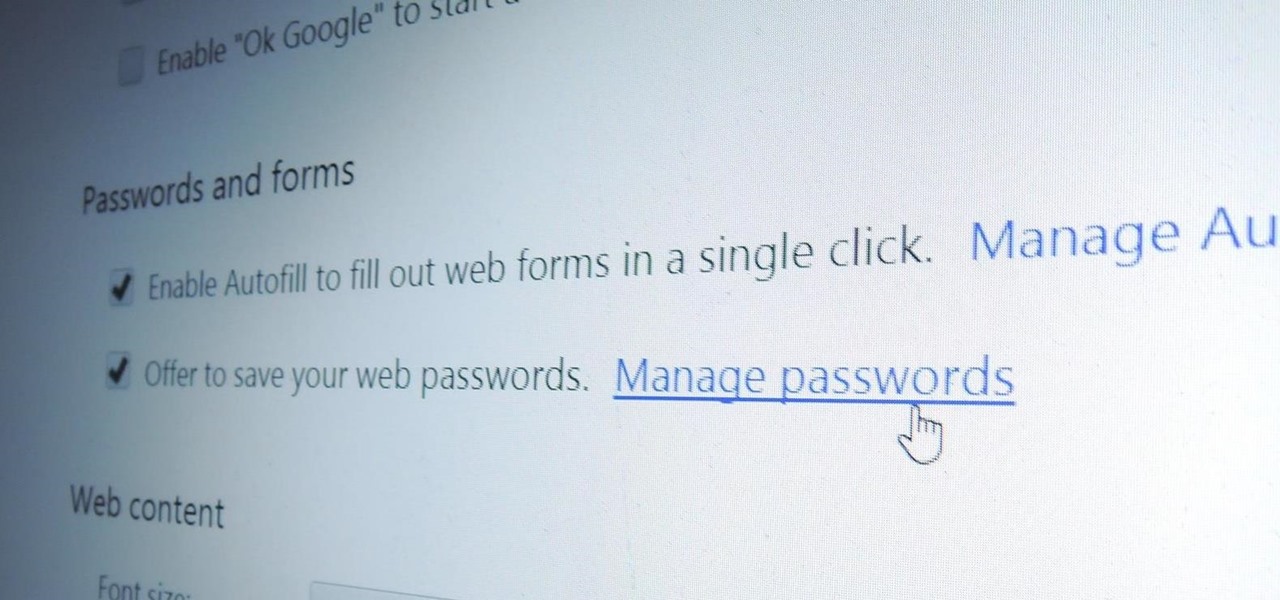
Chrome, Firefox, and Safari all provide built-in features that allow you to save your username and password for your favorite sites, making the process for entering your credentials a breeze when you revisit them.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

It may seem impossible to win an argument against an irrational person, but it turns out the tried-and-true techniques that hostage negotiators use against hostage-takers work surprisingly well in everyday situations. You may not ever deal with a real hostage situation personally, but life is full of negotiations with unreasonable people, and those conversations don't always have to end in rage or disappointment. The mental techniques that professional hostage negotiators use can help both pa...

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.