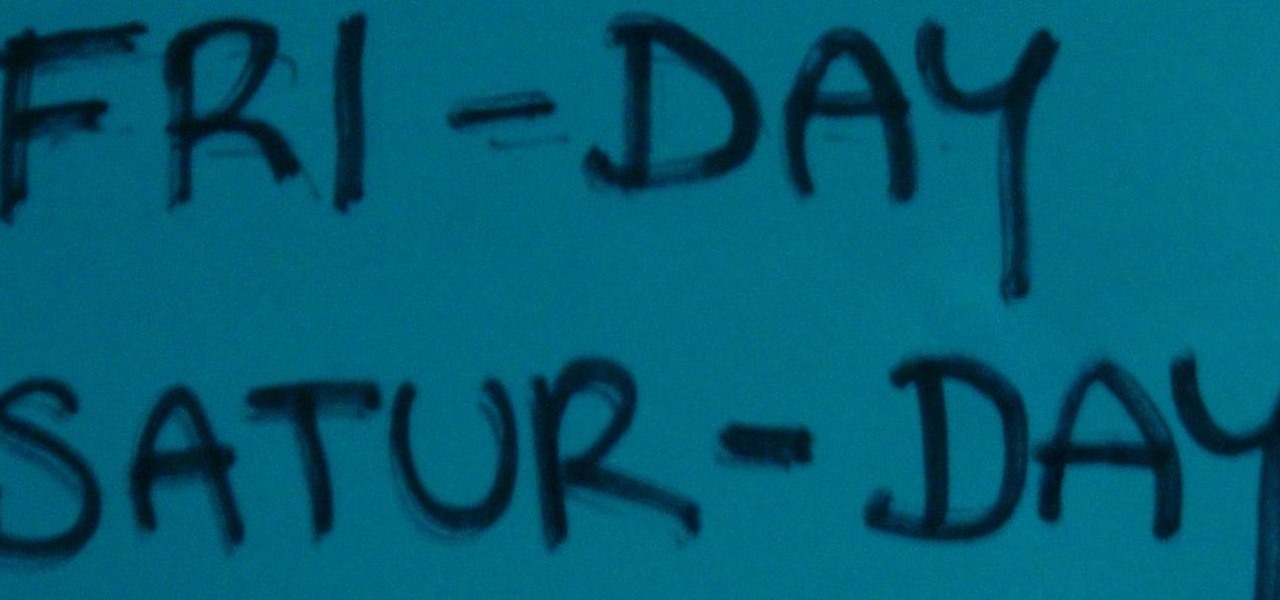The "Discover" tab in the latest version of the Google Home app has a new tip that says multiple users are now supported. Google Home uses a built-in speaker and microphone combo to give users access to smart search, a personal assistant, and smart home controls. This addition has the potential to make the voice-activated speaker powered by the Google Assistant much more efficient for households with more than one user. However, it seems that Google wasn't quite ready to announce this new fea...

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

We've already taught you how to clench your fist to make healthier food choices, and how to make sure you eat healthily at a restaurant, but it turns out there are even more mind hacks we can use in our never-ending quest to control our appetites.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

Like in the original Black Ops, there are a bunch of funny and cool Easter eggs built into Call of Duty: Black Ops 2. Most have been discovered, like the Atari arcade invincibility on Nuketown 2025, but perhaps you didn't know about Thor's hammer?
Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

The mystery surrounding Overture, an app that showed up in the Magic Leap World app store along with the latest Lumin software release, has been cleared up.

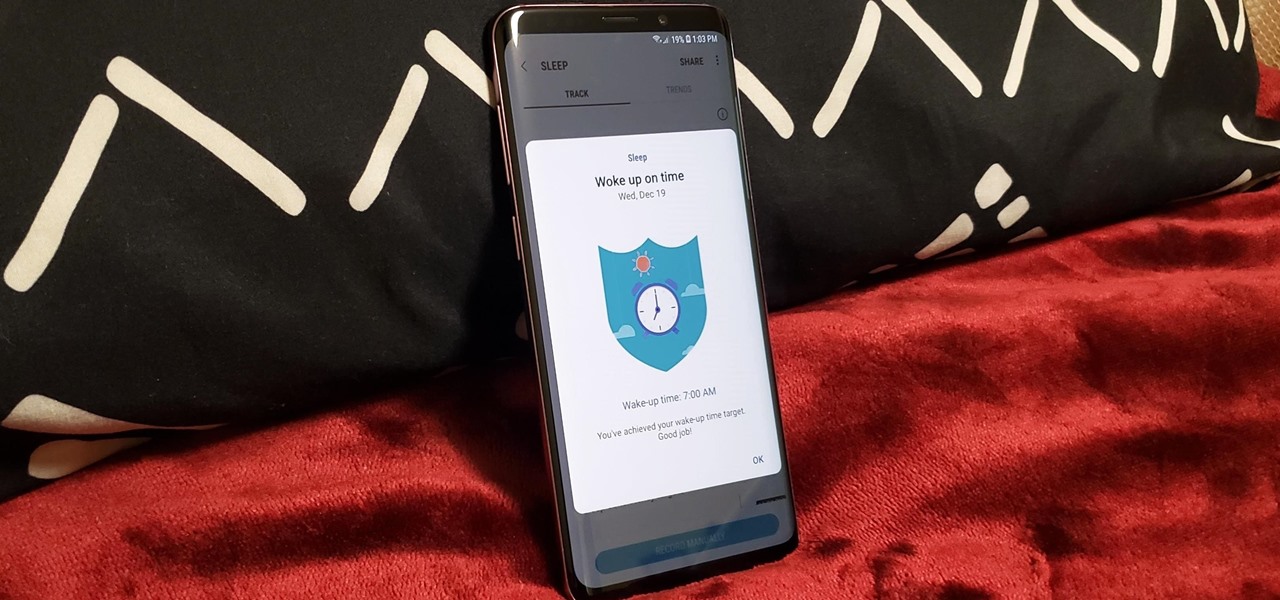
The quality and length of your sleep will almost always dictate how the rest of your day unfolds. Sleeping fewer hours increases your chances of spending the day in a tired and cranky state, while having a restful night's sleep contributes greatly to being alert and productive. Luckily, if you want to track your sleep patterns to figure out how you can improve your circadian rhythm, Samsung Health has you covered.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

In the wild world of Snapchat lenses, this week was an especially good one for cool effects. Lens-crafters (really hoping I can get that name to stick) have gotten a lot better at making non-gimmicky lenses that allow you to interact with them in new and unique ways.

While Magic Leap may have plans to eventually introduce sign language translation for smartglasses in the near future, students at New York University have demonstrated that such a feat is possible today with a smartphone and a prototype app.

Apple released the third developer beta for iOS 11.2.5 on Wednesday, Jan. 3, and public beta testers got in on the action the following day. The update comes two full weeks after the release of the second beta, marking an extended update period of Apple. The second beta mostly brought under the hood improvements to 11.2.5.

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

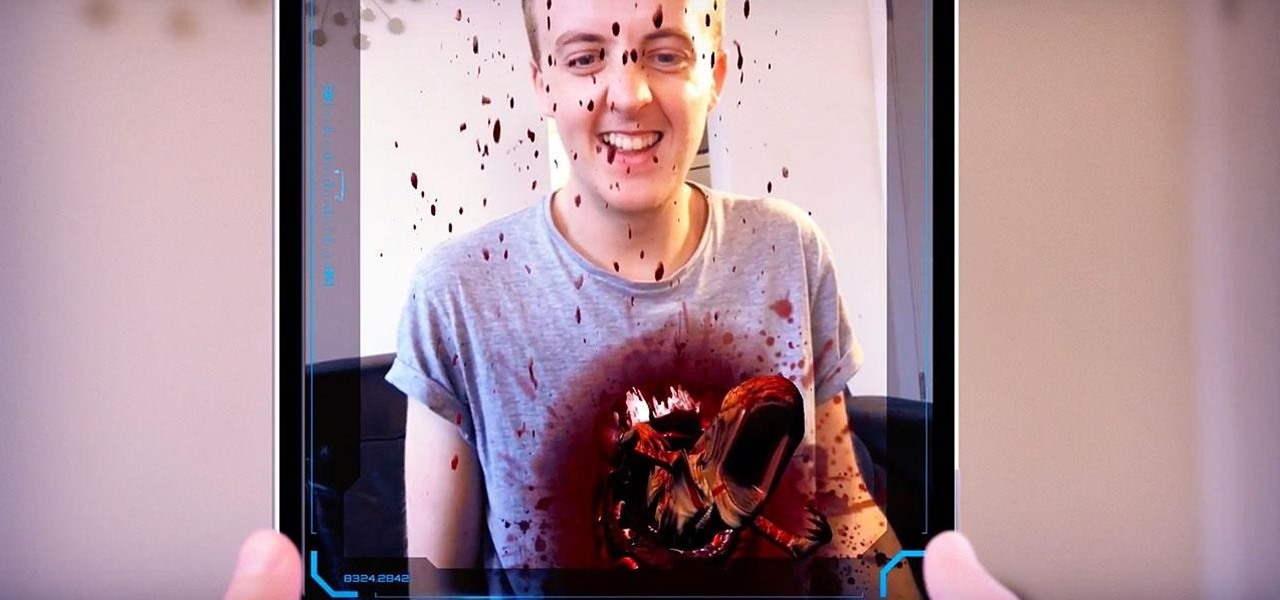
The latest installment in the Alien movie franchise, Alien: Covenant, came out many months ago, and the fan day dedicated to the franchise, Alien Day, April 26, is long past. But for many Alien fans, Alien Day is every day. For those loyal members of the xenomorph-worshipping tribe, a new augmented reality-powered book has arrived to serve their science fiction needs until the next film is released.

Ever since the planet went crazy trying to find augmented reality creatures in Pokémon GO, we've been waiting for the next virtual object game capable of delivering a similar hit. And now, we might finally have one coming, direct from the magical world of Harry Potter.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

In the SoundCloud app, when you find an awesome song, you can build off of it by creating one killer music station that will give you like-minded songs you might not have ever discovered otherwise. And finding cool new songs and artists isn't the only reason to create a SoundCloud station — it's a great opportunity to set the tone of your workday or your party without ever worrying about the music ending.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Say what you want about Samsung's TouchWiz UI being cluttered or overbearing, but one thing you can never complain about is a lack of features. In fact, it's been almost 8 months since I first took my Galaxy S6 Edge out of its box, but I'm still discovering features to this day.

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.

I don't know many meat eaters who don't appreciate a good burger, but unless you eat it plain, it usually gets pretty messy. Toppings falling off and sauce running down your arms seems like it's all just part of the process.
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

A continuation of my earlier science testing in Minecraft, I worked on a few things requested and retouched on TNT as there was suggestion of possible (and confirmed) altered circumstances.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

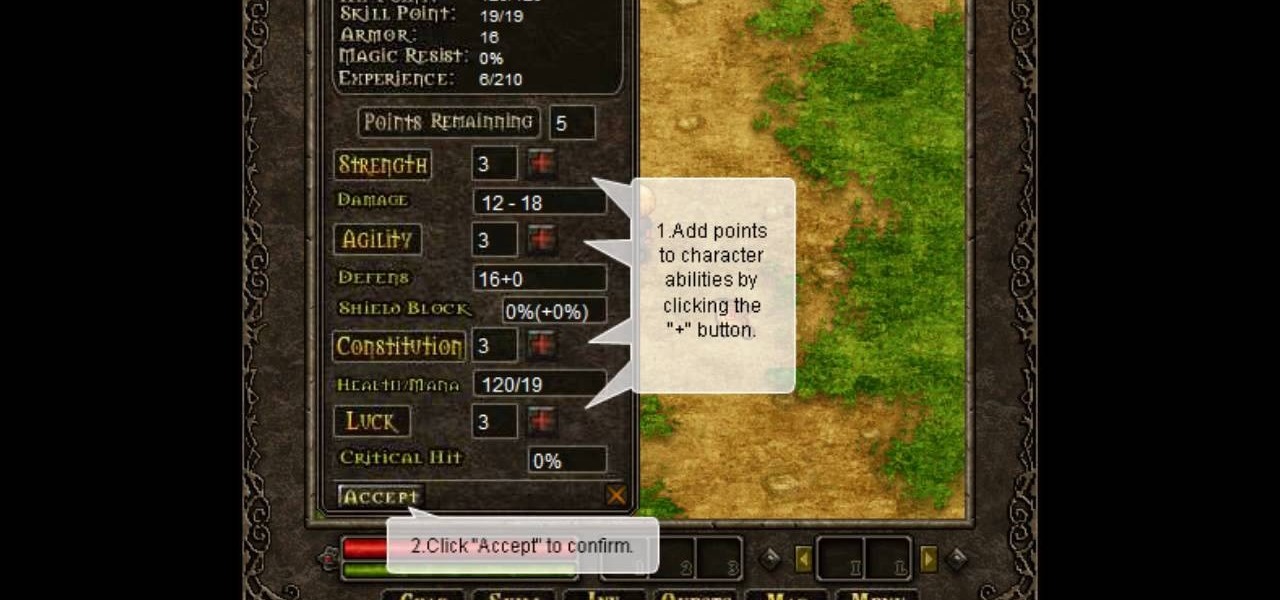
Want more gold? How about more skill points? You may need them in the game Acruz. But how do you get more, more, more? Well, with Cheat Engine, you can get more gold and skill points, with no real hassle.

ThreadBanger's Corinne visits with Luca of Lolibomb to learn how to make winter-inspired vegan beauty products in a DIY fashion. Way to save some money on gifts! In just fifteen minutes and a few easy steps, make an animal-friendly body butter for your best buds with these ingredients: cocoa butter, hazelnut oil, emulsifying wax, stearic acid, liquid glycerin, distilled water, and a vitamin E preservative of your choice. Add the body butter to a decorative jar and you have a great gift that m...

Do you remember "The Heist" from episode 21? Well, the sequel is even more unfair than the original! Check out this video if you want to stump people with a trick called "The Heist II." For this trick, you need only a few simple supplies: a match, a cup, and a nickel.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop the App Store on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

The V-Cube 6 puzzle is a uniquely designed and constructed skill game. V-Cube 6 is a multi-colored, multiple-layered cube, rotating smoothly on based axes. The player is required to discover a strategy to achieve uniform color sides on her or his V-Cube, but in this process, the Rubik's Cube-like puzzle may break, especially if you're in the process of speedsolving.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.