Before adding advanced yoga poses and twists to a yoga routine, make sure the postures are safe for your fitness level. Learn advanced yoga poses and twists from an instructor in this free yoga video.

In this video series, let Robert Wilkens help you fix accessory problems in your car. With his instruction on automotive wiring, you can learn how to replace fuses. Robert shows you how to install radios, speakers, and power windows too. He also teaches you how to put in a car alarm system. Most importantly, learn how you can keep yourself and your car safe as you work with automotive wiring systems. With these simple tips, you may be surprised with how much money you can save.

In these videos, you will learn some techniques for staying fit during the course of your pregnancy. You will see demonstrations of several exercises that you can perform from the first through the third trimester. You will learn how normal exercises such as the pushup, the squat and the crunch, can be adapted to fit the different stages of your pregnancy. In order to adapt normal callisthenic exercises to different stages of your pregnancy, our expert will show you different variations on tr...

In this how to video series, learn about swift water rescue and how to wade and swim through white water, from white water rescue technician Fergus Coffey. Fergus will teach you invaluable tips on swift water rescue and how to swim in and swim out of swift water. He will teach how to swim over a strainer, when it is safe to stand in white water, and how to avoid foot entrapment in swift water. Fergus will also teach and demonstrate how to safely enter white water, defensive swimming, aggressi...

In this video series, watch as expert river rafter Kevin McMillan teaches how to read rivers & safety tips for whitewater rafting. Learn how to organize a whitewater rafting trip, how to do paddle signals, different safety gear for whitewater rafting, how to read the river before rafting, how to swim in moving whitewater, how to pull someone in a raft, how to lean into obstacles, how to rescue rafters, how to bump a capsized raft to shore, and how to right a capsized raft. Whitewater rafting ...

In these rock and mountain climbing instructional videos, learn how to set anchors for lead and top rope climbing. Having strong anchor points is crucial to a safe and successful climb. Get professional tips and techniques on using strong rope knots to secure your climb. Learn how to rock climb with natural anchors like trees and boulders. Discover how to join anchors together for a more stable climb in unstable conditions. Watch this series and use these tricks on your next rock climbing trip.

Take a look at this video clip series and introduce yourself to the newest workout craze, The Vibe Disc! Our expert is one of the co-developers of this new piece of fitness equipment. He will take you through several of the dozens of workout possibilities of the disc and give you tips on how to get the most out of them. You'll learn how to stay safe while using the disc and ways to incorporate other equipment into the workout for conditioning for a specific sport. Check it out and have fun ge...

Curious about the basics of metal inert gas welding? Watch this instructional welding video for some vital safety tips. A shielding gas tank contains 3,000 psi of pressure, so keep your welding equipment safe distance from your high pressure tanks. To run a bead, you need to set your wire feed speed and your voltage in order to begin welding with an average angle iron. This video provides all of the preliminary steps to running a short bead.

A new software update for iPhone and iPad fixes a major Apple Books issue that upset users when iOS 16 and iPadOS 16 were first released last September. If you've fled Apple Books because of that blunder, it's safe to return.

With all of the hype around the new iPhone 13 series and new iPad and iPad mini unveiled this week, it would be easy to overlook a very critical update for the device you already have in your pocket.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

No, you didn't miss a beta. Apple just released the second public beta for iOS 13.6 today, Tuesday, June 9, three hours after the release of 13.6 dev beta 2. This update might come as a surprise to you, considering your iPhone might currently be running iOS 13.5.5 public beta 1. Indeed, this update is that version's successor, just with a major name change.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

While much of the world is currently in some form of quarantine due to the COVID-19 pandemic, augmented reality (AR) gives us all the opportunity to see virtual content while stuck in our homes.

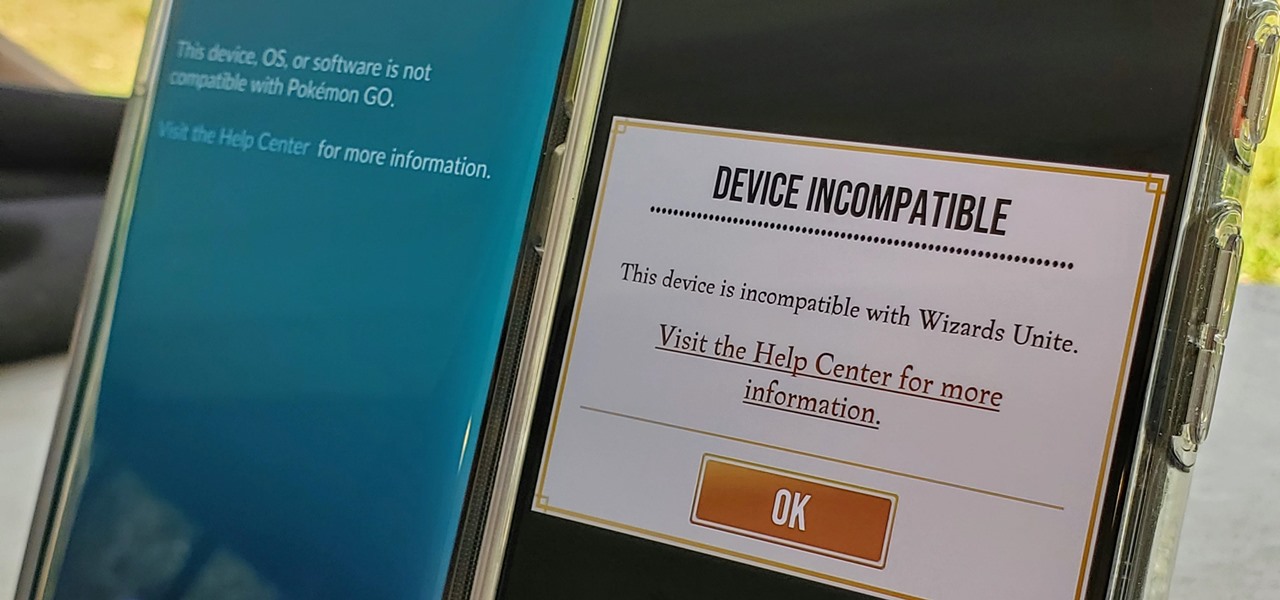
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

One of my favorite perks of this job is the opportunity to try out all the big flagship phones each year. Whether it's rating their suitability for a particular use-case or just entering their specs into our comparison tool, we have to get our hands on all major phones released in the US. We pride ourselves on being fair in our reviews and roundups, but that doesn't mean we don't have preferences.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

Despite their awkward appearance, Apple's AirPods have become the earbuds of choice for working out, largely thanks to quality audio without any wires to tangle. However, at $159 to start, they aren't exactly for everyone.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Hot on the heels of all the talk about Google's newest Android Q update, known as Android 10, there's a new beta to check out. OnePlus is one of the many partners that can now offer its users a chance to test the latest version early. That means you can install the newest Android Q beta right this second on your OnePlus 6, 6T, or 7 Pro just like Google's Pixel smartphones.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Apple's aiming to take over the TV world, and it shows in iOS 12.3. Nothing is going on yet with Apple TV+, Apple's video streaming platform with original content, which isn't supposed to come out until the fall. But there are some goodies in the new Apple TV app for iPhone that you should get to know.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

For lack of a better word, a missing iPhone sucks. Not only do you lose a physical device that cost you a small fortune, but there's also the probability you'll never see your precious data again. Hackers and thieves might, just not you. To keep this from ever happening, there are preventative measures you should take, and the sooner you do them the better.