How To: Upload simple and multiple files in ASP.Net
In this four-part video tutorial, Joe Stagner will demonstrate, using ASP.NET, uploading a single file from the client machine to your server.


In this four-part video tutorial, Joe Stagner will demonstrate, using ASP.NET, uploading a single file from the client machine to your server.

Most of us stay with a certain computer operating system - or a specific version of that system - because it gives us a great amount of ease. But what if you're using an older edition and it's starting to look a bit, well, outdated? Make your Windows Server 2003 look newer by installing the Windows XP Luna theme. You'll have to enable Themes to make this work. Check out this video for the tutorial.
Installing Joomla on a Windows server can be tricky, on Windows running IIS even more so. Installing Joomla 1.5 in this scenario has caused many frustrations.In this video, we take the process step by step and jump over the hurdles that cause some people to wind up pulling their hair out. If you follow along closely, you will be up and running in no time, and if you haven't already tried to do this, you will wonder why people find it so difficult. There are some prerequisites to the steps in ...
When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.
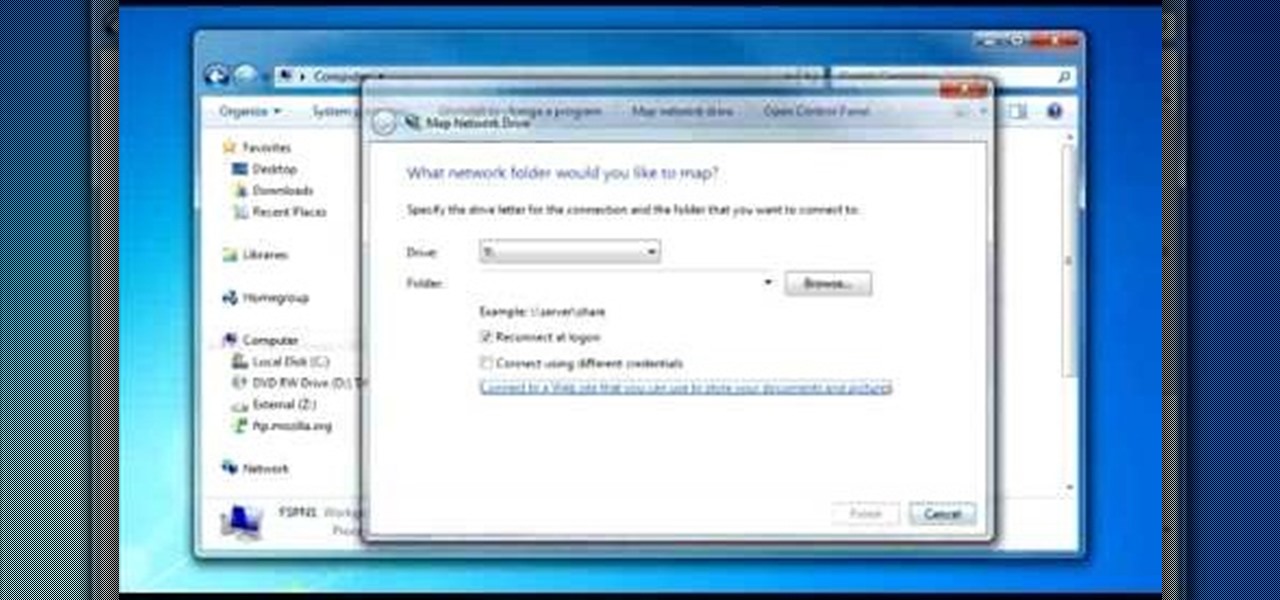
To do that click on tools in windows explorer and choose map network drive. Now click on "connect to a web site that you can use to store your documents and pictures" and then click on next and next. Now you have to type your internet or network address for example you type ftp://ftp.mozilla.org. This is a public server and it does not require a user name or password. Now click on next and there make sure you selected "log on anonymously" but if your server require a password then you have to...

This video by repairs universe shows viewers how to replace the battery in the 2nd Generation iPod Touch. The tools you will need for this project include safe-open pry tools and a small phillips head screwdriver. To begin, remove the screen by releasing several clips that hold it to the frame using the safe-open pry tool. Run the tool between the case and the glass along all edges. Gently pull glass off and pry off the digitizer. Next, remove the small screw in the upper corner, lift up the ...

This video takes us through a process of speeding up our internet connection using OpenDNS.com. Open the webpage and go to solutions and click on the icon open the DNS page and it lists computer or router, she selects computer and list of operating system is listed, she selects vista. She goes to start and selects control panel, click on view network status and connection, in that select view status and then click on properties and on the networking page, go to internet protocol version 4 and...

Safe motorcycle riding requires knowledge and skill. Testing two-wheel vehicle operators is the best measurement of the skills necessary to operate safely in traffic because people often overestimate their own abilities.

Home accidents. It's up to you to protect your family… your children… from accidents in the home. And there's one place that seems to get the most attention when dealing with safety concerns… The kitchen is one of the busiest, most accident-prone rooms in the house. Design a kitchen that will keep your family and guests safe.

In the early days of the internet, if something was there and not password protected, you could see it. In the process of becoming the indispensable work and entertainment resource that it is, the internet also grew the same borders that countries have while also getting less safe for the people using it. If you want to watch something, you have to hope it was available in your country. If you want to keep your information safe, you have to take some extra steps to make sure that happens. The...

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Last week, iOS 12 developer beta 7 was quickly pulled upon release, due to complaints of poor performance and instability issues. While Apple tackled these bugs with the release of developer beta 8 two days later, testers are seeing beta 7 again in their Software Update settings. Why is beta 7 back, and, more importantly, is it safe to download?

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.
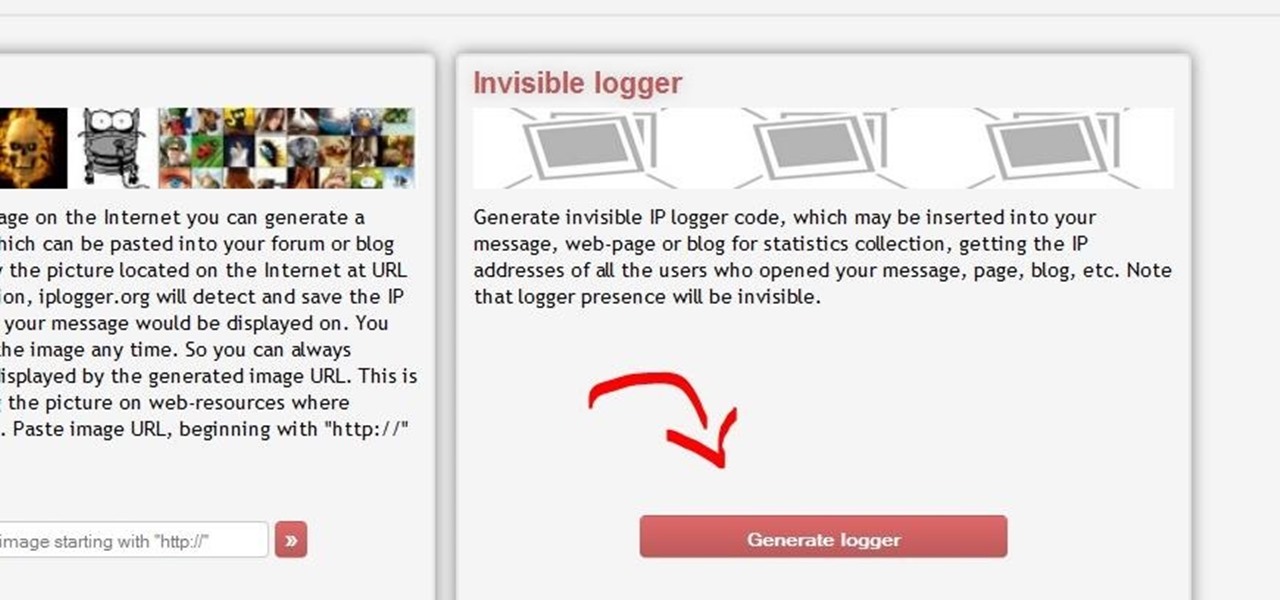
This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.
For those of you who have been taking full advantage of the jailbreak for iOS 8 that's available, you can understand and appreciate what this really offers iPhone users—sovereignty.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

In Minecraft, many people enjoy "Faction" aka "Raiding" multiplayer servers for their unique gameplay and survival aspect. Plus, it's always fun when you find a chest full of somebody else's free stuff.

Greasy bacon is so delicious, but when it's too delicious it can be soggy, a heart attack just waiting to happy, or merely not as good as a less greasy, more crispy taste. But what if you don't have an oven or stove? How do you make crispy bacon without the mess? The microwave. Yes, believe it or not. Make crispy bacon in your microwave in just a few minutes without the greasy mess.
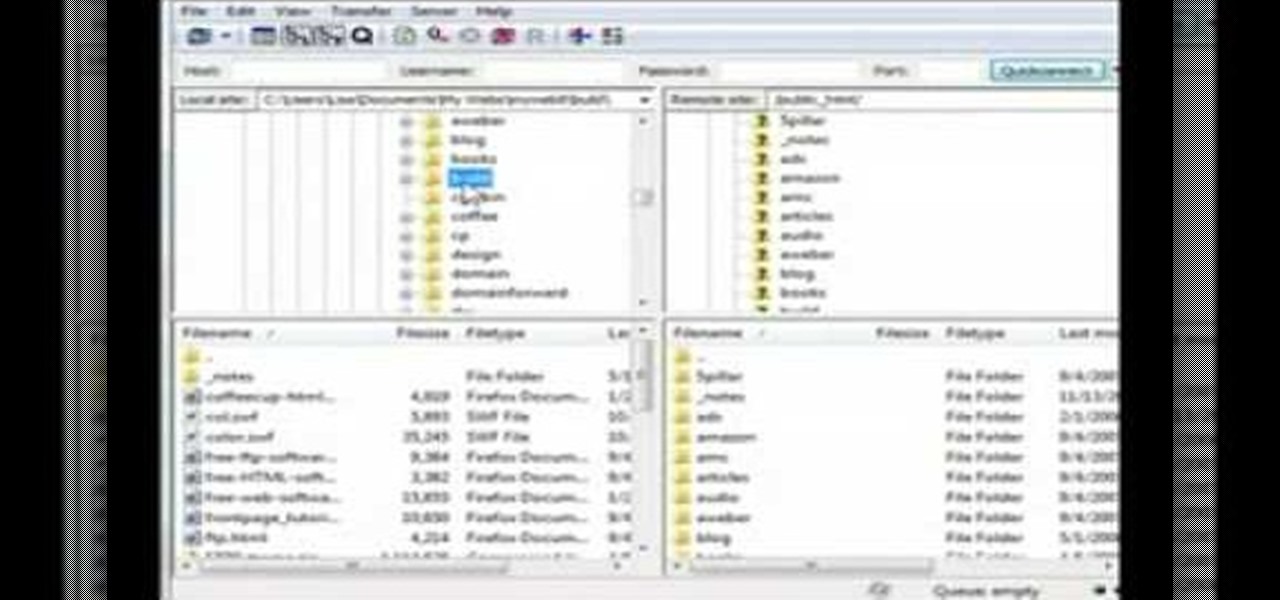
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.
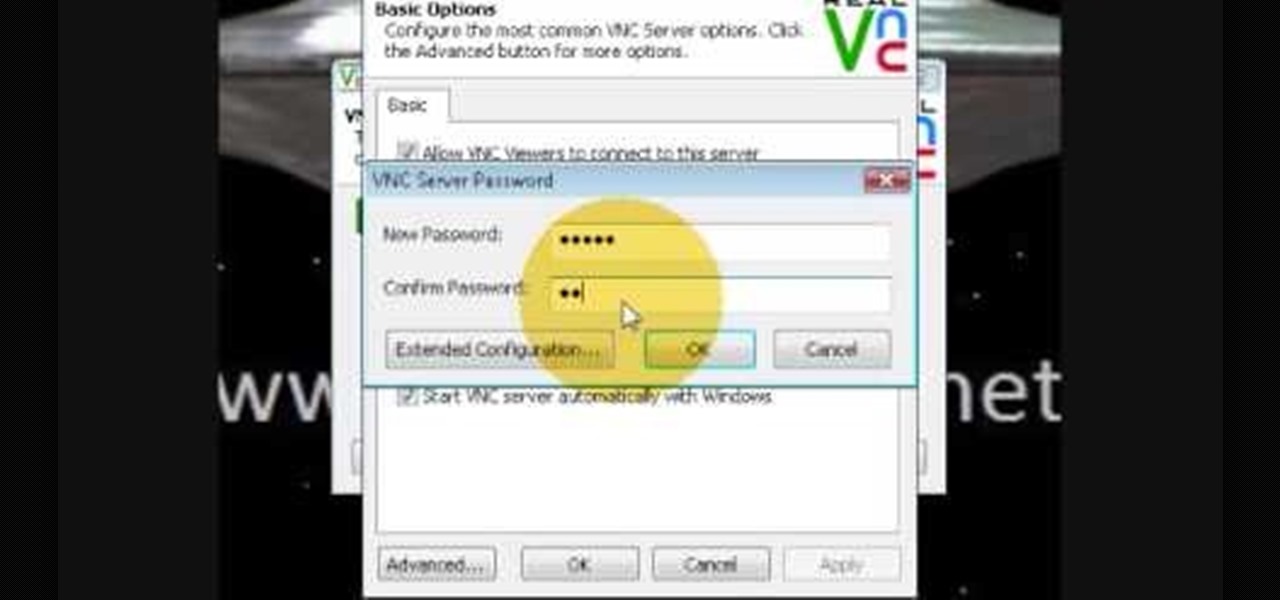
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...
Although Grand Theft Auto 4 was released, many people are still going to want to play GTA San Andreas. Here's how to download and install GTA San Andreas Multiplayer. First, go to Google and search GTA San Andreas Multiplayer. Then, click on the first result that comes up. Go to that website and click on one of the download links that shows up. (Either one of them is fine.) Open the file and follow the Setup Wizard. The installation process takes a very short time and is very easy. Then navig...

Contrary to what most people do, letting your dog stick it's head out the window is not a safe way of transporting your animal! Check out this video for some tips on how to safely travel with your dog.

Put yourself in the shoes of a burglar so you can anticipate where they'd look for your valuables. You Will Need

Learn when it’s appropriate to send your meal back in a restaurant, and how to do it without offending the chef.

Minecraft is such an incredible game that it allows players to create other games within their Minecraft servers. Here is one that is particularly fun. This is Blockey. Watch this video to learn how to build your own Blockey arena and get started playing.
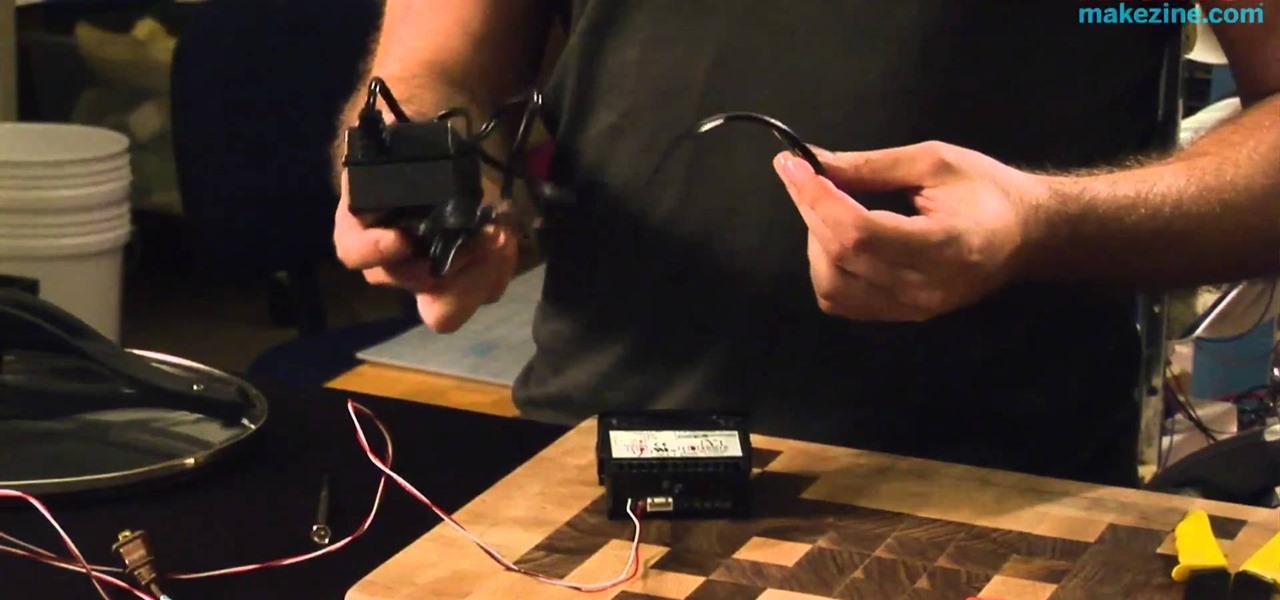
Sous vide, or ultra-low temperature poaching, is transformed into a safe and precise science when you create your own rig in this informative video from Cooking With Geeks entrepreneur Jeff Potter. The essential components of this cooking device are a slow cooker, a thermocouple and a temperature controller. Watch the video to see these components combine into a DiY sous vide rig.

This tutorial shows you a very basic method to create an effective boffer sword using PVC pipe, a foam noodle, duct tape and some open-cell foam for a stabbing-safe tip. You're also shown a good method for constructing the hilt. This is a great tutorial for anyone looking to make a foam sword for their favorite boffer larp!

If you have brown eyes then you know that colors like brown and gold are "safe" eyeshadow colors, meaning they look good no matter what (there's lots of brown and gold in our eyes, after all) and are neutral enough that you can wear them anywhere.

Hide your valuables in plain sight! This tutorial shows you how to take an empty can of whipped cream and then add a few discreet mods. When you're done, it'll still look like a can of whippped cream, but now there will be a way to hide your valuables!

Hide your money, small candies or other tiny items you want to keep hidden! Pry off the top of the battery, take out the innards and then rebuild the casing to re-camoflauge the battery. Then you're ready to hide your goodies!

The Salmonella eggs outbreak sweeping the nation is mammoth in scope, and if you want to keep yourself and your family safe you need to know what Salmonella is and how you can prevent it. This video will explain all of that to you, including the connection between Salmonella and dysentery and how you can prepare eggs to avoid contamination.

One achievement for you to earn in Starcraft 2: Wings of Liberty is the "My Precious" achievement, and you can get this in the Colonist mission of Save Haven. In order to obtain the achievement, you must successfully rescue two Colonist bases from the Protoss attack on HARD difficulty, i.e., destroy the Purifier while at least 2 Colony bases are left un-purified!
So you want to start your own website / blog / forum / web empire. Good, at least you aren't getting into financial services! This video will show you how to install three important programs that will help you get started: XAMPP, Wordpress, and MyBB. These programs will help you set up your web server, blog, and forum respectively, three important tool that you will need to use effectively to become a force on the web.
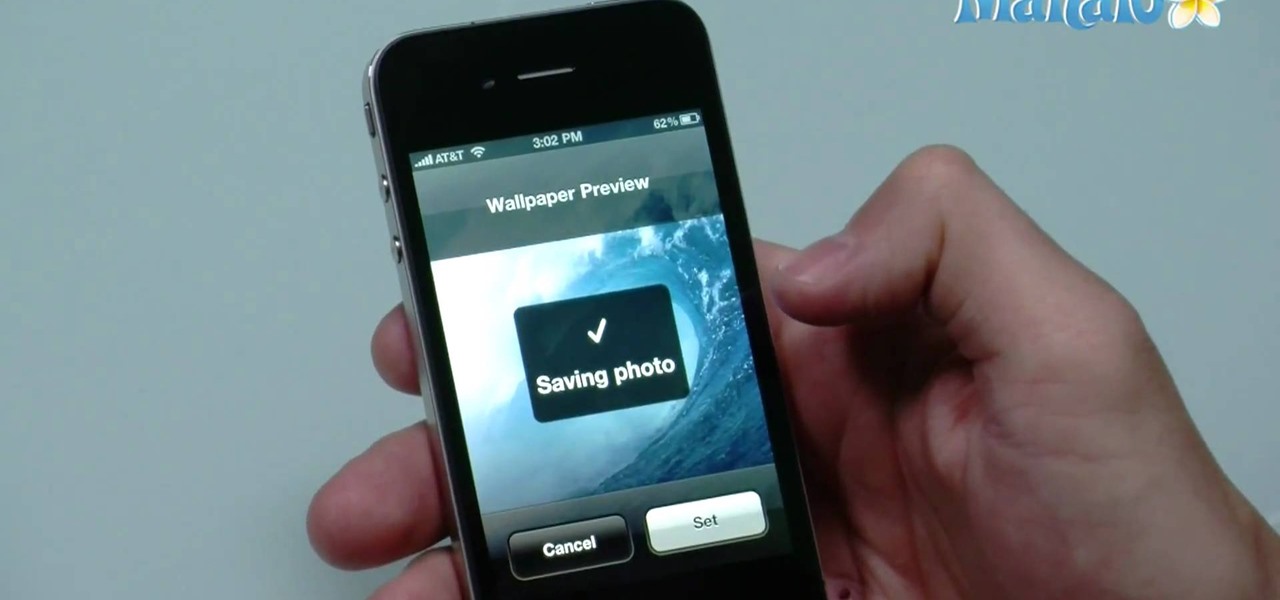
On the new iPhone 4 and in iOS 4 you are able to set a wallpaper as a background. In the past, wallpapers were only used on the lock screen and in this clip, you will see just how easy it is to set the old lock screen as well as the screen behind your app keys. This feature was only available on jailbroken devices in the past and now it is totally safe and made especially for you, by Apple.