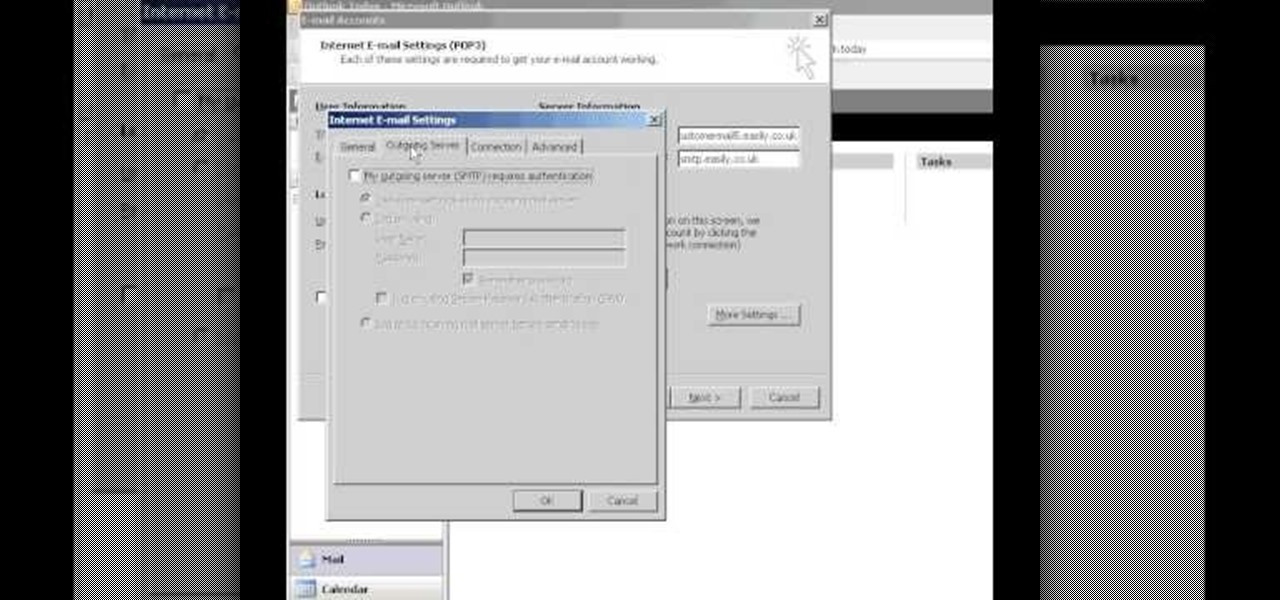
Easilycouk shows viewers how to set up an email account using MS Outlook. First, you should open up MS Outlook. Go to Tools and go to Email Accounts. Choose the option to add a new one. Click next and click the POP 3 option. Click next and Fill in your information such as name, the email address you are using and choose your log on information. Now, you need to fill in your Server information by copying and pasting your email into this. In the SMTP type smtp.easily. Go to internet email setti...

Go to web browser, click on tools- under tools click on 'Fire ftp.' Add an account to get into recall server. Under 'MANAGE ACCOUNTS' - click 'Add new one.' In host type 'Recall.(yourserver.)' then click on 'anonymous.' Click 'okay.' Now hit 'Connect.' the ftp server is then going to connect to your remote server. On right side you can see the remote server and it's file structure. Clicking on plus button (+) will expand the file tree structure. At this point you can see all the folders but y...

In this video the instructor shows how to map a network drive in Microsoft Windows XP. Network drive is similar to the disk drive that is present on your computer like C drive, D drive but instead of pointing to a hard disk on your computer it points to a server that has enabled shares. Shares allow you to create or edit files and folders. By mapping that server share to a folder in XP you can use that share as a normal drive. To do this go to start menu, right click on My Computer and select...

This instructional video shows you how to make a RSS ("Really Simple Syndication") feed using the free program RSS builder. RSS is a script that can be put up on a website that other users can subscribe to in order to get notified when the website gets updated. The xml code behind creating RSS feeds is explained. The code should be entered as shown and the file should be saved as "feed.xml" and upload it to a web server. Go to the URL mentioned, download and install RSS builder. Launch the pr...
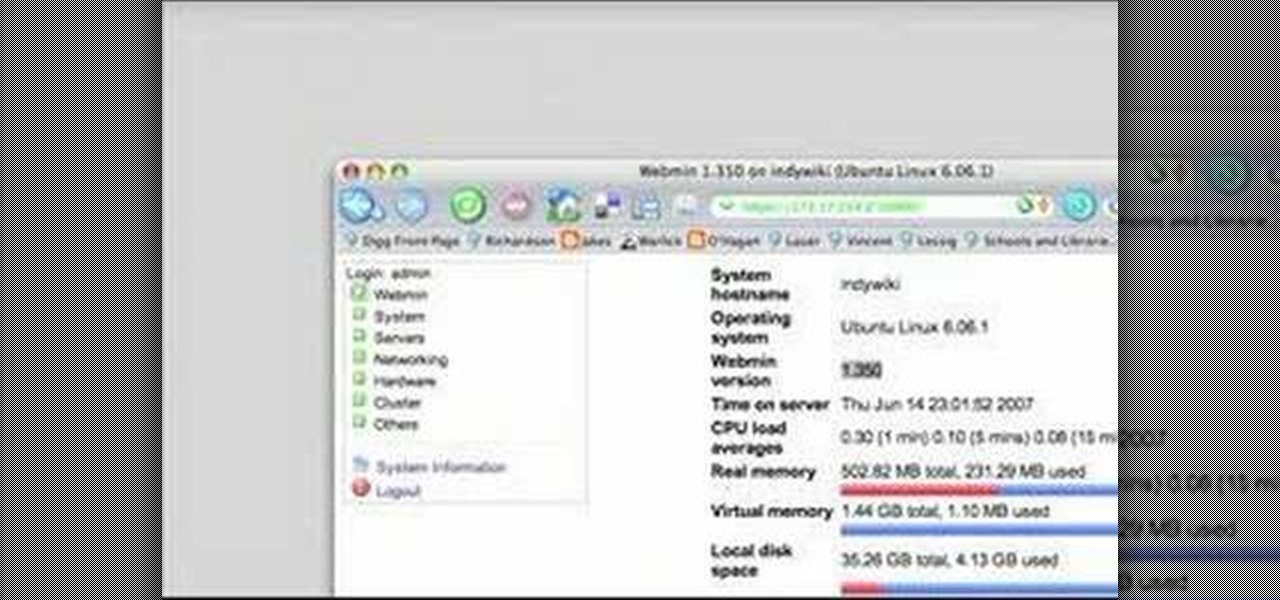
In this video you'll learn how to log in to Webmin, a web-based Unix administration interface, which will allow you to manage your serve with a web browser. Watch this video tutorial to learn how to control your server with a web browser and the Webmin interface.
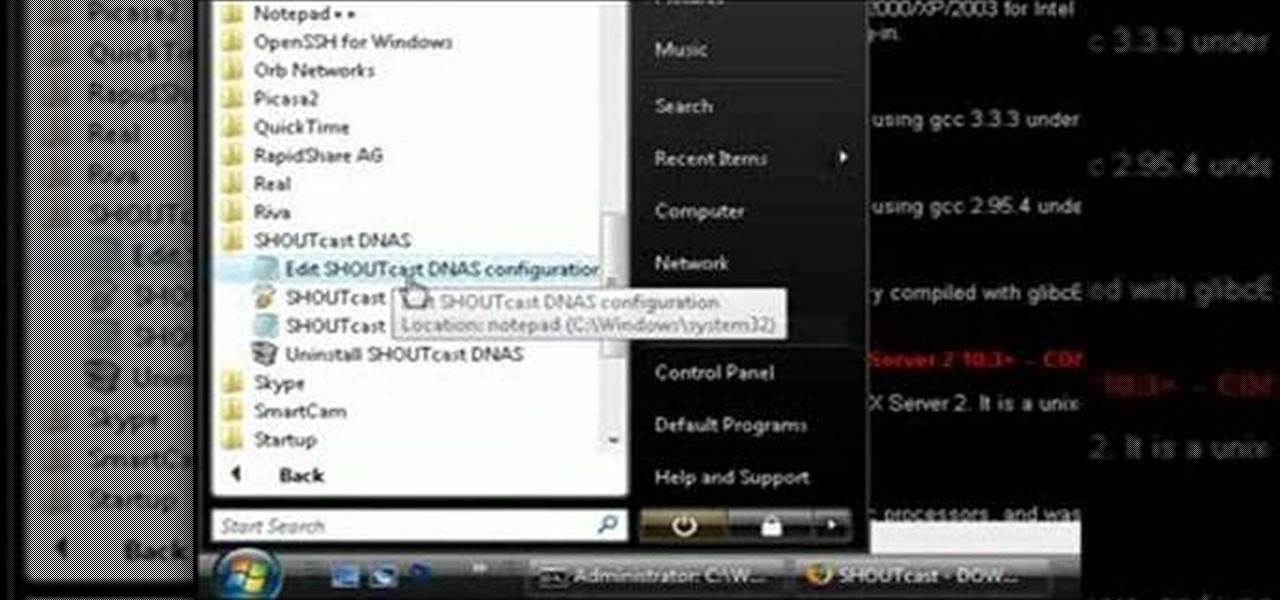
This tutorial shows you how to create your own radio station with streaming music using Winamp, SHOUTcast plugin, and SHOUTcast server. Learn how to choose your music in Winamp and upload it to your own radio station on the SHOUTcast server.

In this video tutorial, Chris Pels will show how to create event handlers for ASP.NET web pages and web server controls. First, learn how to create page level events for the standard page events provided by the .NET Framework. See how to automatically bind the events to a page using the AutoEventWireup attribute as well as programmatically bind the events. Next, learn how to create and bind event handlers for the standard web server control events. Also learn how to connect multiple events fo...

In this video tutorial, Chris Pels will show how to use a control adaptor to provide different renderings for an ASP.NET server control without actually changing the control itself. In this video, an ASP.NET BulletList control will be adapted to display each list item horizontally using div elements instead of the traditional ul elements. First, see how to create a class that inherits WebControlAdaptor and then implements the code to render the new list format. Next, learn how to map the new ...

Performing a software update using Yum, followed by loading and testing Apache Web Server.

If you're having trouble playing video files on your Playstation 3 from your media server this is a quick fix.

How to set up your Playstation 3's (PS3) media server.

A short tutorial on how to view server resources usage using cPanel. This video is provided to you by Scandicsoft.

Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.

This video shows you how to use the Free Internet Chess server and the BabasChess client for it. This video covers some basics, and hopefully some of you who haven't tried FICS will find it beneficial.

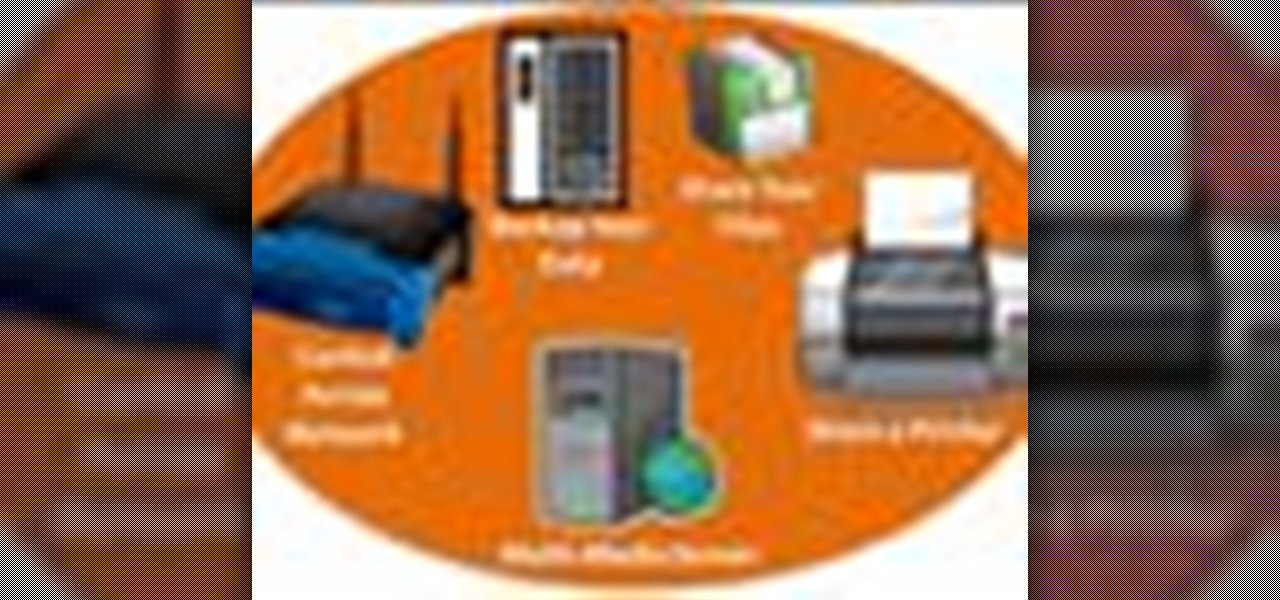
Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

This video talks about what SQL Server Reporting Services (SSRS) is and designed for the absolute beginner - someone who wants a high-level overview of Reporting Services.

Are you using the Internet at a school, library, or some other place that blocks or restricts web access? Mom and dad still trying to protect you from online predators, even though you're more than old enough to be one yourself? Learn how to bypass proxy servers that block access to certain websites by watching this how-to video. In this case it's done to access Myspace but this method can be used with any blocked website. Follow along with this video tutorial and never get hindered by restri...

Roofing is pretty dangerous work, maybe one of the most dangerous is residential construction. But if you're following all of the necessary safety guidelines, the chances of getting injured on the worksite are minimal. Working safe doesn't take long, and you don't have to sacrifice safety to do quality work and make a profit.

Dave and Pat break down the basics of RFID technology and show you how to put it to use by building an RFID beer safe!

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.
Hello, I'm a new guy around here and since I'm not seeing much tutorials in C i thought of contributing with something relatively simple. This will be a short series.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

OK, In my last Tutorial we made a Server for sending Instructions to a Client. This time we will build the Client. Fire up your favourite Python environment and get the Code here.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Defeat the Templars in Mission 8 on the Sony PSP and stop the attacks on the safe house. Altair doesn't really catch a break, although the Safe House assault squad comprises only six Templars. Slay them all. For more info, watch the whole gameplay.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.