
How To: Set up external network access
The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.


The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.
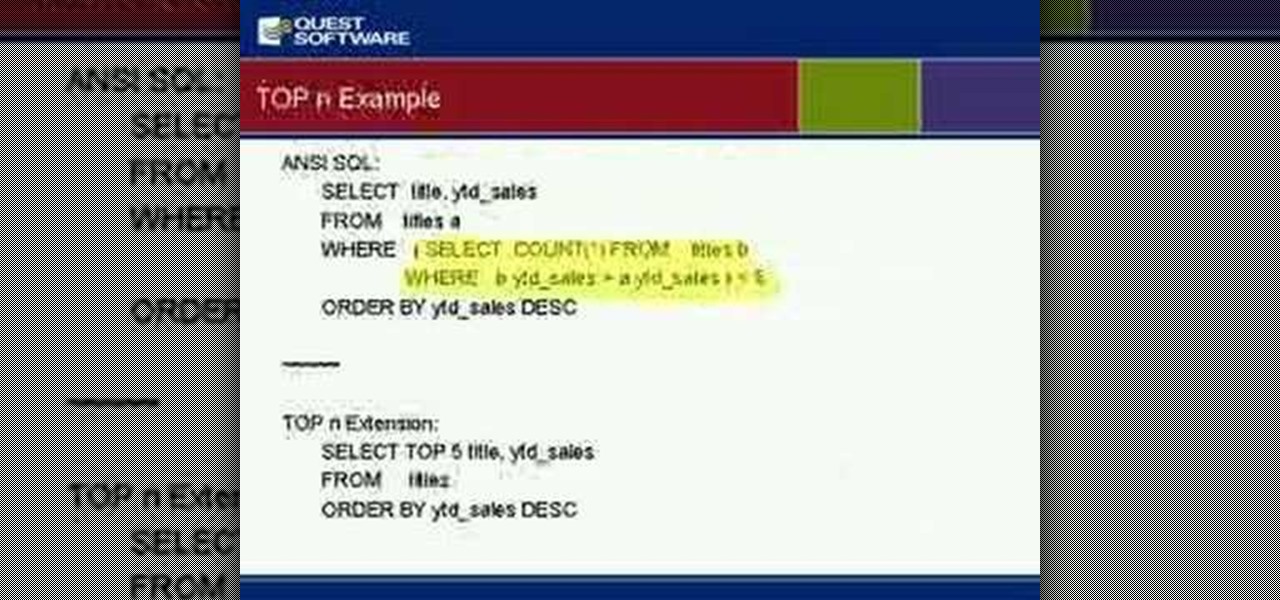
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

Django is a Python web framework used for rapid application development in any environment. In under 10 minutes, you can go from a bare Linux (Ubuntu) installation to a fully functional Django server.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Cycling accidents are more common than you think. In the past month, two men have been hit and killed while cycling in New York City. I even saw a cycling accident occur yesterday morning here in NYC. It's dangerous enough to be cycling in populated areas, it's made worse by people wanting to text while riding.
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Hey guys, today I bring you the fabulous BronzeSMP Server series! I hope you guys will enjoy this video as much as I enjoyed making it!
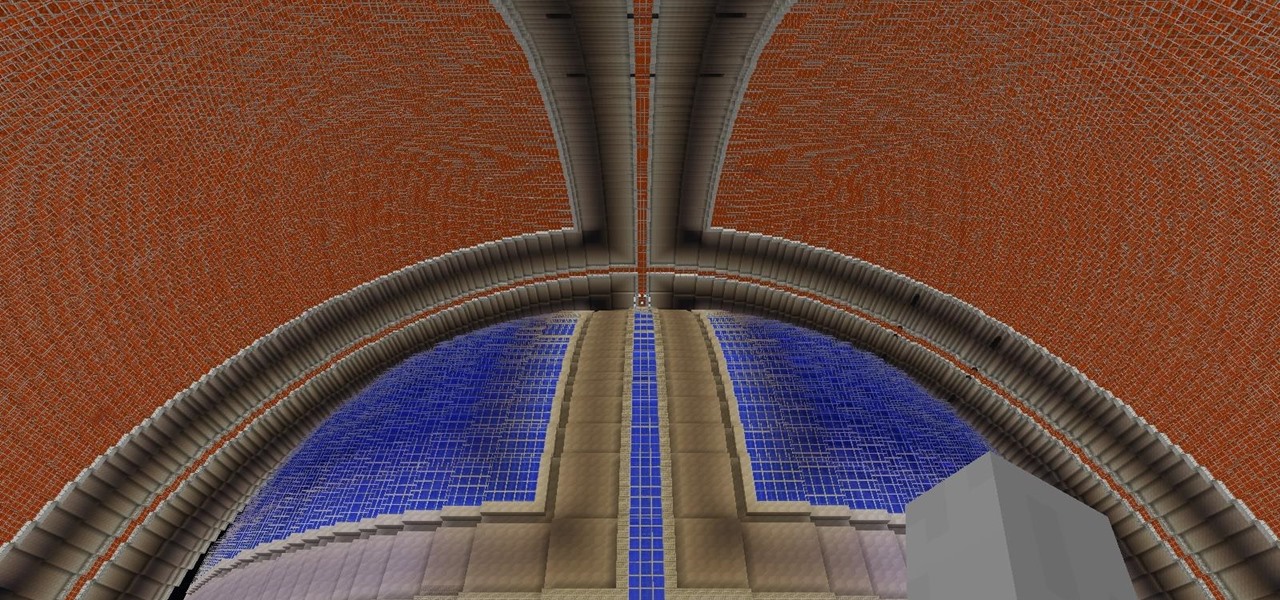
Still working on mega project builds. This one is going into my own PVP server which (will) contain 4 theme'd biomes inside of a 155m sphere - inside of a 255 meter containment sphere inside a 1000m+ void. The outer sphere acts as both artificial sunlight and a drop-death height of 50m. 4 more outer panels to go (water and lava) and it's ready for interior work and redstone - including command-block powered proximity traps that don't have any triggers marking them as well as hidden walls that...

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Having all of your stuff in the cloud is super convenient if you want to access it on multiple devices, or if you want a backup in case it gets lost or wiped. The biggest downside with services like Dropbox, though, is security. With everything sitting there in one place, the last thing you want is for someone to break in.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Use PubSubHubbub
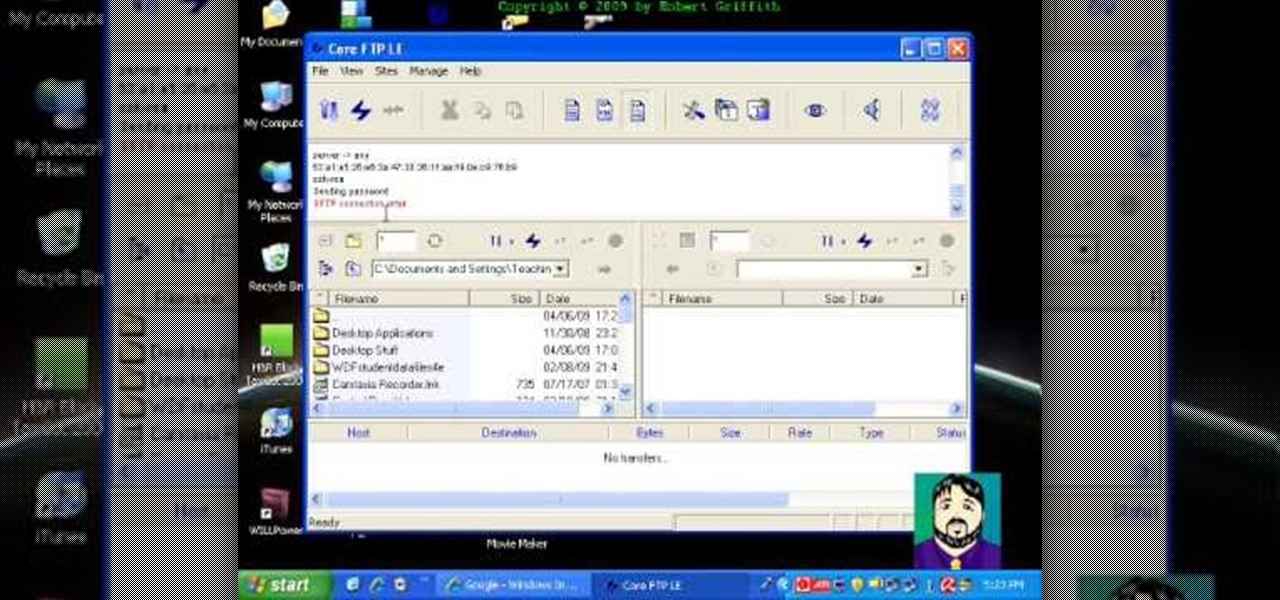
Select an FTP client that allows you to connect to the webserver. Download a free Core FTP Le software. Install the program. Use the site manager to name the internet site. Create a host/url, a user name, password and a connection. Connect to the web server. Create an index file to make files viewable. Open the Core FTP LE software. Drag files from the desktop (left side of the dialog box) to the internet server (right side of the dialog box.)

If you've ever wanted to take your dancing to the next level with a girl at a club (i.e. if you've ever wanted to start grinding pronto), then you know how frustrating it can be. If you move to fast to grinding the girl, she'll get freaked out and think you're a pervert. But if you take your time and only dance with her from a safe distance, she'll star to become disinterested and think that you are too.

This is a video tutorial that is showing its audience how to replace the digitizer screen on a 2nd generation Ipod Touch. The first step is to remove the screen from the Ipod touch. Secondly use a safe pry tool and run it between the backing of the screen and the glass, this will release the necessary clips that are holding your screen in place. Next take the screen off. Next separate the digitizer from the mid section with the safe open pry tool again. Pry apart the digitizer and the mid sec...
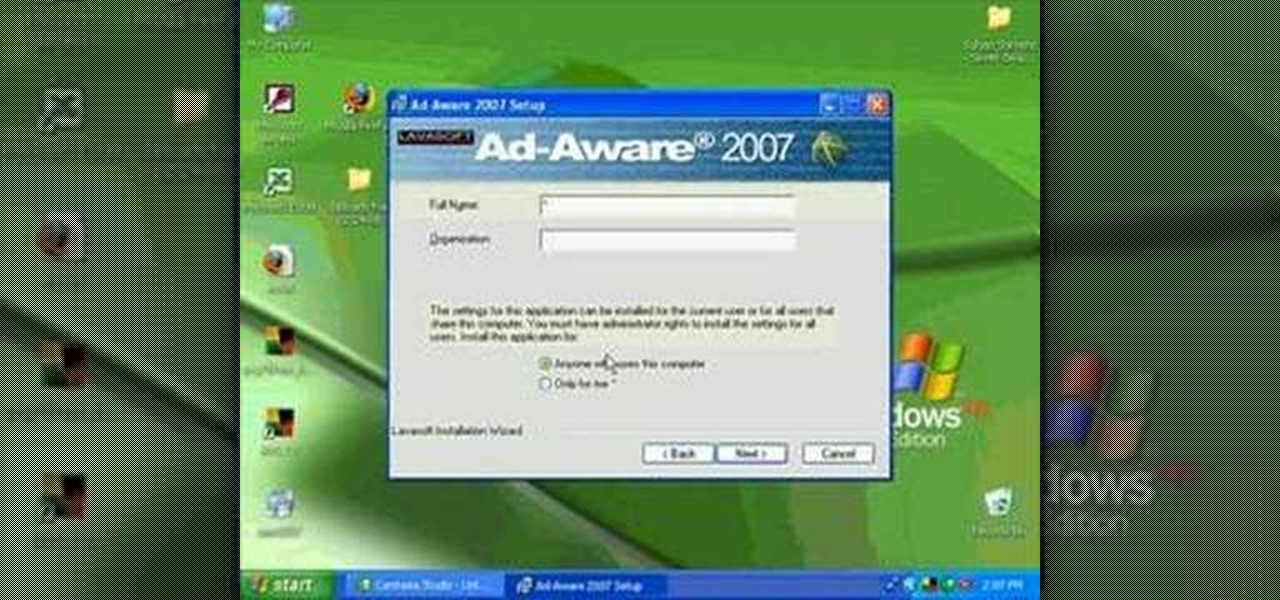
This is a Computers & Programming video tutorial where you will learn how to remove annoying spyware on your PC in Windows XP. Some spyware can be really nasty. This video shows how to remove spyware for free. Go to Download.com, and search for ‘ad aware’, download and install it. This video recommends Ad-Aware. While installing, select safe mode of scanning, otherwise some spyware may not be detected. Then, you need to update the definitions. Keep the definitions updated regularly. After upd...

Did you know that rabbits can be litter-trained? Having a properly trained bunny means less mess and stress for you—and the bonus for your bunny is that she’ll get more freedom around the house.
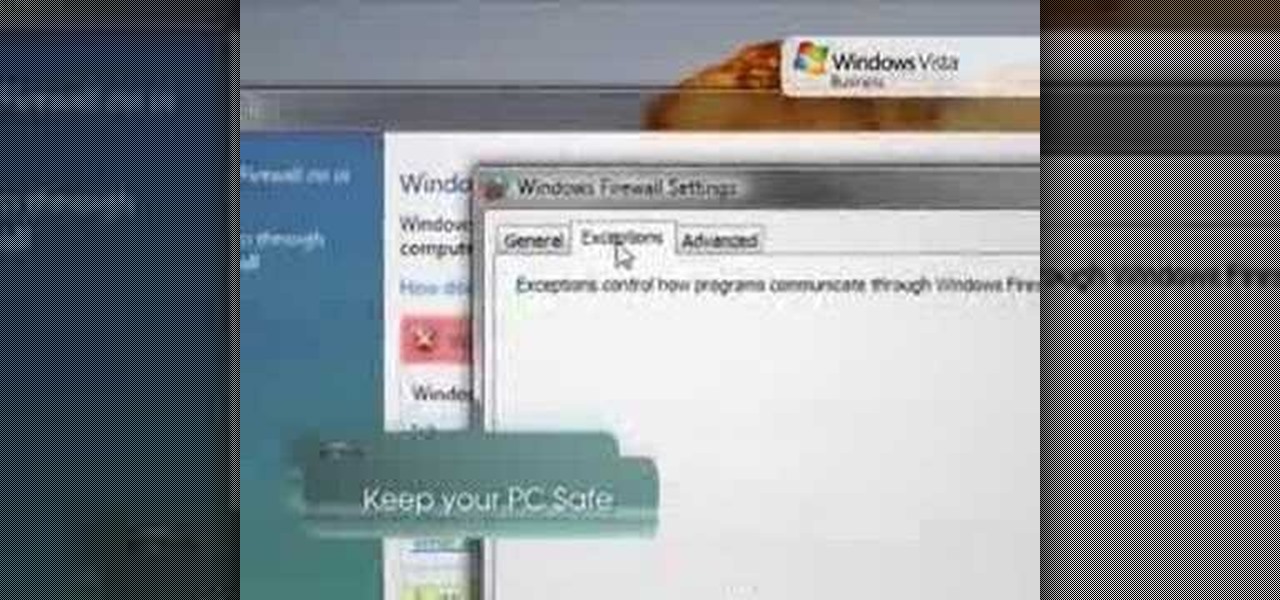
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

If you're headed through the firey hell region of Dark Souls, you may encounter the Ceaseless Discharge boss when you pick up the item in the corner. If you want to defeat the boss, take a look at this guide from IGN on utilizing a safe spot.

Minecraft 1.8 has introduced Enderman to tons of blocky servers all over the world. If you're looking for ways to fight against Enderman or just avoid Enderman all together, take a look at this walkthrough on how to do both. Be sure to grab an Ender Pearl so that you can half their attack range!

Find which airlines Google is providing free Wi-Fi on this holiday season, fix shutter lag on digital cameras, wipe your hard drive for free, improve your Wi-Fi router performance, adjust your television and monitor for accuracy, choose the best 1080p projector, use a single server that can handle OS X, Windows & Linux simultaneously, and use the best audio encoding system for Windows Media Center and Zune.

Electroluminescent devices need electricity to light up, clearly, so if you're working on an EL project building a proper power supply is crucial. In this video you'll learn how to make a DIY power supply for your EL projects that is safe, effective, and cheap.

If you're trying to get a triangle on someone in an MMA or jiu jitzu fight and they hide their arm to try and relieve the pressure on their neck, they might think they are safe. They aren't. Watch this video to learn how to finish the triangle in this situation from Joanne and Hillary Williams of MMA Girls.

Babies are pretty adorable, but the many disgusting fluids they intake and excrete make cleaning up after them a nightmare. If you're a new parent, watch this video. It will show you how to use all sorts of cleaning products to clean up different kinds of baby stains, from drool to baby formula to "mystery stains".

Bubbles are usually soft, airy, safe things. Not when they're on fire they're not! This video will show you how to create burning bubbles using only condensed air dust remover, water, and soap. You may have seen this done in science class with gas from a Bunsen burner, but this requires much less elaborate equipment and can be done nearly anywhere! FIRE!

The human body is full of different kinds of fluids, most of which are either gross or dangerous to remove from a person for use in one of your films. Fortunately, most of them are pretty easy to replicate using household materials. This video will show you how to make edible prop fake blood, feces, vomit, and snot. They all look great, are safe, and will make you movie much more realistic.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.

This video is dedicated to the residential construction workforce and focuses on how to safely install siding. It's intent is to help provide employees and employers with the tools to make the residential workplace productive and safe. It outlines a number of code requirements and will show how to work safely and how to meet all of the safety requirements during the siding phase of residential construction. The areas discussed in this safety video are job preparation, walk-around safety inspe...
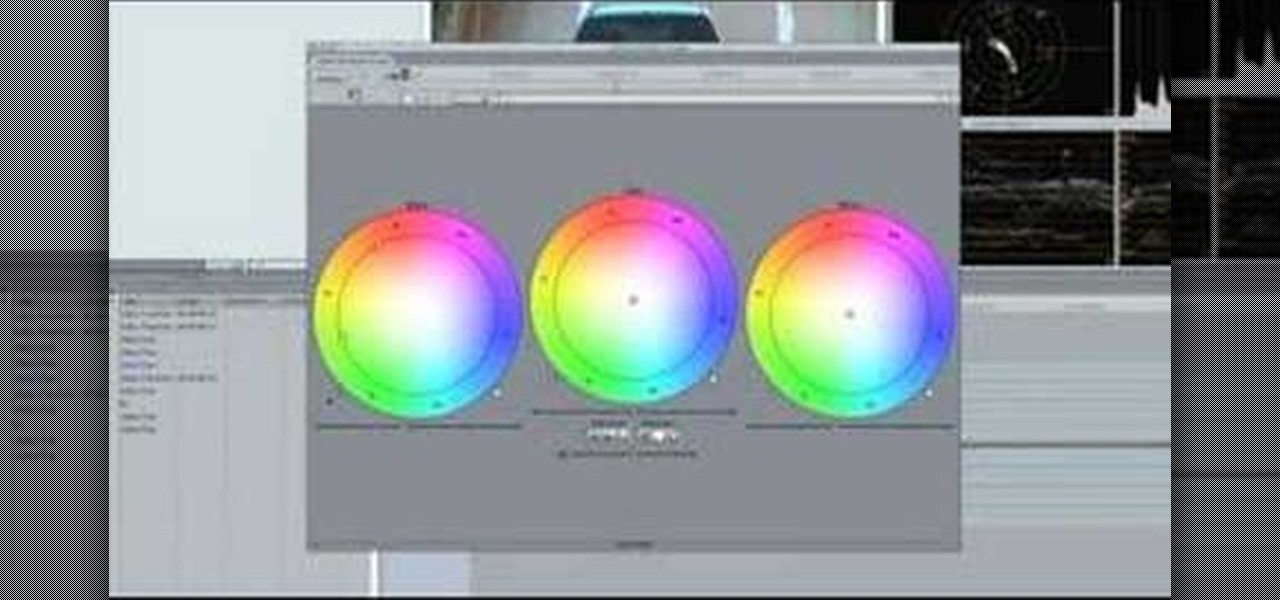
Make sure your video projects are broadcast safe with color correction and the Waveform Monitor in Apple's Final Cut Pro. This free video tutorial presents a complete overview of how to use the Waveform Editor and FCP color correction tools for increased darker blacks and whiter whites while staying with broadcast specifications.
Want to play your video collection on any media extender, console or AppleTV? Step one is to get your movies off of the DVDs and onto your hard drive! If you're like most people you probably have a huge library of DVDs that you've bought and collected over the years. Unfortunately, it's an inconvenient format if you want to playback all that content anywhere around the house. So, learn how to rip and encode that stack of DVDs into a format that you can play on your Windows Media Extender, set...

Car accidents are the leading cause of death of children in the United States. Follow the guidelines in this how-to video to give your child a safe ride. All you'll need is the kid's new car seat and the owner's manual to your vehicle. Proper installation is key, so check out this instructional video to learn where and how to put that car seat in safely and correctly.