One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.
Features like themes and a tab queue make Firefox an extremely versatile mobile browser. Mozilla is constantly adding bonus functionality like this to Firefox, but a long-time staple is perhaps the most powerful feature: Extensions. This system gives you the ability to add features without having to upgrade the entire app.

Unscheduled pit stops go hand in hand with road trips, no matter how well-planned they are. In the past, making a stop due to low fuel or an emergency bathroom break may have snowballed into massive delays when you went off course on your own, but thanks to a feature in Apple Maps, you can do this in the most efficient manner possible.
When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

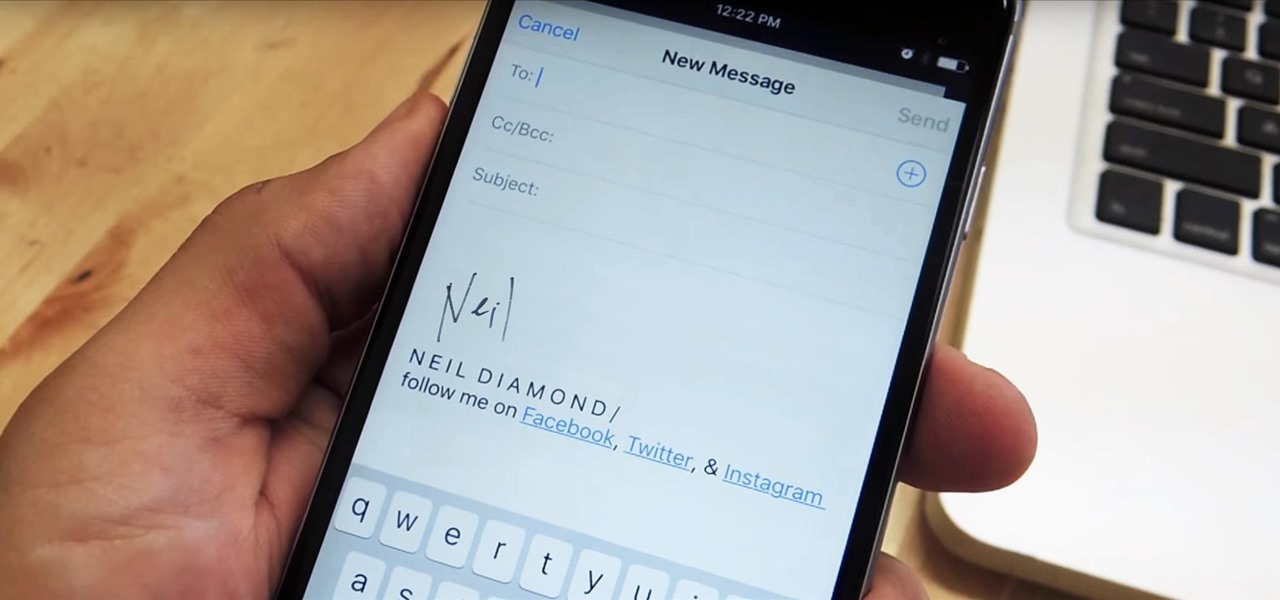
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

If you are among those lucky ones who got a chance to pickup the Yu Yureka from Amazon and looking for a detailed guide on how to root your yureka, then I doubt that there is any better place than this. You might have visited some XDA threads for the same but those are generally brief explanations and you might miss something or the other. Moreover, in most of them, ported Clockworkmod recovery has been used which is less stable and lacks features. So keeping your worries aside, look nowhere ...

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Android Lollipop's new Material Design interface does its best to strike a delicate balance between intuitiveness, usability, and aesthetics. For some folks, though, the use of a lighter color palette throughout the interface disrupts this balance.

We've previously shown you how to get your Samsung Galaxy S4 looking more like its successor by installing the revamped S Voice app and the new Quick Settings. Now, we're taking it a step further by giving you the Galaxy S5's stock Settings app. After this mod, it'll be pretty hard for others to distinguish your GS4 from a GS5.

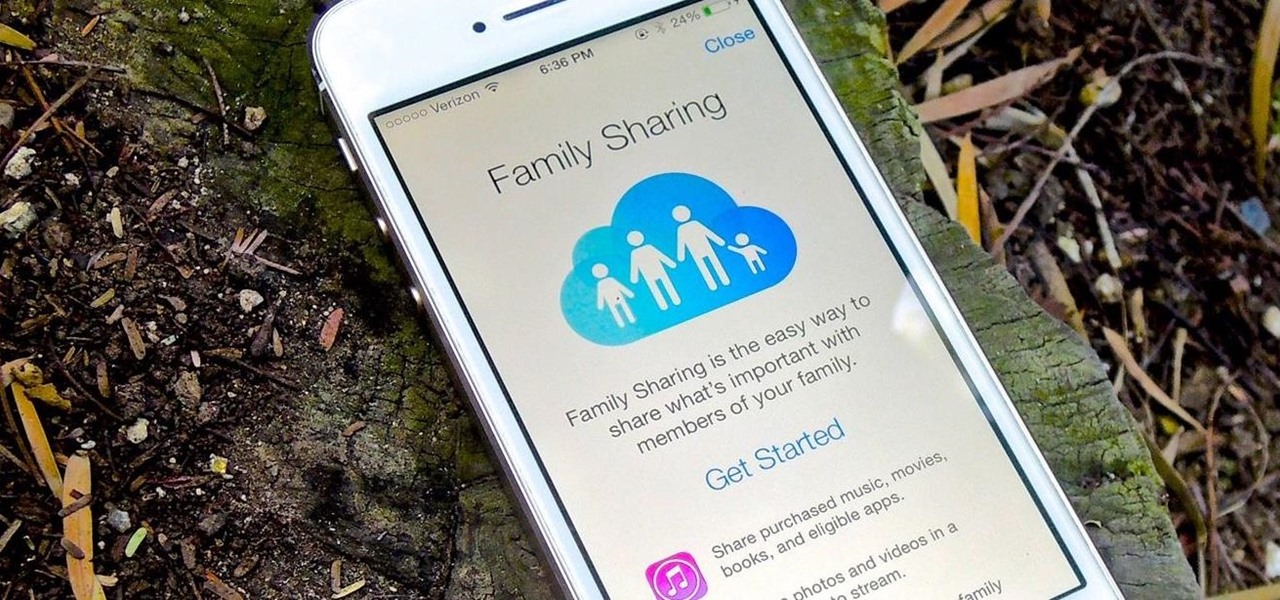
There are a ton of great new features in iOS 8, and one of the most interesting (and perplexing) ones is called "Family Sharing."

Have you ever looked down to your phone and said "This GPS app works well, but why isn't it cuter?" Well, you're in luck! Tokyo's Sunrise Aquarium has what might be the cutest way to navigate to their facility—just follow the penguins!

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

The Galaxy S5 is a flagship-level device with some pretty advanced features, like its 4K video recording capability, water-resistant casing, fingerprint sensor, and KitKat running out of the gate.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

I'm all about safety in my life. I even put on safety goggles when someone opens a bottle of champagne—high life problems. But when it comes to driving, you have to be double safe, because the other drivers on the road may not have your safety in mind.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

Aside from being completely adorable, Fijibot is a completely autonomous robot that automatically seeks out light sources to charge his solar-powered battery. He's built from a 1.5 liter Fiji water bottle, packed with an Arduino Uno, 6 volt solar panel, and an Arduino Proto Shield. His other parts are all off-the-shelf gear you could grab at RadioShack, while the wheels are from a discarded RC car. Fijibot isn't a particularly useful robot, but it's still fun to watch him navigate from light ...

Linux is generally a pretty stable OS, but occasionally things happen. However, as long as your keyboard has a SysRq key, you'll never need to worry about freezes again.

When driving, you can get directions hands-free by asking Siri. You can also make general map searches, show a location's details, call a query's phone number, and view traffic details. However, Siri defaults to Apple Maps for all those. If you prefer Google Maps, Waze, or another third-party navigation app, the map-based Siri commands won't work. But that doesn't mean you can't still use Siri.

Fans attending the US Open Tennis Championships in Queens, New York, which kicks off on Monday, will have the opportunity to meet tennis star Venus Williams in an augmented reality game sponsored by American Express.

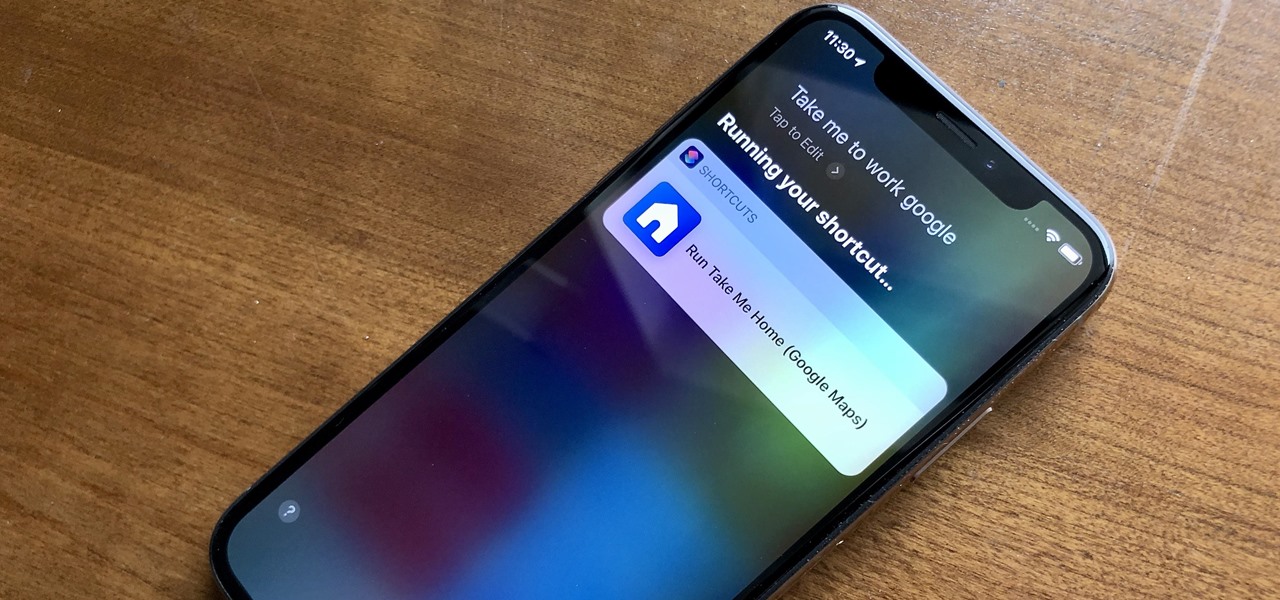
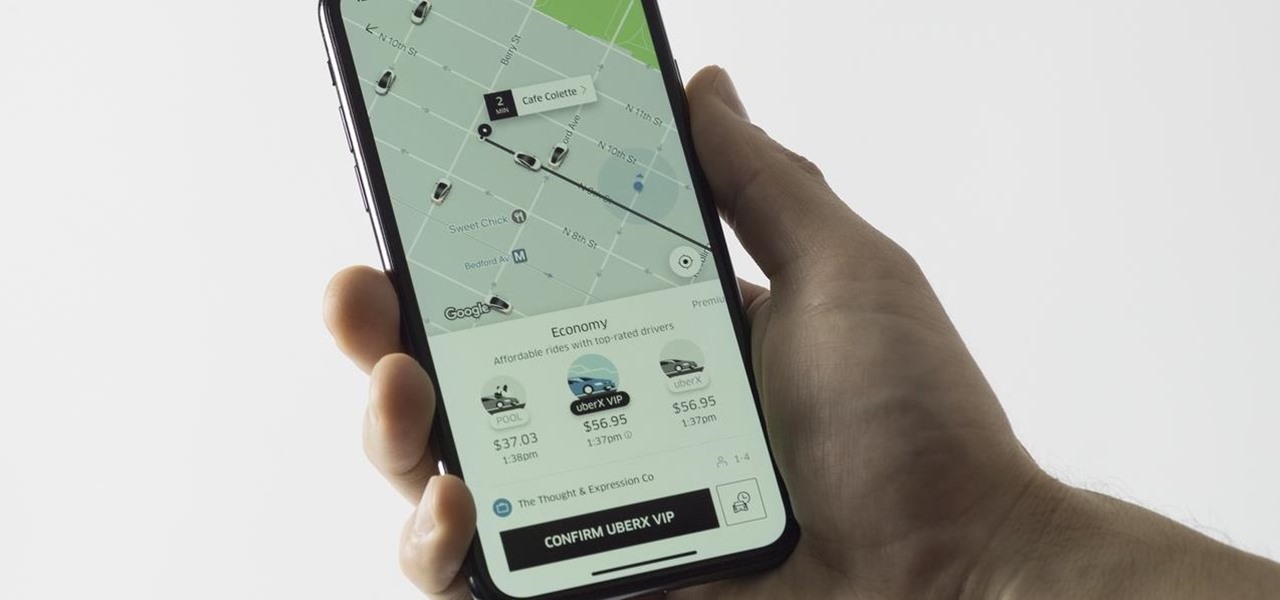
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

If navigating a new city for a sporting event, such as the upcoming Super Bowl LII in Minneapolis, Minnesota, is a daunting task, then making your way through a foreign country to a series of venues may seem like an impossible mission.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

Xiaomi phones run a skinned version of Android known as MIUI, which, over the years, has been a popular custom ROM. One of the standout features Xiaomi has added to the mix is something called Quick Ball, which lets you navigate your phone by swiping inward from a small circle that resides on the edge of your screen.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

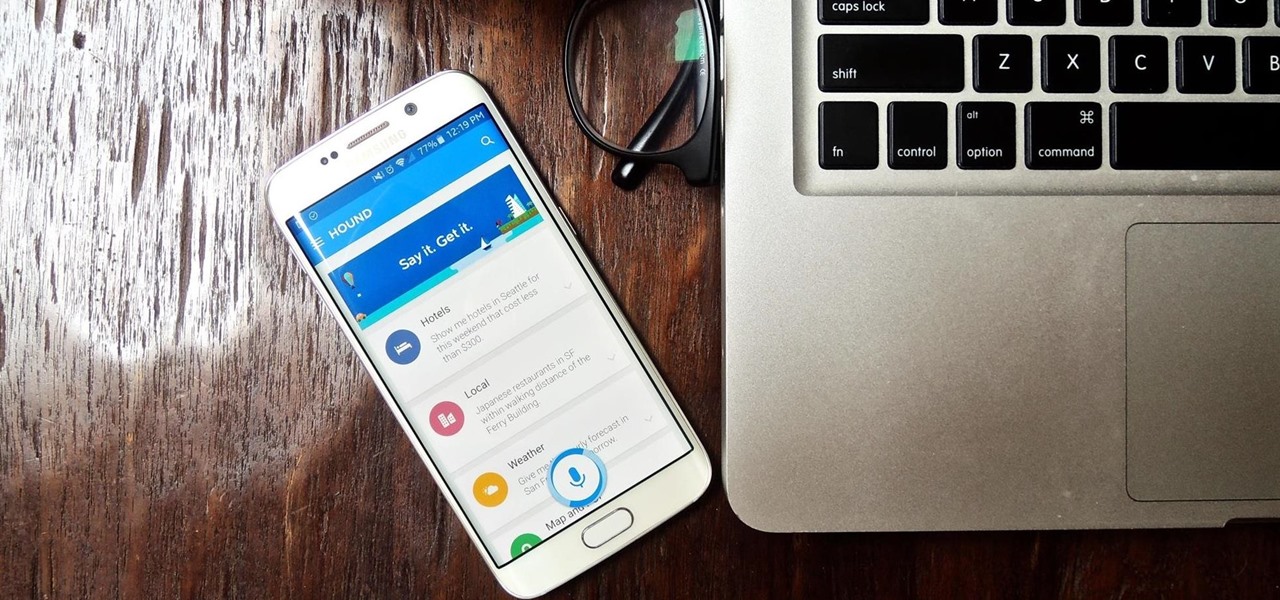
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).

Since the days of Android Jelly Bean, Samsung has implemented an energy preservation feature known as dynamic voltage and frequency scaling, or DVFS for short. What this essentially does is limit or adjust the frequency of the microprocessor to conserve power and prevent excessive heat from being generated.

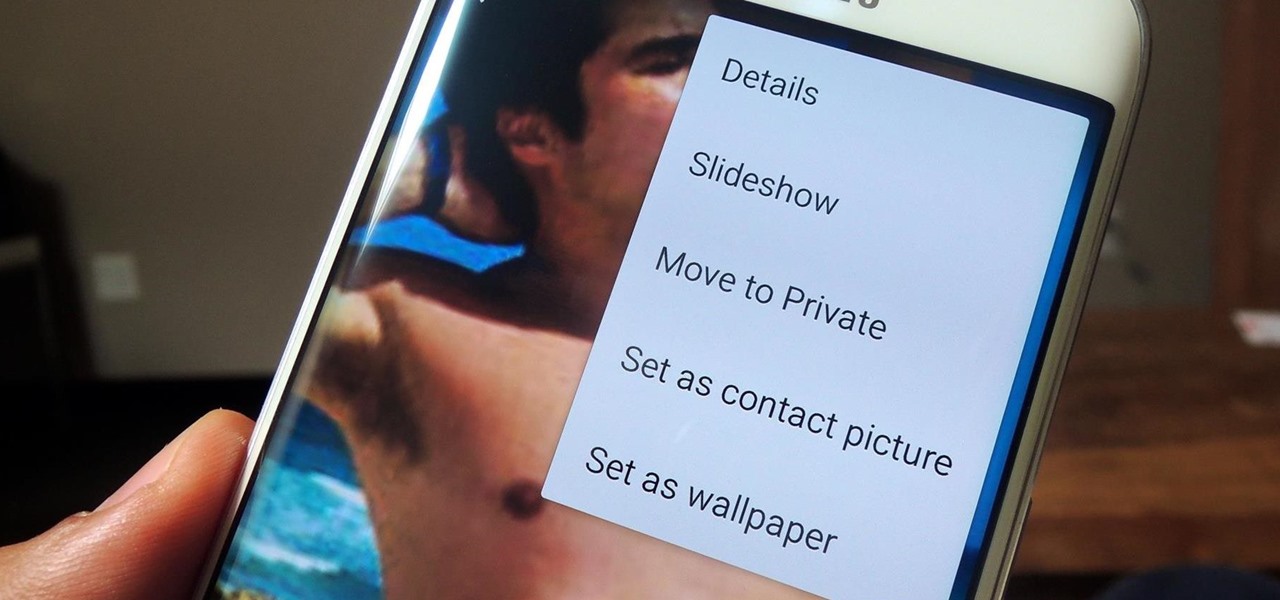
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.

An app with overabundant features can make it more customizable, but too many options can also be overwhelming, even on a mobile web browser. If you're tired of Safari or Chrome on your iPhone, try out Frameless from developer Jay Stakelon, a simpler web experience using just the essentials.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.

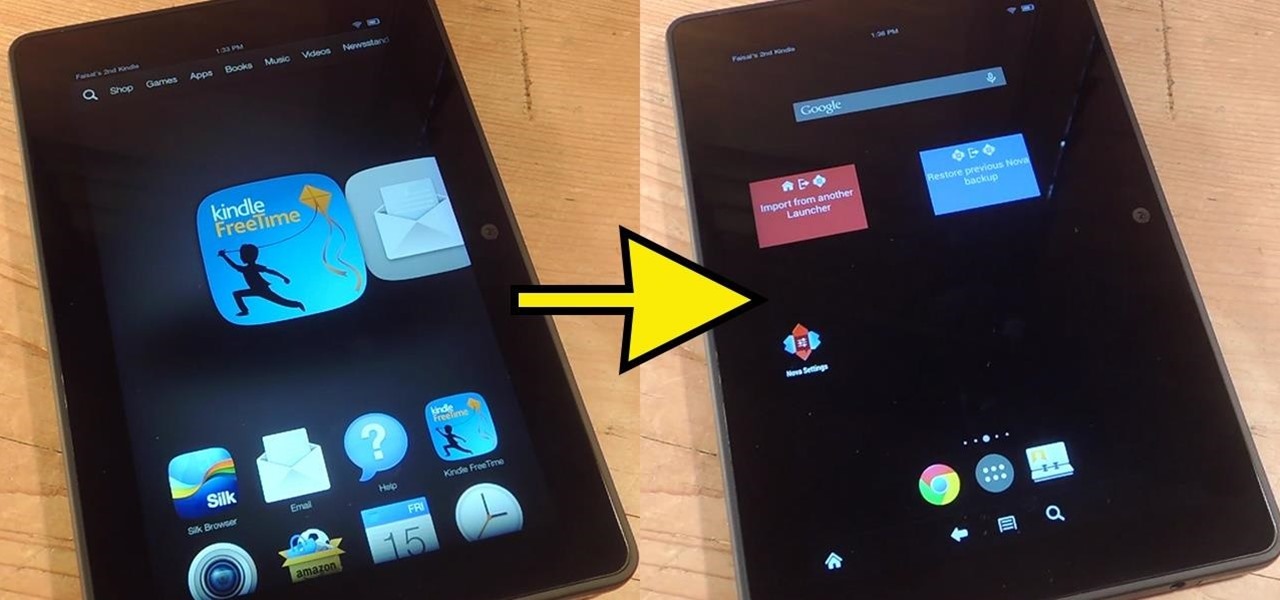
Stocked with a 7-inch LCD display and 323 PPI (pixels per inch), the Kindle Fire HDX is one of the best tablets on the market for enjoying some great literature or entertaining streaming services—and I take full advantage of what this device offers.

No matter whether you're a seasoned Android veteran, or just starting to get into the scene, you have probably heard of Tasker, the king amongst all the various automation tools available.

There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly onto your device and installing it with iFile.

In a previous softModder guide, I detailed how to get the Jelly Bean 4.2 Photo Sphere Camera and Gallery on your HTC One running Sense 5, but that was quickly outdated with the release of the new Google Play Edition HTC One, which has a newer Camera that works great with our hardware.

In a previous softModder tutorial, we installed CyanogenMod on our HTC Ones to approximate the look and feel of the Google Edition HTC One. Unfortunately, this rendered Beats and HTC's ImageChip (among other things) useless.