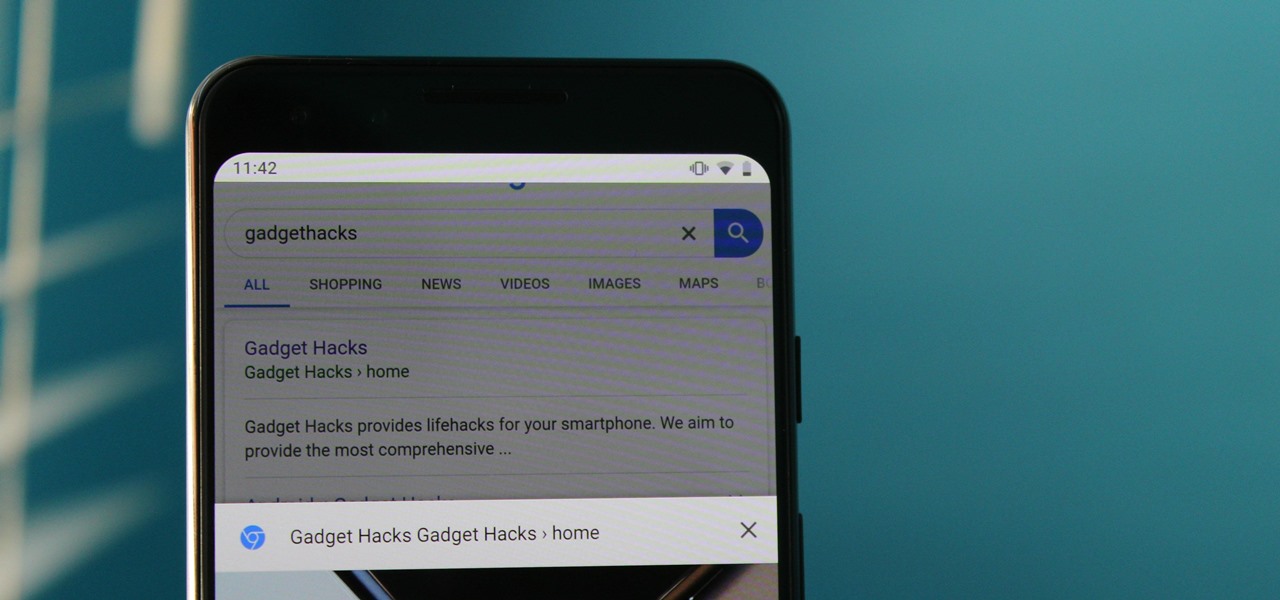
If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, it does make navigating the web easier.
If you're a console or PC gamer, you may be quick to ignore the mobile version of Fortnite Battle Royale. The lower graphics and the switch to touchscreen controls may be enough reason to dismiss this version of the game. But don't be so quick to judge — there are actually some clear advantages to playing on mobile.
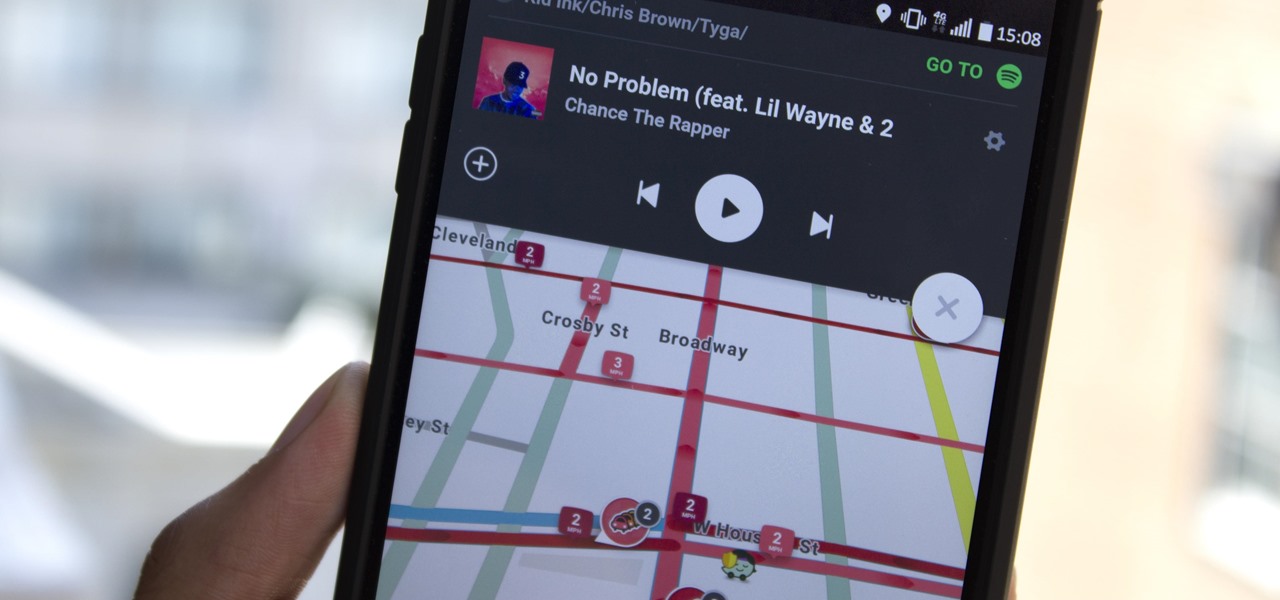
Who doesn't love listening to music or playlists when driving? The open road and an awesome playlist make for a perfect pairing, but it can become quite the challenge if you're trying to navigate at the same time. That's why Waze's built-in audio controls for compatible apps like Spotify and Pandora are so useful, so you can always keep your eyes on the map and road ahead of you.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

If you have a mobility impairment that affects your hands, arms, or manual dexterity, a smartphone's touch-based interface can almost be a barrier between you and the mobile internet. Eye-tracking software requires too much computing power for today's smartphones to handle, so it might seem as though there's no good way to interact with an Android device.

LG, like many other OEMs, usually locks down their bootloaders with an airtight seal. There are a few good reasons for this, the big one being that an unlocked bootloader technically compromises some device security measures. LG would also argue that unlocking your bootloader is absolutely pointless, as having it locked will not hinder normal device usage, which is kinda true.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Greetings all. I'm back with another informational review of the diversity of utilities for use in the sphere of hacking at your disposal. Today we are going to cover the insides of CUPP (Common User Passwords Profiler) in its entirety. The tool is very basic in nature, as there is little to no configuration needed to get cracking (worst pun ever). So let's get started, shall we?

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

At last, what you all finally waited for! Hi! Fire Crackers,

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

From my experiences, there are only two types of U2 people: those that love them and those that hate them. I'm the latter, so it's pretty damn annoying that Apple just added U2's new album, "Songs of Innocence," to my iCloud. If you find it creepy that U2 is appearing on your iPhone or in iTunes, don't worry—I've found a few ways to deal with it. UPDATE: How to Delete U2 Forever & Ever

Welcome back, my tenderfoot hackers! In continuing my series on digital forensics using Kali, I want to introduce you to two complementary tools, both built right into Kali Linux. These are Brian Carrier's tools Autopsy and Sleuth Kit.

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Sony has been hard at work refining its Xperia line of flagship phones. With a 6-month release cycle, they've managed to slim bezels, increase viewing angles, and boost processing power in the 1.5-year span between the original Xperia Z and the Z2.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

We've all been there. Stranded in a large lot or parking garage, braving the rows upon rows of identical cars in an endless concrete landscape because, for the very life of us, we can't remember where we stashed the very ride that brought us there.

A rooted Android device means we're on our way to some truly amazing customization options. But there may be a few steps left to completing that journey, and a major one is installing a custom recovery.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

After a two-month delay, Apple has finally released iTunes 11, which was initially slated to be released alongside iOS 6.

In this automotive repair video, you'll learn how to change your own brakes. Throughout this process, you'll also figure out how to remove your tire, calipers and brake pads, and how to clean the brake pad area. See how to take off the rotor and reinsert everything correctly. It's an easy process, and you don't need to be a professional mechanic to install new brake pads.

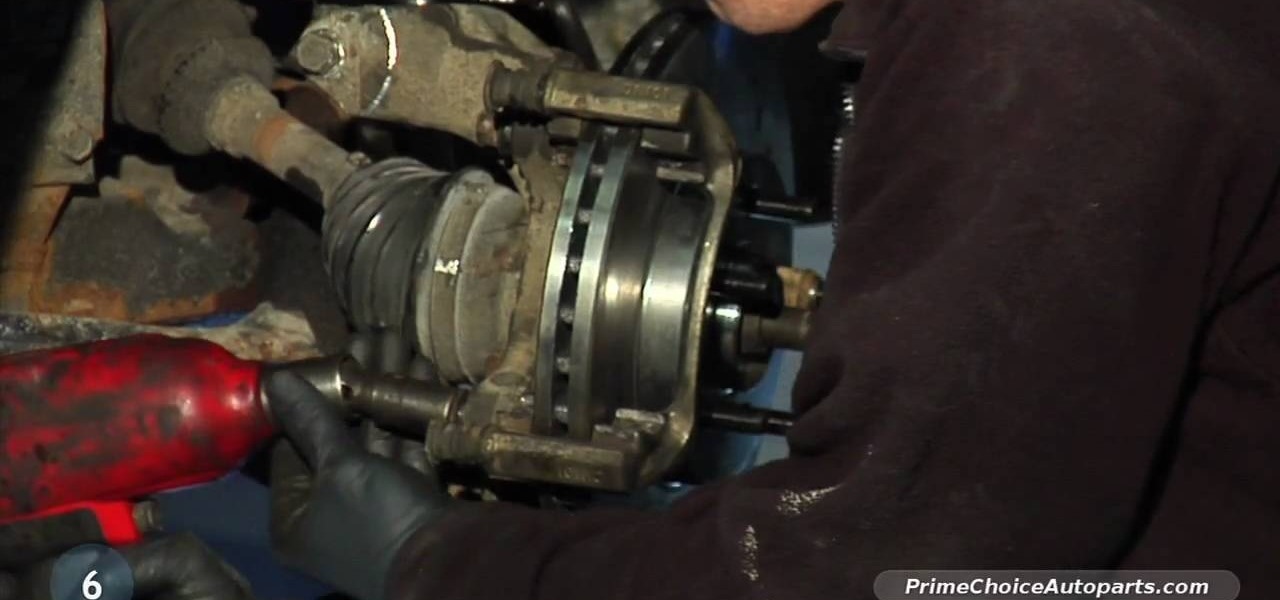
Hub bearing assemblies are one of the most expensive things you could get fixed on your vehicle. And it's not an easy task to repair yourself if you're not a semi-professional mechanic. But with the help of this video, you'll learn the steps to changing hub bearing assemblies, from a licensed technician.

Julie Goodnight guides you through how to safely mount and dismount a horse. First make sure you put the reigns up over the horses head. Keep the reigns in your hands so you always have control of your horse. Check the cinch on the saddle before putting your foot in the stirrup. Make sure the horses feet are square so it can properly brace when you go to mount. Stand to the front of the horse, facing the rear, so you can see the legs at all times. This will also discourage your horse from ste...