While it seemed like jailbreaking methods were always one update behind the current build, the team over at Pangu have already released a jailbreak tool for iOS 9, and it works up to iOS 9.0.2. It is not available for iOS 9.1 through 9.2 yet, but we will update this guide when they are ready.

Accidentally deleting important files can happen as easily as swiping left on something and watching it disappear into the ether. Of course, Apple allows automatic backups through iCloud, which ensures that your data is always stored safely in the cloud in case of emergency.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

Nowadays, protecting your valuables can be challenging especially when you're on the go. That's why I decided to make a little secret compartment inside my car. Only you'll know it's there because nobody will be able to find it. Not only that, but you'll have easy access to it. It's fairly cheap and the total cost was under $5.00. Let me show you how to make it. You can watch the video or scroll down below for the written guide.
The internet is forever. When you put something out there, it can easily be re-shared, floating from server to server indefinitely with no way of taking it back. It's a scary thought when you consider that a young adult's grandchildren will one day have access to their drunken party pics.
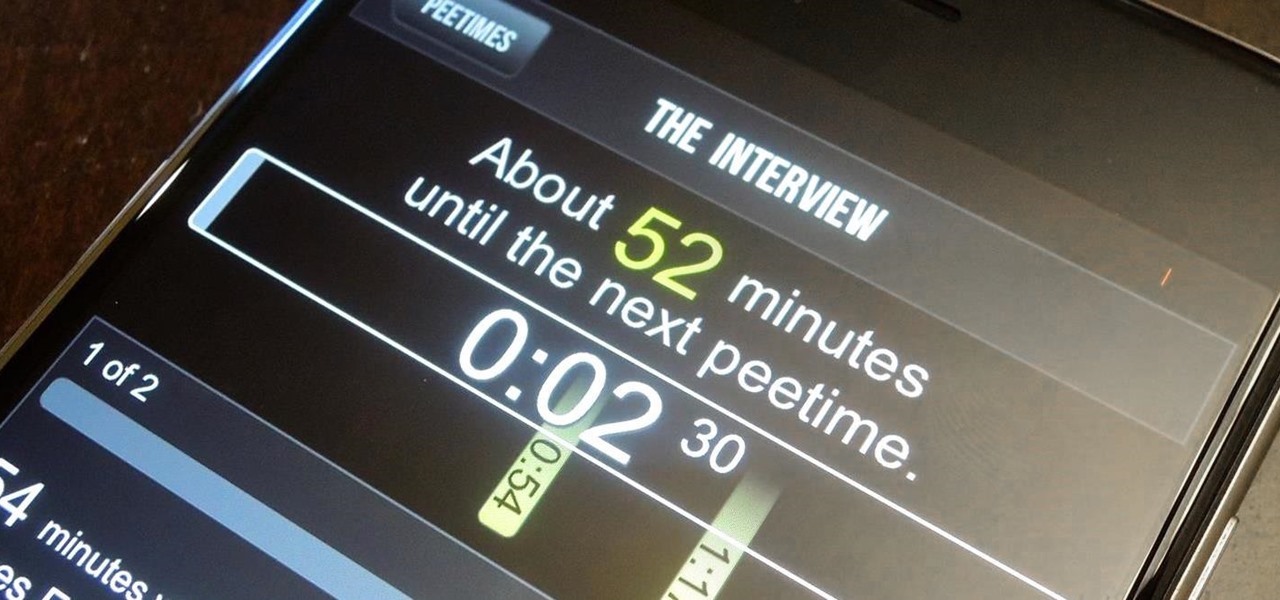
When I watched the first Cincinnati Bengals edition of the HBO series Hard Knocks back in 2009, among wide receiver Chad Johnson's bravado and attention-grabbing antics was a segment on backup quarterback Jordan Palmer and his newly-developed app, which was still in its infancy. Six years later, I've revisited his creation and have to admit—it's pretty damn useful.

When exercising at a high intensity, you know to expect some level of pain. That can make it difficult to identify when your body gives you a warning sign of injury. If you pay close attention, however, you can tell the good hurt from the bad. I talked to Dr. Brian Parr again, professor at the Dept. of Exercise and Sports Science at the University of South Carolina Aiken, who explained which symptoms of exercise are normal and which are bad:

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

Hopefully you never have to deal with a grease fire, but if it happens, how you handle it is important. A grease fire isn't like a regular fire, and trying to put it out the same way can make it worse. Grease fires are caused by letting oil get too hot, so the best way to prevent them is to never leave your kitchen unattended. Oil smokes before it burns, so if you see your pan start to smoke, take it off the heat before it has a chance to catch fire. If you're outside grilling, you can add a ...

If you ever find yourself in a car that's submerged under water, your first instinct should be to try and open either the window or the door in the first few seconds of touching water. Unfortunately, if you wait any longer than that, the lopsided ambient water pressure subjected to the car will make it impossible to open the car door, and the now ubiquitous power windows will likely short out. Sure, you could wait until the pressure has equalized on both sides of the car, but this usually hap...

We have shown you how to get CyanogenMod on your HTC One and Samsung Galaxy S3 in only a matter of minutes. But when modding your phone by installing custom ROMs, you'll often lose your access to Google Apps. Since Google's Apps are very useful (Gmail, Chrome, and Maps to name a few) most people will prefer to have these apps on their custom ROMs. While you can scour the internet searching for individual .APKs, it's hard to find the correct versions to work with your particular system (and do...

Russians are well known for their knack at documenting exciting and horribly beautiful events on the go, from insane car accidents to attempted insurance fraud and even a superbolide meteor streaking across the sky.

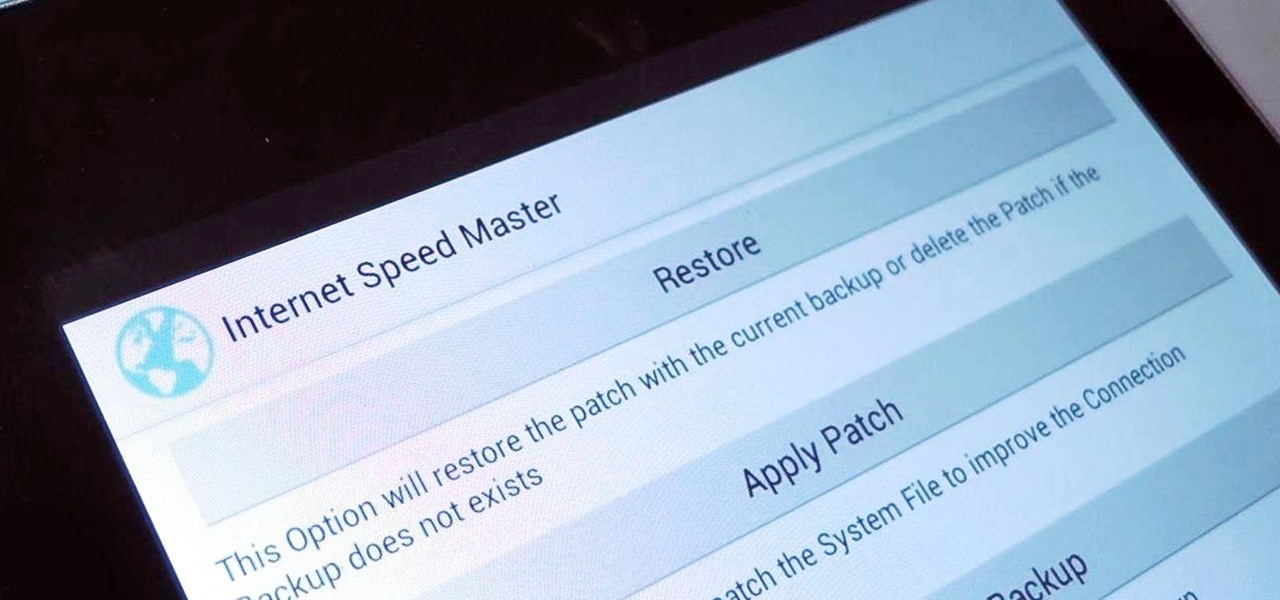
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

At a time when virtually everyone has a cell phone, it's almost inconceivable to think of a time when we're without them. At work, in bed, and even in the bathroom; we're always with our smartphones. I mean, hell, someone even designed a way to bring your smartphone into the freaking shower. It's not THAT serious.

Texting is a godsend to mobile devices, but it also has its caveats. Sending a text to someone requires visual, manual, and cognitive attention—looking at what you're typing, holding the phone steady, and thinking about what you're trying to say. So, texting while doing pretty much anything else is not a wise move.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

The next time a light bulb burns out in your house, don't throw it out. Believe it or not, burned out light bulbs aren't entirely useless. Besides creating an extra task on your to-do list, they can be hollowed out and used for a variety of different things from home decorations to miniature indoor gardens.

Traps are great, but sometimes you don't want to kill anyone, you just want to know when they're around. When that's the case, check out this handy alarm system that uses the power of doors! Doors, you say? Yes, doors! Some of you may already be familiar with how obnoxious doors can be in Minecraft, but if not, check out this video of it in action:

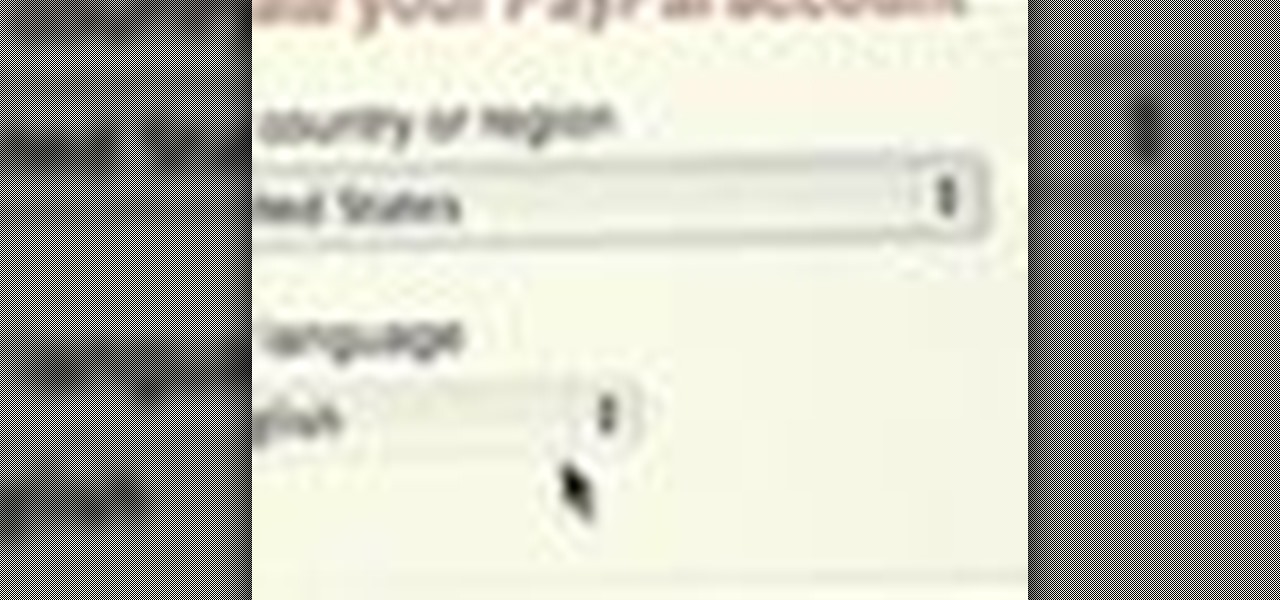
If you like to shop online then it is extremely helpful to have a PayPal account to safely make your online purchases. Help reduce your risk of identity theft by using protected methods like PayPal when your credit card information is involved.

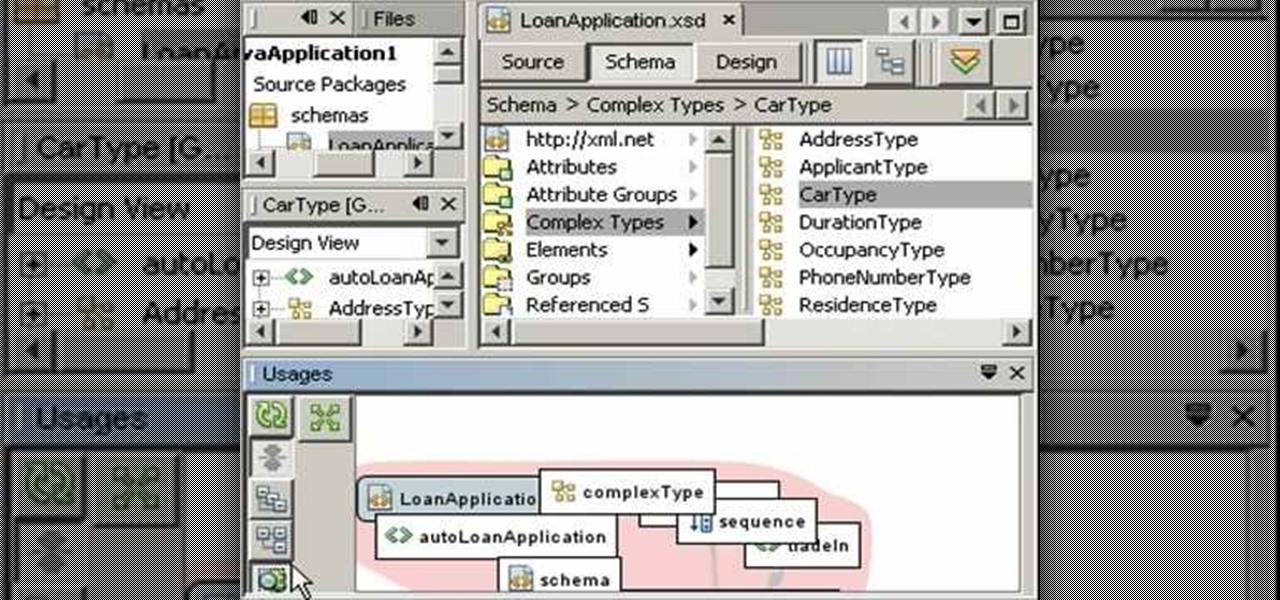
Watch this video tutorial to learn how to use the XML schema tools, which enable you to create, visualize, and edit XML schema in NetBeans 6.0. With these tools, you can visualize relationships between schema elements and use queries to find usages. You will also learn how you can easily create XML schemas by example. You will see how to navigate large schemas in the Design View, and you will learn how to visualize and edit multiple file schemas.

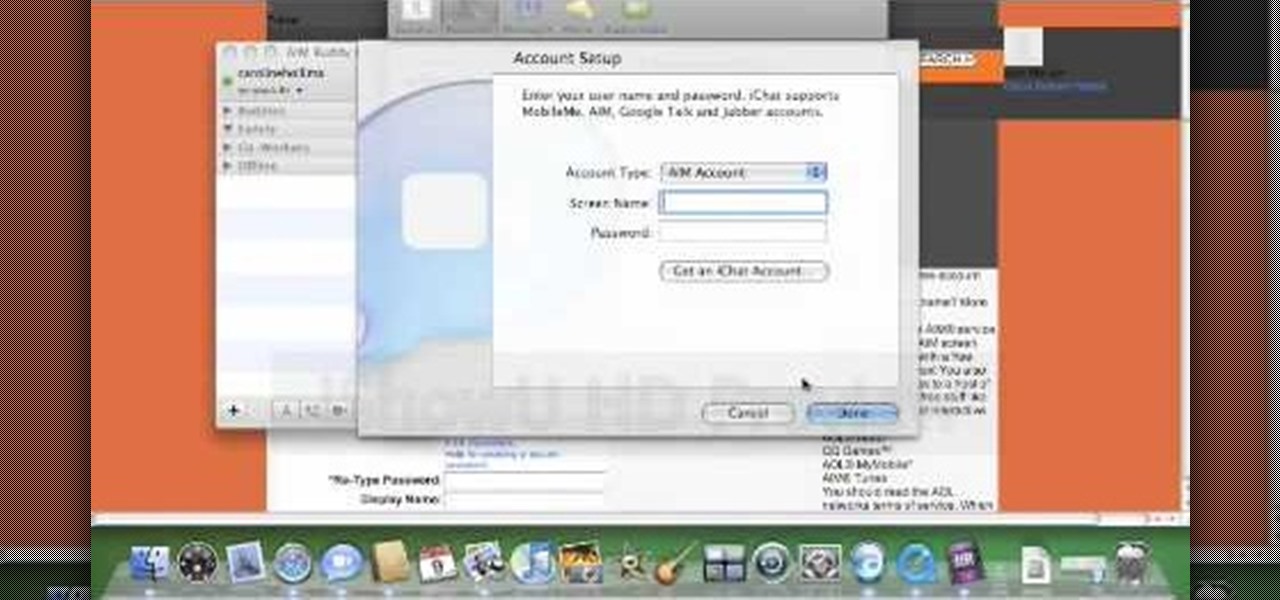
In this video, viewers are shown how to use the iChat feature on a Mac computer. To begin, the video creator instructs us to open Safari (or your preferred) browser and to navigate to www.aim.com. This is the AOL Instant Messenger site (AIM) and from here, you are able to create a screen name. This is important because you have to have a screen name with a instant messaging service to be able to chat using the iChat application.

Internet4Dummies shows how to take a screen-shot of your desktop screen using your keyboard and a photo-editing software like Microsoft-Paint, in this walk-through video first you have to navigate or arrange your screen as desired to be captured in the snapshot. Then using the print screen key the whole desktop screen can be captured. This image can be edited by any photo editing software for ease of use Microsoft Paint is used in this example. For this just open Paint and paste the screen-sh...

The LG KF700 Virgo is designed to maximize convenience, enjoyment and productivity, LG’s advanced UI brings new meaning to the word convenience. The KF700 is the only place to get hands-on experience with the magic of its touch as you control your mobile life with simple gestures.

With the LG KU990 Viewty, you can take and view a crystal clear photo. Packed with high-quality camera features, this camera phone enables you to capture a high-definition image using a 5 MP camera lens certified by Schneider-Kreuznach and edit your photo on a large, clear, 3-inch display just like a professional photographer.

TWRP is the premiere custom recovery for Android because of how many devices it supports and how simple it is to use. But installing it in the first place hasn't always been the easiest thing to do — until now. With the help of a Magisk module, you can finally use one Android device to flash TWRP on another.

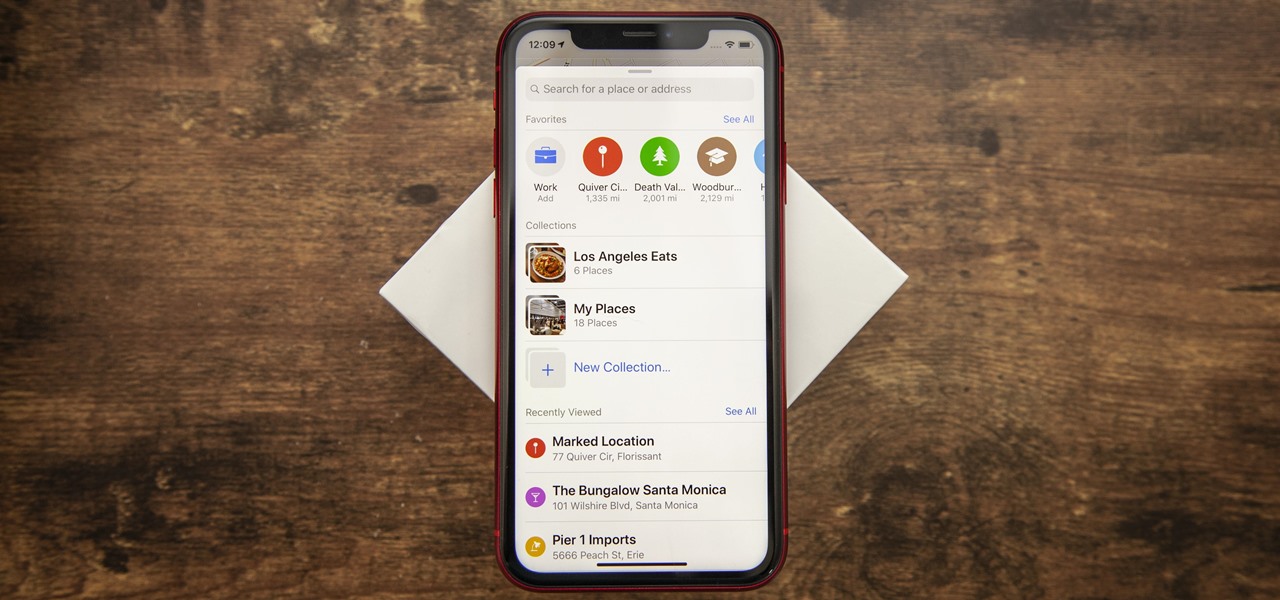
Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

Alright, I'll admit it, iOS can be quite nice. Android loyalist that I may be, I'm not so stubborn that I can't recognize a good thing when I see it. Apple's iOS has a lot of strengths, and our Nexus 4s, god bless 'em, are growing a little long in the tooth.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!