Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

The new and improved Side button, as well as a plethora of new swipe gestures, are responsible for picking up the slack left by the missing Home button on the iPhone X. If you're really missing that Home button, however, Apple's built-in AssistiveTouch tool can help you out by adding a virtual Home button on your iPhone X's screen.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Your dog is doing something charming, and you need to take a quick photo, but you don't have time to search in your app drawer for the camera app. The moment would have long passed by the time you find it. What if instead you could you open the camera or any other app simply by sliding your finger down on the home screen? Well with Nova Launcher and gestures, this is easy to accomplish.
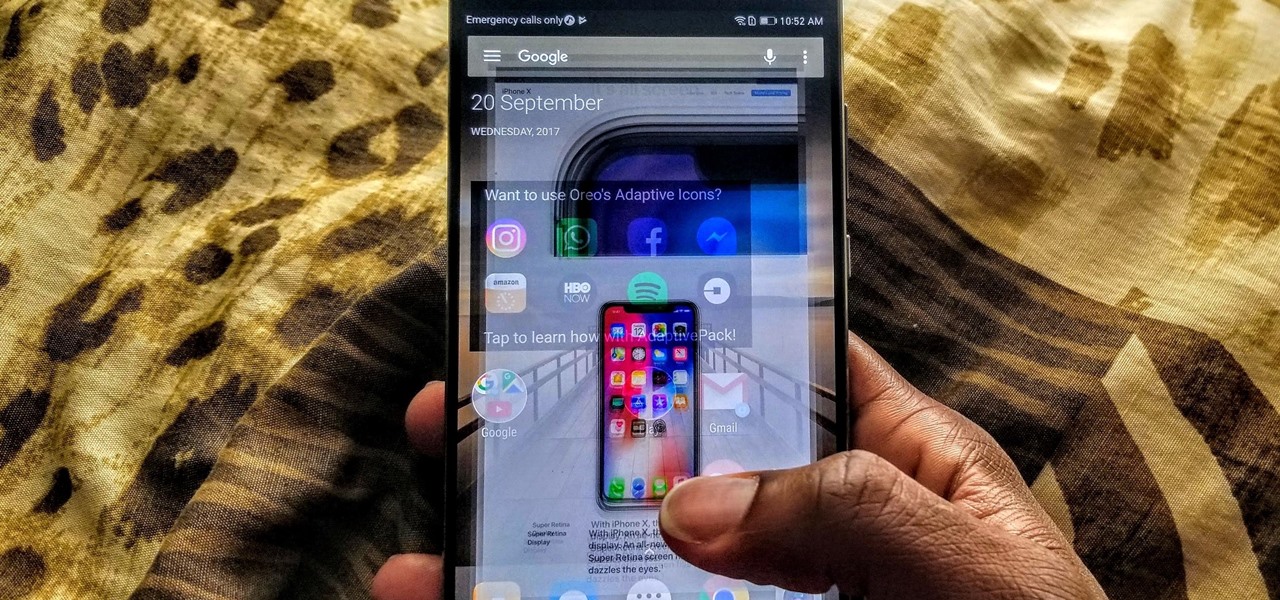
With the new iPhone X, Apple introduced a buttonless design for the first time. But without a home button, navigation within iOS 11 had to change to accommodate the new model. To solve this issue, Apple created gestures to perform the actions that the home button once executed. But while Apple users have to wait until November 3 to use these gestures, you can get these features right now on Android.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

There are a few different ways to install Magisk. If you're already rooted and you just want access to Magisk modules, you can use Magisk Manager to install the Magisk framework. Or, if you want to pass SafetyNet on a rooted device, you can switch from SuperSU to Magisk SU. But the best way to do it is to start fresh by installing Magisk on a non-rooted phone using TWRP.

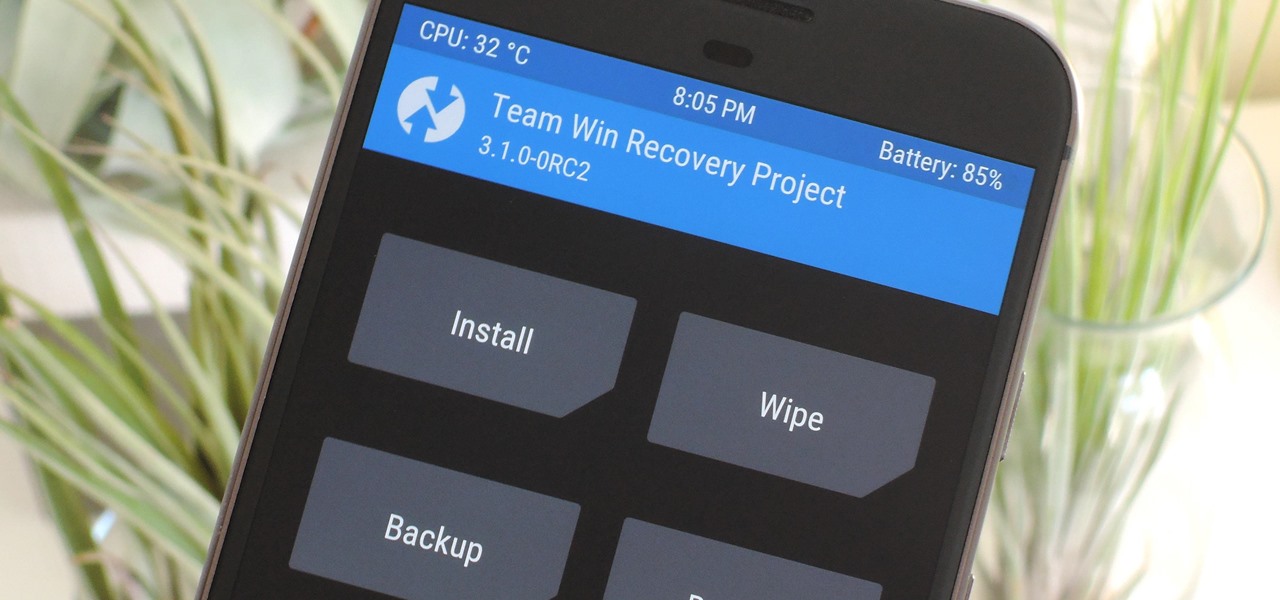
When it comes to modding Android, root gets all the glory, but a good custom recovery is really the only thing you need. Not only does it allow you to back up your entire phone, install flashable ZIPs, and load custom ROMs like LineageOS, but a custom recovery will even let you root your device. For years now, the only custom recovery worth mentioning has been Team Win's TWRP.

The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone.

Scientists know that bacteria create their own energy, get nutrients to run their cellular processes, and multiply. But, bacteria haven't been shown to respond to external mechanical stimulation or signals in a way that's similar to how our bodies respond to touch, until now.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

To really personalize your HTC 10, you'll need to be rooted — but that can't happen unless you unlock your bootloader. Thankfully, HTC has made it relatively easy to unlock the bootloader on their 2016 flagship.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

Tesla hopes high-level personnel changes will help it gain an edge in neural network knowhow for its models' self-drive features, following the replacement of its Autopilot chief and the appointment of a recent Stanford grad to head its AI and Autopilot vision research.

Stakeholders in the driverless industry are anxiously awaiting changes the US Department of Transportation (DOT) is making to self-driving vehicle guidelines.

One of the biggest features to come out with Android O was the addition of a new System UI Tuner submenu that lets you customize the navigation bar at the bottom of your phone's screen. But as it turns out, this same feature can be enabled on devices running Android Nougat, even without root access.

Update Feb. 2020: Google has removed the feature flag to move the address bar to the bottom of the screen. We've out to see if they have plans to bring it back, but received no comment. In the meantime, you can use the new Chrome Duet bottom bar instead.

Within the coming months, software startup Neurable plans to introduce the next paradigm in virtual and augmented reality: the brain–computer interface (BCI).

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

Now that Android Nougat lets you add your own custom Quick Settings tiles, your pull-down menu is probably getting a lot more crowded than it used to be, with all sorts of new and useful toggles. But the trouble is, you can only add up to nine entries before your Quick Settings tiles spill over into a second pane that you have to access by swiping, and that's not exactly "quick."

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

When it comes to modifying Android, the single, most powerful tool available is TWRP custom recovery. It's even more capable than simple root access when it comes to changing the look and feel of your software, and you can even use TWRP to root your device in a few simple steps.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

When it comes to modding an Android device, a custom kernel can take you farther than almost anything else. Most offer the ability to overclock your processor for performance gains, change your CPU governor, or even under-volt to increase battery life, among other features.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

While visiting the Made by Google pop-up shop in New York City this morning, I had a chance to try out the new Daydream View virtual reality headset. First impressions are important, and Google's new mobile VR product makes a good one. The headset is made of a soft fabric that most evokes a beloved old college sweater that's well worn but properly cared for. The demo only featured the Slate (darker gray) model, though customers will ultimately be able to choose from either Slate, Snow, and Cr...

Google has a habit of starting on new projects for Android, then hiding them away if they didn't quite complete them in time for a major release. We saw this with multi-window mode last year (which is now an official Nougat feature), and this year, there was the hidden night mode setting that was easily activated.

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

The new iOS 10 won't be released to the public until September 13 via an OTA update, but the Gold Master edition is available right now. Essentially, it's the same version that Apple will release on the 13th, but only for developers so they can get their apps up to snuff before everyone updates. Users on the iOS 10 public beta will not be getting this GM update.

During the lead up to Samsung's Note7's release, rumors swirled about a leaked "Grace UX" interface replacing Samsung's maligned TouchWiz Android skin. In the end, this seems to have been nothing more than an internal code name that Samsung was using to test a few new icons and a slightly-redesigned Settings menu, because not much else has really changed.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

For many people, the two main advantages of buying a Nexus device are prompt updates and the ability to root without much hassle. But in a cruel twist of fate, these two features are almost mutually exclusive, since OTA updates will refuse to run on rooted devices.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.