Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

The long wait is over — the best augmented reality device on the planet is finally available.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Although the Magic Leap One: Creators Edition is currently officially available in only six US cities, those living outside of Magic Leap's designed US cities now have a roundabout way to order the device.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

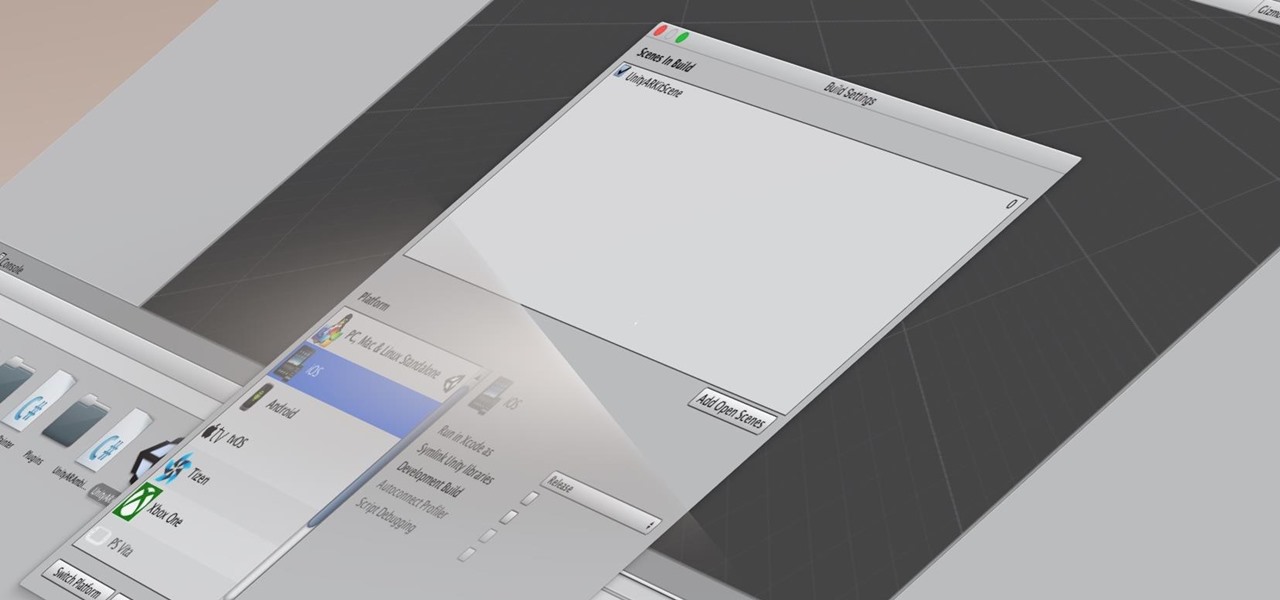
Many developers, myself included, use Unity for 3D application development as well as making games. There are many that mistakenly believe Unity to be a game engine. And that, of course, is how it started. But we now live in a world where our applications have a new level of depth.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

The food TV chefs prepare make our mouths water. From one scrumptious creation to another, they fly through preparation without frustration or error. They make us think we can do the same with similar ease and delectable, picture-perfect results. Some of us have noticed, though, that these TV chefs don't always adhere to the same safe food handling guidelines we've been taught to follow.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Welcome back, my neophyte hackers! In the world of information security, the most common intrusion detection system (IDS) you will ever encounter is Snort. As you probably already know, an IDS works similarly to antivirus (AV) software on your desktop; It attempts to identify malicious software on your network and warns you of its presence.

When to throw meat away is a common question, and one I often ask when faced with meat sitting in the fridge after a few days. With vegetables, you can usually tell on sight (or with this guide) when they're past due, but meat is not as simple.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

Kitchen tools are a personal thing. One hard lesson for me to learn is that just because something is popular doesn't mean that it's right for me. Take the slow cooker, for instance. Many rave about it, but I never cottoned to the thing. However, the more research I do, the more I think the pressure cooker might be a game changer for my cooking style.

We've showed you how to make Butterfingers and Kit Kats, as well as custom-shaped chocolates, but have you ever thought about making your own gourmet chocolate bars?

The buttery scent of crescent rolls bring me back to my childhood, but those tubes that open with such a satisfying pop are more than just retro reminders. Crescent rolls can morph and serve as the base for hundreds of creative and cool dishes.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

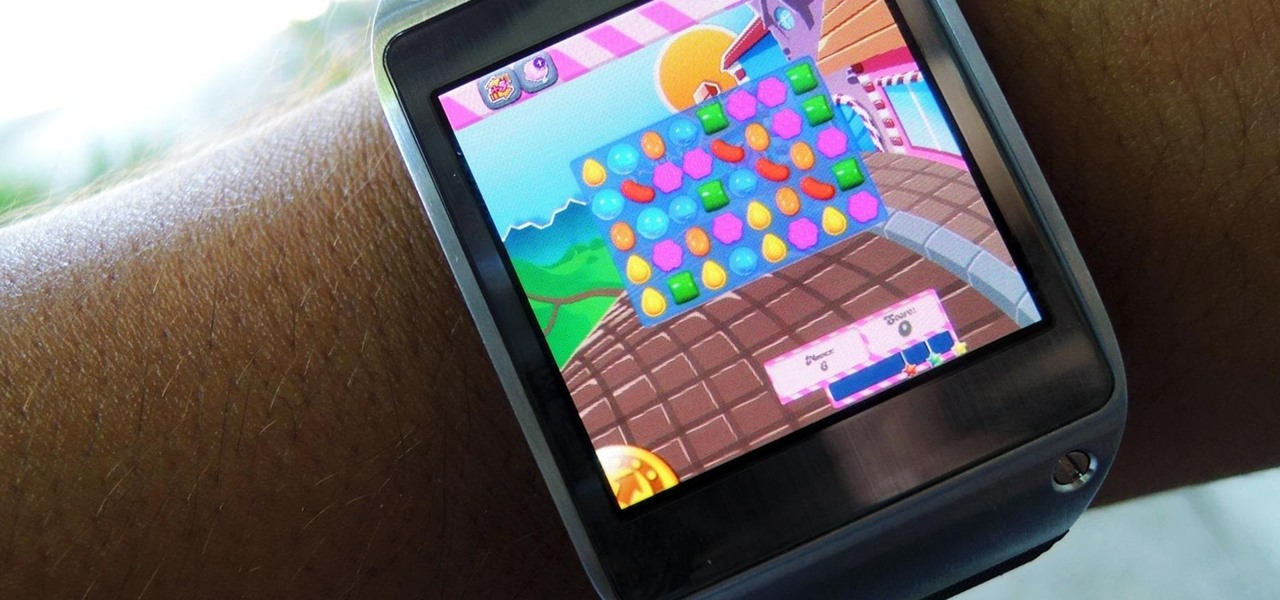
With the Samsung Galaxy Gear smartwatch only several weeks old, the extent as to what you can do with it is limited since there are only about 70 apps in the Gear Store right now, and a lot of those need the full app installed on your Samsung Galaxy Note 3 in order to function properly.

Keep your sound and electronics gear in order! Safety and neatness are everything. Check out this video tutorial from the Good Idea Guys at Good Buy Guys to learn how to keep a mic stand neat and safe. Mic Stand Mike demonstrates how to keep your microphone stands and cables neat and organized on stage. A great helpful tip for cable safety.

Taco Bell's in the news for umpteenth time, and today the controversy is over their infamous beef taco meat. Gizmodo leaked a picture of Taco Bell's "Taco Meat Filling" and surprise, surprise— it's missing a lot of the "meat" that it claims in its advertisements. Taco Meat Filling Ingredients

Cream cheese is delicious on its own, but it tastes simply divine if you spice it up a little with some herbs. While this recipe for herbed cream cheese calls for using fresh herbs, if you don't have an herb garden you can use store bought herbs instead.

In order to find the best drill bits to drill in metal, you should look at the angle of the bit. It will need to have a center point. Bits only cut on the ends. The grooves on the sides are made to remove the excess. The point on the end determines how it will cut. Titanium bits last a long time, but cobalt bits last even longer. They will all eventually become blunt. They will require sharpening.

In some places, it's illegal to ride your bike at night without lights or reflectors, so if you plan on going for a joyride on your street bike, then you need to be prepared to share the road with vehicles and be seen. Appropriate gear and lighting are essential for safety when riding a bike at night.

In this tutorial, we learn how to make a long drawstring skirt. You will need: knit stretch fabric ( 1.5 yards), safety pin, scissors, marking tool, and measuring tape. First, measure your hips and decide if you want your skirt to be tight or loose. For a tight fit, you want 2 inches of ease and for a loose fit, you will want 3-4 inches of ease. You can now decide how long you want your skirt to be and add 2 inches to that. Now cut your fabric and fold it in half, then cut it straight down. A...

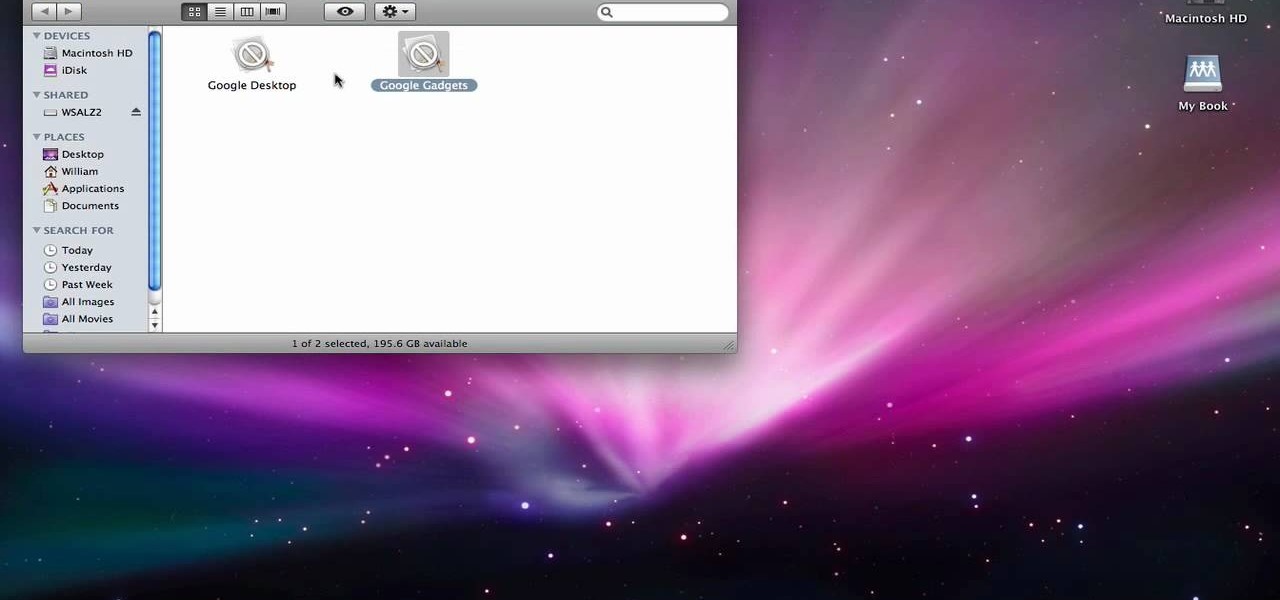
In order to completely delete items from Mac OS X. Download Google desktop. This will search your computer and the web and your computer. Go to Applications. Right click on Google Desktop. Go to Show Package Contents. Drag contents into the trash. Next, go to Google Gadgets. Click and drag it to the trash as well.

Spiders. They live around you, the sleep next to, and they hide in the corners of your room. They're considered pests by most people, but to some, then considered a delicacy. Believe or not, the strongest natural fiber known is from the silk of the Nephila spider, but that spider is nothing compared to a huge, hairy, hideous tarantula. Tarantulas have been a delicacy for years. Enjoy one of these recipes when they are hot and crispy.

Having some friends over for a Super Bowl Party? From Betty of Betty's Kitchen, learn how to make a delectable cream cheese "Saucy Party Dip" great for a sports parties, for an appetizer or just for snacking!

Sandra Lee from Every Day Homemade demonstrates making lemon cream squares. She starts with a whole stick of butter, softened to room temperature. Add a box of yellow cake mix to the butter, and also one egg. Mix the batter with a hand mixer. It will be very thick. Clean off the beaters with a spatula. Spray a baking dish with non stick spray. To save on cleaning time, the pan can also be lined with aluminum foil. Put the batter into the baking dish and spread it evenly. Then take two bricks ...

In this Food video tutorial you will learn how to make a chocolate yule log with Sandra Lee. You will need a chocolate cream roll for this. Take some whip topping, put one teaspoon of vanilla and very gently stir it up. What the vanilla does is it cuts the packaged taste. Now spread this all over the cake and on the front and back; nice and thick. Clean off the edges and round them off like a log. Take a fork and drag it along the length of the log all around. With the knife, make spirals at ...

This video shows how to make a peasant blouse, using a T-shirt pattern from a previous video. Take the front of the T-shirt pattern and cut it out of your fabric. You will need two pieces the same, one for the front and one for the back of the blouse. Save the extra fabric from the neckline to add length to the sleeves. Place the two pieces right sides together and sew the side and shoulder seams.

This video explains how to handle and take care of a horse. Always approach a horse quietly so that you don’t startle him. Talk to him and pet his neck. Horses are social animals and react well to being spoken to in soft soothing tones.

Janice Cox shows how to make fizzing bath bombs like the ones you see in bath and beauty boutiques or department stores. These bath bombs can be very relaxing when dropped into a warm bath and can be given as gifts. She starts with about a cup of citric acid crystals which is also called powdered vitamin C or ascorbic acid. Citric acid can be purchased in places that sell wine and beer making equipment and online. The next ingredients come from right out of the kitchen cupboard: a cup of baki...

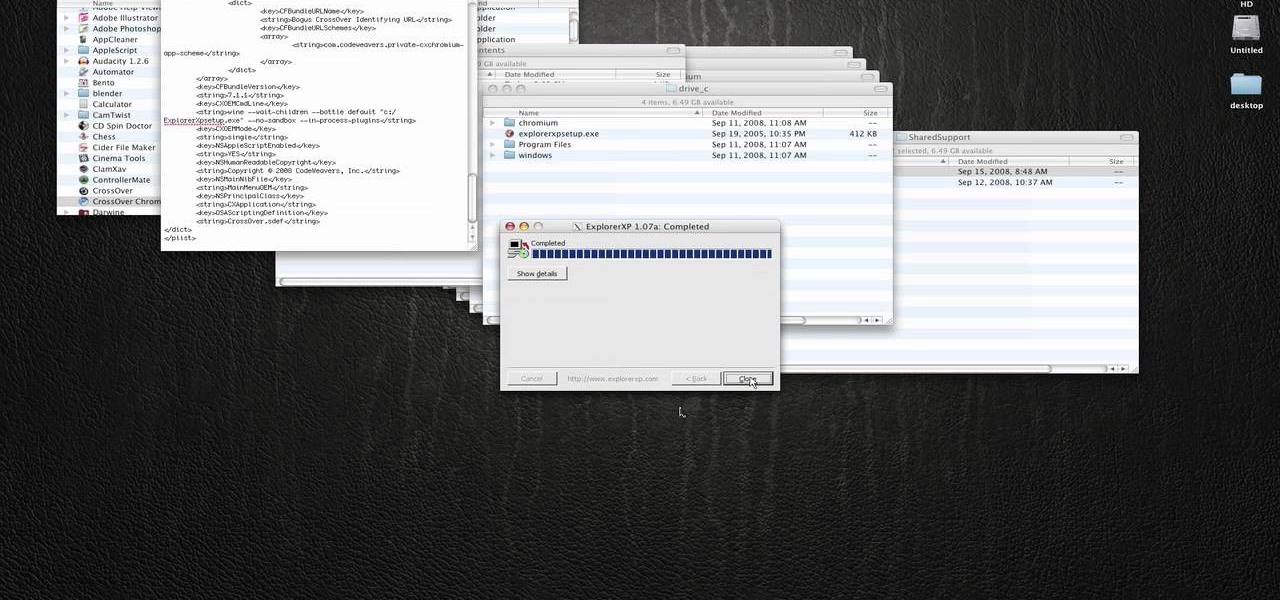
In this how to video, you will learn how to run Windows programs for free on a Mac using Crossover Chromium. You will need to download Crossover and install it by downloading it and dragging it into the applications folder. You will also need Explorer XP. Go to the applications folder and show the package content of Crossover. Go to shared support as you will need a file here later. Open Chromium, go to support, Chromium, and Drive, and then drop Explorer XP into the folder. Open the info fil...

Maria demonstrates how to make pita bread. First, she runs hot water over her mixing bowl to warm it. Then, take a cup of warm water and dump it in the bowl. Add one package of active, dry yeast. Then add a tablespoon of sugar. Let that sit for about five minutes. It should bubble up in that time. Next, add a teaspoon of sea salt, two tablespoons of olive oil, and one cup of flour. Using the dough hook on her mixer she stirs in the flour. Next, add a half cup of flour at a time to the mixture...

WeaponCollector teaches viewers how to make a mini survival kit using an Altoid's tin. You can get an S.A.S. guide for exact instructions and further information on what you will need in an survival kit. First, you should make sure you have rubber bands around your tin to hold it shut. It is easier to get into it and it keeps it closed. You can also wrap the tin with a power cord. Elastic bands work better if you plan on using this everyday. Simply wrap 3 bands around the width and one around...

First you must take inventory of all items in order to be able to create your bag. Make sure all labels are in the correct order. Lining should be ready before attempting to begin construction. The stay should be 10in long and 4in wide. Pocket the stays and glue the stays to the outside fabric. Use the notches to line everything up. Take the magnetic snap and attach it to the front and back. Take a knife and cut holes for the magnetic snap. The magnetic snap comes with a washer. Use cardboard...