
How To: Create Service Files with Systemd
Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.


Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

Ask 100 chefs what the most important tool in their kitchen is, and you'll get 100 chefs saying the exact same thing: their set of knives. For home cooks and professional chefs alike, nothing is more important (or exciting) than a good knife. A good knife allows you to work more quickly, more efficiently, more consistently, and more safely. And best of all, they're just a lot of fun.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?
If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Look on any bistro or pub menu in America and you'll likely find the term caramelized onions as an option for your burger. The word "caramel" may conjure up images of candy, which is somewhat correct.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

The drinking straw isn't just there to help you make annoying noises when you get to the bottom of your soda. That little tube of plastic is extremely versatile and can make your life a lot easier with a little know-how. Curious? Read on to find out more.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.

Welcome back, my apprentice hackers! In this series on password cracking, I have been attempting to develop your skills in the age-old art of password cracking. Although it might seem like a simple and straightforward exercise, those of you who have attempted password cracking know that there are many subtleties to this art.
Apple's grand reveal of iOS 8 at WWDC in San Francisco is still a few days away, but that doesn't mean there isn't any speculation as to what features and enhancements might come packed in the new mobile operating system.

Americans consume over 1.2 billion pounds of potato chips each year, making it one of the most popular snack foods in the United States.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.
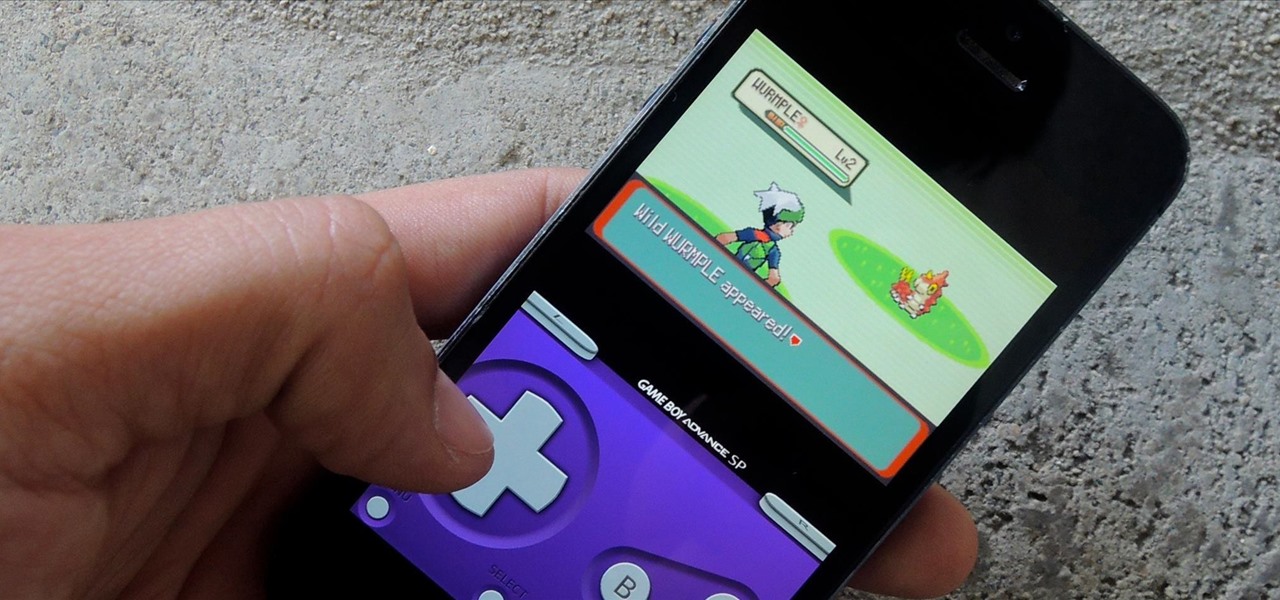
Normally, you'd have to jailbreak your iPad or iPhone to play any games that aren't available in the iOS App Store, like the now-extinct Flappy Bird game. But this isn't the case if you want to play some of your favorite old school Nintendo classics.

From personal photos and videos to online banking passwords saved in your web browser, your phone has all kinds of sensitive data that needs to be protected. One of the best things you can do for your Samsung Galaxy S4's data is have a lock screen with a hard-to-guess PIN or password.

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

To make soap, you need fat, and if you've seen Fight Club, you're probably well aware of where soapmaker Tyler Durden got his fat from. Liposuction clinics. If you're not willing to go that far for a perfect bar of homemade soap, you can just use some drain cleaner and America's favorite food instead—bacon!

Every home cook has their most-hated kitchen task. For me, peeling hard-boiled eggs and garlic are pretty high up there. Actually, peeling just about anything is, but for every annoying job, there's a shortcut to make it easier.
The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.
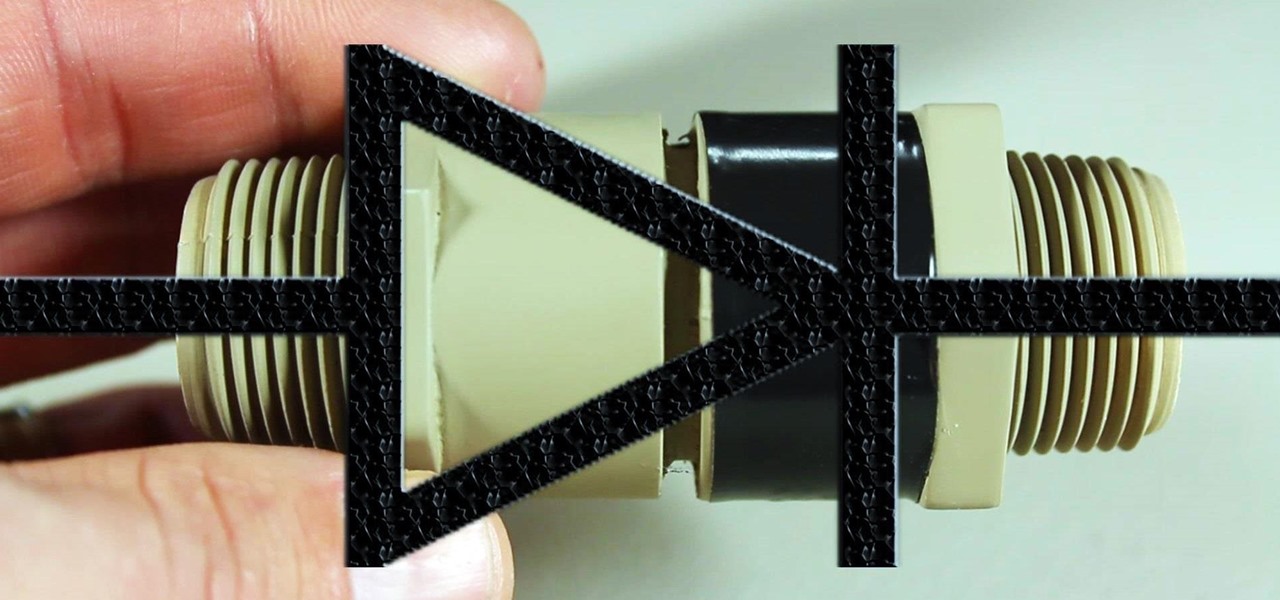
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.
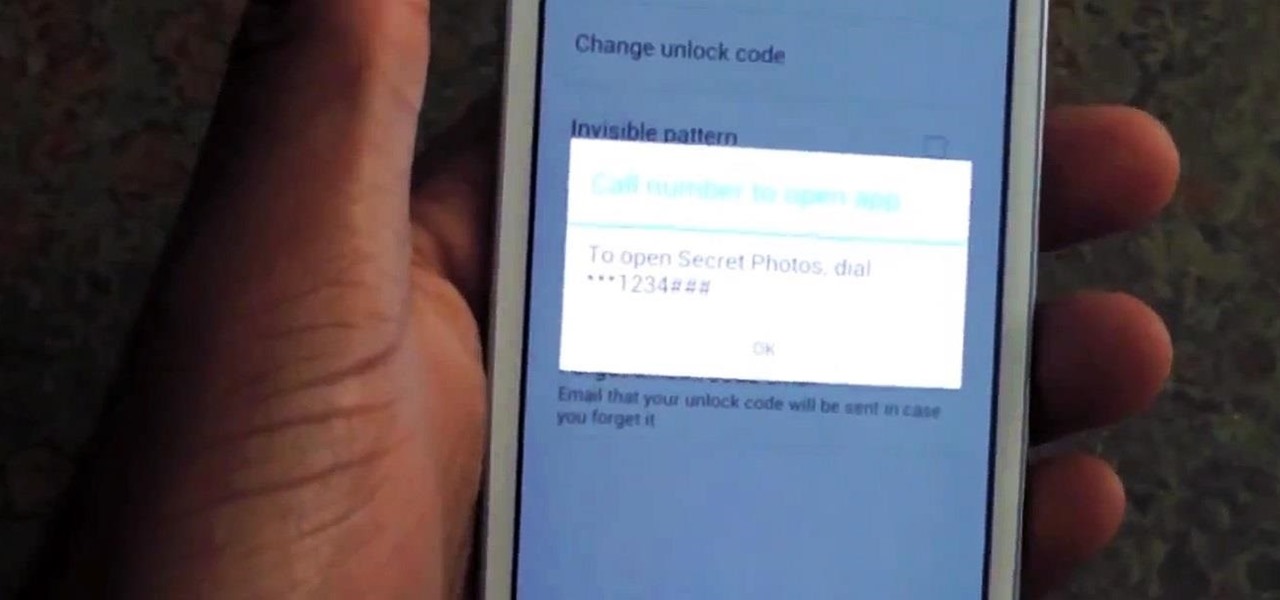
Whenever a friend borrows my Samsung Galaxy S3 to browse the web or make a quick call, I always pause to make sure there's nothing incriminating on it. I'm no superfreak, but some of my friends are, so I have more than a few photos on my device that I wouldn't wish upon anyone. I like to avoid these kinds of looks.

Last time, I showed how to start putting together an AC arc welder from scavenged microwave parts, focusing on the transformer modifications. Now, I'll show you how to finish up your DIY stick welding machine by fixing up the electrical system and performing the finishing touches.

Thought I would cross-post a piece I did a while ago.

Today's project will show how you can convert your laptop, smartphone, or tablet computer into a makeshift projector—just in time for March Madness! It's super cheap to build, and can add a little bit of creative fun to your next sports party.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

There is never a dull moment when it comes to the internet. You can find practically anything you want, whenever you want it. To make that process even smoother and more direct, companies have created a bunch of apps designed to help you find what you're looking for, or enlighten you on a subject you may not have even thought of yourself.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

A travelator, also known as a moving walkway or moving sidewalk, seems like a tricky thing to build in Minecraft, especially when it's zigzagging, but there are really simple autowalks out there (like this one).

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Need a quick repair job for your HP iPAQ Pocket PC RX3100, 3115, 3400, 3415, 3417, 3700, or 3715? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ RX3100, 3115, 3400, 3415, 3417, 3700, or 3715 back together.

Find out how you can kick butt in Obsidian Entertainment and SEGA's video game Alpha Protocol. The RPG and action hybrid came out on June 1st, 2010, and is available on the PlayStation 3 (PS3), Microsoft Windows (PC), and the Xbox 360. This video game walkthrough series from Mahalo focuses on Alpha Protocol for the Xbox 360.

Need a quick repair job for your HP iPAQ Pocket PC H4150 or H4155? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ H4150 or H4155 back together.

Your iPhone has hidden apps that work behind the scenes to filter SMS messages, trust computers, deal with payments, test ads, and perform other actions. You won't find any of them in your App Library, but there are tricks you can employ to unlock and use some of these secret apps.

For whatever reason, you may want or need to remove multiple posts from your Instagram grid. If you only have a couple to hide from the public, archiving or deleting posts one by one is fine, but there's a much faster way when you have tens or even hundreds of Instagram posts to purge from your account.

It's super easy to add filters, adjust levels, and crop images using the default photo editor on your smartphone, but there's rarely any built-in tool for removing the background in a photo. A third-party app can help isolate people and objects in your pictures, and we've found a free one that's easy to use, works with high-resolution images, and is available for Android, iOS, iPadOS, and the web.