
Market Reality: Immersv Closes Funding Round While Lampix Completes Coin Offering
This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.


This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

How would you feel if the stethoscope used by your doctor to listen to your heart and lungs was teeming with potentially unfriendly bacteria?

Augmented reality can be used to fascinate and entertain, but it can be applied in the workplace. While companies on the entertainment end received their votes of confidence via funding, two companies working with enterprises demonstrated their worth by teaming up to pursue customers.

The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.
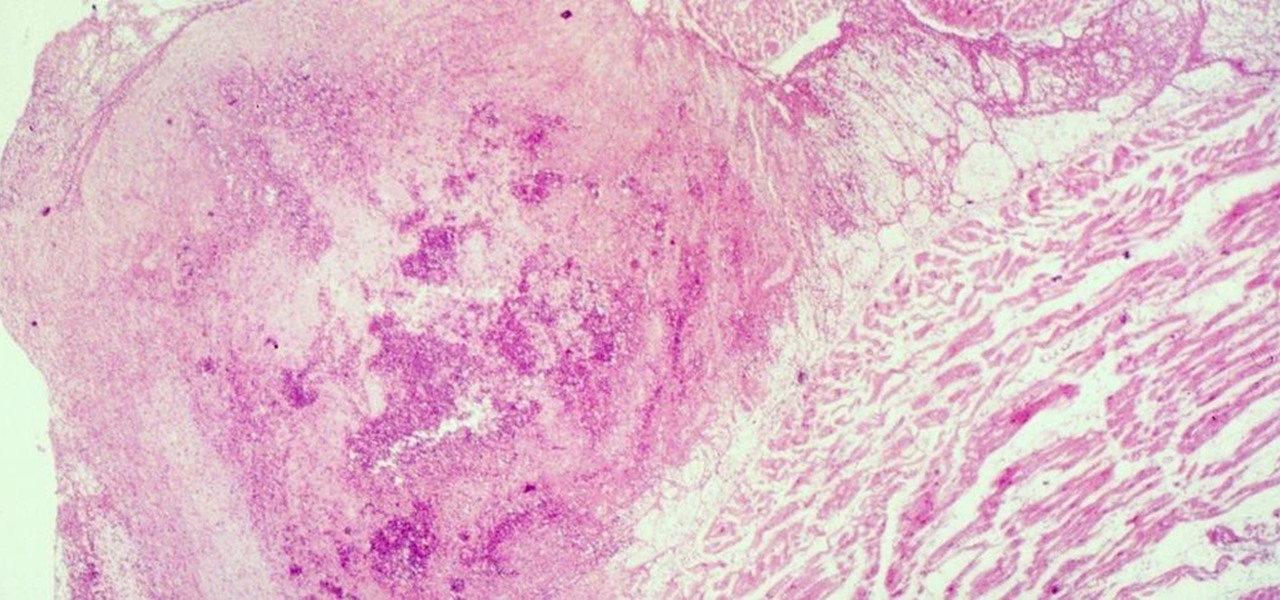
Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.
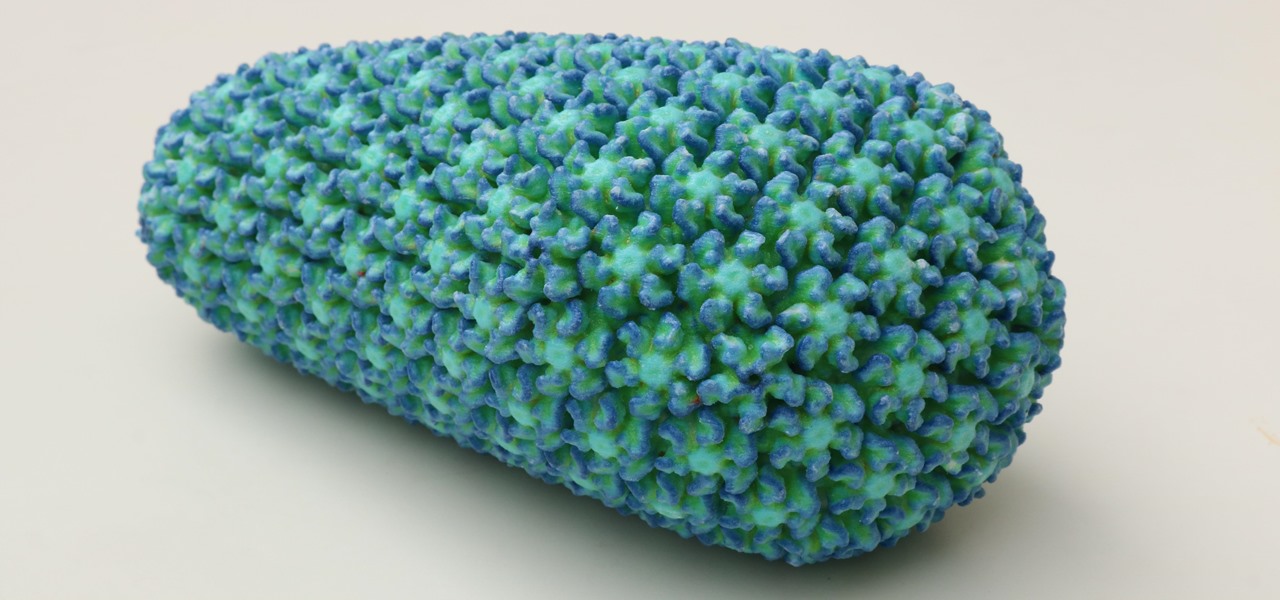
While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

The evidence is mounting and is becoming indisputable: Gut bacteria play a role in strokes and heart attacks. The link may seem a little far-fetched, but cardiovascular disease may have less to do with what we eat and more to do with what chemicals gut bacteria make from the food we eat.

Yogurt is more than an excellent source of protein, calcium, and gut-healthy probiotic bacteria. A protein isolated from probiotic lactobacillus bacteria in yogurt is capable of inhibiting drug-resistant bacteria.

A report by PwC highlights that immersive experiences in augmented and virtual reality represent the fastest growing segment of the entertainment and media industry over the next six years. News from two companies working in the industry, Fox and NetDragon, underscore the growth forecast.
Over the past week, we are seeing more companies capitalizing on services leveraging augmented reality. One company secured funding to expand their service, while two other companies grow its own services through acquisition.

The future of forests looks dreary in the face of a warming climate, but scientists are exploring the relationship between soil microbes and the ability of trees to move to higher altitudes, a key component of their survival.

Our canine best friends could spread our bacterial worst nightmare, according to a recent study. The problem with drug-resistant bacteria is well known. Overused, poorly used, and naturally adaptive bacteria clearly have us outnumbered. As science drives hard to find alternative drugs, therapies, and options to treat increasingly resistant infections, humans are treading water, hoping our drugs of last resort work until we figure out better strategies.

There have been a number of rumors about the iPhone 8 over the past couple of months, but the latest speculation about the device's dual FaceTime camera, that could take 3D selfies, has definitely grabbed our attention.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

After a brief reprieve, Zika fear is back with a vengeance as the US mosquito population booms. And we're just now seeing the true impact of this devastating virus, as babies of mothers infected with the virus are being born.

General Motors acquired Cruise Automation in March 2016 for a reported $1 billion (well, at least $581 million). GM President Dan Ammann made a point of being in the press release photograph with Cruise founders Kyle Vogt and Daniel Kan (see photo below). On January 19, 2017, Vogt posted on Twitter: "Took GM Pres. Dan Ammann for a ride in a Cruise AV."

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!
It's been a while, since I have just started High School. I have put a hiatus to my pentesting for a few weeks, and now, I am making a return. I have taken time to read about code, (even did a research article analysis on how humans can write "beautiful" code and something like that) and pentesting, but never made a full return. I will be occasionally coming back for a while.

There are rules that cooking in general always follows: cakes should be fluffy. Steaks should be heavily seasoned, and nowhere near a bottle of steak sauce. Every stock should start with aromatics (onions, carrots, & celery). And, until very recently, meringues should always be made with egg whites.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

It was a chilly but otherwise beautiful night at YouTube Spaces LA—food trucks, ping pong, a photo booth, and the chance to view film school projects created completely with Glass. About a year ago, the Glass Creative Partnership was formed to explore how Glass could be used in filmmaking, with partnerships spanning from the American Film Institute to CalArts and UCLA. On July 16, 2014, the products of that partnership were screened under the Southern California night sky. Three films were sh...

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Welcome back, my novice hackers! In a recent tutorial, I showed how the SNMP protocol can be a gold mine of information for reconnaissance on a potential target. If you haven't already, I strongly suggest that you read it before progressing here, as little of this will make much sense without that background.

Welcome back, my amateur hackers!

It's almost here. Another year has come and gone, and it's time to watch the Baltimore Ravens and the San Francisco 49ers battle it out in New Orleans for Super Bowl XLVII. For the truly football-obsessed, this Sunday is a day almost as exciting as Christmas. Personally, I just use it as an excuse to cook food that's way less healthy than usual since I never quite became a football fan (sorry, Dad).

Every year the fine folks at Row Three do a post-TIFF mega-wrap up, collecting the micro-blurbs of a bunch of attendees into a giant meta-analysis of what everyone liked, loved, hated, etc. etc.. We'll link to that post when it goes up on the weekend, but in the mean time, here's my contribution:

You've probably noticed how we like to stress the importance of a strong password. After all, there are still people out there who continue to use passwords like 123456 and even just "password". But passwords aren't the only barriers that protect your information.

If you've ever wanted to start learning to code but haven't known where to start, then one of the best places is with Python. It's great for introductory programmers, and it's also a must-have addition to the repertoire of anyone experienced in the industry. As of 2019, over eight million programmers have used Python, and the industry has only grown since then, so the best time to start practicing is today!

When smartphones were first getting popular, apps were much more limited in scope. Because of that, it was easier to find better programs to do what was needed. Now, in the App Store alone, there are nearly two million apps for you to choose from. When you're just looking for an app that will work well for the task at hand, two million is a lot to sort through.

Linux is a diverse and powerful operating system that virtually every IT professional must learn and know well. Whether you realize it or not, you have likely already used a Linux device, and learning to design things for it is a key step in any Data Science career path.
Safety means something different to everyone, but everyone wants to feel safe. For many, the best way to feel safe is to have something external that offers that sense of security, whether it's an alarm system, a friend on standby, or just something that helps you feel in control.

IT is a competitive field, and finding success requires more than knowledge of a couple of coding languages or knowing how to google really well. To stand out among your peers and competitors, you should learn everything you can and get as much diverse experience as is available.