This article details the step-by-step instructions on how you can make a strawberry tower that can be used for your hydroponics/aquaponics system. The water dripping through the system contains the nutrients, so soil is not used. The growing media is expanded shale, but you could also use expanded clay or gravel.

Solving a Dilemma This is a simple how-to for a cost effective drip irrigation system for your garden. My motivation to set up my garden for drip irrigation was pretty simple. In the summer, it gets to 90+ degrees outside, and my 50’ garden hose didn’t reach the far extents where I have the majority of my large trees. I noticed a large amount of the water I applied to the trees just ran off and did absolutely nothing. This was a huge waste of resources.
How do you review an app that refuses to work for you? I was quite excited this week to review iCinegraph, an iPhone App that simplifies the creation of cinemagraphs. However, if this was a car review it'd be the kind of review where the car under consideration is never able to start (do those reviews even exist?). The reviewer has the keys to the automobile, the interior lights come on, and perhaps there's air conditioning. But, the car itself? Unfortunately, it never moves on its own power.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!
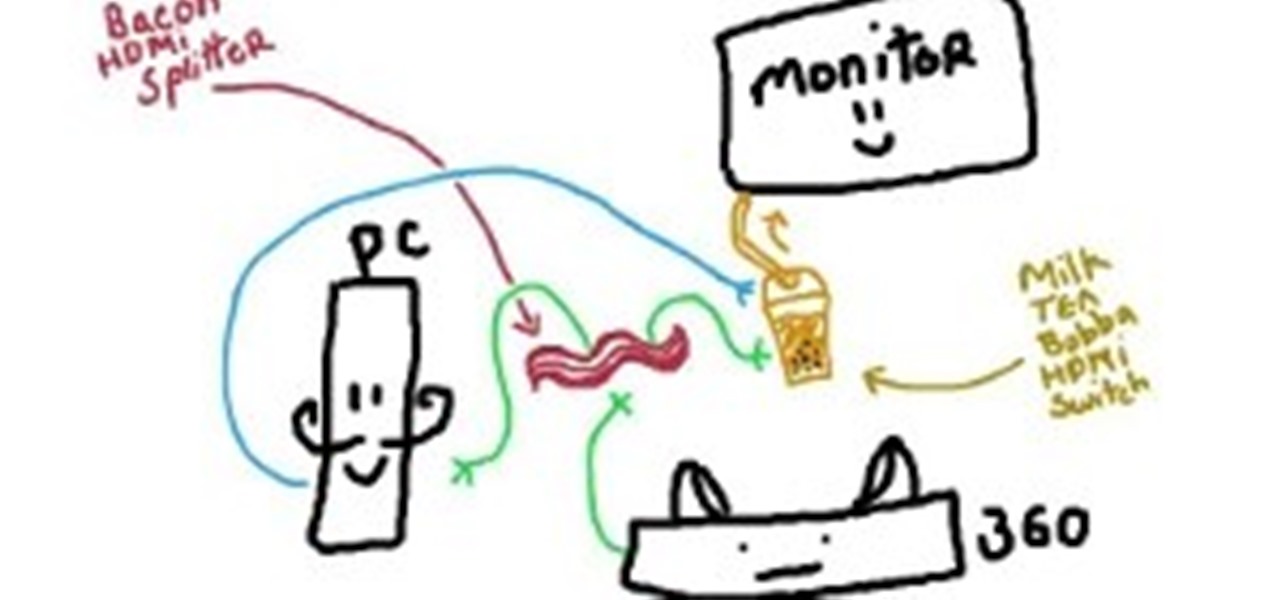
Video capture... how does it work? Apparently, I have no idea. What I thought would be a simple undertaking turned out to be a slow and annoying pain. I just wanted to capture video in high definition and to lessen the time it takes to setup, record, and upload the video.

Making your way into an online community can be really exciting. Some life-long friendships and lasting romances begin in humble chat rooms and message boards. But for the novice internet user, one of the biggest hurdles can be trying to figure out just what people are saying to one another.

Jezebel has compiled 8 user-posed questions that address not just the hair-down-there, but any and all shaving and waxing concerns.

The 2011 Toronto International Scrabble Open (TOSI) took place last weekend, with former World Champion Adam Logan beating out all of the human competition for the $3,000 grand prize. But when it came time to take on the Quackle program in the Human vs. Computer Showdown, he lost his first two games and won the last two, ultimately losing with a measly 28-point differential of the combined total scores. But he still came out three grand happier.

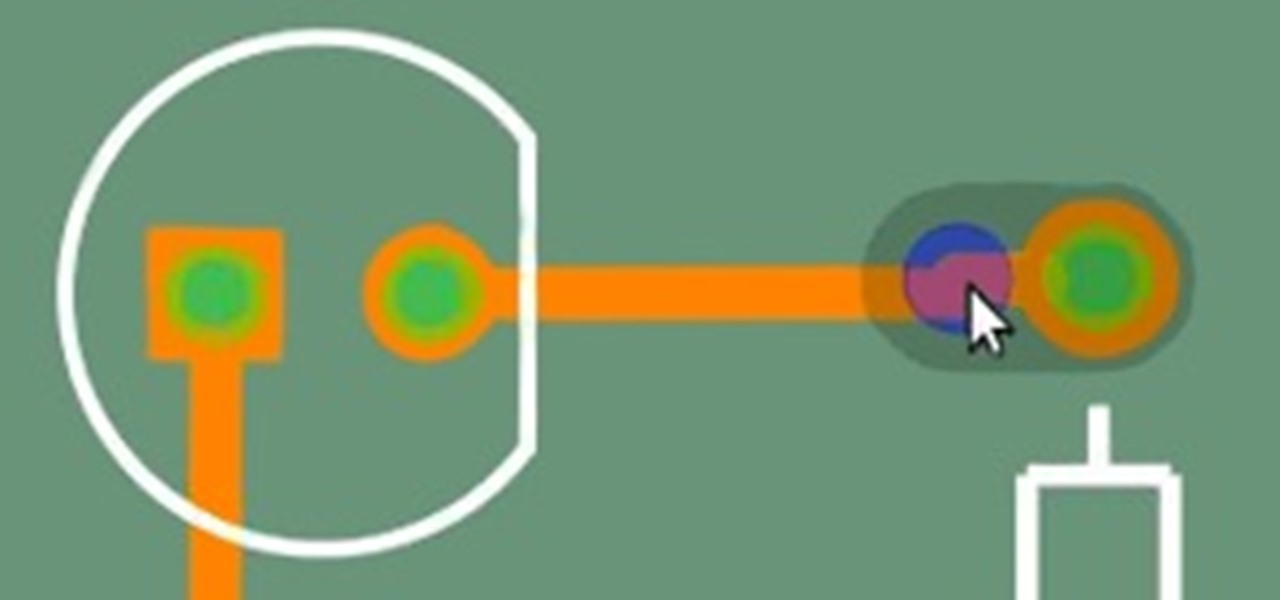
Making your own circuit boards can be a daunting challenge. You have to design a schematic, test it on a breadboard, design the board layout, and then after all of that, you still have to print and etch a board!

Thanks to the advent of smartphones and mobile apps, Scrabble has spread like wildfire across the globe, whether it be Scrabble or one of its many popular word game spinoffs, such as Words with Friends, WordWise and Kalimat.

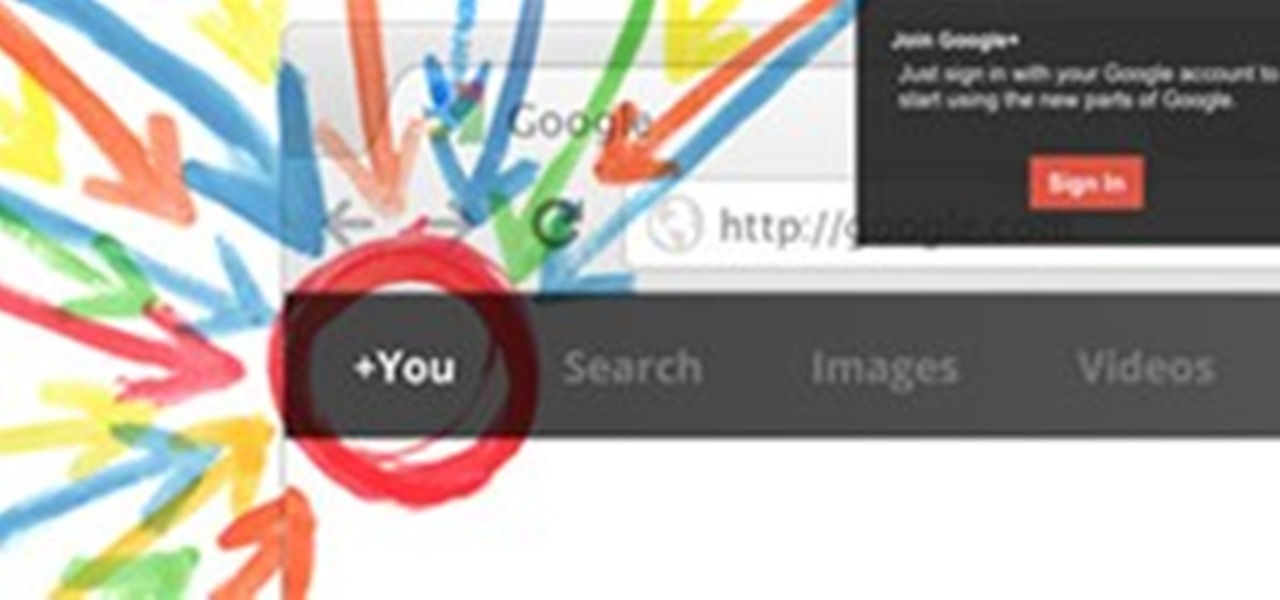
You've finally got an invite into Google+. Now what? At first glance, things can be a bit overwhelming. We've got some great tips to help you get started.

My JO was watching The Simpsons on FOX the other day, like she wholeheartedly does every evening, and I joined her, much like I always do— though I must admit, I'm not as obsessed with the cartoon family as much as she is. Just like she isn't as obsessed with SCRABBLE as I am.