What would it be like to have clothing that killed microbes? Or paper that repelled pathogens? A research team from Rutgers University has developed a prototype out of metalized paper to zap the bad guys without being super expensive. Sound good? Read on.

Are you a foodie? Then chances are that you wear out butcher boards faster than Paris Hilton goes through men. Perfecting your cooking skills is a great thing, but you can definitely preserve your butcher block for longer than you think. Take a look at this video to learn how to clean, sanitize, and seal your butcher block so it lasts for many years.

Glintzy shows viewers how to sanitize all of their makeup products. To do this you will need, a spritz bottle with rubbing alcohol in it and some paper towel. You should always wipe down wherever you put your makeup on with a germ killing spray. Also, always clean the outside of your makeup to make sure this is clean because you are always touching the makeup. Also, don't forget to clean the handles of your brushes. Foundation you cannot sanitize if it does not have a pump so you have to be r...

If you make mead honey wine or are thinking about making some you have to be very conscious of the santization of your equipment. This tutorial looks at how to correctly clean and sanitize your equipment so you have a successful batch of mead.

Looking to give your kitchen a good cleaning this spring? Don't go out and spend a ton of money on sanitizing sprays and cleaning equipment. Cleaning and sanitizing your kitchen is easy, effective, and inexpensive, because everything you need is likely in your kitchen!

This is a demonstration of sanitizing shoes if bought secondhand or before storing. The shoes are first cleaned thoroughly with cloth or soap and water to remove all the dirt and patch marks. If the shoes don't have parts which can spoil if soaked it can be washed in a washer. Once the cleaning is complete it is sprayed with Lysol spray. This works as a disinfectant. Since the shoes are wet with the spray it is left to dry before storing it.

Learn how to discourage the spread of bacterias with this sanitizing tutorial.

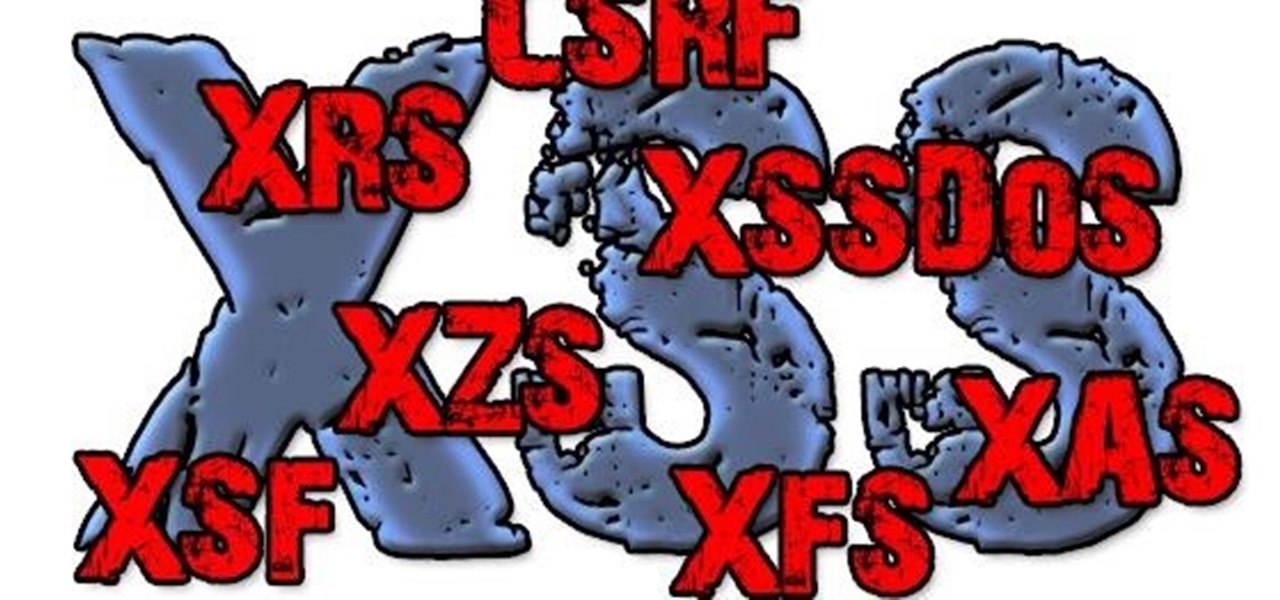
In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

Find out how mouthwash can multitask for you. Use that mouthwash for more than bad breath. Uses include: clean cuts and burns, tone your face, make your own hand sanitizer, banish dandruff, extend flower life, sanitize your toilet, neutralize smelly hands, and prevent underarm odor.

There's nothing like milking a dairy cow straight from the teat. Of course, before milking you'll need to sanitize the teat with a sterile solution and paper towel. This video tutorial demonstrates the proper methods of milking cows using a standard milk machine pulsator for professional results.

In this tutorial, Zephyr Clarke-Dolberg tells us how to handle a stray dog that you find and want to help. Shelters are always a good option for dogs you find on the street, if you cannot keep it. If you decide you can keep your dog, you should make sure to sanitize yourself until you can take it into the vet to get checked out. The vet will also check to see if it has a microchip, so you know if it has an owner. If you can't keep the dog, you can foster it for a couple of weeks, then a human...

In general, this video is approximately one minute and eight seconds long. The host speaks about personal hygiene by using a small packet of antibacterial wipes. She generalizes the use of this product, which includes hand sanitation, cleanup, and emergency antibacterial use. She specifically speaks about deodorizing the underarms. She relates to the audience about forgetting to use deodorant and how using the antibacterial wipes will help fight bacterial body odor, but clearly states it won'...

Life stinks. Literally. Daily living leads to lots of lingering smells. Household odors from cooking, kids, pets, bathrooms, and guests can accumulate. Get rid of them with some simple remedies.

Salt is one of my favorite ingredients, by far, and also one of the most overlooked foods in the kitchen. This is probably due to the fact that it's an essential component of almost any recipe; because salt is a necessity, it's easy to forget how dynamic and versatile it can be as well.

You just sat down, coffee in hand, and the day is ready to start. Now that you have taken a few sips, let me pose a question: What is living in that coffeemaker of yours? The answer might make you dump that coffee down the drain pronto.

Acetone-based nail polish remover is great for removing nail polish, and it's also great for some DIY uses around the home. From eliminating scratches to fixing the consistency of correction fluid, its uses are varied but all effective. With nail polish remover, you can also clean your computer keyboard, get rid of ink stains, and even remove leeches from your skin. Talk about versatile!

Maintaining a clean living space is important, but it shouldn't have to be a hassle. The KAPSULE™ UV Sanitizing Wand 2.0 is designed to keep surfaces pathogen-free. This powerful wand emits 254nm UV-C light and makes quick work of pathogens. In a laboratory test, KAPSULE even eliminated more than 99% of E-coli!

Early in the morning, there's almost nothing worse than discovering your razor is dull midway through your pre-work routine. No matter how hard you try to preserve those precious blades, it can seem like they're dull every time you reach for the razor. With one, seconds-long step after each use, you can save your razor blades and make them last longer.

Both professional and home cooks have been rinsing raw chicken and turkey before cooking it for what seems like forever. It's one of those divisive practices—either you do it or you don't, and people tend to be rather opinionated on their stances.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

What's good, peeps? I've been noticing some rather advanced tutorials slowly emerging here on Null Byte and I know that people want more of them but I've been reluctant to post something of such caliber because I fear that the information will just go over their heads, but hey, as long as it's there, people can always go off to research themselves and eventually understand. So here is my contribution to the gradual and inevitable progression of Null Byte!

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Stop! Do not pour that leftover wine, coffee, or bacon grease down the drain. And those herbs that have been in your fridge so long they've literally turned on you? And what about when that recipe only calls for two tablespoons of heavy cream, a quarter cup of tomato purée, or three cloves of garlic? Unless you plan on using the leftovers again in the next week or so, don't bother refrigerating them because they won't last.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

In this video series, learn how to apply fiberglass nails. Once you have gotten your manicure, fiberglass nail application is easy and painless. There are many benefits to fiberglass nails as well. They strength your natural nails, and they protect your nails as well. Learn how to sanitize your nails and hands. Our expert, Valda Sarty, shows you how to trim, glue, and etch your fake nails. Also, learn how to buff and polish fiberglass nails.

A butcher block table (or counter) is a solid, wooden table. Originating in butcher shops (hence the name), this has become a popular household item. Butcher block tables and counters are durable and attractive looking. The downside of butcher block is that the wood is so porous it can stain easily. Butcher block can be sanded and refinished to get rid of stains, but that drastic step isn't always necessary.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

Commonly associated with cleaning and disinfecting items around the home, bleach can also be used as a water sterilization method in an emergency situation when you do not have access to clean, running water. Simply add 6 drops of bleach to a gallon of water and wait for 30 minutes before drinking.

BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.

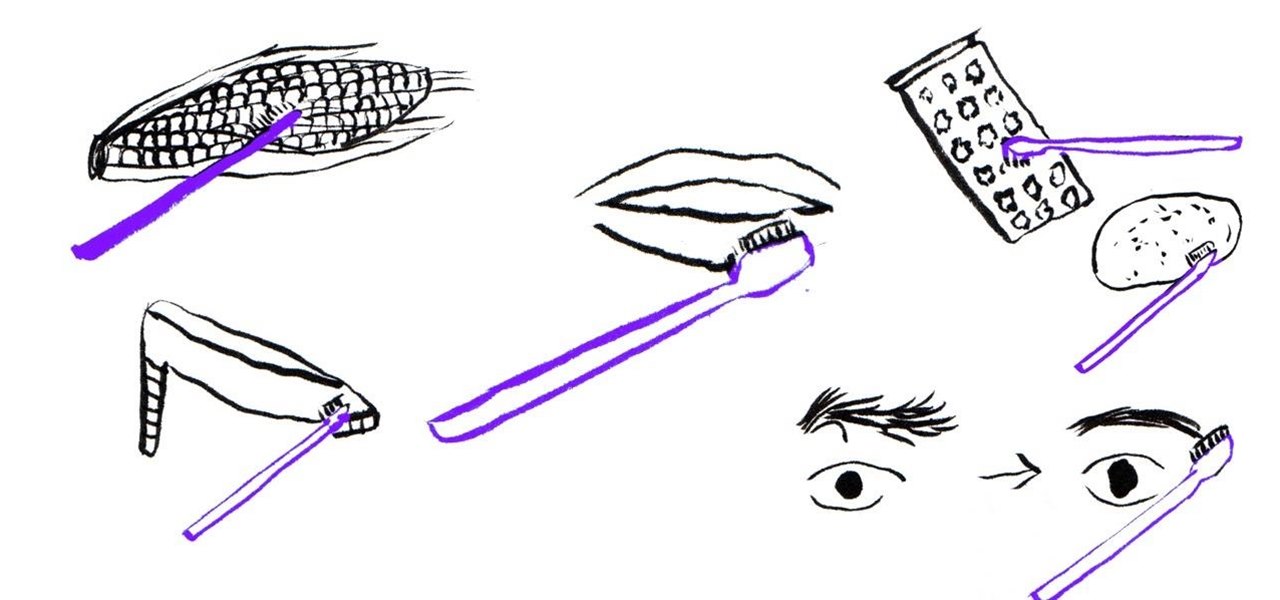
We all know to should swap out our toothbrushes one every three to four months, but did you know your used Toothbrush still has a number of handy uses once its time in your bathroom is done? You can use an old toothbrush indefinitely to remove silk from corn, exfoliate your lips, tame your unruly eyebrows or clean your cheese grater before sticking it in the dishwasher.