Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

There's a lot more to your iPhone's dialer screen than just entering phone numbers and hitting the green call button. It's not very obvious, but there are secret codes that you can enter on the dialer to find out information about your device, help troubleshoot issues, and mask outgoing calls, to name just a few things.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

A powered-off Windows 10 laptop can be compromised in less than three minutes. With just a few keystrokes, it's possible for a hacker to remove all antivirus software, create a backdoor, and capture webcam images and passwords, among other highly sensitive personal data.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

The iPhone X was released in November 2017, and the iPhone 8 and 8 Plus dropped right before it, but the hottest news right now revolves around the 2018 iPhone releases. The rumor mill regarding the iPhone X's successor started churning out speculations on names, cameras, display size, and more almost immediately after last year's devices, and there have been many new leaked details since.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

One of the most popular usages of modern-day smartphones is listening to music. It doesn't matter if you download or stream your tunes, you are part of a massive group of users who do exactly the same. While statistics are a bit foggy on how many smartphones users download music, we do know that over 68% of American smartphone owners stream music on a daily basis.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

HBO GO is quickly gaining ground on Netflix as a must streaming service for our wireless devices. Especially since it's the only way you can watch TV shows like Boardwalk Empire, Game of Thrones, and Veep, since Netflix and Google Play do not offer them, and there is no Android app for Android Instant Video playback.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

Still on the fence about Apple's native Notes app? The latest Notes update for iPhone, iPad, and Mac is about to change your mind. With some fantastic new features and plenty of valuable tools from previous software versions, Notes is becoming a clear winner when it comes to saving important information from your personal and professional life.

Apple has finally given Control Center the love that it needs with an updated interface design and more customizations than ever before. Taking the more customizable overhaul one step further, iOS 18 and iPadOS 18 have elevated controls beyond Control Center, so you can use controls from other places on your iPhone or iPad for even faster access to your most-used shortcuts.

Things just got a lot better in your iPhone's Messages app, and the most significant change lets you text Android users with iMessage-like features such as typing indicators, read receipts, large file sharing, high-quality photos and videos, and even emoji reactions.

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.

You probably know of Apple's Text Replacement feature for iOS, iPadOS, and macOS, but you're probably not using it as much as you should. With it, you can create your own keyboard triggers for almost anything you can think of, whether it's an email address or an entire email. There are endless reasons to create custom text replacements — and we'll show you why.

Apple's TV app for iPhone didn't get any new features with the iOS 17.1 software update, but iOS 17.2 is a totally different story. There are big changes to playback controls, your channels, store content, and more.

Visual Voicemail revolutionized phone calls and the voicemail system when Apple introduced it with the original iPhone. Now, thanks to iOS 17, Apple has done it again with its newest calling feature, Live Voicemail. This feature uses speech-to-text technology to show you voicemail transcriptions on the incoming call screen in real time, helping you decide if it's important enough to answer the call.

Many of the iPhone 15, 15 Plus, 15 Pro, and 15 Pro Max features were carried over from last year's models. Still, quite a few capabilities are exclusive to the 2023 lineup, and some may be worth the upgrade.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

Your iPhone's Health app has a new medications hub that can be a one-stop destination for all the medicine, vitamins, and supplements you're taking. Adding new entries is easy and well worth the effort to get reminders to take your meds, learn about drug interactions, easily share your routine, and track your history to see what is and isn't working for you.

Some phone lines make it nearly impossible to get past the busy tone, whether it's a viral call-in giveaway, your state's unemployment office, your local post office during the holidays, or the repair office for a broken warrantied product you have. Thankfully, there are apps you can use to help break through the noise.

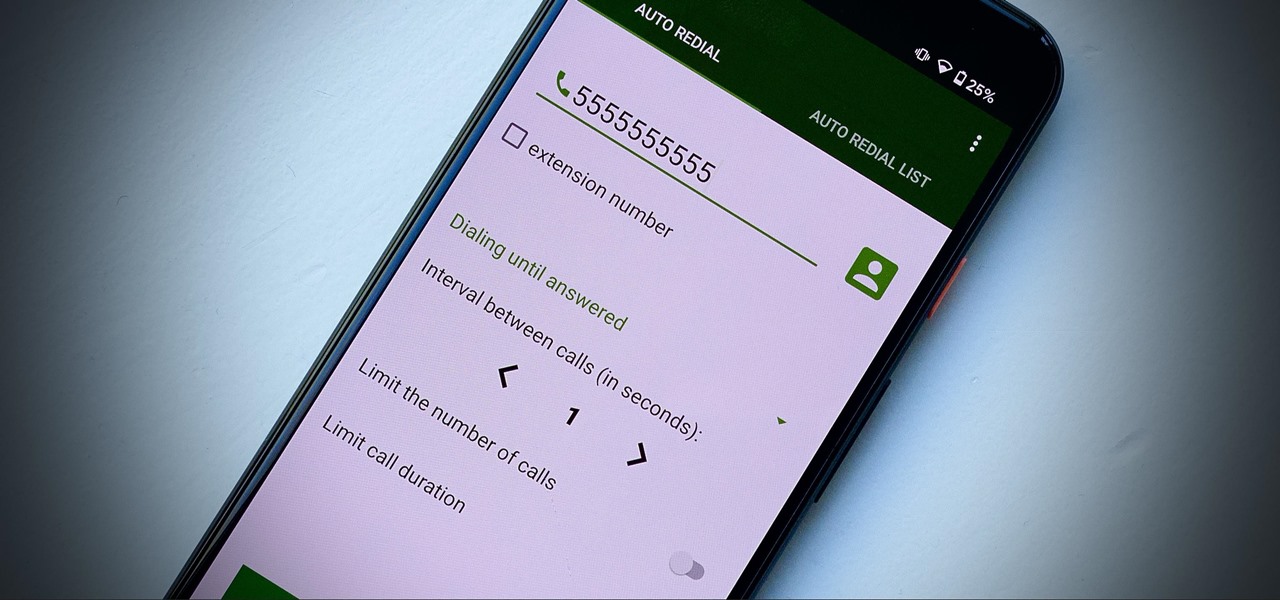
Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Google and Snap held their annual conferences this week, and both companies managed to upstage their new AR software features with fantastic new AR hardware.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Despite making great phones for years, Sony continues to struggle to penetrate the US market. Sales volume has fallen year after year, with 2019 limited to only 5 million units sold globally. To help alleviate this drop, last year, Sony released the Xperia 5, the return to compact smartphones. This year, rumors indicate a sequel is first on their agenda.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.