HTC is one of the few OEMs that make it easy to unlock the bootloader on their devices. And while they do warn you that doing so voids your warranty, they don't tell you that it also prevents you from collecting promotions that come with their devices.

While the legality of recording phone conversations varies from state to state, it's still a sought-after feature for most people. How else are we going to shame all of those bad Comcast customer service reps? Since it's a legal gray area, HTC and other smartphone manufacturers have omitted call recording capabilities from their devices.

Even if your business is mostly online and computer related you will need paper, which in other hand will need classifier to be sorted out and easily accessed. The paperless office is as much of a myth as the paperless toilet, so accept it, if you are serious about business, you need paper. Important contracts between customers signed on papers, leaflets, reminders, advert previews, drafts for preview at the table. The paper is always used even in today highly computerized epoch.

So, you want to cause a little mischief, do you? Here are six super-easy pranks to help you make the most out of April Fool's Day (or pretty much any other day of the year). There's something here for everyone—TV fiends, magic trick lovers, fruitoholics, and even spam companies.
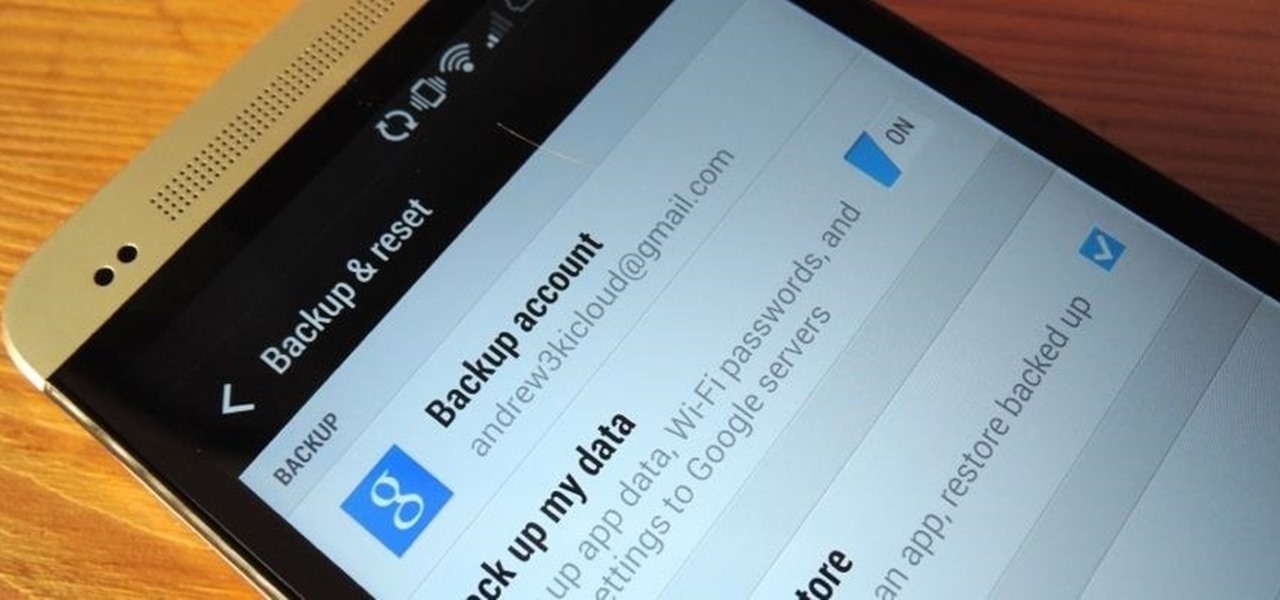
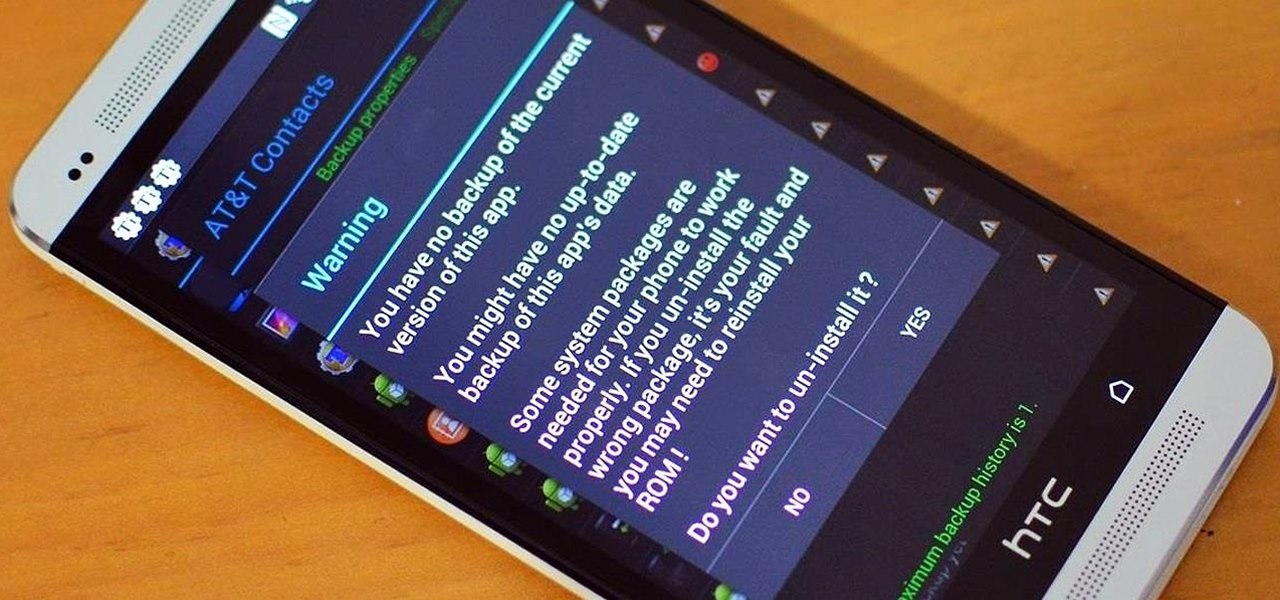
If you are using the the AT&T variant of the HTC One, you are well aware that the carrier opted not have the HTC Backup app pre-installed on the device. Luckily for us, HTC said "screw it" and put the app on Google Play, allowing anyone with an HTC One, regardless of carrier, to be able to download and use the app—if you're an AT&T customer, grab the app and let's take a quick walkthrough (again, the rest of us on other carriers should have the app already).

Android 4.4 KitKat has begun rolling out for the Galaxy Note 3 in India, Poland, Russia, Switzerland, and several other countries, and an unofficial build for AT&T customers has been leaked for all of us stateside.

Starbucks' app is the most used mobile payment app in the U.S. because it's well-designed and convenient. But if you use the iOS version on your iPhone, your username, email address, password and location data could be compromised because the app stores them in plain text.

Via Twitter, HTC, the Taiwanese device manufacturer, announced today that their barely 18 month old flagship phones will not see official updates for anything past Jellybean. HTC went on to elaborate, saying:

The possibility of the Sriracha factory in Irwindale, CA being shut down was one of the biggest food stories of 2013. Huy Fong Foods was almost forced to close the plant due to complaints about the factory's smell, but luckily the brand emerged triumphant.

I've been a Sprint customer for a long time. Normally, Sprint (flagship) phones come with some useful apps, such as Sprint TV, Sprint Zone (for payments, updating PRLs, and account information), and NBA Game Time. In other words, relatively free of bloat.

The Pro Bowl has definitely had its ups and downs. It's probably the most glorified exhibition game on earth. I mean, even the NFL Commissioner, Roger Goodell, wanted to cancel it this year.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

Christopher Nolan's Batman trilogy has been one of the most successful film series of all time, so it comes as no surprise that everyone wants their own real-life versions of the Dark Knight's gadgets and vehicles.

Yesterday, Microsoft released the customer preview of its newest version of Office, the first version optimized for both touchscreens and desktop systems. The entire suite got a much-needed facelift and a few new cool features. Here are some of the most notable changes.

In this lesson we will learn about one of the most important concepts in algebra SQUARE ROOTS. The square root of a number m is another number n that satisfies the following formula: m = n x n. You can also say that m is the square of n. The opposite of squaring a number is finding its square root. You can use the radical symbol to indicate that the square root of m is n:

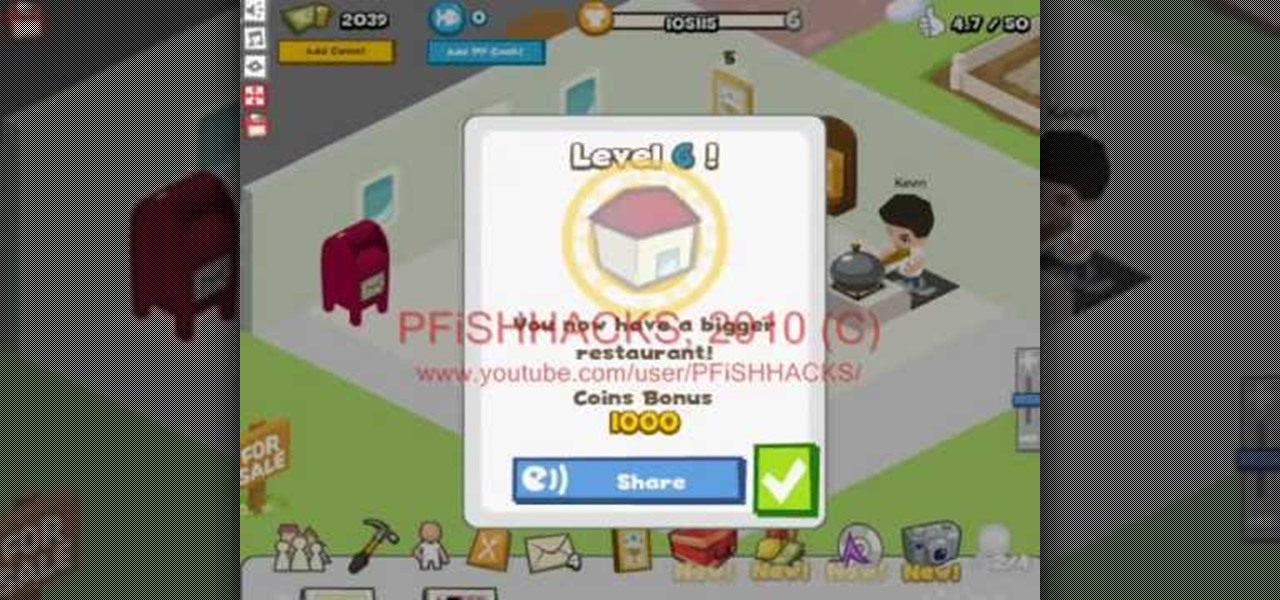
Open up Cheat Engine and be prepared to hack Restaurant City! This is a new level hack that will help you gain levels fast.

If you are looking to sell a lot on eBay, while maintaining satisfaction and product integrity then you are in prime position to be an eBay PowerSeller. As long as you stay within the bounds of the requirements, you can hold this particular title.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

Due to the apparent lackluster adoption of its Explorer Edition, it can be easy to forget that Google Glass still exists as an enterprise product.

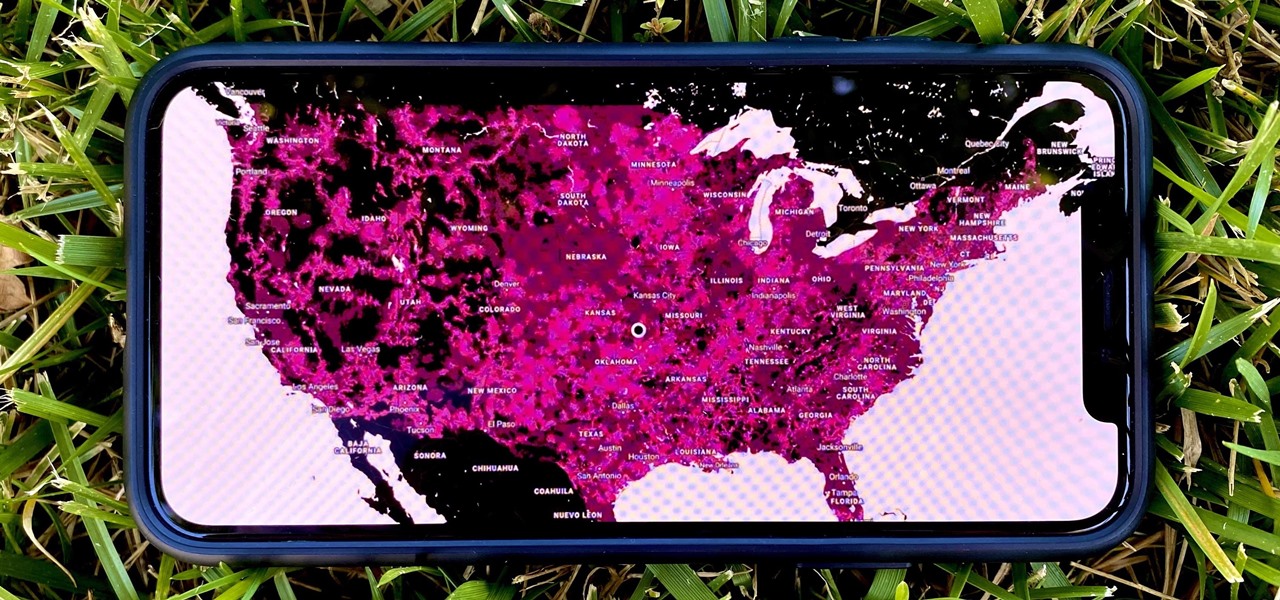
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

The long wait is over — the best augmented reality device on the planet is finally available.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

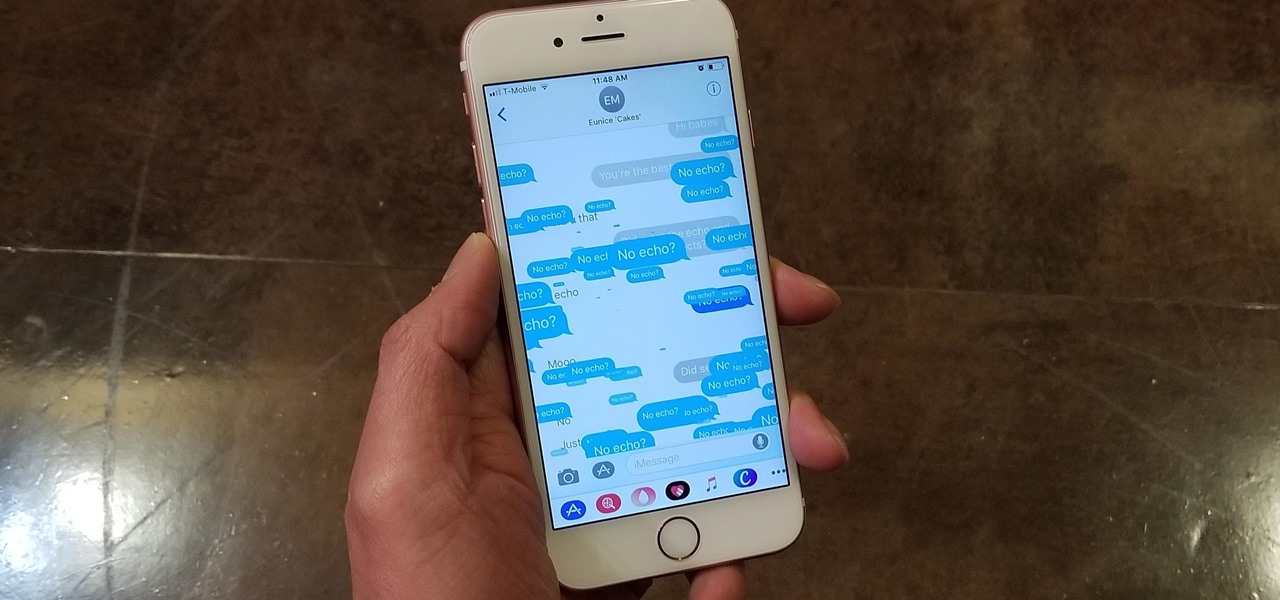
Apple gave the Messages app a massive makeover with iOS 10, with a slew of options that made iMessages on the iPhone a lot more fun. While not quite as comprehensive, iOS 11 builds upon that success and makes the app more user-friendly and all-inclusive.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

Yes, I know it's autumn and the trees are losing their leaves, but the seasons do not decide when I can or cannot enjoy ice cream. No matter how warm or cold is is outside right now, I will remain completely fascinated by rolled ice cream. Yes, rolled.

The yogis of the internet have started a wonderful food trend that has everyone wanting to eat healthy—gorgeous buddha bowls. Okay, so maybe not everyone, but a lot of people are definitely entranced by these beautiful, multicolored meals.

My husband's and my daily schedules are constantly changing. Frankly, it's complete chaos sometimes, so I can't plan to have elaborate dinners on the table at six o'clock every day. And by the time we actually get to eating in the evening, we've become so hungry that our moods have taken a nosedive.

With Passover soon upon us, many Jews are dreading a week (or eight days for Conservative and Orthodox Jews) of making matzo, the staple of their diet. Matzo is also known as "the bread of affliction," and I'm pretty sure it's because by day three or so you're convinced that matzo is the 11th plague.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

As our lives grow busier, we get secluded in our indoor activities, consuming all types of fatty junk food and what not. Obesity is a very obvious yet unfortunate outcome of our unhealthy living standards. With it comes the predictable rush towards efforts to lose weight. Consequently, we have designed hundreds if not thousands of ways to lose fat and grow slimmer. To ease out your choice of ways, here is a list of the best ways to lose stomach fat. Step 1: Don't Eat Sugar

We've all been there. You can't decide what you want to eat and, even more confusingly, you want two distinctly different things, whether it's sweet and salty, Chinese and, well, cheese. Chances are when you're in this state of indecision, you also want to make this mythically satisfying meal really, really fast.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

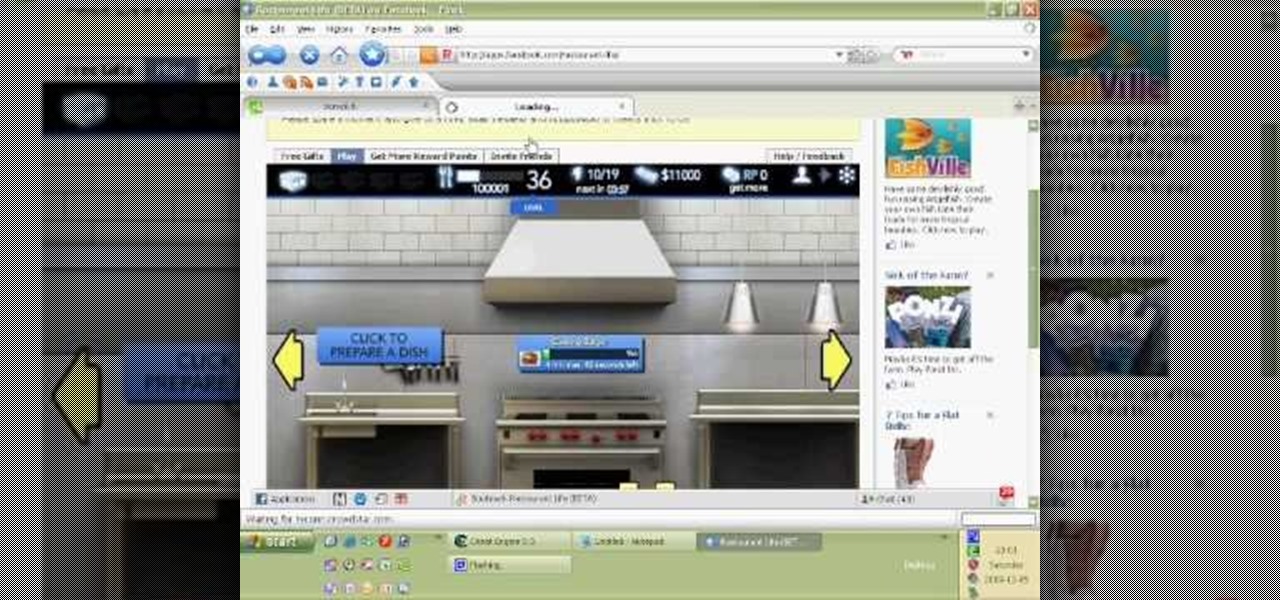
Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).

Watch this video tutorial to learn how to level hack Restaurant Life (12/05/09). 1. Open RL and Cheat Engine 5.5, then point CE 5.5 to the process of your browser.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

We don't mean to alarm you, but we may have just found the coolest charger in the world. The Mopoint World's Smallest 65W GaN PD Charger offers fast and simultaneous charging, and it just happens to be on sale right now for 14% off, costing just $42.99 (regular price $49).