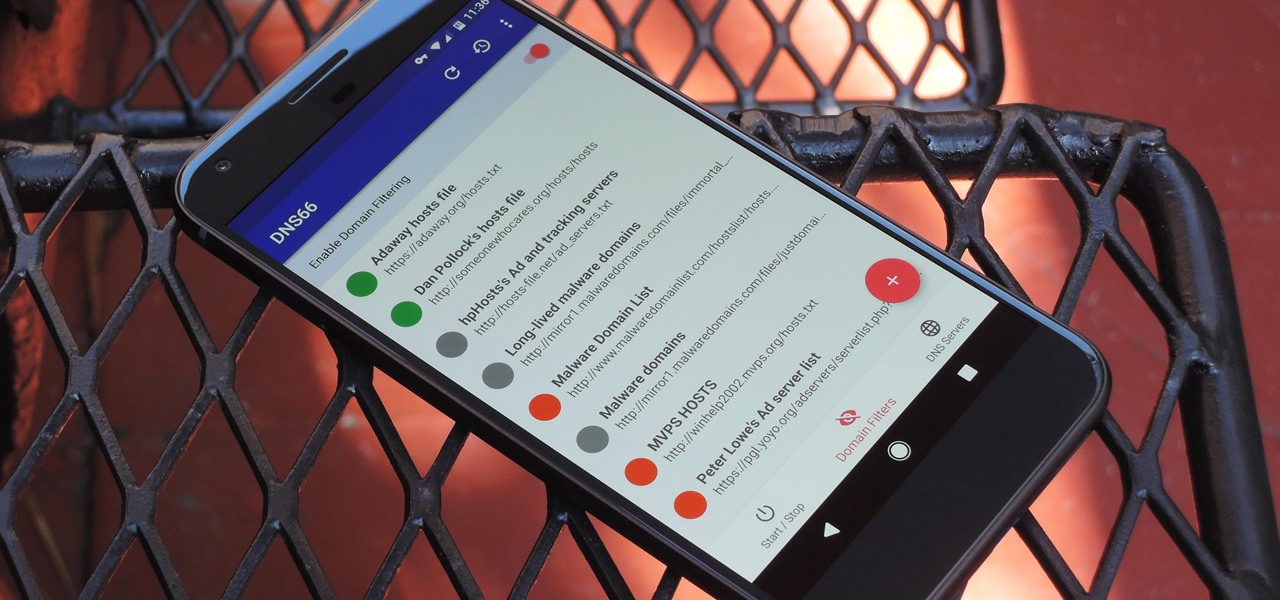
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

When your day sucks, all you want is a tall, ice-cold glass of beer at the end of it all. Nothing complicated about having some booze to temporarily drown your sorrows.

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.
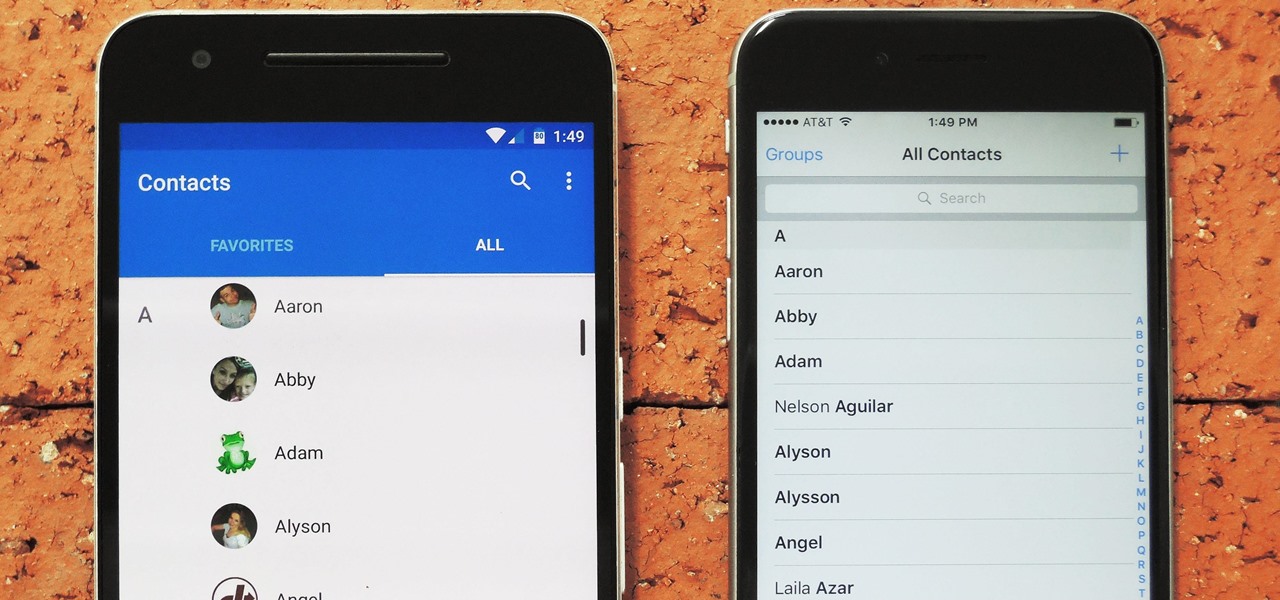
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.
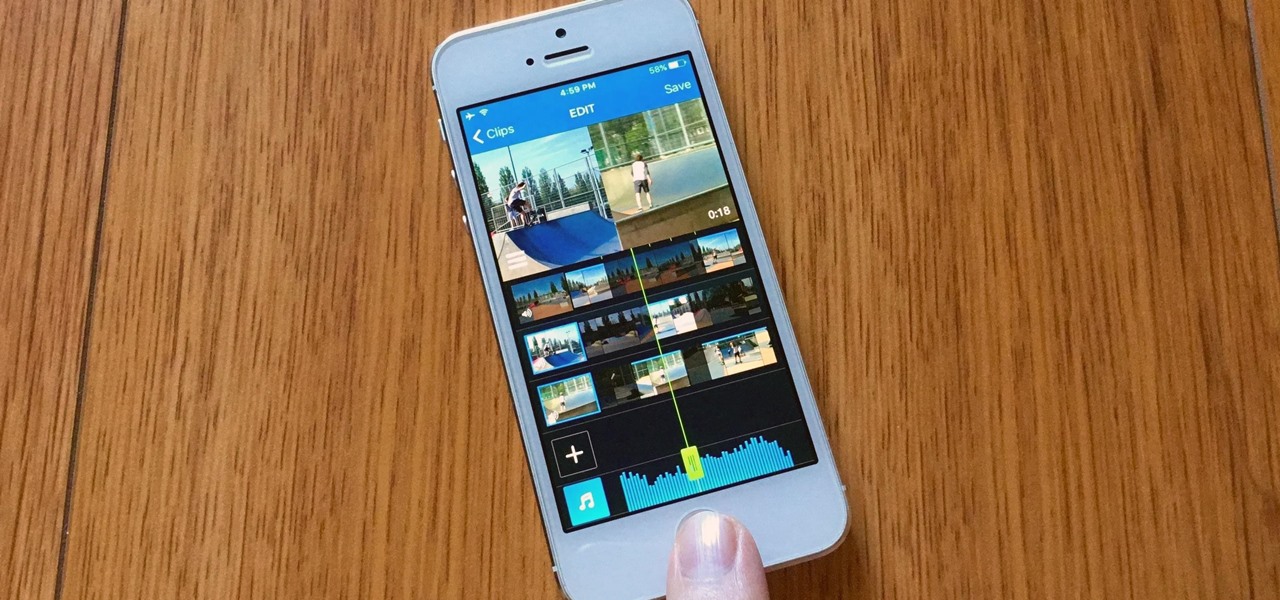
Let's say you're with friends at a sporting event, music festival, lounge, or some other fun venue, and you want to create a fun split-screen compilation from all the videos you took independently. It's not an easy task, because someone has to get all the video footage and then use a video-editing program that supports split screens. It's a daunting task most people will just skip.

For the most part, when you take a screenshot, it's because you intend on sharing it with someone. And, of course, we all take pride in our smartphones, so we want to show them off as much as possible. But the downside here is that regular screenshots are pretty boring, so they don't do a great job of showing anything off, really.

Bread doesn't have a long shelf life, as most of you probably know quite well from firsthand. You get it home from the store and before you know it, the loaf has turned from soft and perfectly pliable to hard and crumbly—and maybe even moldy! So what's the best way to keep your bread from going bad before you've finished off every delicious slice? Put it in your freezer. It's a simple solution that you've probably heard many times before, but one you probably don't use very often because you ...

We used to saunter into the grocery store and gaze longingly at the pre-made roasted chickens, wistfully thinking of things we could do with the golden fowl if only we didn't already have dinner plans.

I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audiobooks.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage into one you actually want to drink.

Samsung's latest flagship devices—the Galaxy S7 and S7 edge—both sport an interesting new feature called Always On Display, or simply AOD. When enabled, this feature keeps the clock, date, and other bits of information visible at all times—even when the screen is off.

Frozen meat is a saving grace for weeknight meals. Whenever I crave a certain protein, all I need to do is defrost it. Sometimes, I don't even need to defrost it in order to use it.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

Winter is already here, and when Jack Frost is nipping at your nose, he tends to nip on your wallet, too.

BlackBerry has yet to find a home amongst the iPhone and popular Android phones, with sales plummeting over the last couple years, but this might be a thing of the past thanks to their latest device, the BlackBerry Priv. It has decent numbers so far and was even sold out on Amazon shortly after its initial release.

Hearthstone is a collectible card game by world-class developer Blizzard Entertainment. It has taken an entire generation of casual and professional gamers alike by storm. So many people play it, chances are you've already sunk some money into it. So, if you're going to pay a little anyway, you may as well get a discount.

I love making everything from scratch, but some things are just easier to buy. So there are times when you have to find a creative way to split the difference. For me, the easiest dish to buy without compromising on flavor is cornbread mix.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

In this article, we will explore the basics of radare2, a powerful package that comes with Kali. We are going to write a simple program, and then disassemble it, to see what is really doing in the processor.

Manufacturers like Samsung and LG have added their own implementation of multi-window features to Android for years now, but with the release of version 6.0 Marshmallow, Google has finally gotten around to working the same feature into stock Android.

If there's one thing that gets used far too frequently in the modern kitchen, it's the trash can. Home cooks everywhere waste enormous amounts of food by throwing it away before it's actually ready to be tossed.

The standard way to make pasta requires a lot of water, and it takes a long time for that big pot of water to actually start boiling. For these reasons, as well as my hatred for washing large pots, I don't cook pasta at home very often—at least not the traditional way.

If your iPhone can't last a full day without being recharged multiple times, something's wrong—but it might just be working harder than it needs to.

Convenience in the kitchen can be a very, very good thing. As fun as it can be to spend hours toiling over Julia Child's boeuf bourguignon, there's a reason that we have canned soup, microwave dinners, bouillon cubes, and, of course, boxed mixes.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Just recently, I was experimenting with a dual-boot Windows setup, and somehow managed to wipe my primary Windows installation in the process. "Why," I asked myself, "Why didn't I make a backup before I started this?" Still to this day, I'm going through the painstaking process of installing and configuring all of my favorite programs, and I may not ever get things back exactly the way they were.

When I finally saved up some cash and got my first good chef's knife, I vowed to do everything by the book: clean it properly, hone it regularly, sharpen it faithfully, stand by it in sickness and in health, blah blah blabbity blah.

A lot of people like to trash stand mixers for being overpriced and rarely used kitchen appliances. As an avid bread baker I certainly don't agree with that assessment, but I understand where people are coming from. A good Kitchen Aid stand mixer costs a few hundred dollars, and if you only occasionally bake, you probably don't use it much, and therefore aren't getting your money's worth. But what most people don't know is that stand mixers are one of the most versatile appliances in the kitc...

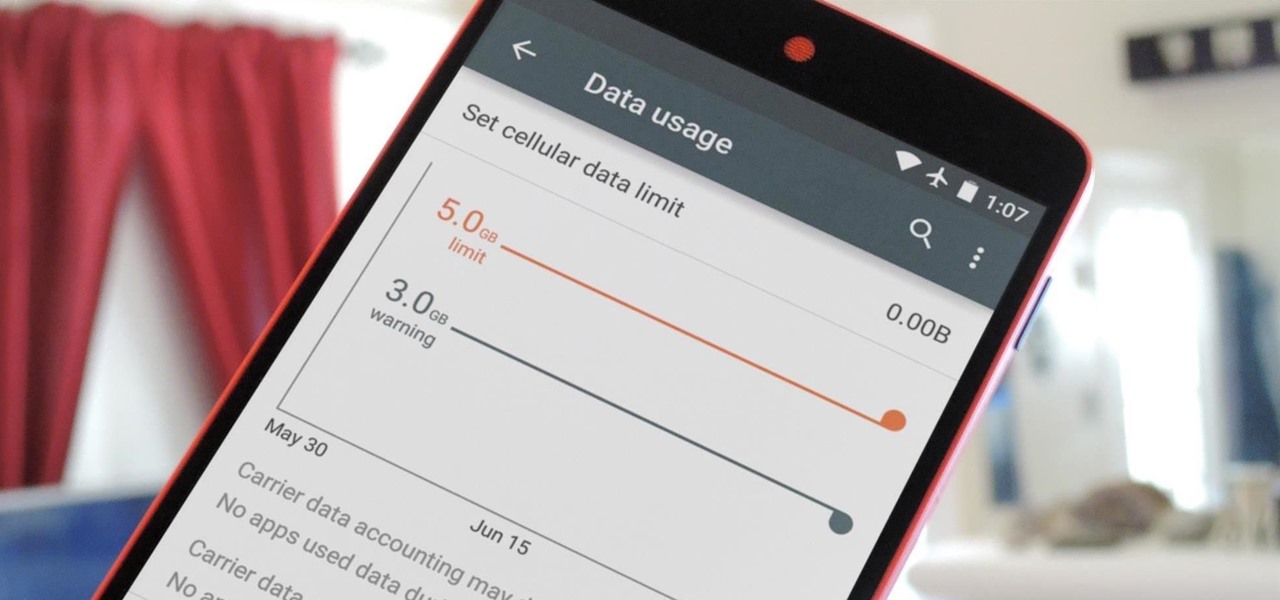
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.

There are certain ingredients that chefs regularly use to elevate their food beyond the status of what us mere mortals can create. Shallots are one. Good, real Parmesan cheese is another. And the rind of that real Parmesan cheese just so happens to be one of the culinary world's biggest kept secrets.

Oatmeal isn't the most glamorous breakfast, but it's definitely one of the best. It's healthy, filling, delicious, and easy to personalize. And, if you have instant packets, oatmeal is also a very quick and easy breakfast.