
How To: Play Charades
Charades is a word-guessing game that's acted out in pantomime by players at parties or other gatherings.


Charades is a word-guessing game that's acted out in pantomime by players at parties or other gatherings.

Help yourself win that must-have item with these tips. You Will Need: a computer with internet access, money, & patience. Create an account. Browse the categories to familiarize yourself with the site, especially if you don’t have a specific item in mind. If you know what you want, start searching by using broad terms and synonyms to yield the most results. Add quotes around your search terms or qualifiers, such as a specific color or size, to narrow the field. You can also post on the “Want ...

You can't use social media these days without running into stories. They're simply everywhere. If you're an avid Facebook Messenger user, you know that you can view your friend's Facebook and Messenger stories at the top of your Chats list. However, a new Messenger feature puts yours and other people's stories inline for chats.
Amazon Web Service's do-it-yourself tool for building augmented reality experiences and VR has graduated from beta and is now available to all interested users.

While certainly faster than writing by hand, manually typing passages from a book or document can be slow and frustrating. But thanks to Google Assistant, this is no longer the case. Whether you need to quote text for an essay or need to win an online argument, all you need to do is point your phone's camera at the paper and tap a few times.

If you're playing word association with the terms "augmented reality" and "automobiles," your first thoughts probably center on navigation displays in cars or virtual models of exotic vehicles.
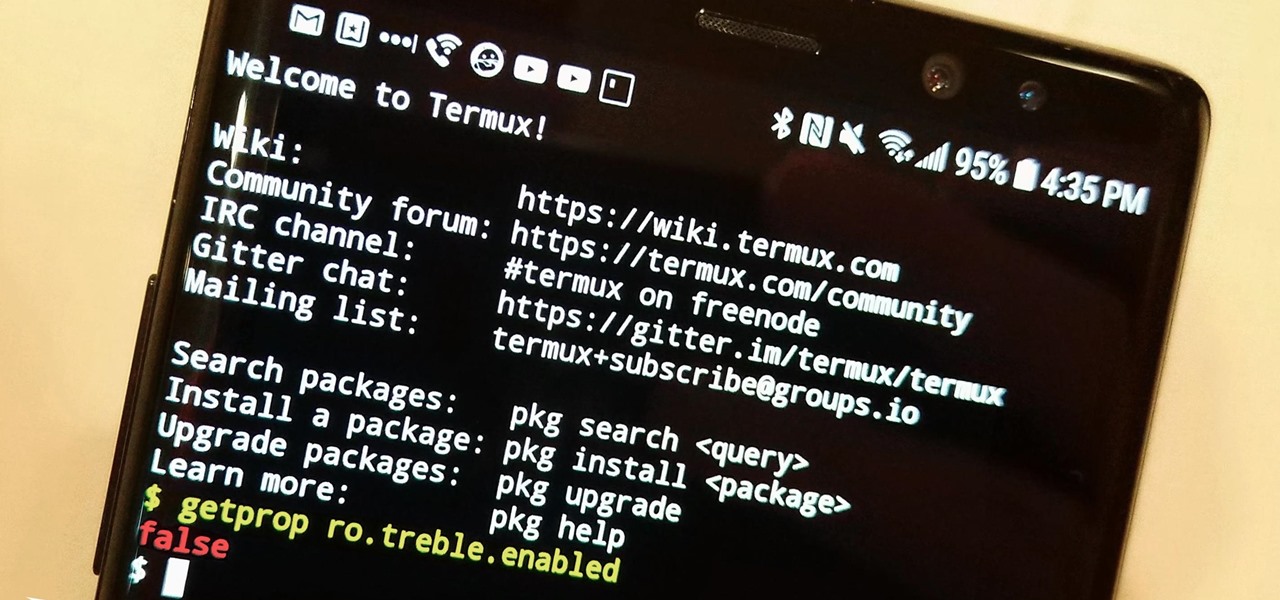
The Oreo beta updates for the S8 and Note 8 have been avilable for some time now. If you're interested in running Oreo on your Galaxy Note 8, you can check out our guide on how to do so. As we dig deeper into the updates, one question on the minds of Galaxy fans is whether or not the Oreo update will support Project Treble. Today, it appears we have an answer.

You can retweet on Twitter, and you can reblog on Tumblr, but you cannot regram on Instagram. Until now, that is. For years, third-party apps have made it their business to help Instagram users share content from other users. With some new developments, Instagram looks to render those apps obsolete by adding a native regram button to the official Instagram application.

This week, Samsung officially kicked off the Oreo Beta Program for the Galaxy S8 and S8+ in North America and several other markets. The full list of changes is quite substantial, so we'll be running through them in a series of posts detailing what's new. First up, the Galaxy phones inherit notification channels from Android 8.0.

Google's YouTube Red is an awesome service, particularly in the United States where it comes bundled with a subscription to Google Play Music. You don't have to worry about ever seeing ads again on any videos, you can continue playback after you exit the YouTube app or even when you turn your screen off, you can download videos for offline playback, and you'll have access to YouTube Music.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.
Windows 10 universal apps are actually pretty awesome—regardless of if you're using a desktop, laptop, tablet, or convertible, the same app automatically scales up or down to suit your device. Definitely cool, but the Windows Store is pretty bare-bones as it stands, so the downside is that you can't always find a good universal app for every purpose.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Hackers are claiming money for a security flaw in Apple's new update. Quick Summary:
Ah, the fabled dark mode. In the past, many users were delighted to find the existence of something called Royale Noir, a dark theme option that was available for Windows XP. Yet for reasons unknown, Microsoft had kept knowledge of Royale Noir a secret until some bright minds discovered its existence, and the rest is history.
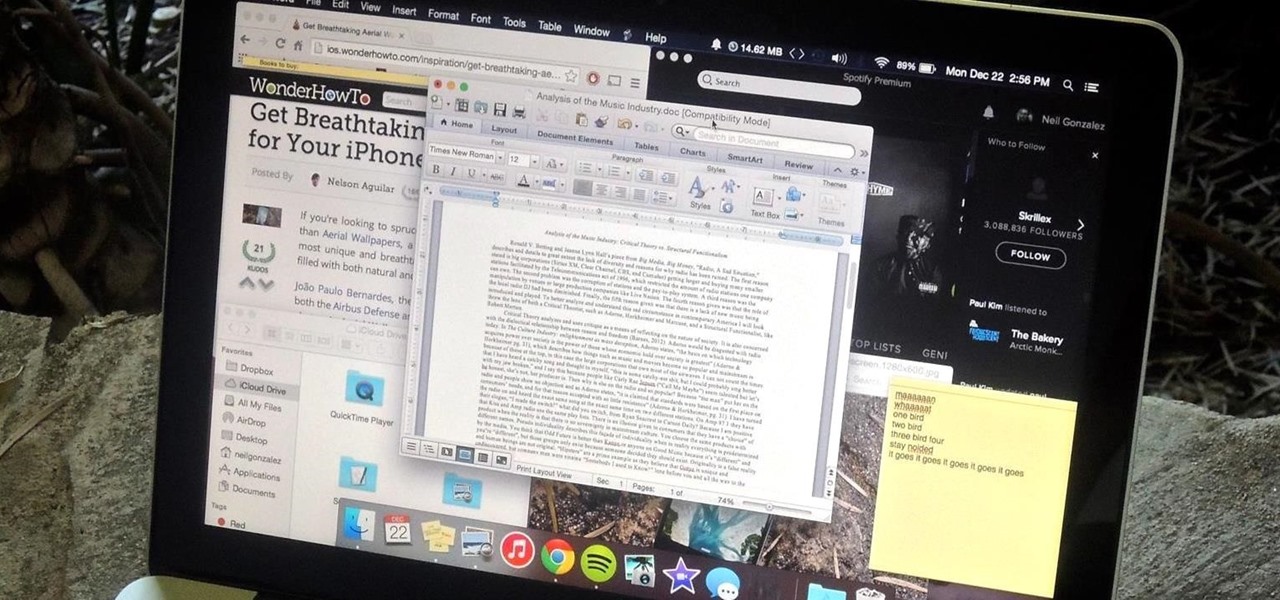
To contemporize a popular quote, "A cluttered desk(top) is a sign of a cluttered mind." Of course, it's difficult to maintain a tidy desktop... as you read this, mine is cluttered with screenshots, folders, Word documents, videos, pictures, and apps.
A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Copy and paste keyboard shortcuts are beautiful gifts from the gods, and any website that blocks such an offering can burn in hell. But really, Cmd+C and Cmd+V (Ctrl+C and Ctrl+V for Windows folks) are second nature to most of us, so it's very frustrating when sites like PayPal don't let us use them.
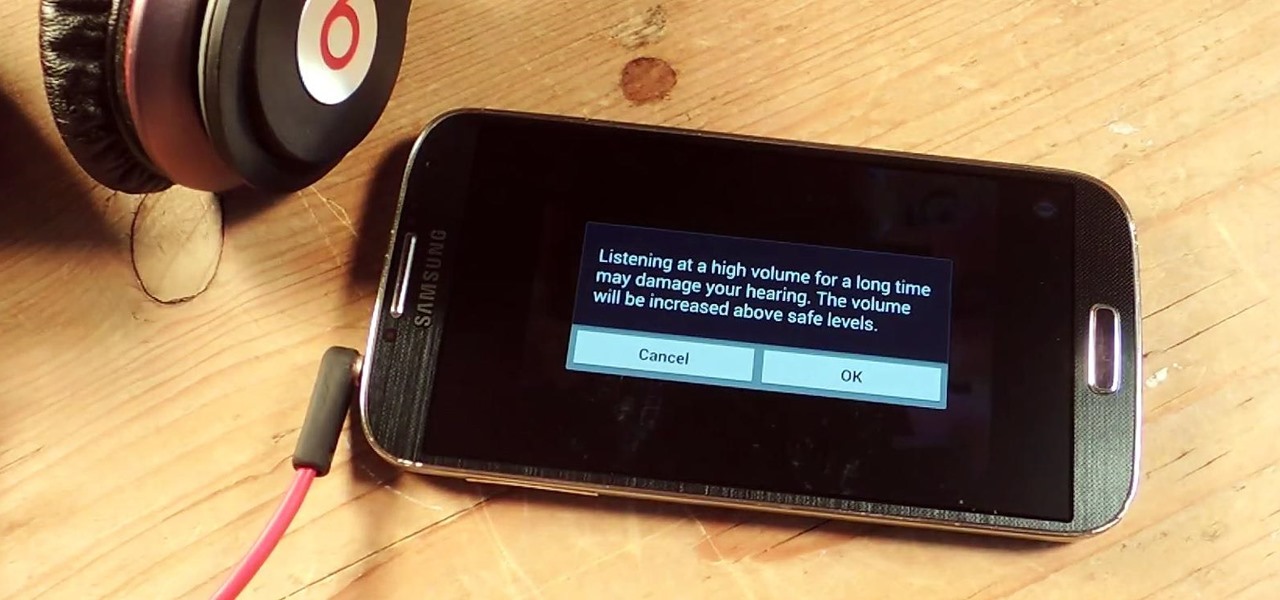
I've been told numerous times that I listen to music way too loud, to the point of potential hearing damage, especially when I have my headphones plugged in. Not only do my friends tell me this, but my Samsung Galaxy S4 likes to nag me as well. Once I pass a certain volume threshold (nine steps) with my headphones, I get that annoying high volume alert. Sorry, my hearing isn't as good as it once was, so let me jam in peace!

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

If you have a lot of friends on Facebook, chances are that every day is at least one of their birthdays. If you took the time to individually post a message every time, you'd spend ALL of your time on Facebook, but you don't want to be a bad friend either. Let's face it, some people take this stuff personally.

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

If you have a smartphone with a good camera, chances are you don't think it's good enough. There's always something that can better with your mobile pics, and for me, that something is closeup shots.
How Do You Do A Business Plan? Part 1 of 5 (Series designed to discuss the parts of a business plan, what information is involved in each part, and why a business plan is needed.)
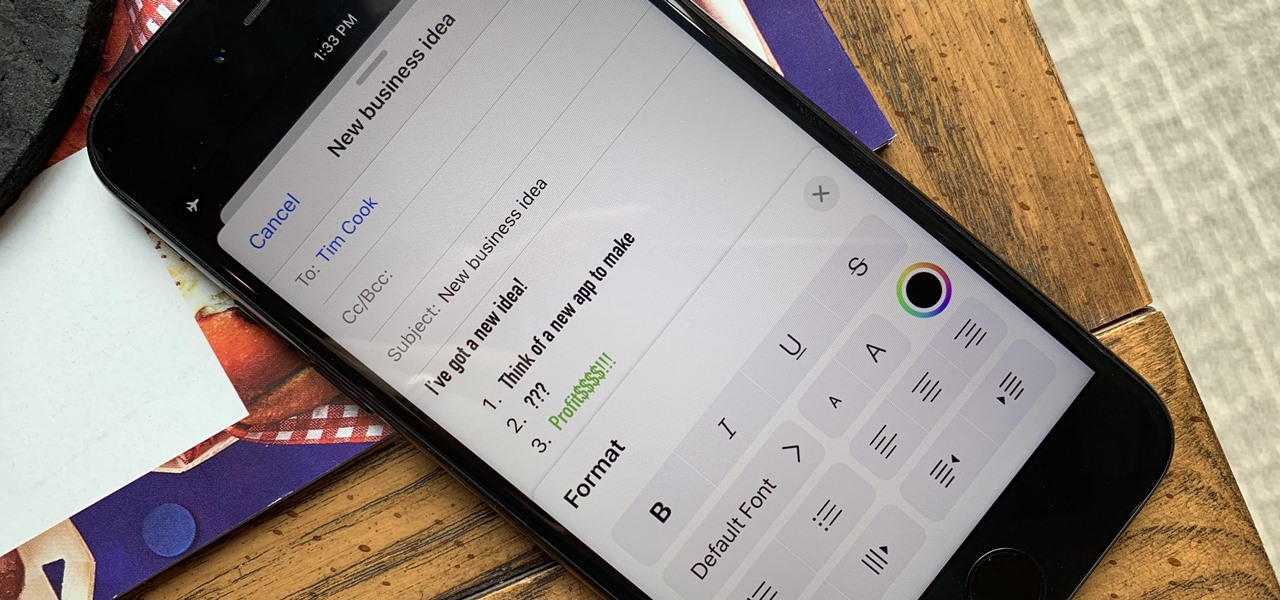
Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Earlier this year, we got our first taste of Android Pie in the form of Developer Preview 1. As with all past Android previews, DP1 was limited to Google devices — but at Google I/O 2018, Google announced that Developer Preview 2 would be accessible to other devices, including the Essential PH-1.

Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.
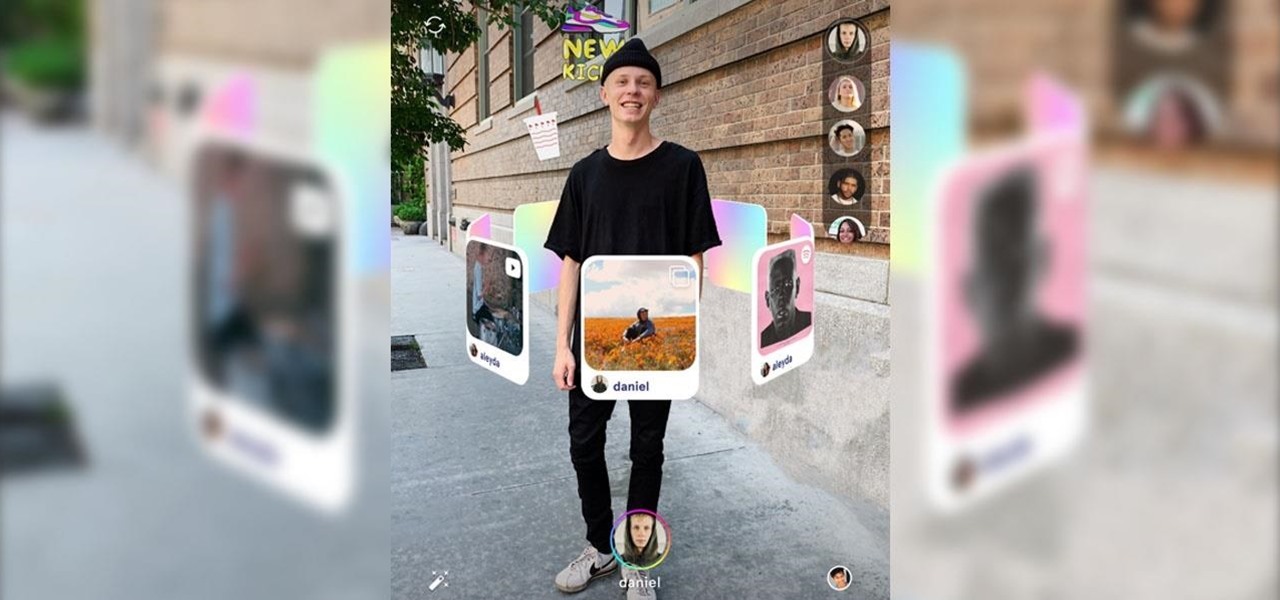
In a world full of augmented reality camera effects apps, one app is going in a more social direction.
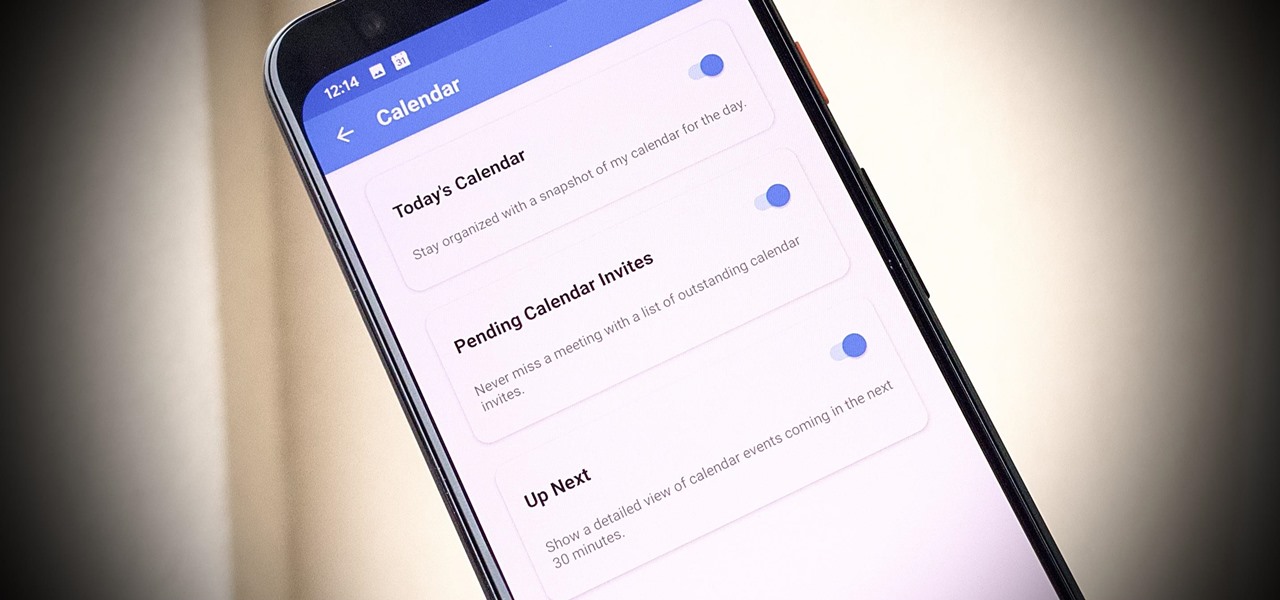
One of our favorite email apps, Edison Mail, just got even better. In versions 1.17.0 (iOS) and 1.12.0 (Android), the app introduced a new Assistant, a powerful tool that makes organizing travel, packages, entertainment, bills, calendar, and more a breeze over email. The best part? You can customize it to your liking, so the Assistant works precisely as you need it to.

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

A year after making a splash at the annual Consumer Electronics Show in Las Vegas with Amazon Alexa integration, smartglasses maker Vuzix is bringing a notable weather app to its Blade smartglasses for the 2019 edition of the conference.
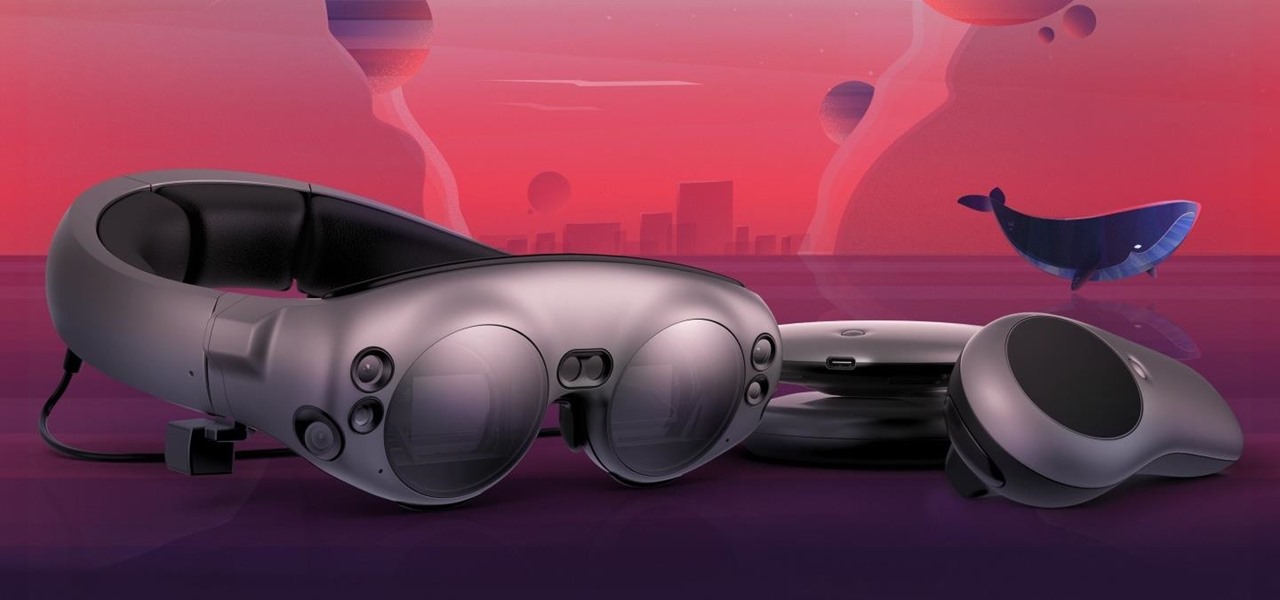
If you subscribe to notifications for Magic Leap CEO Rony Abovitz's Twitter feed, you'd think everyone in the world already has a Magic Leap One. Alas, that is not the case, but those not within the geographic areas of Magic Leap's LiftOff service now have a loophole through which they, too, can join the "Magicverse."

This week's crop of Snapchat lenses is jam packed with pop culture, and spot-on examples at that. Post Malone and Famous Dex are super hot right now, and there's a ton of buzz surrounding Arrested Development's latest season.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.