
How To: You Can't Stop Gmail from Scanning Your Emails—But You Can Limit Their Ad Targeting
Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.


Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Mobile 3D scanning company Scandy has released a new app for devices on Google's Tango mobile AR platform that gives users the advanced 3D scanning capabilities.

Scanners are much too cumbersome to fit in a pocket, but with the use of just one application, you can replace all that bulky hardware with your Android smartphone and take it with you wherever you go. All you need to do is find the scanning app that fulfills your needs. Here are our five favorites that are good for business pros and average joes alike.

Complex games in mixed reality require a pretty detailed scan of the room, and getting this process right can be both time-consuming and annoying. Computer science students at the University of Washington decided to fix that by turning it into a game.
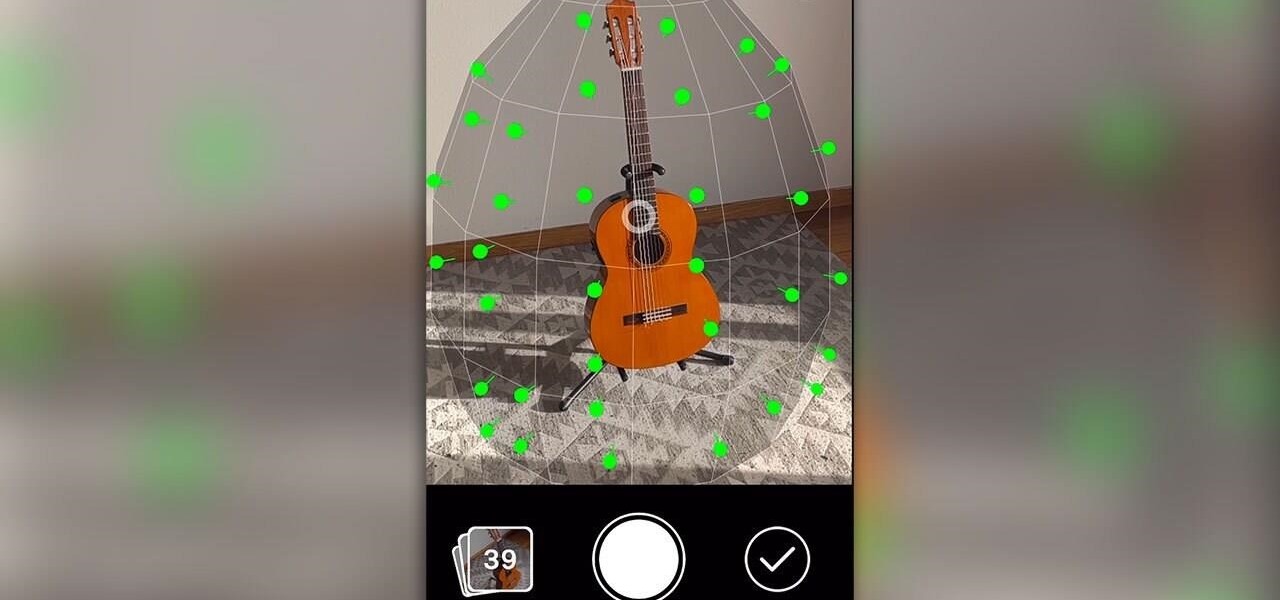
One of the more exciting augmented reality announcements Apple made during its WWDC keynote on Monday came in the form of Object Capture, a new 3D scanning feature coming to macOS Monterey.

Augmented reality app developer Laan Labs has shared a preview of a beta app that achieves 3D scanning with just an iPhone and produces highly-detailed models for sharing with others.

At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

In off-record discussions with AR experts, the consensus on ARKit is that it takes a software approach to the depth-sensors available on Tango devices. As a result, the toolkit has shortcomings, such as detecting walls and vertical surfaces.

The mobile augmented reality war for dominance between Apple and its Asia-based rivals is in full effect.

Researchers have developed a new method that harnesses the power of augmented reality to detect a patient's heart rate using a Microsoft HoloLens and computer vision.

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.
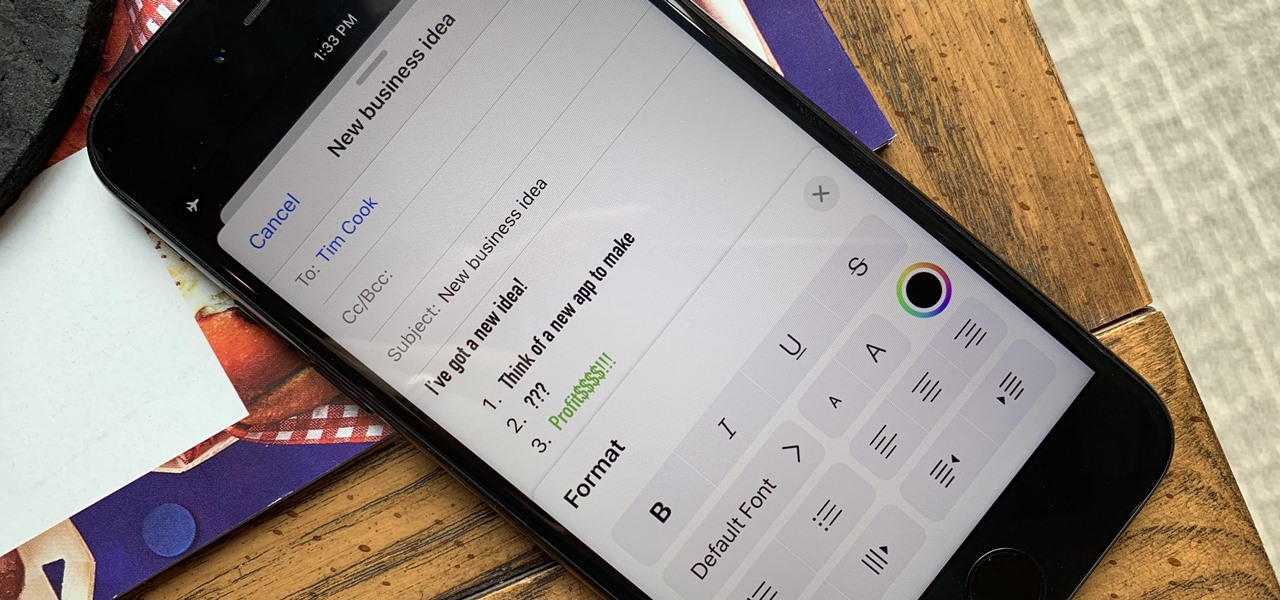
Although Mail didn't get a massive update in iOS 13, the new formatting and attachments toolbar makes it easier to stylize your messages and get quick access to files you'd like to send. It even includes the excellent document scanner built into iOS, so you can use your iPhone to turn a physical document into a PDF and attach it to your message — all from within the Mail app directly.

As brands and content makers create more augmented reality experiences, the demand for tools to create 3D content grows in kind.

Here is a short video tutorial which demonstrates how to debind books using a hair dryer. You may need to take books apart for detailed scanning projects. However, this is a destructive process which will destroy your book. The hair dryer method is a fairly failsafe method of removing binding from books.

DARPA and Dallas's Southern Methodist University are collaborating on a super high tech camera, capable of scanning eyeballs in a moving crowd.
With the TSA's full-body scanners occupying a great deal of airports nationwide, the debate remains as to whether air travelers should continue to be subject to immoral security techniques and possible health risks due to the x-ray scanning devices. The "advanced imaging technology" may help keep obvious weapons out of major airports, but scanning naked bodies seems more voyeuristic than crucial to national security. But while the argument continues, one woman is taking a stand… well, not rea...
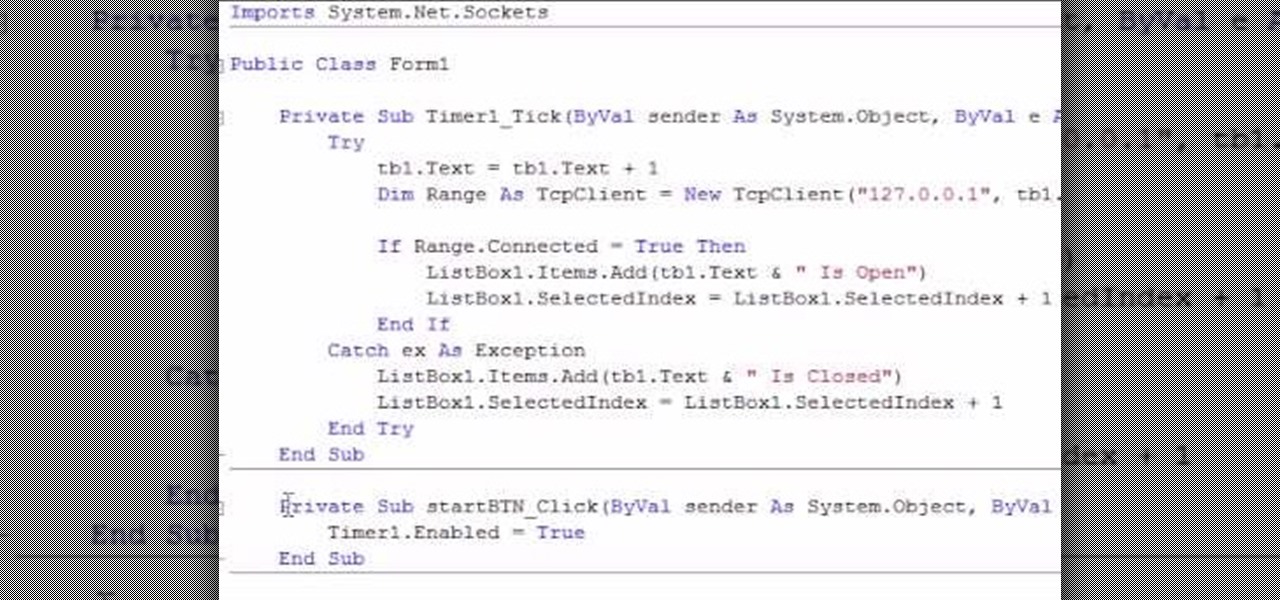
This is a Computers & Programming video tutorial where you will learn how to make a simple port scanner in VB.Net. It detects all the open ports on your network. Open up a Form1 and you will have a ListBox1, a ‘Start’ and a ‘Stop’ button and a blank text box. There is also a Timer1 button at the bottom. Thereafter, the video shows the various parts of the code on the screen. Then click on Debugging, and click ‘Start’. The system starts scanning ports starting with port 1. In the video it show...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

While many retailers have introduced try-before-you-buy features in their apps, Walmart has gone in another direction by bringing shoppers an augmented reality tool to help them compare products they want to buy.

When you hear people say the iPhone "just works," it's because of all the finishing touches Apple adds to iOS. A perfect example of this is the new QR-scanning feature in iOS 12 — by tapping a single button in the iPhone's Control Center, you can scan a QR code within seconds.

After parting ways with Papa John's, the National Football League has drafted Pizza Hut as its official pizza purveyor, and the company has hit the field with an augmented reality game to entertain hungry football fans.

Mobile scanning applications are nothing new in the world of Apple, except that the majority of them usually come with pesky in-app purchases that stifle the entire experience and render some features useless until you pay for them.
Document scanning is possible via the Google Drive app, but my brain doesn't think of opening a cloud storage app to scan a document. I usually just open the camera app and take a picture instead — and apparently, I'm not the only one.

Gathering information on an online target can be a time-consuming activity, especially if you only need specific pieces of information about a target with a lot of subdomains. We can use a web crawler designed for OSINT called Photon to do the heavy lifting, sifting through URLs on our behalf to retrieve information of value to a hacker.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

The new Samsung Galaxy S8 and Galaxy S8+ phones were announced on March 29 at the Samsung UNPACKED 2017 event. Preorders start on March 30 for the Korean tech giant's latest flagships, and sales officially begin in the US on April 21. Samsung will need a smooth release to win back consumer trust after the Note7 mess, and it's already looking like the S8 won't disappoint.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

This is one of the coolest applications of Apple's ARKit that we've seen so far. The 3D software product studio gradientspace has created a Minecraft 3D scanner using ARKit.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.
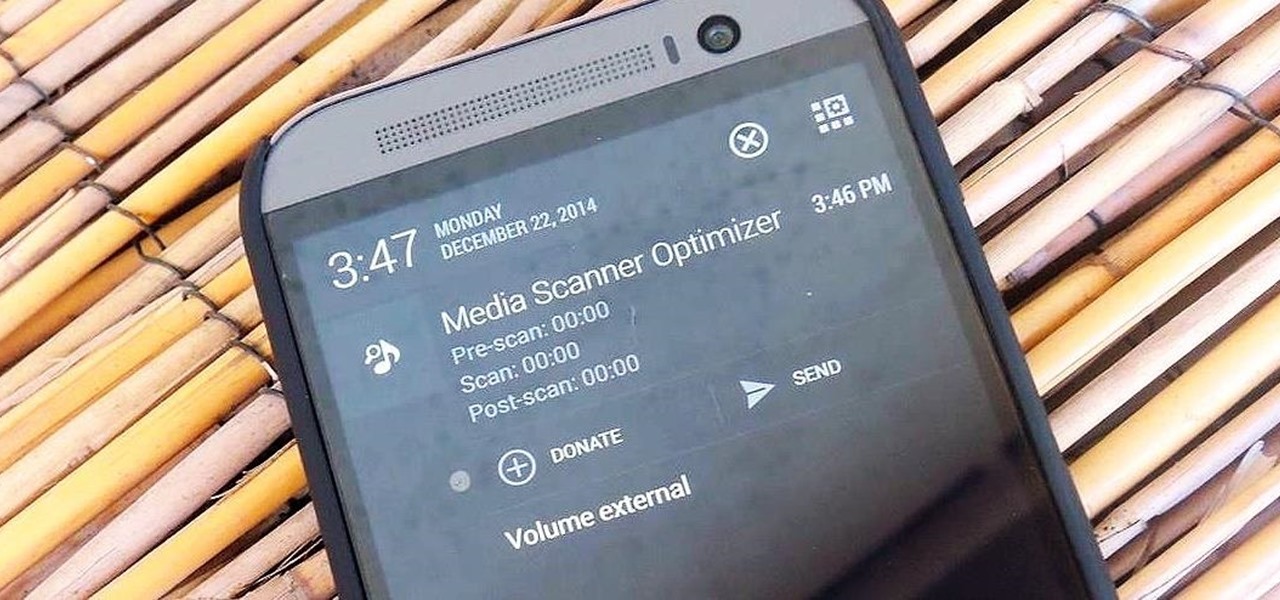
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.