The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.
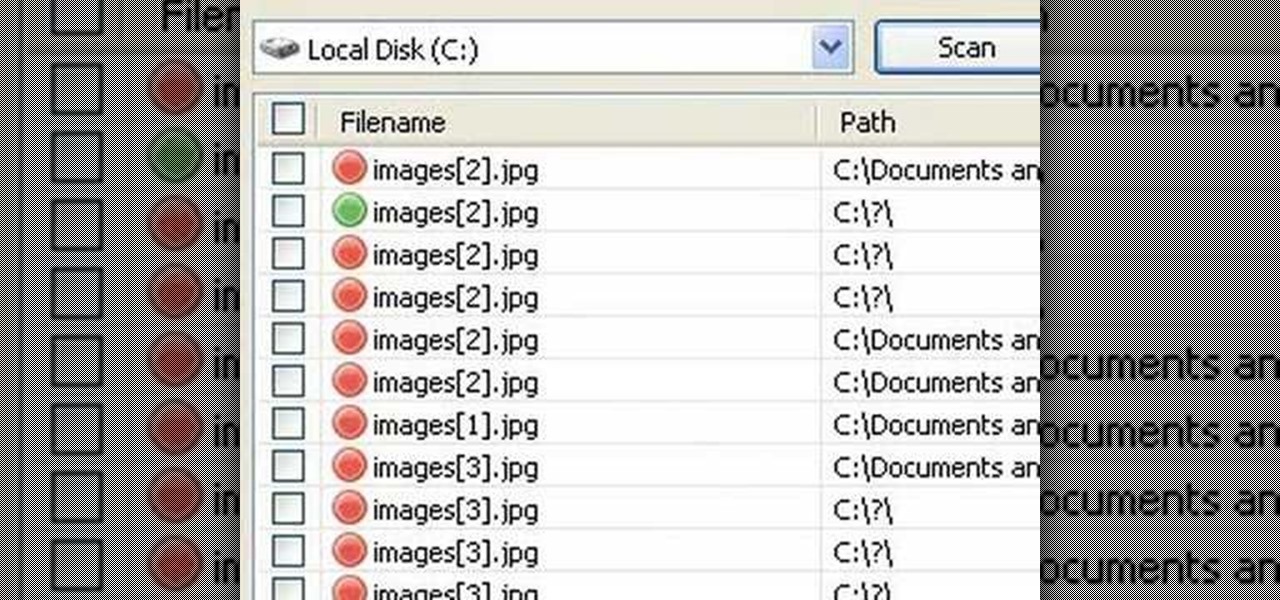
In this video tutorial, viewers will learn how to restore and recover deleted files using Recuva. Recuva is a freeware data recovery program. Recuva recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Begin by selecting the type of file and continue inputting the information. Then it will begin scanning the driver for the deleted files. It will then display all the deleted files. The green files are recoverable while the red ones are not recover...
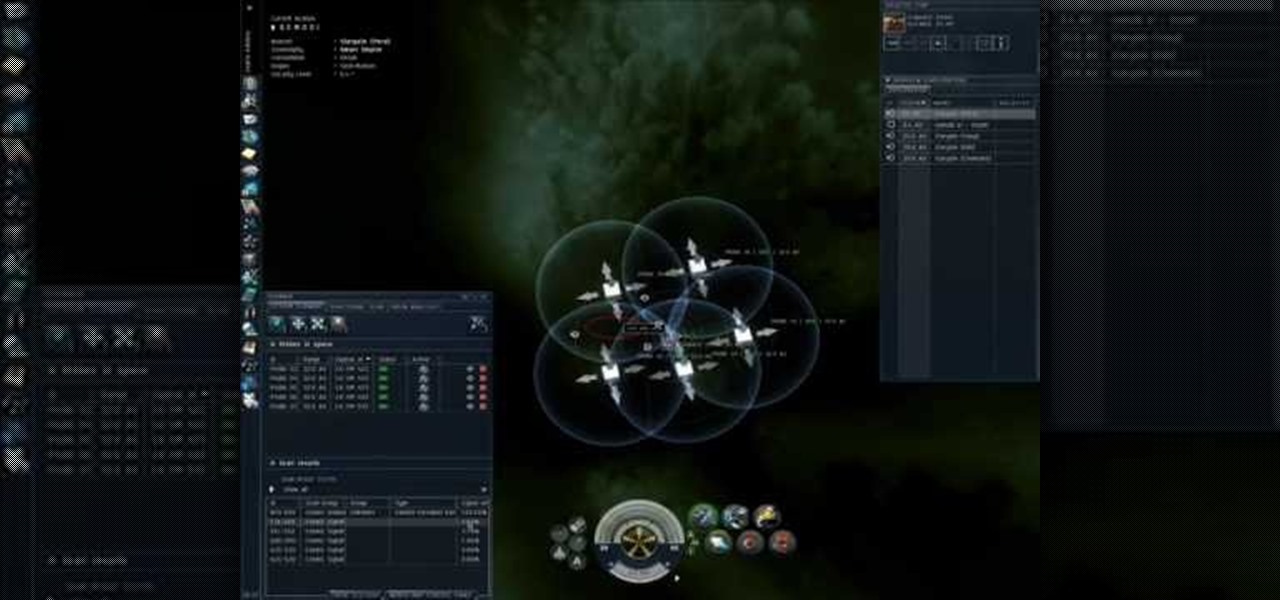
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

Think of your brain like a muscle, if you train it correctly and diligently, it will perform at its top capacity. The retention of information is a skill like any other that can be improved with some practice and even rest when appropriate.

Here, Gina Trapani explains three cool ways to combine the camera on your iPhone or Android with two of their apps, Google Goggles and Shopsavvy, to accomplish productive goals. These include scanning bar codes, translating text, and storing your membership cards for the gym or the library.

Need a quick solution to digitalizing your book collection? Well, here comes the BookSnap. This video will give you a brief tutorial on how to use this system to upload your pages to your computer, and then possibly, the web.

Need to get your books digitalized? Well, BookDrive DIY is the solution to scanning them for the web. This video will show you how to use it to get your books in your computer.

C-SPAN is one of the best ways to get your news on the web. Watching their videos from their website will get you up-to-date on all of the new headlines, and it will always give you a history lesson with all of the past headlines. See something interesting while watching a C-SPAN video and want others to see it, too? C-SPAN makes it easy to clip the exact portion you want, and share it with friends or embed it on a website or blog. Just follow these instructions.

TheUMLabs shows how to setup a wireless network with Ubuntu. The first thing the user does in this task is open Hardware Drives. After the searching for drives box finish scanning it list available drives to install. This s then selects a driver that is available to the computer they are working on. The next thing that the user do is edit the Wireless connection. If you follow all of the steps in the video, you should be able to connect to a wireless network in Ubuntu.

Mass Effect 2 may have been around for a whole year... but not on the PlayStation 3. And last Tuesday, January 18th, PS3 gamers finally got their hands on a copy of the critically acclaimed RPG. Actually, this is the first time any Mass Effect game has been available on the PS3, making this a historical event for BioWare.

This interactive Kodak EasyShare software tutorial takes you through every step necessary to fully use your AiO Home Center software. If you have a Kodak EasyShare digital camera and a Kodak ESP 3 or ESP 5 All-in-One Printer, you probably have this printer suite program. Let Kodak teach you how to use the AiO Home Center software. See how to perform basic scanning with the printer, advanced scanning, basic copying, advanced copying, printing pictures, checking ink levels, and other helpful re...

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

This hour-long hacking tutorial looks at the Nmap security scanner. In particular, this Nmap tutorial looks at port scanning concepts, TCP three way handshake, stealth scans, idle scans, bounce scans, version detection, OS detection, NSE/LUA scripting and firewall logs. To get started using Nmap, watch this video tutorial. Use the Nmap security tool.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel today's lesson.

Listing your accomplishments is an essential part of your resume. Completion of this video instructs you how to list your accomplishments on a resume in bulleted lists while using action verbs, showing results and impressing the reader. Build an amazing resume today.

QR codes are like smart little cubes of data. To unlock this data, you will need a QR reader. These are annoying because you typically have to download a third-party app, and some of these apps are shady. Luckily your Samsung Galaxy running One UI has a hidden QR scanner built right in.

There are over 425,000 apps in the iTunes App Store and the Android Market has over 300,000 available, which makes it really hard to tell which ones you want and which ones you don't. One of the best ways to find new mobile apps is from your family, friends and colleagues—those who have similar tastes in games and productivity. And it goes both ways, which means you need to share your favorite picks with those around you. But what's the easiest way to do that?

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials of any skill level, about anything you feel like sharing that is ...

Scanner photography + sandwiches = Scanwiches (simply put: "scans of sandwiches for education and delight"). The web-famous Tumblr is the invention of Jon Chonko, a NYC-based designer at thehappycorp global.

MY MULTIPLY.COM SITE IS: HTTP://WWW.STANDP.MULTIPLY.COM/

This panhandling robot isn't too proud to beg. In fact, it's custom-built for it. And who could refuse? Get a load of that puppy-dog eye.

There are plenty of cutting edge apps out there, and endless innovations in the field of 3D printing. But to combine the two—and make it available to the common consumer—is unprecedented.

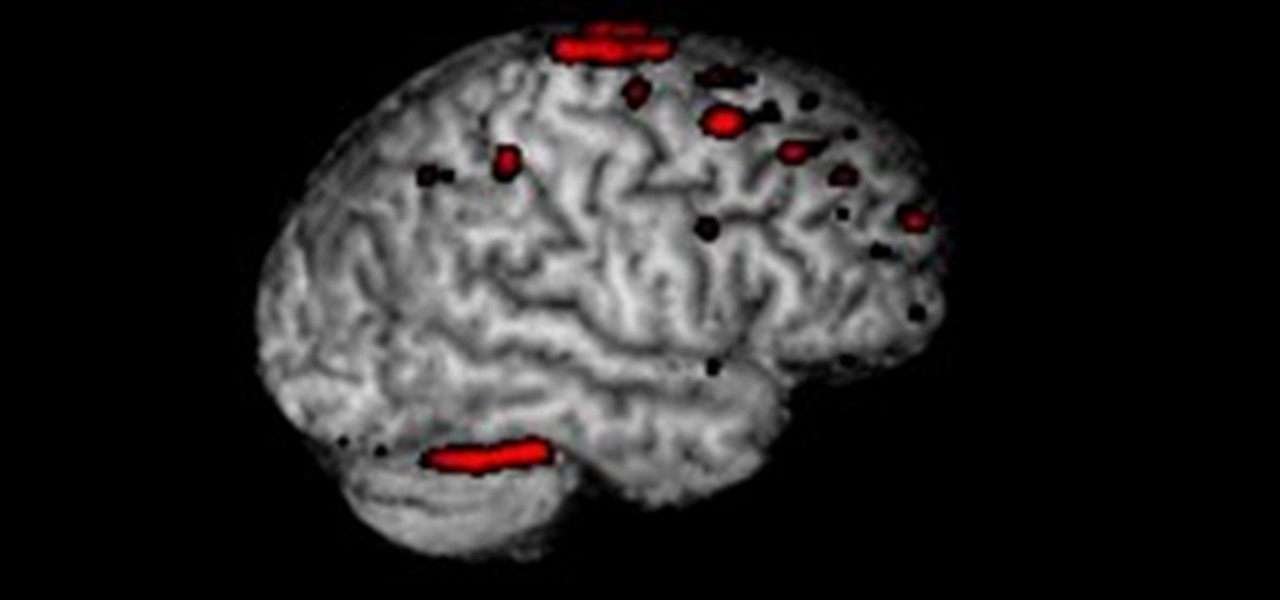
Ever wonder what your brain looks like on video games? Below, Matt Richtel of the New York Times lies in a $3 million M.R.I. scanning tube while playing a simple driving game, as researchers sit by and observe the real-time images inside Richtel's brain.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

You may not do it in public, and you might not admit to it among your friends, but you do it. We all do it... sing. We sing when we're alone in our cars, at home when no one's listening, and when we've had a little too much to drink and don't care anymore, all inhibitions aside. We love to croon and belt out lyrics to our favorite songs because it makes us feel good, no matter how good or how awful we are, or how well we know the words. Well... now you can at least be proud of one of those th...

A couple months ago, the world was supposed to end. It didn't. But that didn't stop the Centers for Disease Control and Prevention (CDC) from warning citizens of one global possibility besides complete destruction—ZOMBIES. They used the farcical flesh-eating living dead as an excuse to teach you about the necessity of real-life emergency planning.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

No matter how you feel about Apple, I think most Samung fans would agree that AirPods have some great features, including the ability to pair and use the earbuds without messing around with Bluetooth settings. But did you know your Samsung Galaxy S20 has this feature as well?

Encryption is on everyone's mind these days, from the FBI's battles in court with Apple to WhatsApp's recent announcement of end-to-end encryption for their one billion users. Now you can add Signal, whistleblower Edward Snowden's favorite messaging app, back to that whirlwind discussion. Created by Open Whisper Systems, Signal is an encrypted messenger app that allows you to send text, images, video, and audio messages without the fear of prying eyes. They already have an Android and iOS app...

Mobile World Congress is just around the corner, and if patterns stay consistent, Samsung will be unveiling their newest member of the Galaxy line, the Galaxy S5.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.