The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

In this series of videos you'll learn how to connect and use a 2D scanner. Electronics & media expert Tony Ramirez shows you step by step how to load the drivers and software onto your computer, how to adjust the scanning settings, and how to save and print an image you've scanned.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!
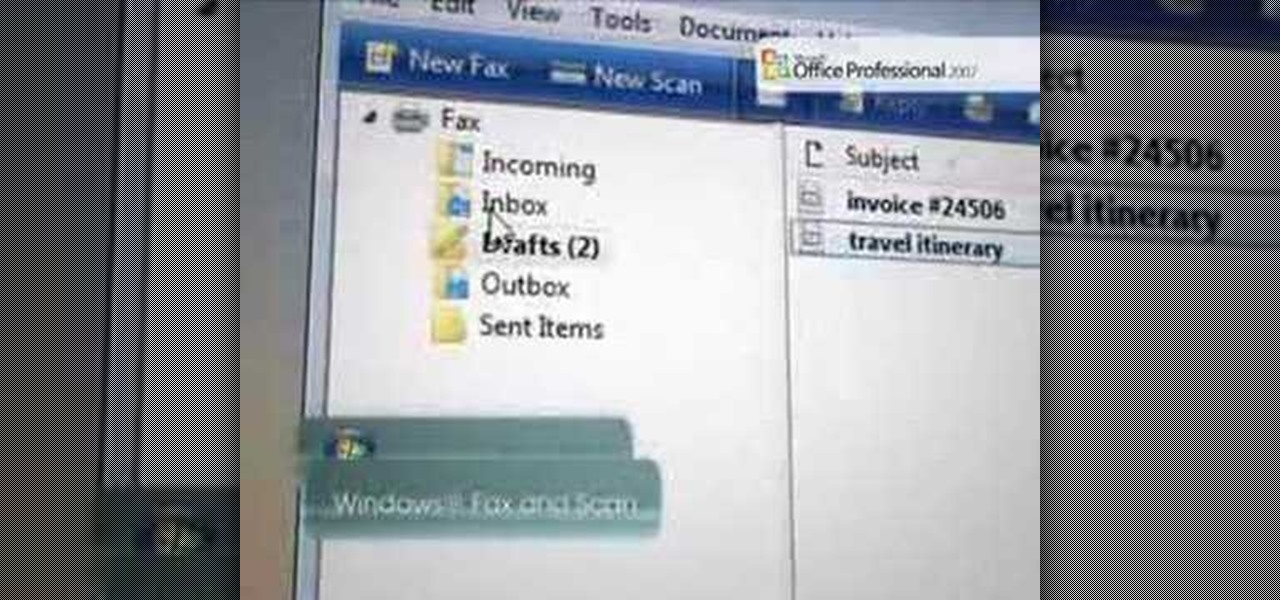
With Windows® Fax and Scan feature that works with the Windows Vista™ operating system makes it even easier to share fax and scanning capabilities with multiple users. Where previous fax and scanning programs allowed an individual user to send and receive faxes or scan documents with a locally-connected fax or scanner; Windows Fax and Scan provides a flexible system for multiple users to share local or network-connected scanners and fax devices. F

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

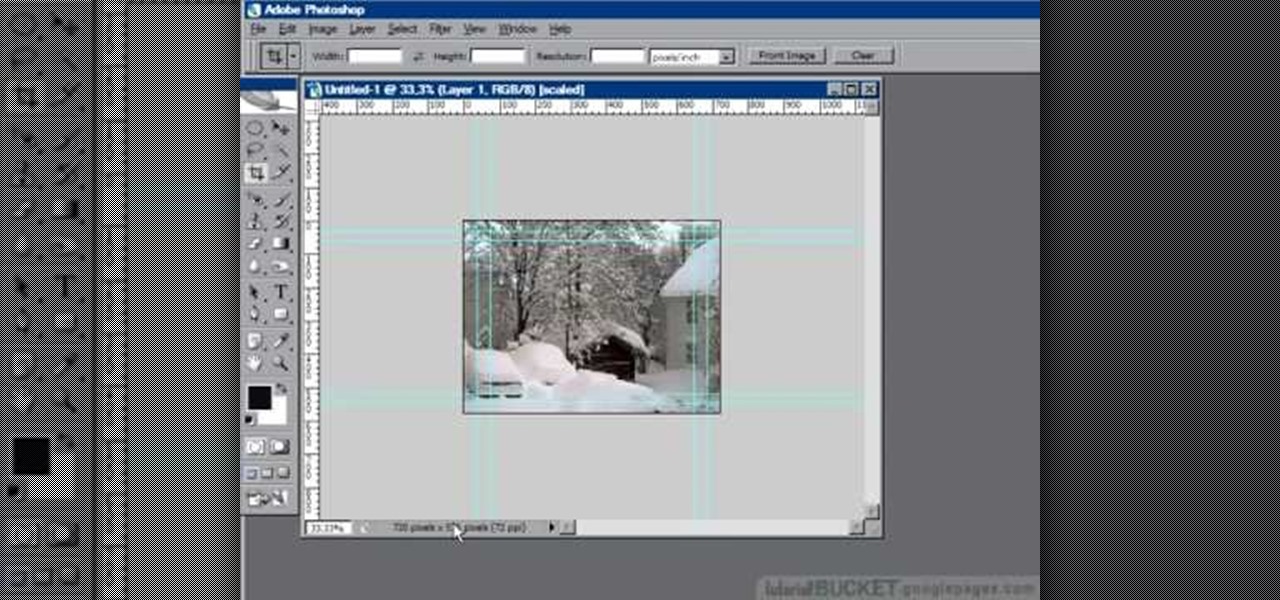
In this Adobe Photoshop tutorial the instructor shows how to prepare pan and scan images. To prepare an image by panning and scanning is quite different than preparing an image normally for using in your video. These images should be extra sized as you would perform special effects on the image in your video. This is also called as "Ken Burns" effect. Now go to the file, new menu and select the video format that you want to use according to your requirement. Enable the correct pixel aspect ra...

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

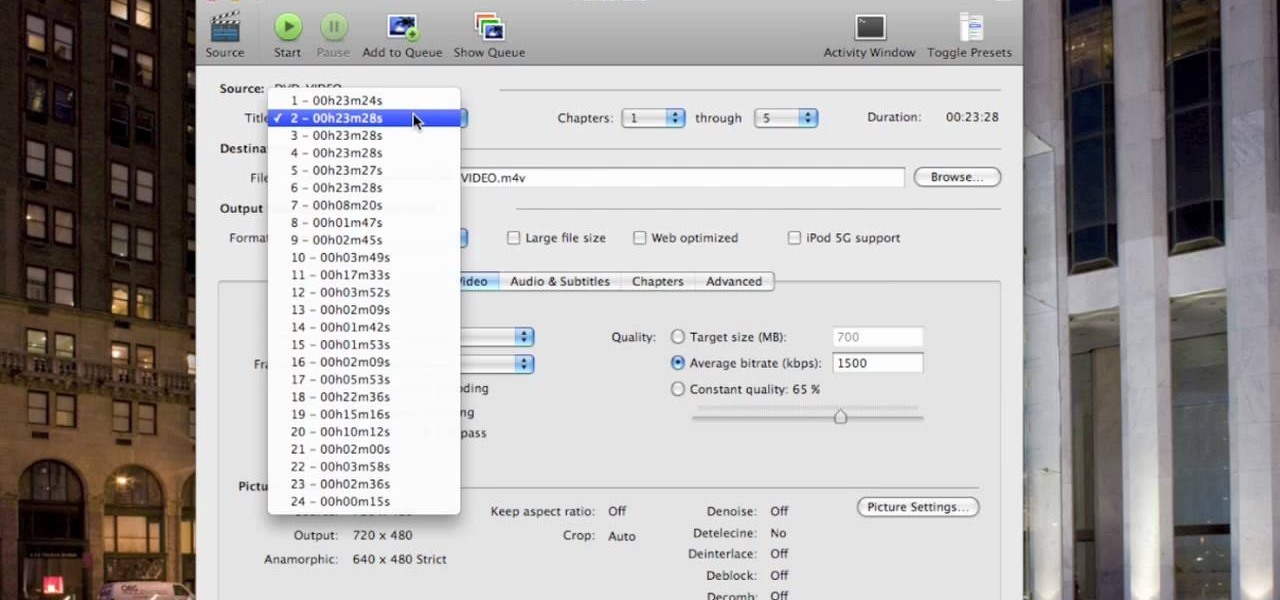
This video shows you how to copy a DVD to a Mac using a free application called Handbrake. Open the Handbrake window, select the DVD you want to copy from where it's listed on the side, and click open to start scanning. After the scanning is done, a window will come up where you can choose which file on the DVD you want to copy. If you're copying a movie, it's usually the largest file. Choose what type of file you want to convert it to, and it will start copying. If the DVD is encrypted, you ...

Buying a digital camera doesn't mean your old prints, slides, or negatives are obsolete. You can easily convert them with a scanner to bring them into the 21st century. Watch this video to learn how to convert photos to digital.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Believe it or not, there was a time when smartphones weren't the primary tool for taking photos. People actually walked around with bulky film-based cameras on their necks, and some even used cheap disposables. While photography wasn't introduced to the world when smartphones came out, it's definitely more accessible—and everyone is a photographer now.

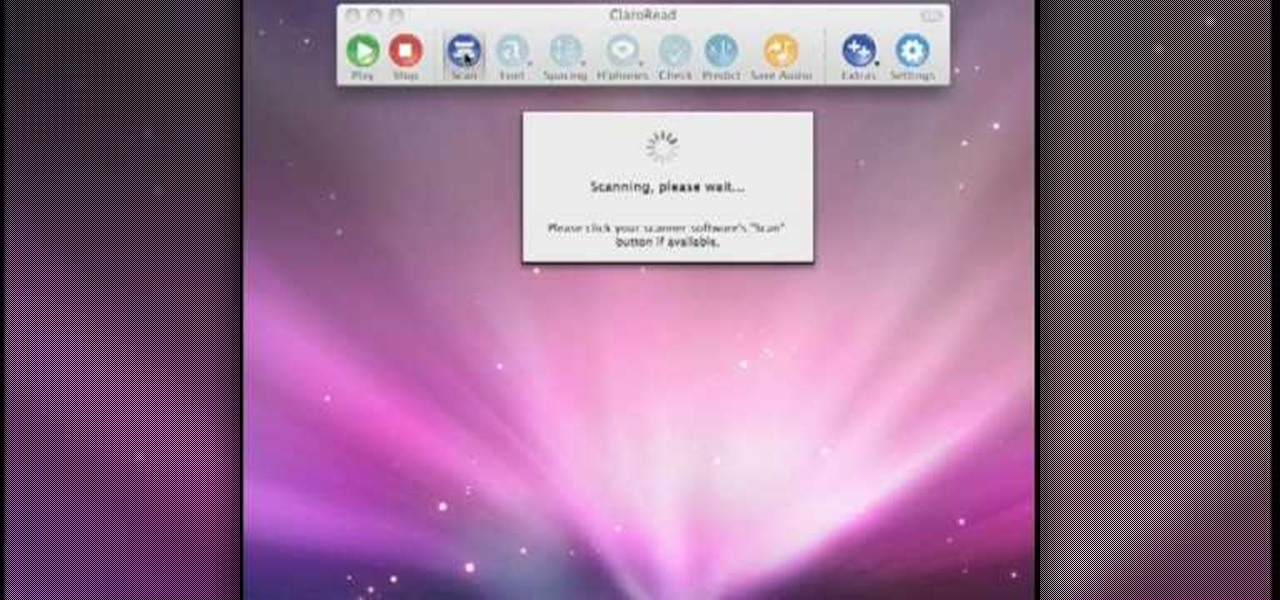
Scanning is an awesome, fast way to transport a document into your computer. But, what if you want to edit it once you've scanned it? Most scanner programs will import your document as a read-only PDF or image file. With this tutorial, learn how to use the program ClaroRead on a Mac to scan your document directly into Microsoft Word for editing. This will save you a lot of time and a lot of annoying formatting and copy and pastes!

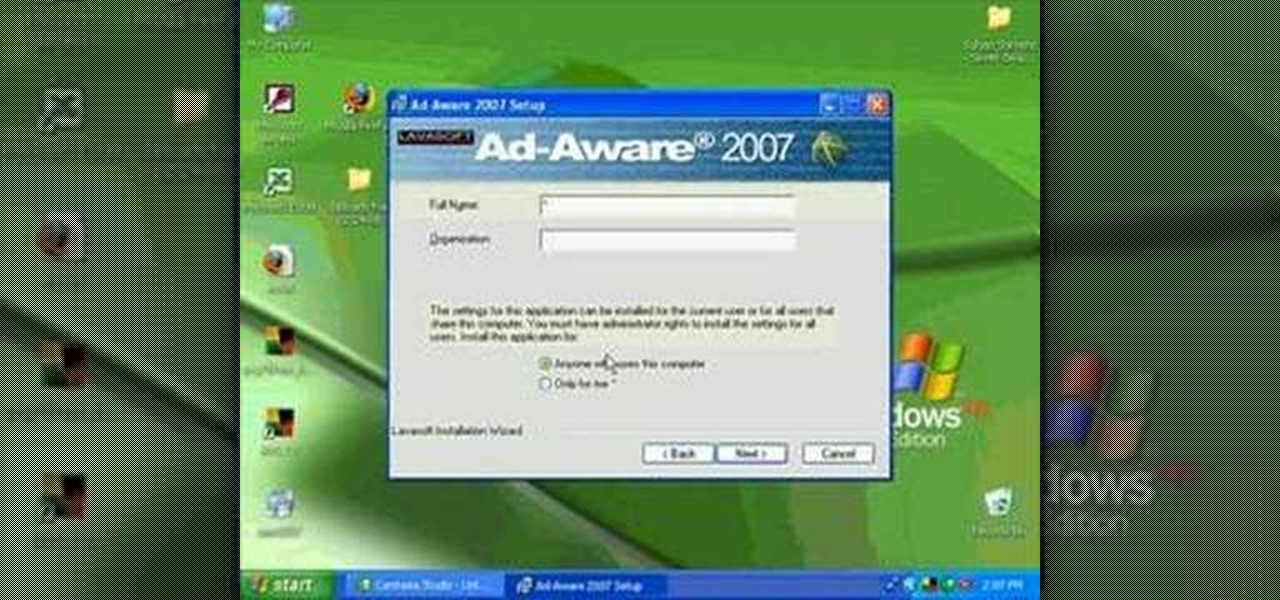
This is a Computers & Programming video tutorial where you will learn how to remove annoying spyware on your PC in Windows XP. Some spyware can be really nasty. This video shows how to remove spyware for free. Go to Download.com, and search for ‘ad aware’, download and install it. This video recommends Ad-Aware. While installing, select safe mode of scanning, otherwise some spyware may not be detected. Then, you need to update the definitions. Keep the definitions updated regularly. After upd...

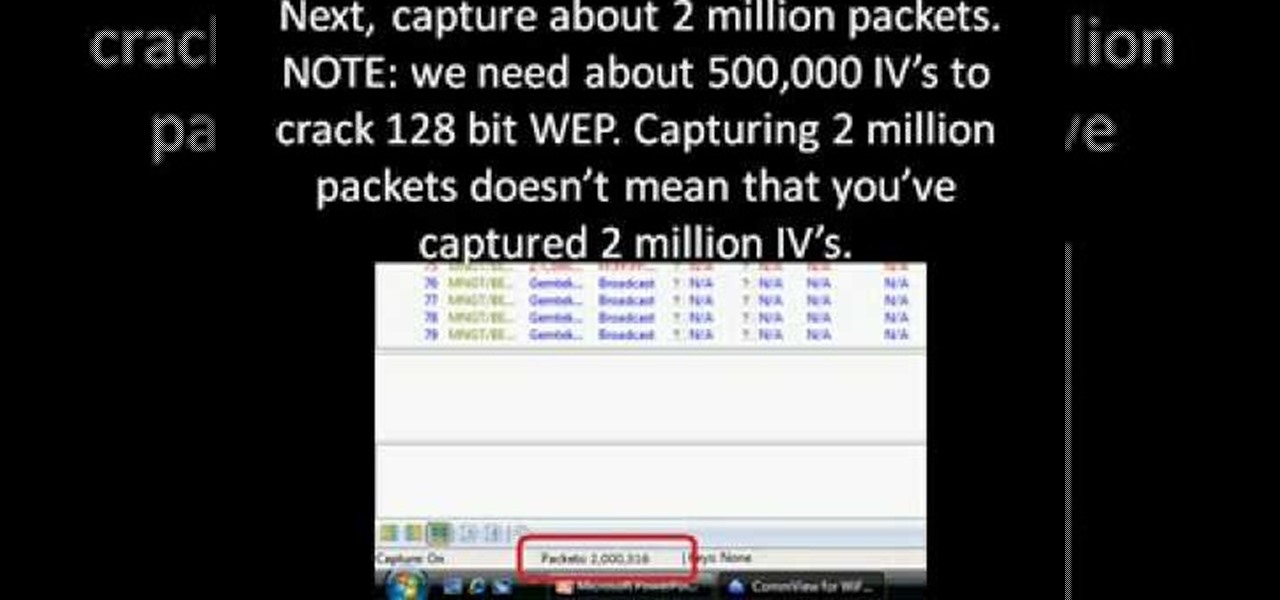
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

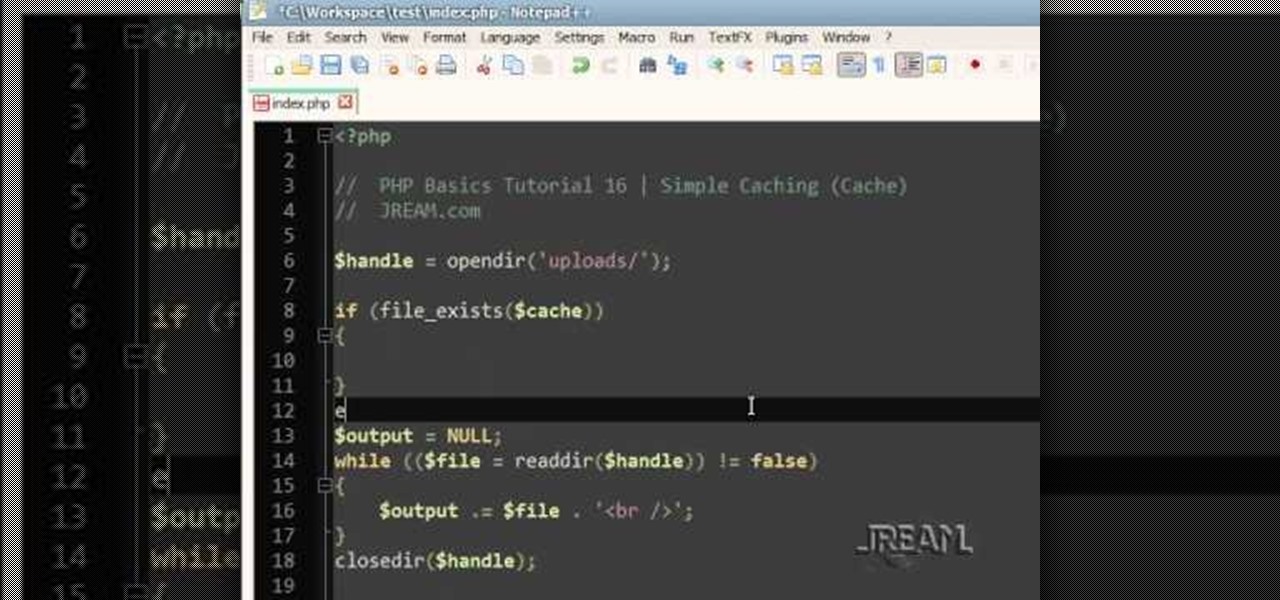
Sometimes server space can be an issue, especially when you're talking about costly actions such as iteration, file scanning, and numerous queries. In those instances it's often best to cache! This tutorial gives you a simple example which can help your site load faster and take less abuse.

If you've been playing the Minerva's Den DLC for any period of time, you may have noticed that there is one secret achievement in your list that doesn't really make sense. But, if you've been scanning the forums, you will have noticed some people talking about a secret arcade game called Spitfire. In this video you will discover its location and also watch how to play the game and how the achievement works.

Interested in scanning QR matrix codes with an Android phone? This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, watch this video guide.

Want to know how to make HijackThis, the popular malware scanning program, display only malicious registry entries? Learn how to use the Ignore List to acheive just that with this free home computing how-to from the folks at CNET TV, which offers complete instructions on how to tweak HijackThis to make removing viruses and spyware a breeze. For more information, and to get started protecting your own Windows PC from malicious software, watch this handy how-to.

Years ago, in 2013, Occipital introduced its original Structure Sensor for iOS, a mobile 3D scanning device for measuring three-dimensional objects. Soon after, in an unrelated deal, Apple acquired PrimeSense, the company that made one of the components for Occipital's scanning device.

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Have you ever marveled at those knitting doyennes at Michael's who can just run up to the yarn aisle and speedily pick up some yarn because they know exactly what type of of yarn they need for their project without reading the yarn label? Most of us struggle with different yarn consistencies, scanning the label to get a feel for how the yarn would play out if knitted.

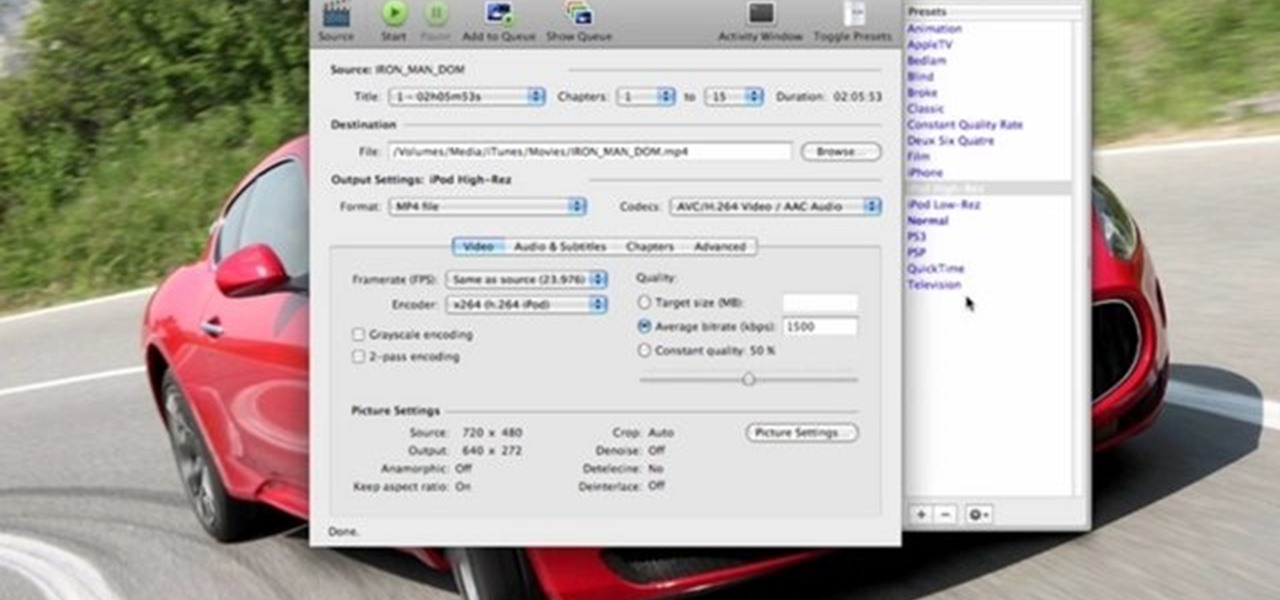
In this video tutorial, viewers learn how to rip a DVD with the program, Handbrake. Begin by opening the video in the program by clicking on Source and locating the DVD drive. Handbrake will start scanning the all the titles of the DVD. When finished, it will automatically select the correct title for the movie. Under Destination, click on Browse to select your saving destination. You are also able to change the name of the file. Now select the video format and aspect ratio. When finished, cl...

As part of the iOS 11 update, Apple added a document scanner function that creates high-quality digital copies of physical documents, but it was only available inside the Notes app. With iOS 13, Apple has built its scanner right into the Files app, enabling you to quickly create PDFs with your iPhone and do more with them.

Animate drawings by scanning them and painting them on the computer. Learn how to scan and color hand-drawn animations using Adobe Photoshop and Flash in this free computer art lesson from a professor of animation and interactive media.

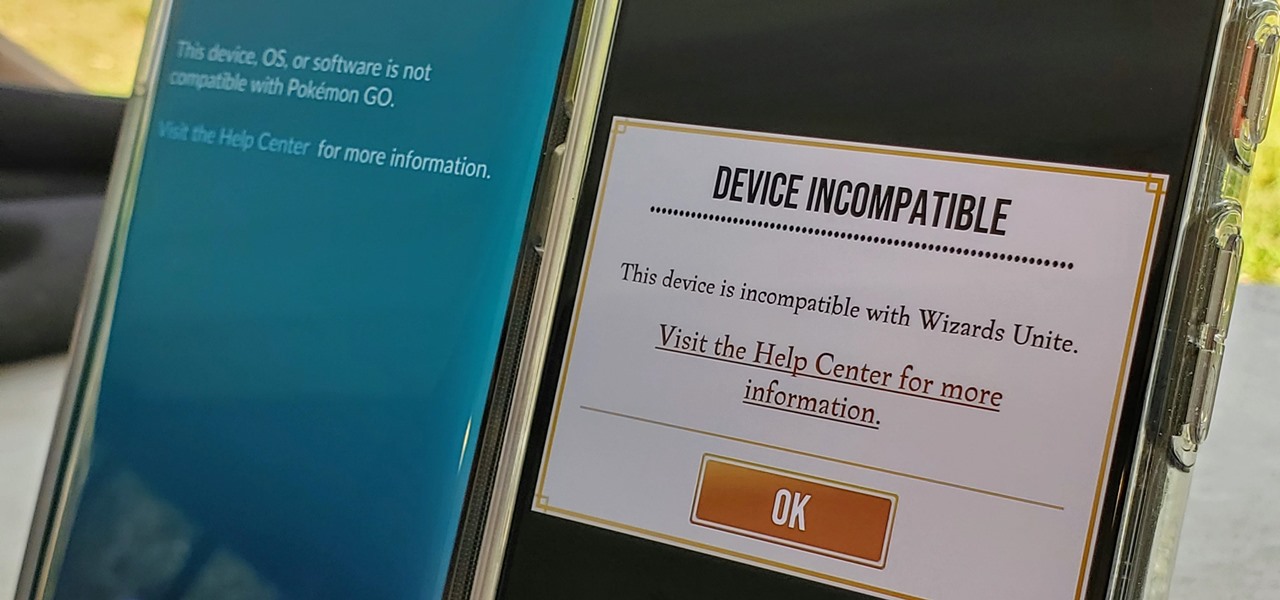
Both Pokémon GO & Harry Potter Wizards Unite are augmented reality games developed by Niantic, and neither needs much introduction. Pokémon GO, all by itself, created a worldwide phenomenon that still carries a strong fan base years later — Wizards Unite is working on doing the same. However, things are not all fun and games, as you might think in the world of monsters and magical creatures.

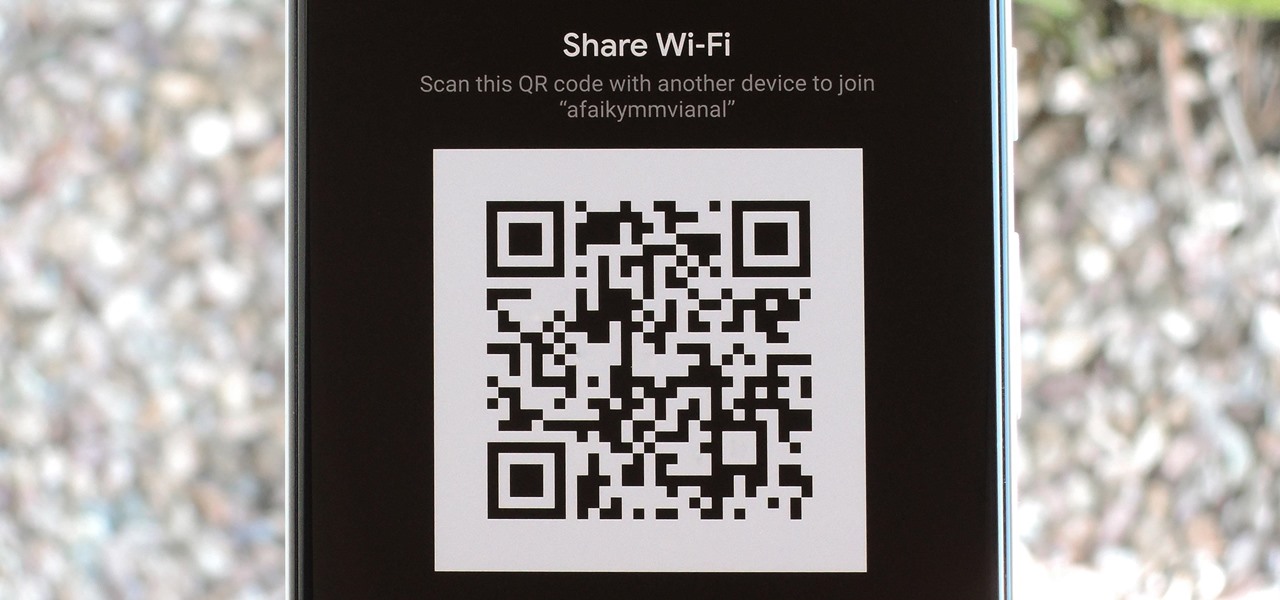
If your phone is running Android 10, you can now share your Wi-Fi network with friends using a handy QR code. The other person doesn't have to be running Android 10 — in fact, you can even share this code with iPhone users. In most situations, this is now the fastest way to share your Wi-Fi password.

There are plenty of third-party apps for scanning documents on your iPhone, but they can all be tossed out the door since iOS 11 includes one by default now. Instead of a dedicated app, it's included as part of the Notes app, and it's fairly easy to use. After scanning, you can save it, print it, turn it into a PDF, add markup, and more.

The Franklin Institute is rolling out the augmented reality carpet for the arrival of the Terracotta Warriors of the First Emperor exhibit, which will open on Sept. 30 in Philadelphia.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

Scanning important paperwork on smartphones is a tedious process, often relying on either external scanners or third-party apps that had to be either purchased or were loaded with annoying ads just to get the job done. Thankfully, iOS 11 now lets you easily scan documents using your iPhone, and finally does away with the need for third-party apps or machines.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.