Apple has implemented a new sensor on the rear camera of its fourth-generation iPad Pro, and it's pretty exciting. It's called the LiDAR Scanner, a scanning "light-detection and ranging" sensor, and you may very well be acquainted with it if you follow any driverless car news. Will we also get it on the upcoming iPhone 12 Pro?
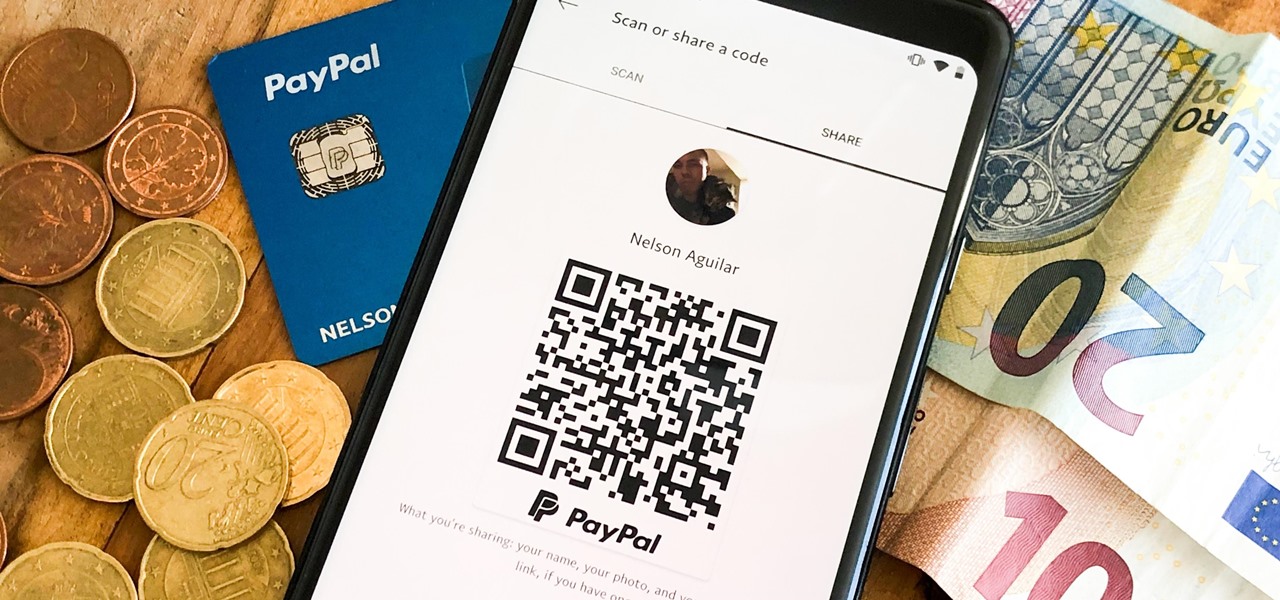
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

When Apple unboxes the next major update to its mobile operating system this spring, iPhones and iPads will gain some significant new features for augmented reality experiences: verticality.

A Jedi does not seek adventure or excitement, but Star Wars fans can seek Jedi with the Find the Force augmented reality scavenger hunt promoting the launch of merchandise for Star Wars: The Last Jedi.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The company that pioneered music scanning for mobile devices is moving into the augmented reality advertising arena. Included in an update of their iOS and Android apps last week, Shazam can now scan special codes to immerse users in 3D animations, 360-degree videos, mini-games, and other AR content.

If you've ever wanted to live in the Matrix—or at least the iconic digital rain data visualization that Neo saw when realizing he was, indeed, the "one"—you can now do that with the Microsoft HoloLens. Just download The Red Pill.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

With iOS 11, Apple's very own Notes app will now come standard with a number of new features that aim to make it significantly more user-friendly and help it compete against more popular notepads like OneNote and Evernote.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

Despite the wide availability of markerless augmented reality experiences for mobile devices, there is still a market for scanned triggers for content, as evidenced by the new image recognition capabilities on Facebook's Camera AR platform.

Thanks to Apple's beta preview of iOS 11.3 released last week, app developers are already experimenting with the ARKit capabilities that will be available to regular users this spring.

Thanks to ARKit, homeowners and apartment dwellers can visualize just about every aspect of their abodes, from furniture and decor with the IKEA Place, Houzz, and Amazon apps to new countertops with Cambria's app and retractable awnings via Markilux.

Online glasses retailer Warby Parker built its reputation by selling fashionable yet affordable eyeglasses, so it perhaps a surprise that it's one of the first developers to take advantage of the technology in the least affordable iPhone yet.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

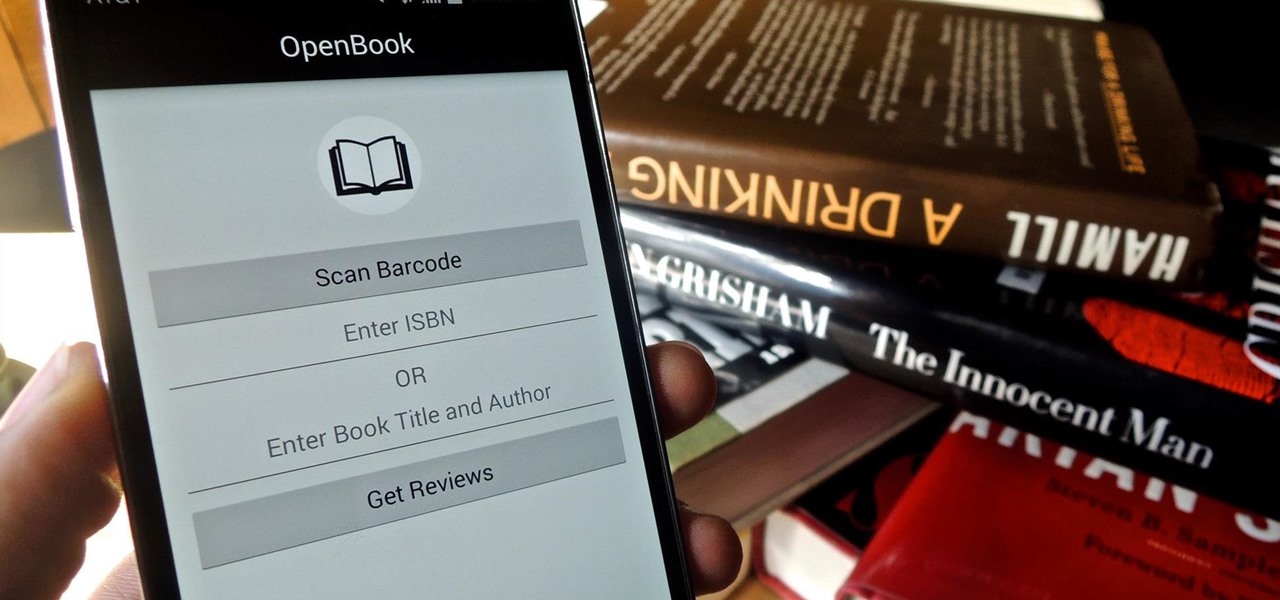
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

While its competitors are concentrating on building out AR cloud platforms to give advanced AR capabilities to mobile apps, Ubiquity6 is taking a step in a different direction.

The road to becoming a skilled white hat is paved with many milestones, one of those being learning how to perform a simple Nmap scan. A little further down that road lies more advanced scanning, along with utilizing a powerful feature of Nmap called the Nmap Scripting Engine. Even further down the road is learning how to modify and write scripts for NSE, which is what we'll be doing today.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

Google just rolled out a revolutionary feature to its Pixel devices — Google Lens. Previously, Lens had only been available in the Photos app, but now, whenever you want to learn about something in the real world, you can just bring up Google Assistant, turn on the camera, then let Google's famous AI analyze the scene.

The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a couple of years.

This fall, DC Comics fans will be treated to an augmented reality experience promoting the Justice League movie. Likewise, history buffs will be able to enjoy their own augmented reality content by way of the Terra Cotta Warriors exhibit at The Franklin Institute in Philadelphia, Pennsylvania and an in-store promotion featuring famous convicts from 19 Crimes wines.

When it comes to applying augmented reality to various business functions, as the saying goes, there's more than one way to skin a cat.