If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

While Touch ID has been a part of the iPhone's legacy since 2013, Apple waited until 2016 to add biometrics to its MacBook lineup, and it's not as impressive. An iPhone with Touch ID can register up to five fingerprints, but Macs can only register a maximum of three per account. If that seems unfair, there's an easy trick to doubling that number, meaning six of your fingerprints could unlock your laptop!

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

There might not be a better brand partnership for the speedy Sonic the Hedgehog character than a fast-food restaurant. For that matter, augmented reality is also the ideal technology for promoting a movie that features an animated talking rodent living life in the real world.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's even better since you can now add attachments to your reminders, such as photos, documents, and webpages.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Lebron James, or King James to his royal subjects, is extending the reach of his kingdom beyond basketball and into the realm of augmented reality.

Badges? We don't need no stinkin' badges! That is, unless they have augmented reality content embedded in them and give us full access to Facebook's annual F8 developers conference — in that case, yes, we'll take all the badges.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Fans of The Walking Dead can now kill time until the series returns from its winter hiatus by raising walkers from the labels on bottles of wine influenced by the show.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

Lowe's Home Improvement has been an early adopter of augmented and virtual reality in their business practices, so it was a bit of surprise that their name was absent from the ranks of companies launching ARKit apps last week.

While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight.

As with any new smartphone (but especially with Apple), the iPhone 8 is generating rumor after rumor. This newest rumor, however, rocks the boat a bit, as BGR reports that the iPhone 8 may release at Apple's standard time in the fall, but the 3D camera will be pushed to the 8s.

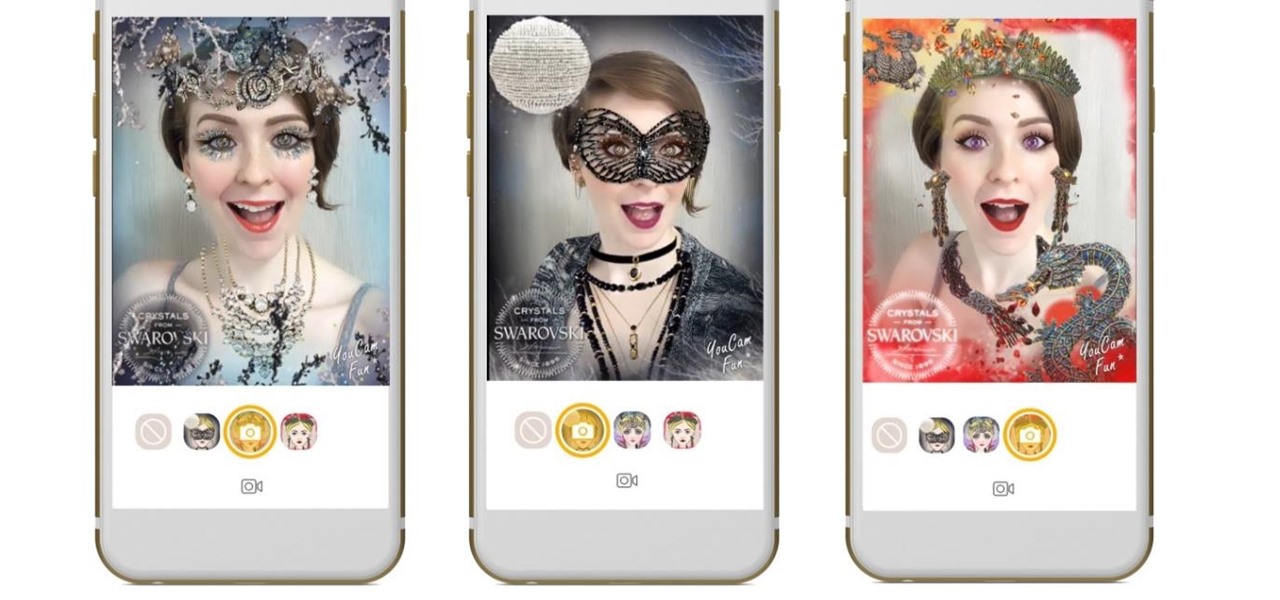
Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

Welcome aboard my inquisitive comrades. I am starting a new series that nobody expected coming. It may not seem very exciting at first, but await the last few parts as many startling discoveries will be made. This is a series which I plan to continue after the completion of Nmap, unless you have major objections.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

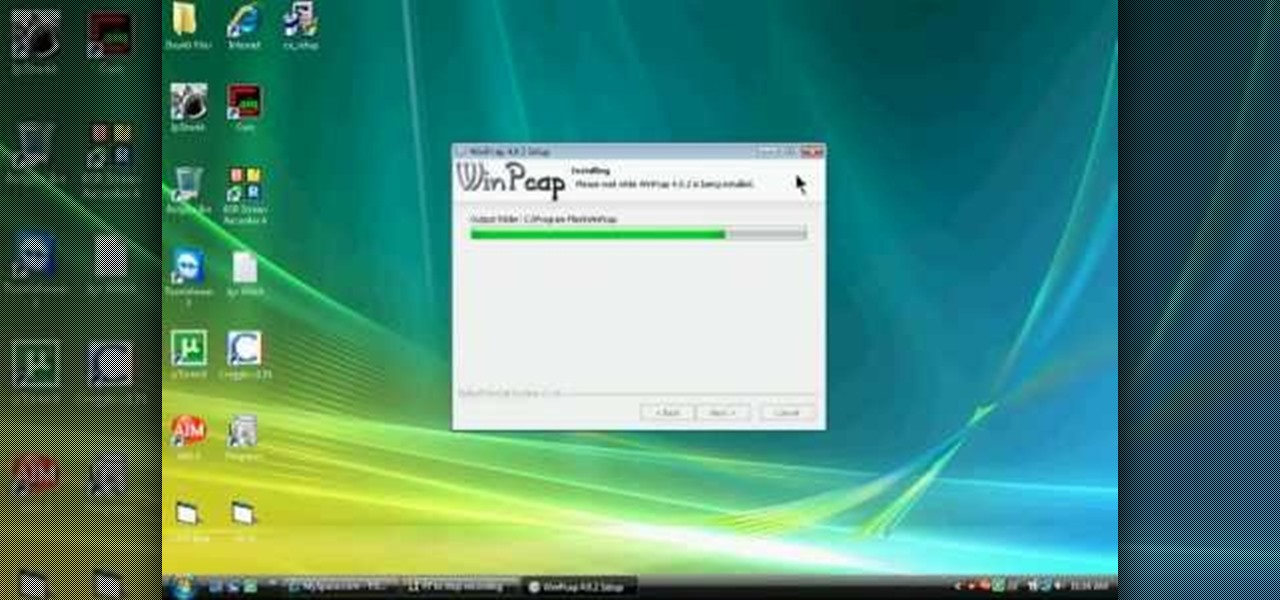
First you have to install program, called 'Cain and Abel'. Then, you will be automatically asked to install 'Win Pcap' and you should do that. After installation you have to click on 'Cain and Abel' program icon with right mouse button and start it as administrator. Then push blue plus sign to scan Mac addresses. After scanning go to the bottom of program window and press APR tab. Then push blue plus icon again. When table appears push first option in first square and first option in second a...

The TSA has placed new laptop bag procedures, shown in this how-to video, into effect. As expected, there have been a few folks who thought they could just leave their laptops in any old bag with cables and gadgets galore. The TSA expected some confusion and just like any new procedure rolled out, hopes that the majority of folks will get the hang of it pretty quickly. This video travel tutorial demonstrates the proper procedure for scanning a laptop at the airport.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

Roughly six months after emerging from stealth, AR cloud company 6D.ai is now ready for public consumption, and it has a big name partner to help it kick off its platform.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Last week at Mobile World Congress 2019, Google put an augmented reality twist on its annual Android Partner Walk via its ARCore toolkit.

The availability of space for filming immersive content has just gotten bigger with the launch of Innovation Studios by Sony Pictures Entertainment.

Setting up Face ID is simple, but getting it to work correctly every time is a different story. While there are numerous tips for getting Face ID to work every time you need it on your iPhone X, XS, XS Max, or XR, Apple has added a better option in iOS 12 that lets you add an "alternative appearance."

When traveling or sightseeing, you may come across a landmark you can't quite identify and want to know what exactly it is and the history behind it. It could be a building, waterfall ... anything. If there are no signs around or they're in a different language, you'll have no idea what you're looking at. Fortunately, Google Photos can be your personal tour guide with the power of Google Lens.

Not content to just be a provider of rugged smartglasses for enterprise users, DAQRI has made the jump into the AR software side of the industry with its new Worksense productivity suite.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Nowadays, with the convenience of online shopping, brick-and-mortar retailers and malls have to work harder to draw shoppers to stores. This year, many of them are turning to augmented reality for assistance.

Marketing and healthcare, two of the leading industries in the adoption of augmented reality, continue to demonstrate applications for the technology in their businesses. Meanwhile, improvements to augmented reality devices are just around the corner with new developments from two display makers.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.