When you're browsing the internet on a computer, you just need to hit Ctrl F (or Command F) and type something out to find all instances of that word in the webpage. It's a handy feature baked into most browsers (nearly all mobile browsers have a "find" feature, too), but unfortunately, it doesn't work with real-world documents, signs, and menus—or at least it hasn't, up until now.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.
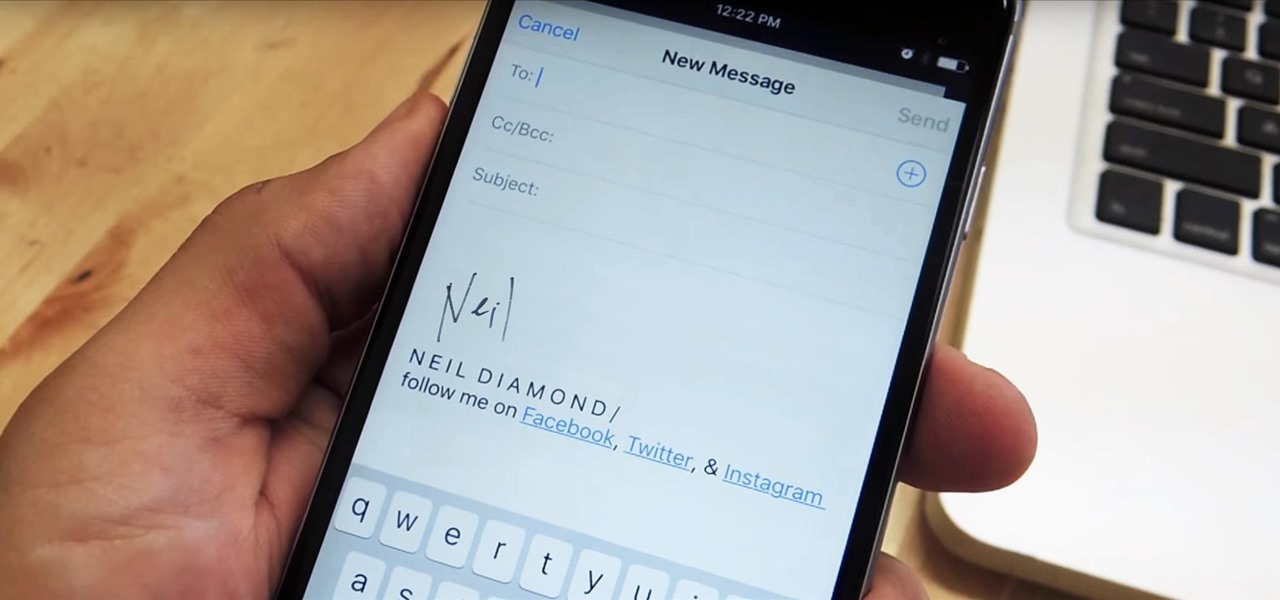
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.
There's a handy new feature in Windows 7 called the Ease of Access Center, which brings together settings and programs that can make your PC easier to use. This is where you get quick access to programs like Magnifier, Narrator, On-Screen Keyboard and more. Learn about the accessibility.

Windows 7 has a new feature called Device Stage. It's a powerful and handy hub for all of your electronic gadgets that connect to your PC. It's device management for the power user! Microsoft shows you the layout real quick, so watch and learn.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Apple released the first public beta for iOS 14.3 today, Friday, Nov. 13. The update includes ProRAW support for iPhone 12 and 12 Pro, upgrades to air quality in Weather, support for the PS5 controller, among other new features and changes.

Apple released the first developer beta for iOS 14.3 on Thursday, Nov. 12, only to pull the update back, push it back out, and finally release it for real. An afternoon marred by Apple server issues spanning macOS Big Sur downloads to iMessage and Apple Pay could have been part of the issue. The new update for iPhone adds ProRAW support for iPhone 12 Pro and iPhone 12 Pro Max.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

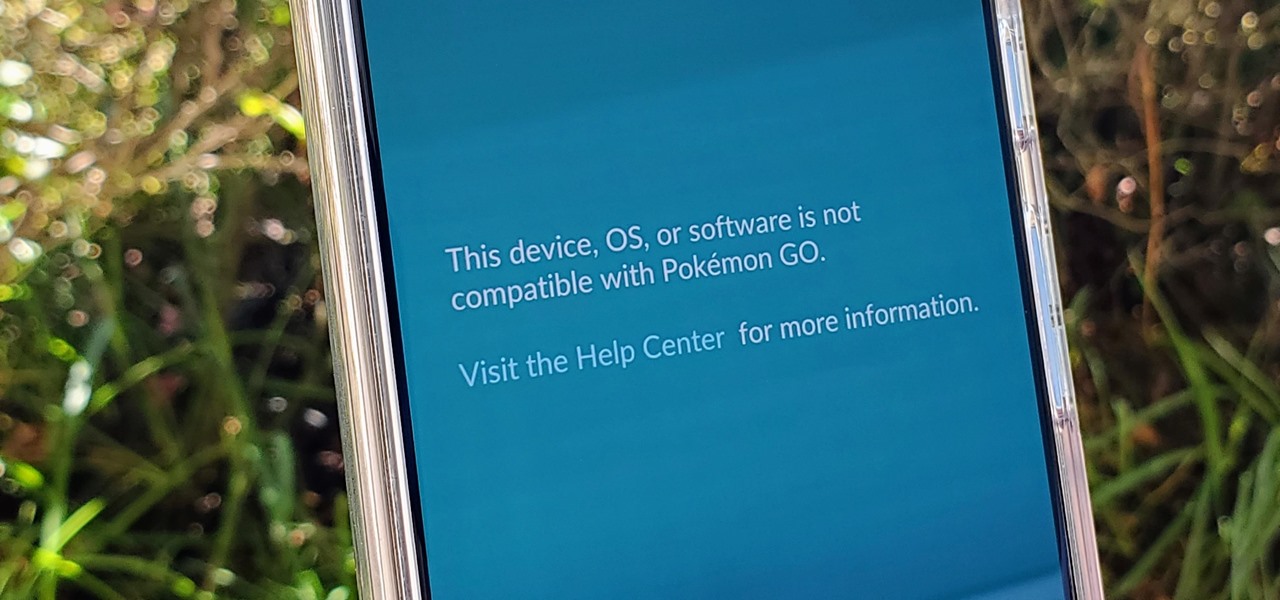
If you're a root user who has played Pokémon GO over the years, then you're probably familiar with the detection methods used to spoil your fun. The game's developer, Niantic, has publicly mentioned their ongoing battle with rooted Android phones and are unwilling to let up. They have a no-nonsense approach to try and keep you from playing, and they've stepped their game up once again.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

iOS 12 has a feature that lets you instantly share saved Wi-Fi passwords with other iPhone users, but it can be finicky when you're sharing with multiple people. Then there's an even more pressing question: How do you share your password with Android users? Thankfully, there's a Shortcut that can solve these problems.

Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

ARKit is a marketer's dream. By providing tools for creating augmented reality experiences on mobile devices, AR apps can now be deployed easily alongside just about any campaign. As expected, we now have ARKit apps pushing wares ranging from automobiles to tequila.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

In the era of smartphones and cloud-based computing, it almost seems irresponsible to keep a stash of paper documents. Not only is a physical paper printout environmentally impractical, it's also a lot harder to organize and keep track of than a digital file stored on a hard drive.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

As the U.S. inches closer to herd immunity and reopening after the pandemic, it may become necessary to keep your COVID-19 vaccination cards on you at all times to gain access to places and events that are prone to spreading the coronavirus. You probably won't want to lose your card, so it may be wise to load a copy onto your smartphone for easy access.

One of the most iconic architectural landmarks on the planet, the Arc de Triomphe in Paris, France, will become a part of augmented reality history thanks to a new project from Snap.

With fears over the COVID-19 pandemic subsiding, live concerts are returning. And Doritos wants to send music fans to a few of them via an augmented reality promotion.

Niantic recently added a new Field Research task type called AR Mapping that challenges players to capture video footage of PokéStop landmarks and upload them. In return, players receive rewards in the form of in-game items.

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

OpenVAS is a powerful vulnerability assessment tool. Forked from Nessus after Nessus became a proprietary product, OpenVAS stepped in to fill the niche. OpenVAS really shines for information gathering in large networks where manual scanning to establish a foothold can be time-consuming. OpenVAS is also helpful for administrators who need to identify potential security issues on a network.

Whether you're a professional mechanic, a hobbyist, or someone who just wants to know why their check engine light came on, your Android device and an OBD-II adapter can provide insight as to what's going on with your car. Most adapters sell for less than $10, and once you plug it into your vehicle, you'll just need a good app to help you make sense of all the data it can gather.

In the tech world, when you're a small startup going up against the Goliaths and their massive marketing budgets, you're forced to find and produce something almost magical to help your product stand apart from the rest. And that's exactly what Occipital Inc. has done with their Bridge headset.