Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Hackers can be notoriously difficult to buy gifts for, so we've curated a list of the top 20 most popular items Null Byte readers are buying during their ethical-hacking studies. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2017 selection of hacker holiday gifts — just in time for Christmas.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

I was bored when I found this piece of literature: ==Phrack Inc.==

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Welcome back, my greenhorn hackers!

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

Welcome back, my novice hackers! I've written a couple of articles on reconnaissance and its importance, and as I've said before, a good hacker will spend 3 to 4 more times doing reconnaissance than actually exploiting the system. If your recon isn't good, you'll likely fail, or worse—end up serving time and becoming Bubba's wife for a couple years. I can't say it enough—recon is critical.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.

It seems that cupcakes are the designer foodstuff of choice these days. They're really not all that different from cakes (they're made from the same dough, after all), but their miniature size makes them individually portioned for convenience and also a great base for adorable decor.

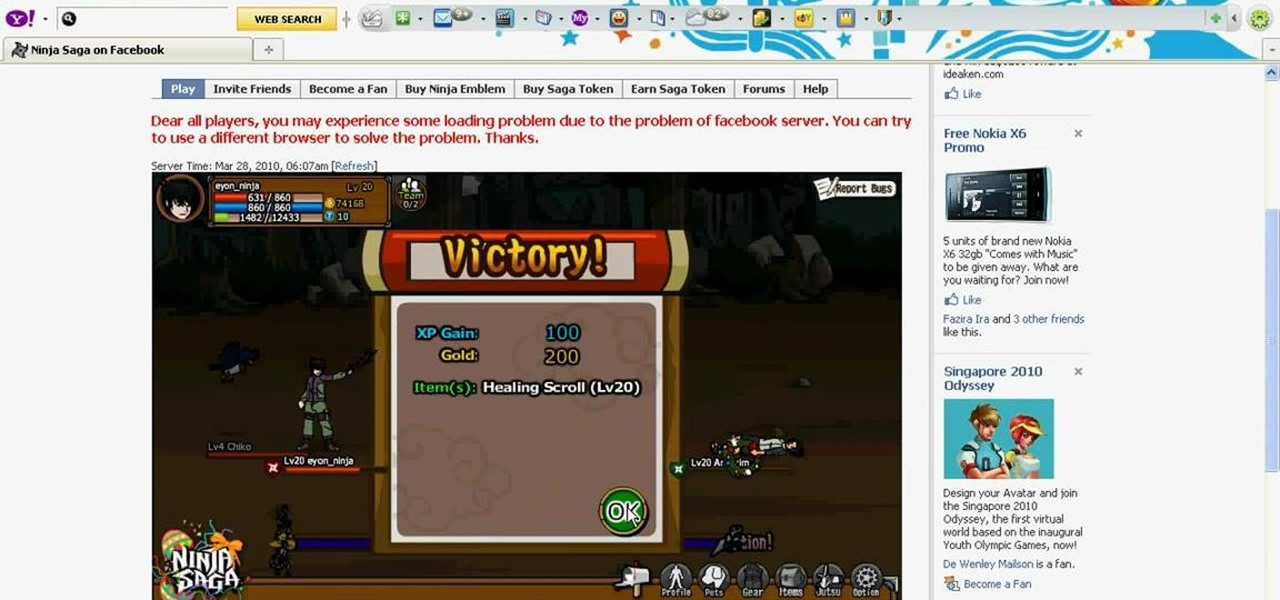
Want to vanquish even the toughest of foes with the greatest of ease? This hacker's how-to demonstrates a method for killing your Ninja Saga enemies with a single hit.

Looking for a way to generate an unlimited amount of Pet Society coins? Look no further. This hacker's how-to will show you how to hack Pet Society's frisbee & ball games to generate more digital cash money than you could ever spend.

No matter how you cut it, slides are tons of fun. There are all types of slides, and while some are big and scary, many are not. Regardless of whether you are having a blast on some mellow slides or trying to set a world speed record on something large there are a few techniques which will help you ensure success. Watch below as Shane helps us out with some basic slide technique:

You should encrypt everything. These are what you need: BackTrack 4,0, modify IP tables, Python and ARPspoofing. Program the PC to flip to forwarding mode. Adjust the programming in the IP tables. You are convincing the host and the client that the man (PC) in the middle is the host and capture passwords, user names and other information from unsuspecting clients. This program strips the "S" from "https" which make your computer vulnerable to hackers. You need to observe the address bar and m...

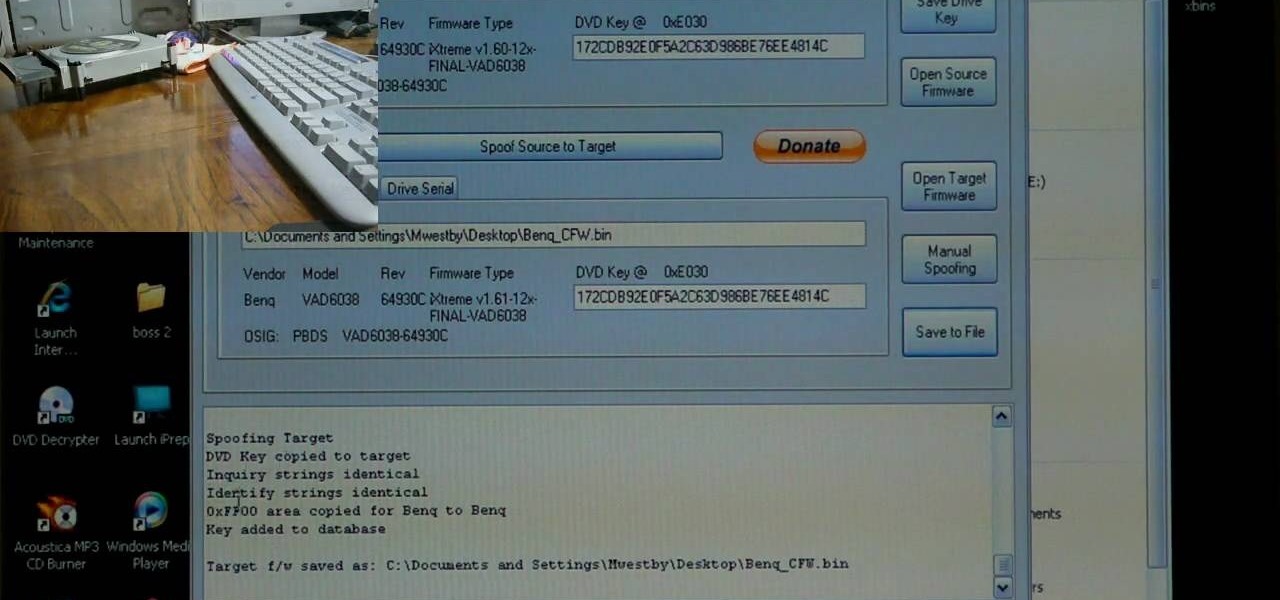
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

Bobby pins have been integral tools in a girl's makeup case since the 1920s, when bobby pins were used to secore the fashionable hair bobs of the Jazz Age. They've also recently been used by young boys and hackers to pick open locks. And now you can add one more fun use to the list.

Identity theft is a huge problem and one of he fastest growing crimes in America. A number of credit card companies now issue credit cards with embedded RFIDs (radio frequency ID tags), with promises of enhanced security and speedy transactions.

Most people find the default SMS background for the iPhone fairly dull, so why not spice things up? Thanks to Cydia and some clever hackers, there is now a way to modify the background of your text messages!

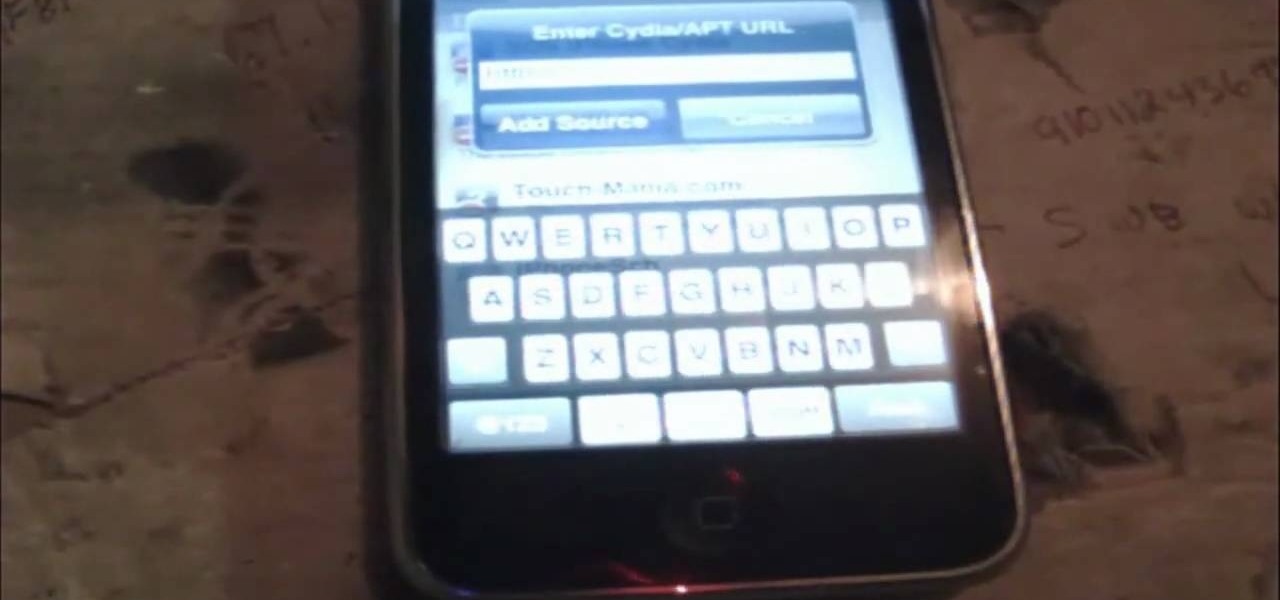
Worried about not being able to get Cydia on the 3.0 firmware? Never fear! Hackers are here! Check out this video to learn how to jailbreak your iPhone using redsnow to get Cydia. With Cydia, a whole world of iPhone and iTouch hacks and cracks are at your fingertips!

In this how to video we show you how to utilize a pen and paper to conceal a small cheat sheet right under your nose but out of view from everyone else.