
How To: Twitter's Massive Security Flaw Makes Your Password Easy to Hack
What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.


What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

This was a one shot prank that requires prepping. Earlier in the day, I told the victim, that I wanted her to do a promo for my "New Easter video". I told her to go outside, get my bunny and come back inside to show it to the cameras. Have one guy dress up in the scary bunny outfit so when she opens the door to the balcony she'll see the scary bunny. This prank is tons of fun to watch! Use this as inspiration for one of your April Fools Day pranks!

The Windows Phone 7 platform has been out long enough now that hackers the world over have had ample time to play with it, and the fruits of their labors are coming fast and thick now. This video will teach you how to unlock or "jailbreak" (misnomer in this case) your Windows Phone 7 with ChevronWP7 so you can install custom ringtones and perform other power-user functions. You'll also need the certificate for it, ringtone manager, and the Windows Phone Developer Tools.

With custom ROMs said to be impossible on Verizon's new Motorola Droid X, thanks to something called eFuse, many users will be deterred from trying to mod their Droid X mobile device. But it's only a matter of time before a hacker figures out a workaround for the Droid X, but if you want to try to hack it yourself, this video tutorial will get you started. It will show you how to get into the Droid X bootloader. It could possibly help you "root" the cell phone, if you're lucky.
Hacking the Wii is a fun and not-too-challenging way to have a lot of fun with your console and give yourself a geeky sense of accomplishment. This video will show you how to hack a Wii from any region and with any firmware version between 3.2 and 4.2 using these files for versions 4.1 and below and these for version 4.2. If you've already upgraded to 4.3 that's too bad, because as yet 4.3 is hackproof. You'll just have to wait for the hackers to figure it out.

Note that is always best to try and avoid a hangover in the first place by pacing yourself and drinking lots of water before sleeping. But if you find yourself hungover follow our directions for a faster route to feeling better.

This weekend, hackers broke into the servers of the popular shoe shopping site Zappos, giving them access to the personal information of 24 million Zappos customers. The user data taken included names, email addresses, billing and shipping addresses, phone numbers, the last four digits of credit card numbers, and encrypted passwords. However, full credit card data was not lifted, and passwords were cryptographically scrambled.
BitLocker. What is it? And what can it do for you? Well, it's a handy new feature built-in to Windows 7, and it can help protect all of your data from loss, theft, or hackers. It's the easiest way to make sure your documents and files are safe from the devil's hands.

Bead frames are pretty simple to understand. Rather than simply stringing beads onto a pendant or necklace, you can attach them to bead frames, which come in all shapes and varieties, to make a novel design that can take advantage of negative space. It goes without saying that elaborate bead frames make the entire design more ornamental, whereas a simple round wooden bead base helps put the spotlight on the bead in the center for a subtle glamour.
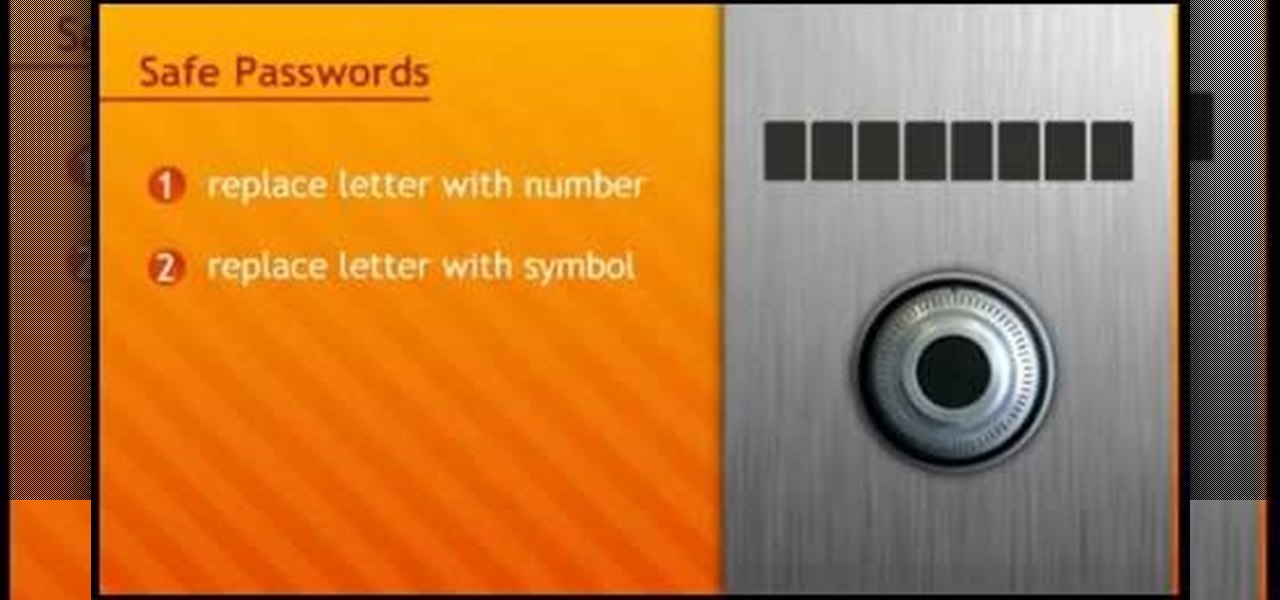
In this tutorial, we learn how to make a safe password. Passwords are essential, and need to be safe for when browsing around the internet. Other people aren't meant to be able to nose around your information, so protect your information with an indecipherable password. Don't choose a password that is easy to crack, never use personal information. A random number in the phone book isn't a good idea either, software used by hackers can crack these. Make sure your password is 8 characters long ...
Having security setting on your web browser is a pretty important tool. It keeps you safe from potential hackers and makes sure you don't visit unsafe sites that could lead to a virus. But sometimes the security settings on a web browser can be a pain and the best choice would be to turn it off. So in this tutorial, you will learn how to easily change the security settings to INternet Explorer 8. So sit back and enjoy!

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...
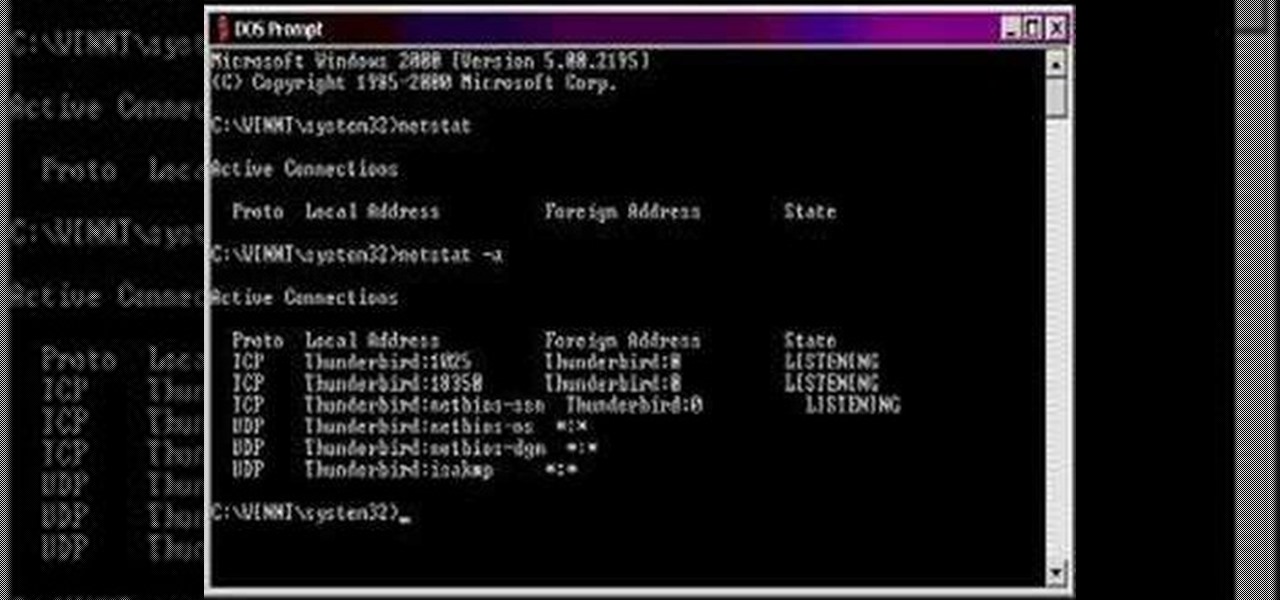
In this how to video, you will learn how to keep your Windows operating system secure by look for and closing open ports. First, you will need to run the program called Net State. Once this is open, type in netstat -a. This will list main connections. Next, type in netstat -an. This will give you the numbers of ports that are open. Some may be used for file sharing and anti-virus programs. If you want it completely secured, you should only have one running. This video shows you how easy it is...

Hacker Daily teaches you to how to make a rocket "outta trash". They take a bunch of everyday materials (paper towel roll, body spray cap, paper cup glue gun, scrap cardboard and a model rocket engine) and create a rocket, by first cutting cross hairs in the bottom of the cup and gluing the rocket engine inside. The video than tells you to insert the paper towel roll trough the bottom of the cup. Than they tell us to glue the body spray cup on top of the "rocket". After adding fins the rocket...
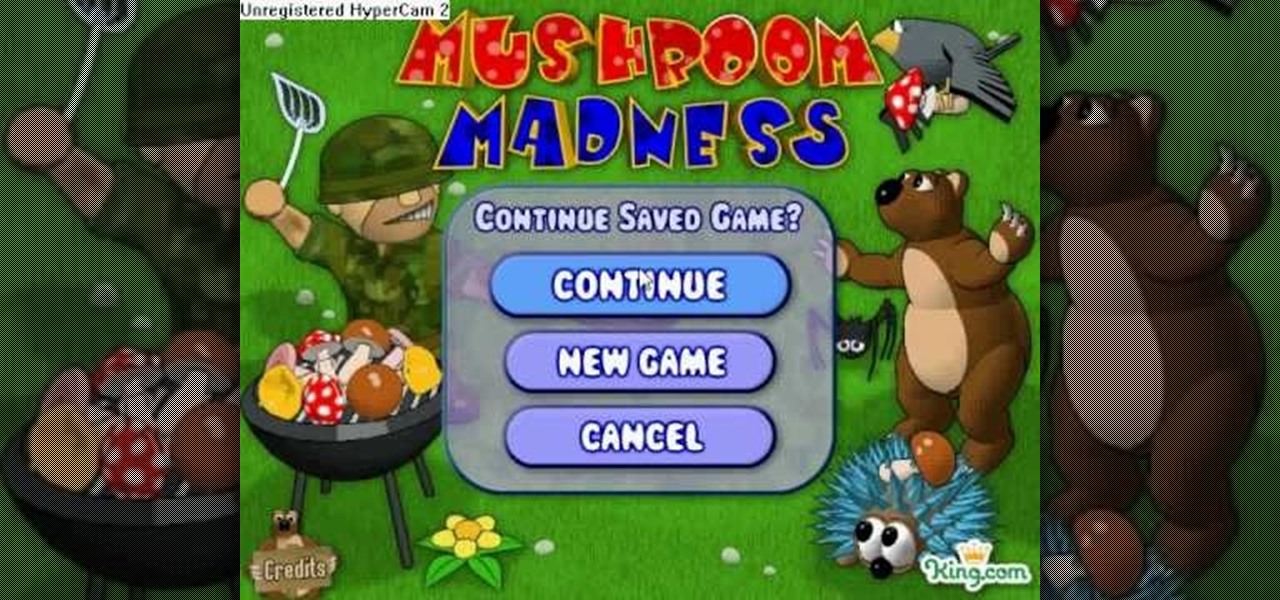
YouTube user Hacker of None teaches you how to hack Mushroom Madness using Cheat Engine. Start the game from Kongregate website and then run Cheat Engine. Search for your browser, which may be Firefox, Chrome or Internet Explorer, in the Process List and then click Open. Change the Value Type to Array of bytes and make sure the Hex box is checked. Then simply enter the values provided in the video to access the hacks. These give you one hit kills, unlimited ammo or no money will be needed. En...

Notorious hacker Chris Tarnovsky opens his underground laboratory to WIRED, providing a peek into the world of satellite television smart-card hacking. This complicated process involves nail polish, a pin head and various acids -- so don't try this at home (unless you're Chris Tarnovsky)! Chances are you won't even know what's going on here, but that's not going to stop you from watching this video tutorial on how to reverse-engineer a satellite TV smart card, is it?

In this video tutorial, you'll find a step-by-step guide to how a n00b hacker (like you?) can get usernames and passwords easily through one of the security flaws of the Ethernet ADSL router. More than half of Internet users never change their default password which makes this "hack" easy. Take your time to read the text on the slide. For more, and to get started testing the security of your own Ethernet ADSL router, watch this hacking how-to.

Notice: This is probably not new to many people. This *IS* new for some people however, and meant for them! Post interesting cameras you find.
Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

2020 has been a rollercoaster of a year for all of us, the type of year that makes you feel like you're not sure if you're upside down or right side up. But as the holidays arrive, it's time to get your bearings back and find the good in the world — the type of good that we could use more of right about now.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.

The Halloween season is the perfect time for telling scary stories, but augmented reality is here to bring the tradition of frightening children to the modern age.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Scary movies seem to be a natural fit for augmented reality experiences, with the latest example coming from the Insidious film franchise.

Sending fleets of ships into battle as an ancient Nordic god? Sign me up.

Matteo Pisani, CTO and co-founder of Remoria VR, has managed to do something the folks over at Google said couldn't be done for at least a couple of years. With a little bit of tinkering, Pisani was able get his Google Daydream VR headset and remote to work on an iOS device.

Lightning is scary and powerful, yet when harnessed correctly, it can become a beautiful pattern for hand-crafted wooden furniture. Muchd like Zeus in ancient mythology, Canadian Woodworks is harnessing the power and beauty of lightning, but they're doing it for aesthetic purposes.

The highly anticipated VR headset hasn't been on the market long, but there's an issue that has some consumers, and even government officials, concerned about the Oculus Rift. You probably guessed the issue surrounds privacy and the extensive, not-so-secret way that it's collecting your personal data. The privacy concerns came about as various customers and media outlets took notice of the rather lengthy Terms and Services that pop up once you strap yourself into the Rift headset.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

By now, you've likely used or have seen friends and family use Face Swap Live on their phones. It's a fun little app for iOS (and soon to be Android) that harnesses current tech to—you guessed it—swap faces.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

Welcome back, my greenhorn hackers!

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

This is a really tasty "scary" snack as it incorporates a lot of the flavours you'd usually put together (along with the almonds)

Baking thinly sliced salami in the oven changes it to an awesome and savory crispy snack. They're dippable, crowd-pleasing, and healthier than your average slice of salami —the amount of oil that drains from each slice is a little scary!

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.