During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.
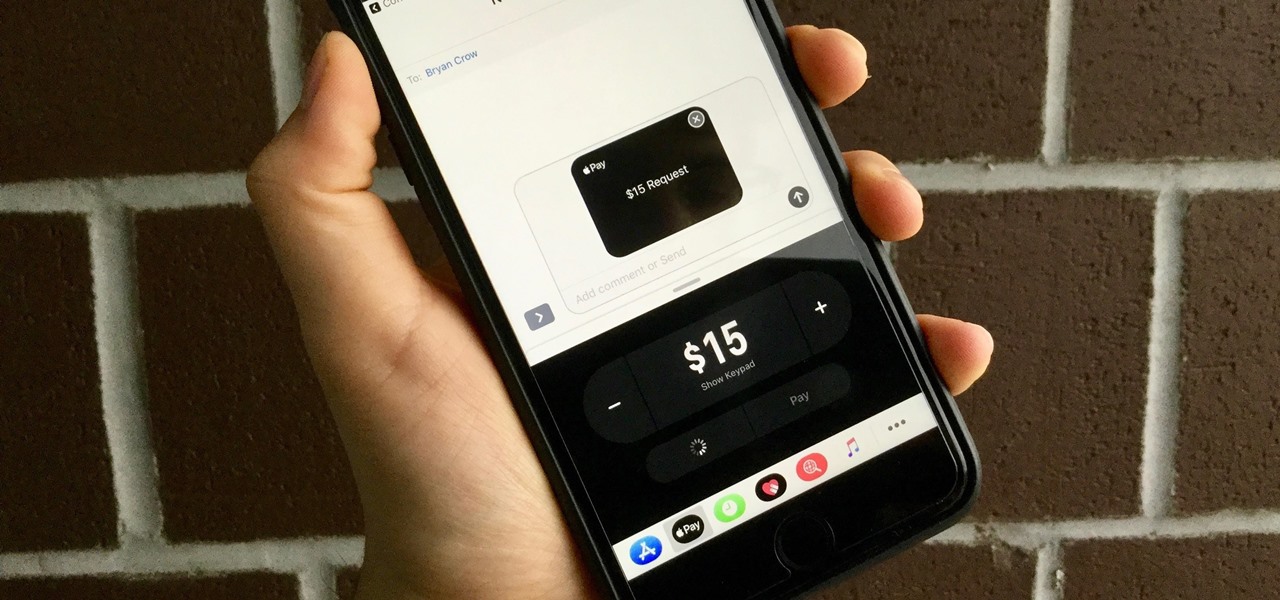
With the release of iOS 11, Apple promised to give us person-to-person transactions by way of iMessages. In the iOS 11.2 update, the new Apple Pay Cash system is now ready for you to send money to family and friends right from your iPhone — and there are multiple ways to get it done.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

While iOS offers a plentiful mix of excellent and exclusive features, what you see is what you get. Apple doesn't leave much room for customizability, meaning most people's iPhones look relatively the same. You can make yours stand out, however, by giving your apps unique and personal icons.

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

In my last article, I explained why text adventure games are some of the most Steampunk computer games out there. I even shared a free Steampunk text adventure game that I'd made myself!

Safari has a new feature that helps you discover the most beneficial aspects of a webpage without having to dig through the page or read the entire thing — and it works on iPhone, iPad, and Mac. It can make web browsing more efficient and websites easier to navigate while ensuring the visibility of important details.

Some iOS and iPadOS apps offer alternative app icons you can switch between. Beyond that, you'd have to create aliases in the Shortcuts app to customize the look of the app icons on your Home Screen. But that would mean two icons for each app in the App Library. Now, in a new software update, Apple has given us a middle ground for Home Screen icon customization.

Emoji have taken over the world, so there's a good chance you regularly use (or overuse) emoji on your iPhone's keyboard just like everyone else. But before emoji were popular, there were emoticons, short for "emotion icons" — and iOS has a secret emoticon keyboard just waiting for you to unlock.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

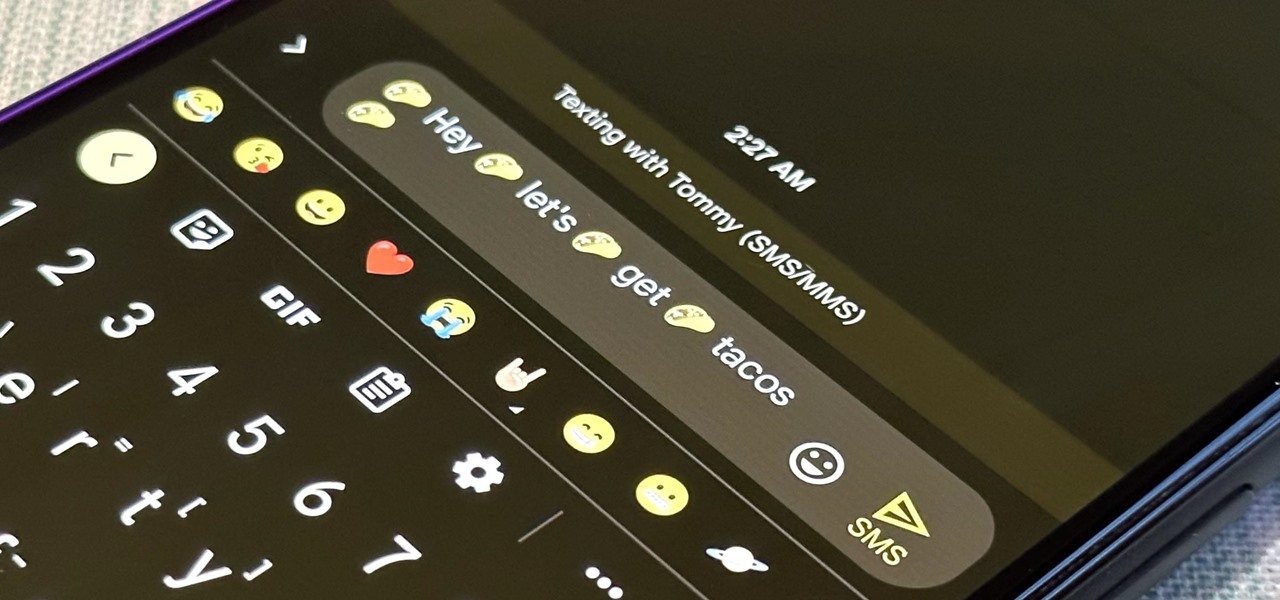
Emoji characters make messaging more fun, and Google has continuously added convenient and fun ways to insert playful symbols into your conversations using Gboard. After getting Emoji Kitchen in early 2020, we now have Emojify, a tool that automatically adds emoji to your message drafts.

Emoji characters give you a multitude of colorful characters to express yourself with on social media and within messages, and stickers give you even more symbols to play with. While Android and iOS both have a healthy arsenal of emoji and stickers, Android goes a step further for even more emoji madness.

If you're not using your iPhone's Files app yet to manage images, documents, and other files on iCloud, third-party cloud services, or your local storage, it's time to start. Apple's built-in file manager is finally a powerhouse with many tricks up its sleeve in the latest software update.

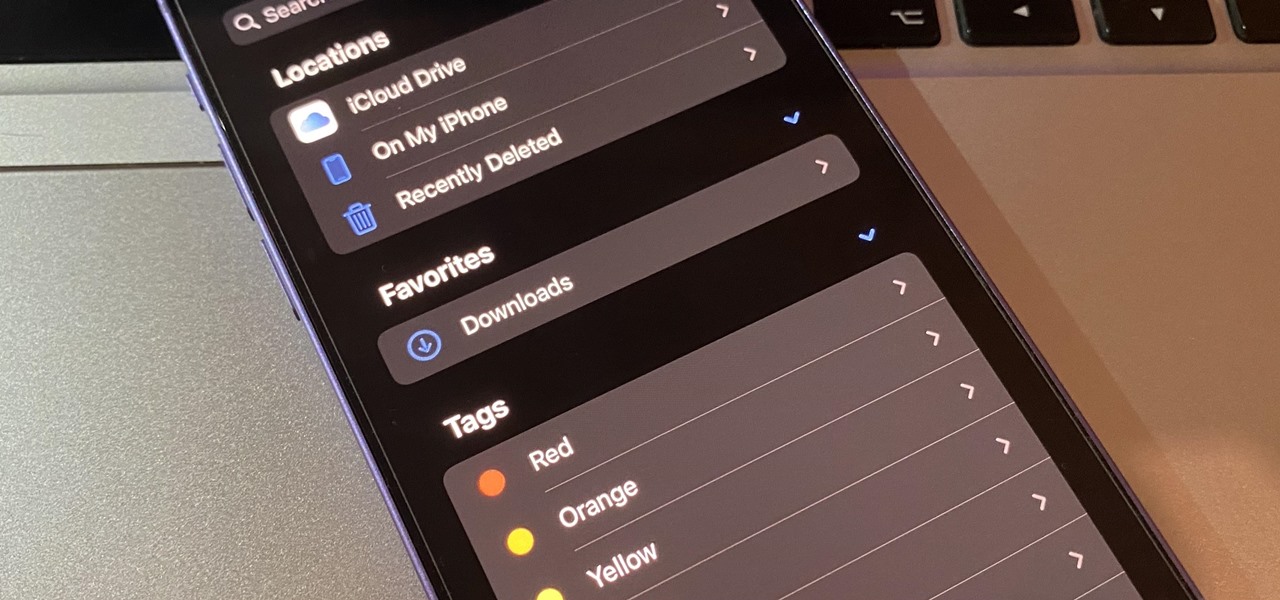
The standard way to sort your notes and to-dos in Reminders has always relied on you putting them in the correct list and group. Then came smart lists for flagged and scheduled tasks, followed shortly by a smart list for tasks assigned to you. In iOS 15, Apple brings yet another way to find your reminders more easily — tags.

If you're not planning to upgrade to a new iPhone 13, the new version of the iPhone operating system will breathe some new life into your iOS device.

Two brands with affinities for augmented reality, Marvel and the NBA, joined forces to inject some AR superpowers into Monday night's matchup of the Golden State Warriors and New Orleans Pelicans.

Apple's Reminders app has come a long way. In the past, if you really wanted to keep track of your important daily, weekly, and monthly tasks, you needed to install a specialty third-party app to make it work. While those apps still offer valuable features, Reminders can get the job done for many iPhone users now. With iOS 14.5, Apple only sweetens the deal.

TikTok is a video-platform first, and while visual content is critical to its popularity, what has carried many of these videos to millions upon millions of views isn't only what you see but what you hear.

Apple's big iOS 14 update includes Memoji improvements such as new hairstyles and headwear to choose from for your personalized Animoji character. Even better, there are now face coverings, so you no longer have to resort to that one masked emoji to get the point across in these times of COVID-19.

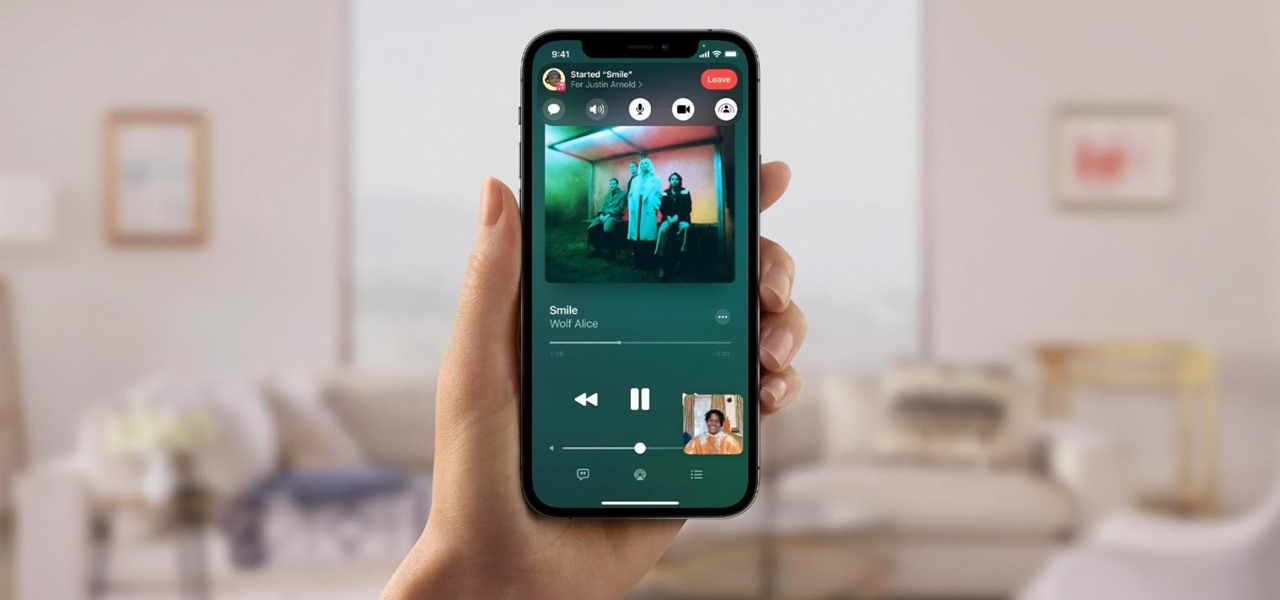
Facebook Messenger is a messaging app first, but of its more than 1.3 billion monthly users, 32 percent use its video chat feature at least once every month. While it may seem pretty straightforward to video call with family and friends on Messenger, there are many tips and tricks that can help enhance your experience.

Apple released iOS 13.0 on Sept. 19 and announced on the same day the release of iOS 13.1 on Sept. 30. But that deadline was pushed up to Sept. 24, and that's why we have 13.1 just five days after 13.0. But that's good news since we don't have to wait any longer for some of the features promised in iOS 13 that didn't make the first cut.

Typography is an important aspect of the video editing process. You deal with it when adding captions to news clips, giving on-screen recipes in food videos, creating burned-in subtitles for short films, making no-sound-needed videos for social media, and so much more. Enlight Videoleap for iOS makes this all easy.

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

So, you rooted your Pixel 2 or 2 XL and everything seems to be working quite well. However, a month passes, and you get a notification to install the monthly security update. Like clockwork, Google has been pushing out OTA security patches every single month for a while, but there is a new problem for you at this point — as a rooted user, you are unable to apply the update correctly.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

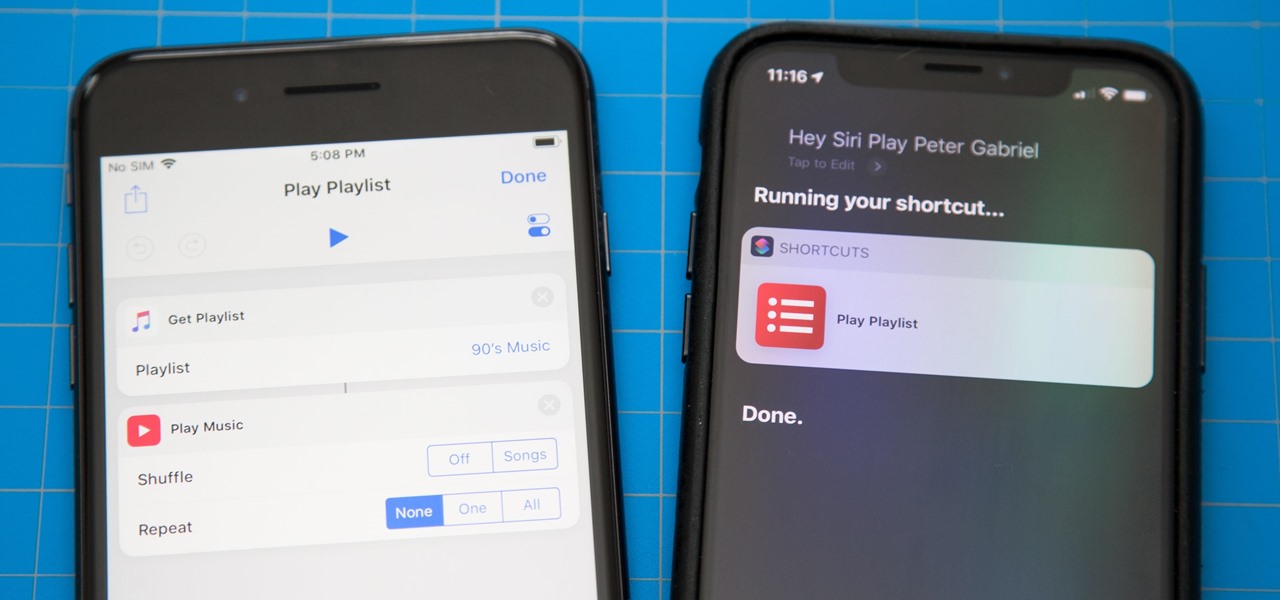
One of the most exciting additions to iOS 12 for iPhones is called Shortcuts, a tool integrated with Siri to help you get things done faster. While there are a few recommended shortcuts available to you in Siri's settings in iOS 12, the Shortcuts app brings the functionality of Workflow to Siri so you can build your own custom actions or select from the gallery of available shortcuts.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.