The next generation in mobile communications has officially arrived. A new "Universal Profile" was just published to help carriers and OEMs enable Rich Communication Services (RCS) on any of their smartphones, and the standard hopes to replace SMS with a feature-rich, iMessage-like experience on all phones.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

Bigger and faster. Two words that are pretty much always wanted no matter what the scenario is. The new PlayStation 4 has been out for only a few hours now and people are already looking for ways to one-up their friends and upgrade their already awesome systems.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

Obviously, millionaires like me don't really have to worry about an empty wallet, but for the rest of you out there, having no cash when it comes time to paying a bill can be excruciatingly embarrassing.

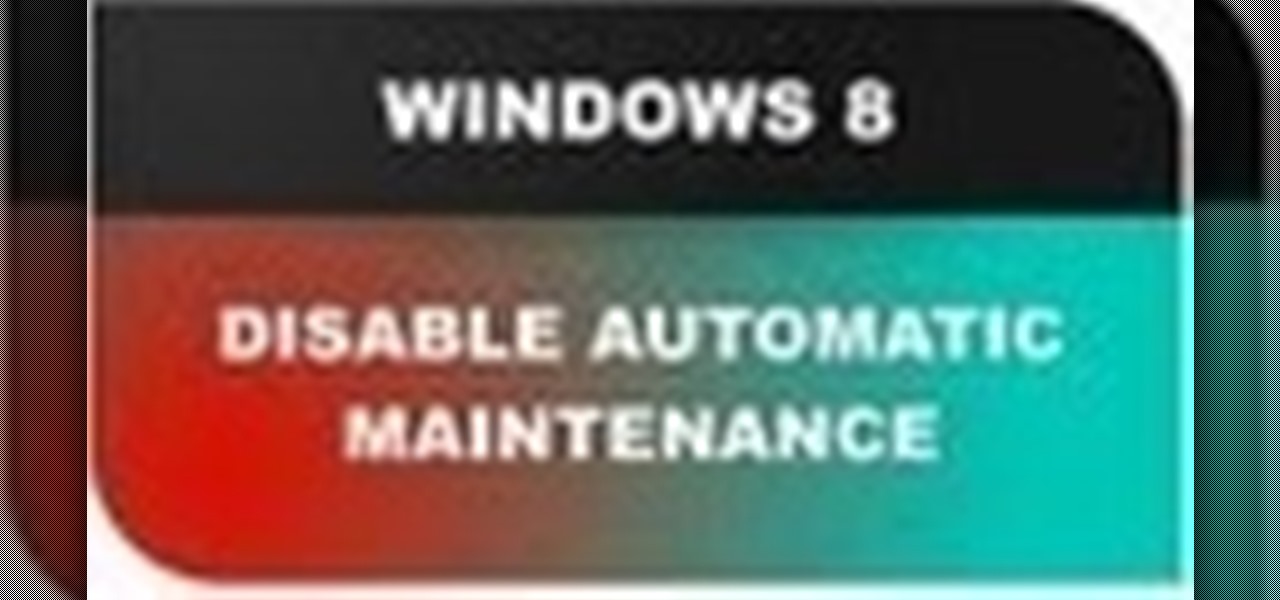
In this Windows 8 Tutorial you will learn how to disable automatic maintenance. Their are really two situations I can think of when you would want to disable automatic maintenance in Windows 8. The first being if your Windows 8 computer came with a Solid State Disk then you will probably want to disable automatic maintenance. The reason being is that a solid state disk does no benefit from defrags and the automatic maintenance automatically defrags your hard drive and this will take away from...

With the Samsung Galaxy S III being a hot commodity, it's no surprise that your friends might try unlocking your fancy password-protected phone. While some friends have good intentions when using your phone, there are those certain friends who get into the phone to do this... The worst scenario might be that you leave the phone around a group of friends, come back and find that all of your social media accounts have been hacked. When you yell out to your friends asking who did it, no one make...

Why do you need augmented reality? Because enterprise, they say. And while that's certainly true for several disciplines, there's still that mainstream use case hanging out there waiting for users to discover beyond the realm of enterprise and gaming.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

The mysterious technology product teased via an eccentric TED Talk nearly five years ago has finally been revealed, and it's called the Magic Leap One: Creator Edition. After all of the non-disclosure agreements, furtive comments from CEOs and insiders given early access to the device, and a seemingly never-ending string of hints dropped by the company's CEO, Rony Abovitz, on Twitter, we finally have a real look at the product.

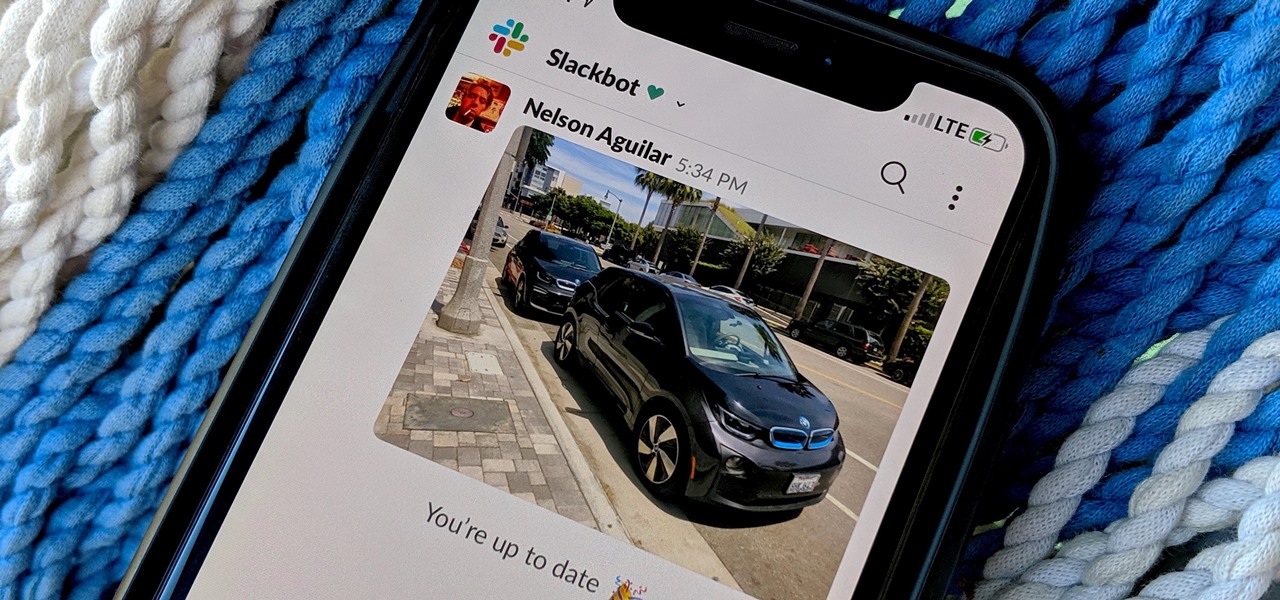
By default, Slack optimizes the images you upload and send to other users in your workspace. Although optimization lowers the resolution of the image, it does send quicker, which is better if your internet service is poor. However, you may want to send the highest-resolution image possible, so how do you stop Slack from sending only optimized and lower-quality photos?

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

The Pixel 3 has an indisputably great camera, but a software update coming soon is going to make it even better. Google will be adding a "Night Sight" shooting mode that's so good with low-light situations that you'll have to see it to believe it.

Scavenging for weapons and supplies in PUBG adds to the element of excitement and dread of the unknown. But this feeling can quickly turn into annoyance as you attempt to swap your weapon for a better one on the ground, only to automatically pick up the gun you just dropped again.

Medical training technology company CAE Healthcare has given birth to the latest example of how augmented reality can help to build practical operating room skills for doctors and nurses. The company's newest product is called LucinaAR, which harnesses the power of the Microsoft HoloLens.

At the Augmented World Expo Europe press conference in Munich today, RE'FLEKT will unveil the addition of remote video calling to their RE'FLEKT One enterprise augmented reality platform, in addition to ARKit and ARCore apps that demonstrate the platform's capabilities.

As we have seen previously with the likes of SethBling's Mar I/O videos and other examples, video games seem to be a great source for training AI neural networks. Augmented reality and machine learning are part of a collection of technologies that seem to be growing toward a point of maturity, and that will likely cause them to be intertwined for the foreseeable future. As developers, machine learning will definitely change the way we create software in the coming future. Instead of going lin...

Forget 3D movies. Warner Bros.' newest patent shows off designs for a mixed reality movie-going experience that will leave other theater-going experiences in the dust ... all in the comfort of your own home.

If you have any group chats going, you're surely familiar with this scenario: One person sends a picture, then, within 30 seconds or so, all other participants chime in with one-word responses like "Cute," or "Awesome." It's a social nicety, so you have to expect this behavior, but that doesn't make it any less annoying when your phone randomly beeps and vibrates ten times in a row because of it.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

This is a familiar scenario: you light up the grill, get cooking, eat the fruits of your labor, then clean up every trace of your barbecuing once you're finished — except maybe the hot charcoal, which usually gets dumped right before the next cookout.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

Hello aspiring hackers, It's been a while since I wrote a tutorial, so I figured I might just share one of the tools that I have created to help the community grow.

You're smashing your keyboard to increase your screen brightness, yet it won't go any higher, but you know you've been able to set it higher before. Angered by this, you get up and move your laptop, only to suddenly notice that the display does in fact get a lot brighter.

Picture this scenario—you're using your phone in a dimly-lit room, then you move to an area with a lot more ambient light, and Auto Brightness kicks in within a few seconds to ramp up the backlight. That's the way it should be, right? But then you move back to the darker area, and your phone takes 30 seconds before it decides to dim back out. Pretty annoying, isn't it?

As messaging and texting have all but replaced the need to actually call someone, emojis have seemingly replaced our need to type out text. With a simple emoji, you can relay emotions like "I don't feel very well" or "I love you" quickly and easily, knowing that the other party will instantly know what you're feeling.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

There are so many mods we can apply using a custom recovery. From themes to bug fixes and feature ports, a typical rooted user spends a decent chunk of time in TWRP Recovery.

There is no better example of a risk-versus-reward scenario than jailbreaking your iPhone or rooting your Android phone. While both jailbreaking and rooting undoubtedly has its advantages, this possibility of something going wrong and you ending up with a 500-dollar doorstop is never too far out of mind.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

Tomorrow's the 1st of April which means it's the one day of the year you can put aside the daily grind, and go at it Dwight Schrute and Jim Halpert style. Yes, there are easy apps to do your dirty work, but if you're old school and you like to do it the old fashioned way, here are 10 simple pranks for torturing your co-workers.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

As you already know, the Galaxy Note 10 and 10+ have gotten rid of the beloved audio jack (RIP). Fortunately, it has never been a better time to switch to wireless. There are Bluetooth headphones and earbuds for every budget and every need.