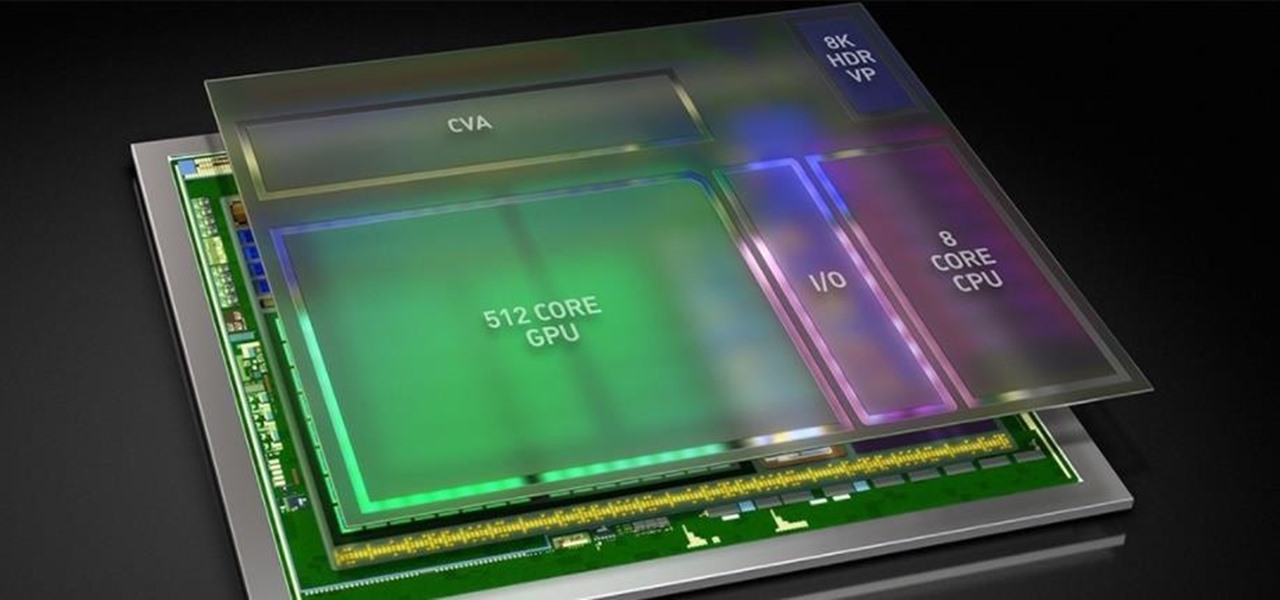
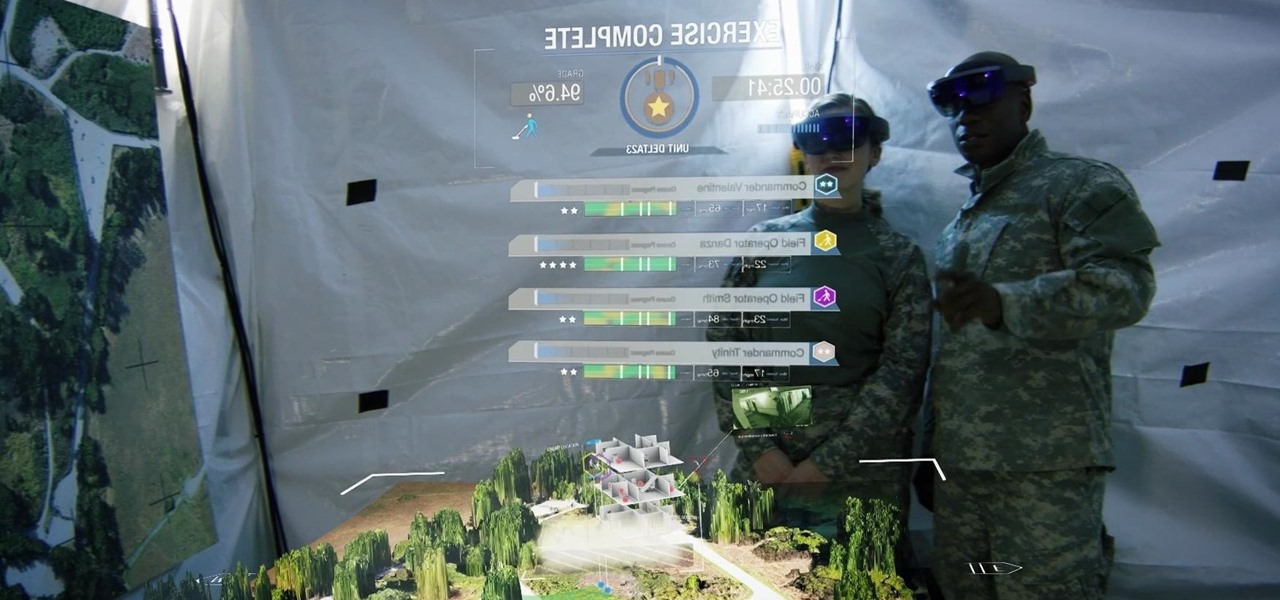
In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.
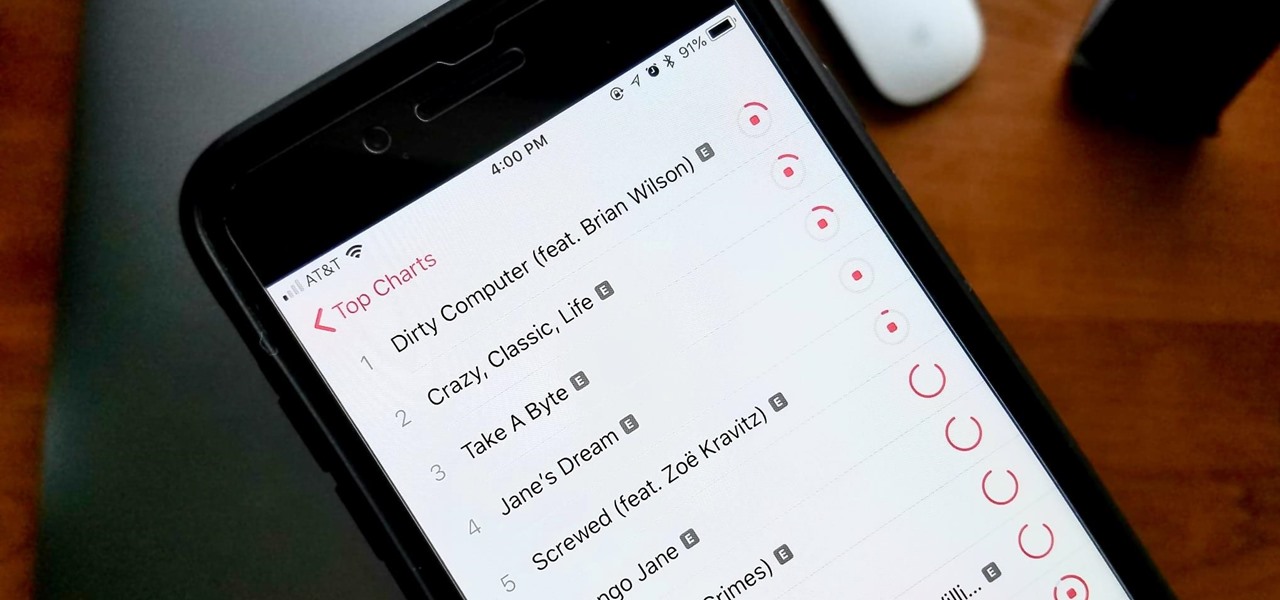
When you've exhausted your data plan, streaming isn't an option unless you want overcharges. While Apple Music makes it easy to download songs for offline listening, you need to add the music to your library first. This creates an extra step in downloading music, but it doesn't have to — Apple Music lets you automatically download any song, album, or playlist that you add to your library.

While the public now knows much more about the Magic Leap One: Creator Edition today than it did yesterday, there's still a quite a bit that's unknown. One of the most significant questions — with any mixed reality product — is the field of view. How much of what we see through these glasses will contain the computer's virtual creations?
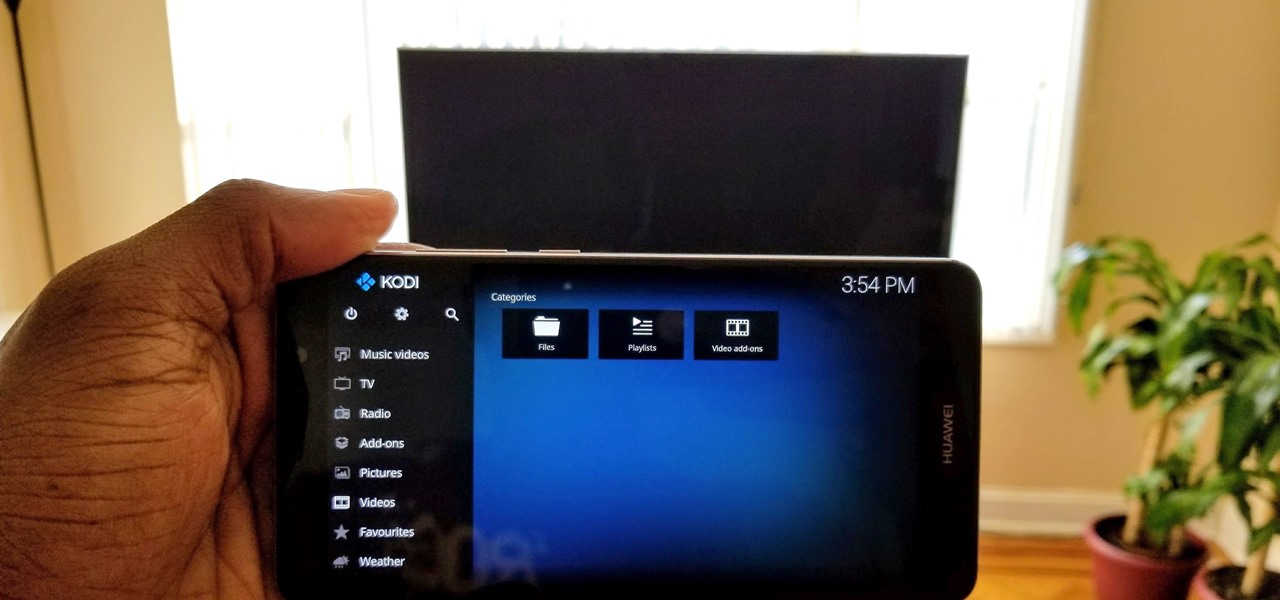
Over the years, Kodi (formerly XBMC) has become one of the most popular media players. It provides all the essential functionality needed for any home theater setup while remaining open source and free. However, Kodi is not limited to just your living room. With the Kodi app for iOS or Android, you get a streaming media player that can act as a video player, music player, picture gallery, and so much more.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

Elon Musk has repeatedly said Tesla models in production today have the requisite hardware to offer "full self-driving" capabilities. But for features more advanced than Level 3, Tesla will, in fact, have to revamp Autopilot's hardware to handle the extra computing load.

It seems that mobile app developers are constantly coming up with new ideas to apply augmented reality, with Apple's ARKit promising to increase adoption in apps exponentially.

As the world goes into a frenzy over the latest strain of WannaCry ransomware, it might be a good time to remember to update all your devices. Yes, those little reminders your phone and computer throw at you every now and then to update your junk can be really annoying, but not without merit.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Electrical impulses course through our heart and keep it beating. That's why a jolt from an automated external defibrillator can boost it back into action if the beating stops. But new research says there may be more to keeping a heart beating than just electrical impulses.

As Intel steps up their investment in driverless technology with a $15 billion acquisition of Mobileye, so have automotive supplier Bosch and NVIDIA teamed up to manufacturer driverless car systems with the much-awaited Xavier chip.

The limitless applications of 3D data visualization will enable a more efficient approach to many of life's problems. Each day, developers exploring this technology are finding new ways to solve these problems in mixed reality; 3D modeling, easier house management, spinal surgery, and forest fire management are just a few recent examples of ways 3D data visualization can benefit us all.

If you're an Android user, Google probably has almost your entire digital life stored on its servers. Family pictures are backed up on Google Photos, your e-book library resides with Google Play Books, videos are on YouTube, chat logs in Gmail and Hangouts, starred places and location history in Google Maps, and so much more.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

You may have had to deal with this unfortunate scenario when you have a hankering for homemade ice cream: you find a great recipe, just the flavor you want to make, you start reading it... and you discover those ever-dreaded words "pour into your ice cream maker and process according to manufacturer directions." Oh no!

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

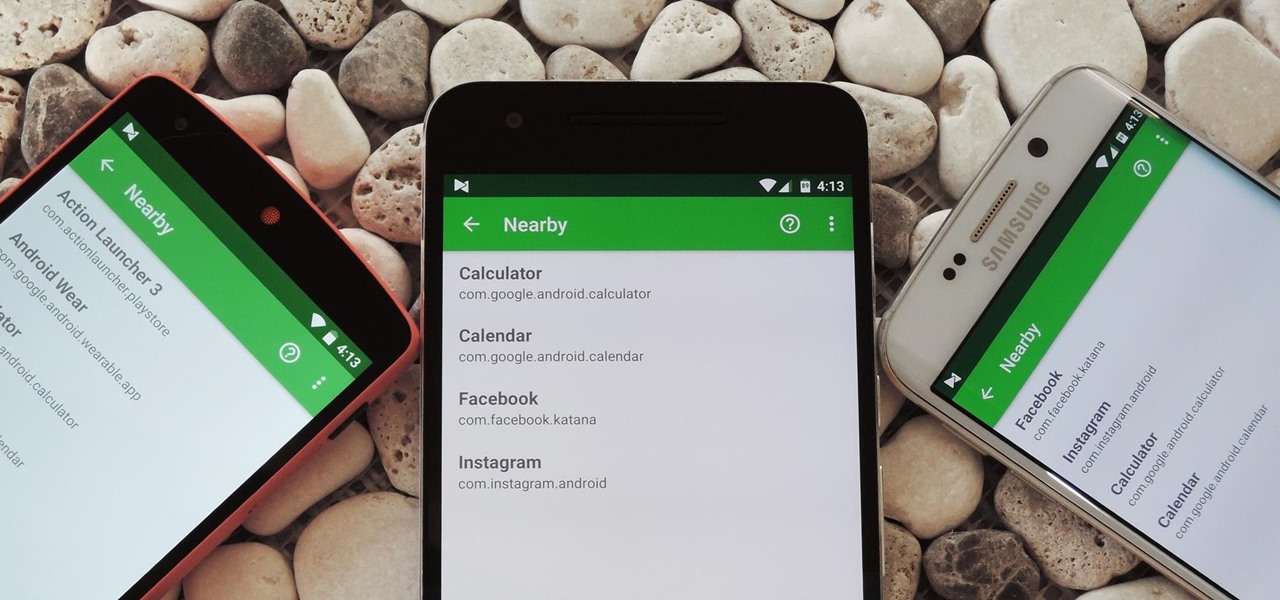
Google has an intriguing feature called Nearby that lets users share content without being on the same Wi-Fi network, or without even exchanging contact info first. Instead, the function uses an array of standard smartphone features, as well as subsonic sound, to identify other devices that are in the room, then makes a secure connection to transfer any data.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

Whether you're ready to admit it or not, we've all got our alter egos—especially when it comes to the internet. Perhaps you have one Facebook account that you use publicly, while maintaining a second account for more private interactions.

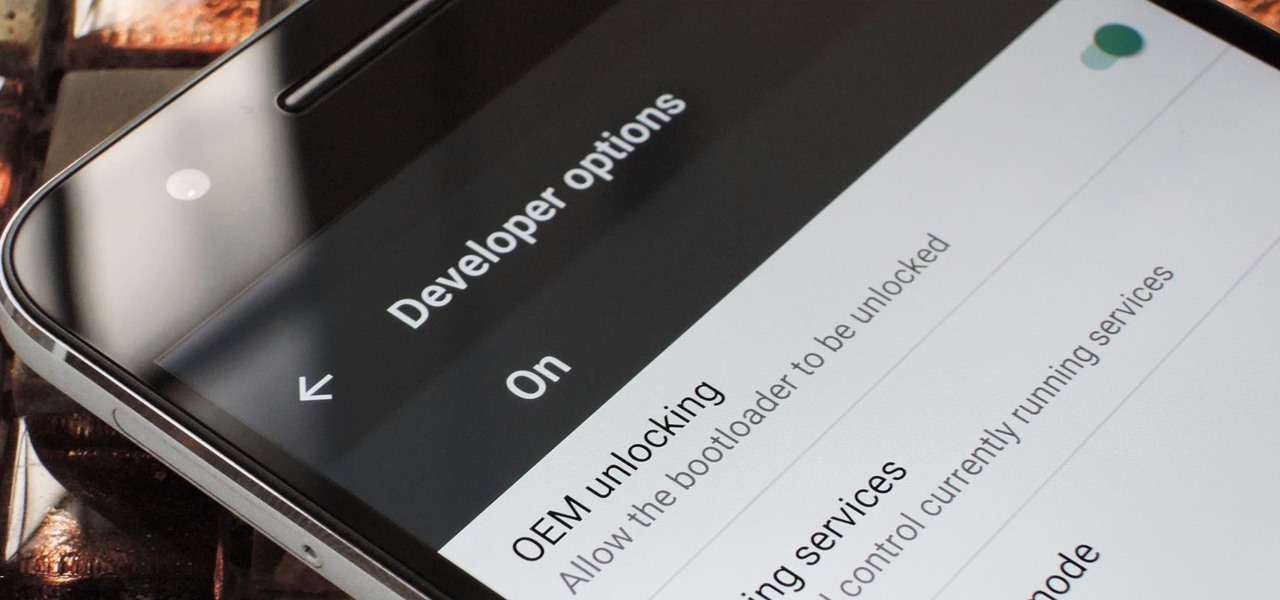
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

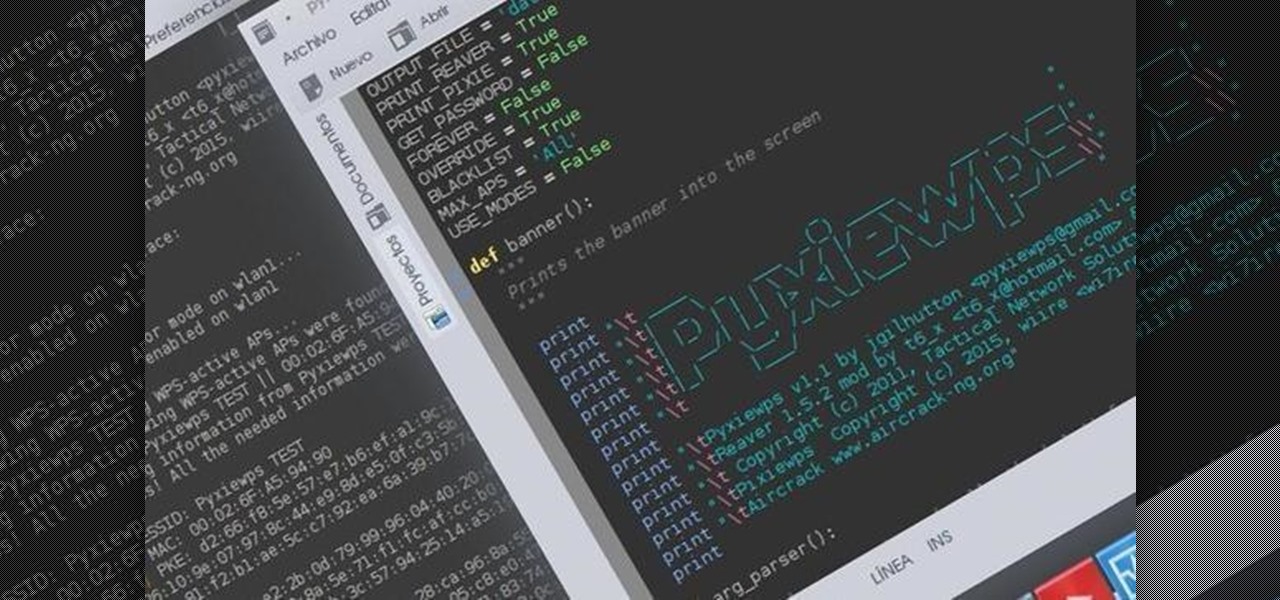
Hello dear friends! I'm jgilhutton and I want to show you guys a Python wrapper I made a few months ago.

I'll bet this scenario will sound familiar to you: you're in the middle of making a spectacular dessert that will knock the socks off of your guests, and you've almost finished gathering all of your ingredients to create your mise en place. The last ingredient listed is powdered sugar, and you reach for where it's stored, when—drat! You don't have enough for the recipe.

In this tutorial I am going to look at what services are running on our Metasploitable machine and setup firewalls. This is more basic scanning of our machine to get an idea of how to get in. Obviously in a real engagement you would want to do research on Google and whatnot to find out as much as you can about your target but this series isn't about all of that.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

Welcome back, my hacker novitiates!

If beauty is in the eye of the beholder, music lies in the ear. Even within a group of friends who share enough common interests to sit around and socialize over, music tastes can vary dramatically.
Welcome back for another How-To on the Xbox Community Ambassadors World! In this How-To, we are going to tell you how to help someone the right way so you can get a 9/9 rating when your finished assisting someone! Lets begin, shall we?

CyanogenMod has always been on the forefront of ROM customization, and its newest release, CyanogenMod 12, is no exception. In the newest nightlies, they have included an updated version of their Theme Engine, which allows you to effortlessly change the way your entire system looks.

First, I want to give credit to the author where I first found how to do this: Astr0baby's Blog. This article was dated, so I took the script on his page and reworked it to make it work today. (I also included the way to make it hide the cmd line popup.) Requirements

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

If you have a custom recovery installed on your Nexus 5, you're able to flash custom ROMs and lots of other cool Gadget Hacks. But when it comes time to receive and Over-the-Air (OTA) update directly from Google, having a custom recovery installed can be a fairly big hindrance—and for the upcoming Android L release, you're going to want to alleviate that.

You hand your iPhone to a friend to show them a picture. What happens? They swipe. Left, right, it doesn't matter. You don't remember what lies in either direction of the photo in question, and you don't want anything compromising exposed to the unassuming viewer. Luckily, Apple includes a safety net in iOS to prevent this scenario from ever happening, so long as you set it up ahead of time.

Welcome back, my newbie hackers! Hackers often are associated with clandestine and illegal activity, but that is not necessarily always the case. Hackers are increasingly being used and employed for law enforcement, national security, and other legitimate purposes. In this installment, we will look at how a single hacker could save the world from nuclear annihilation.