The iOS 17.2 update for iPhone is a big one. Aside from huge new features like the Journal app, Contact Key Verification for iMessage, and a revamped TV app, there are 50 new URL schemes you can use in your self-created shortcuts.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Watch this video from This Old House to learn how to choose exterior paint schemes. Steps:

Sure, you've probably seen a million YouTube videos that feature the impressive schemes of 2,000-sided modular origami balls that seem to defy gravity as well as patience. But sometimes the simplist origami craft is the most striking.

This video tutorial will show you how to apply four styles of lighting. This video teaches you how to apply four styles of lighting, namely Rembrandt, Beauty, Cameo and filling in from the Key Side. You will learn about high contrast lighting schemes, dealing with the amount of contrast used to highlight a person's face, as well as spotlight effects, and how these tend to draw the viewer into the scene. You will be shown how the Rembrandt Lighting setup contains three steps, namely taking a K...

Master of decorative schemes, god of modern motifs, Todd Oldham shows rocker Joan Jett how to make a round, rock and roll inspired ottoman. Nothing bizarre here!

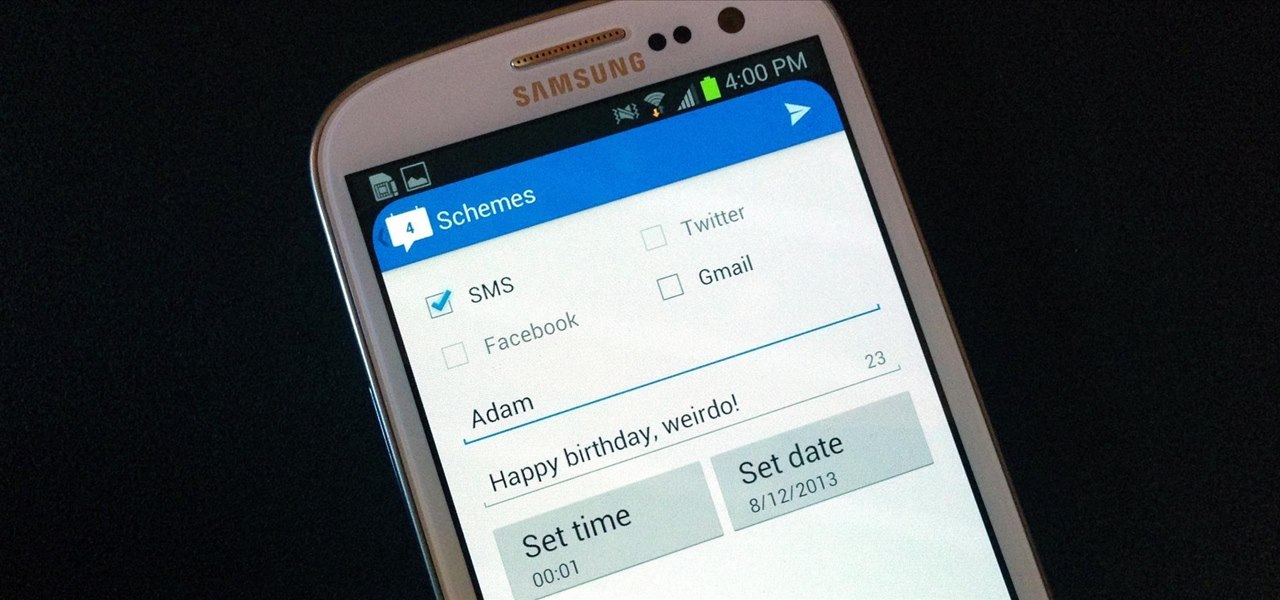
I'm sorry your mom hates you now, but it's pretty hard to forgive someone who forgets to say "Happy Mother's Day." Your poor ole ma could've spent anywhere from 10 to 20 hours popping you out, so the least you could do is set aside two minutes every year to say thanks. If you live to be 90 years old, that's only 3 hours over your entire lifetime!

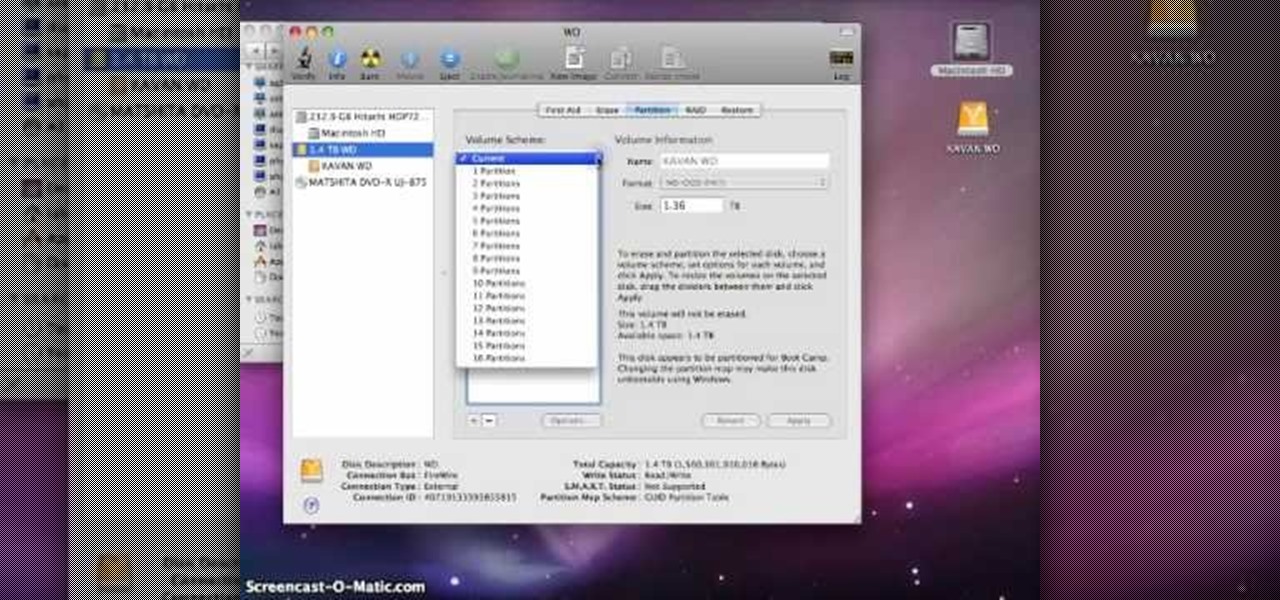
In this video tutorial, viewers learn how to partition an external hard drive on a Mac computer. Begin by open Macintosh HD. Scroll down the list on the left and click on Applications. Double-click on Utilities and select Disk Utility. Under Volume Schemes, select 2 Partitions. Select the name of the partition and choose the format that you want for the drive. Select the second partition and do the same. Now click on Apply and click on Partition. This video will benefit those viewers who use ...

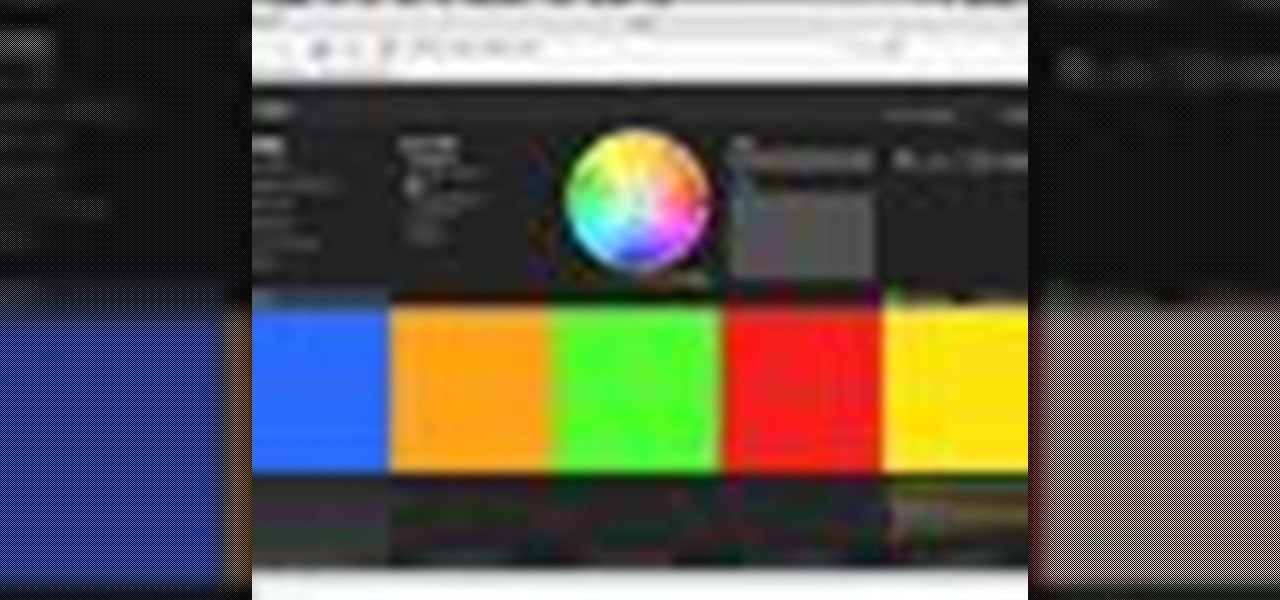
Check out this video from Sessions on using the color wheel. Better understand color relationships, color schemes and color theory. This is a great lesson for designers, artists, stylists and decorators. Create color harmony using the color wheel. Tutorial video from Sessions Online Schools of Art & Design's "Color Theory" course. Part of Sessions' Graphic, Web, Digital Arts, Marketing, and Multimedia Arts Design certificate programs.

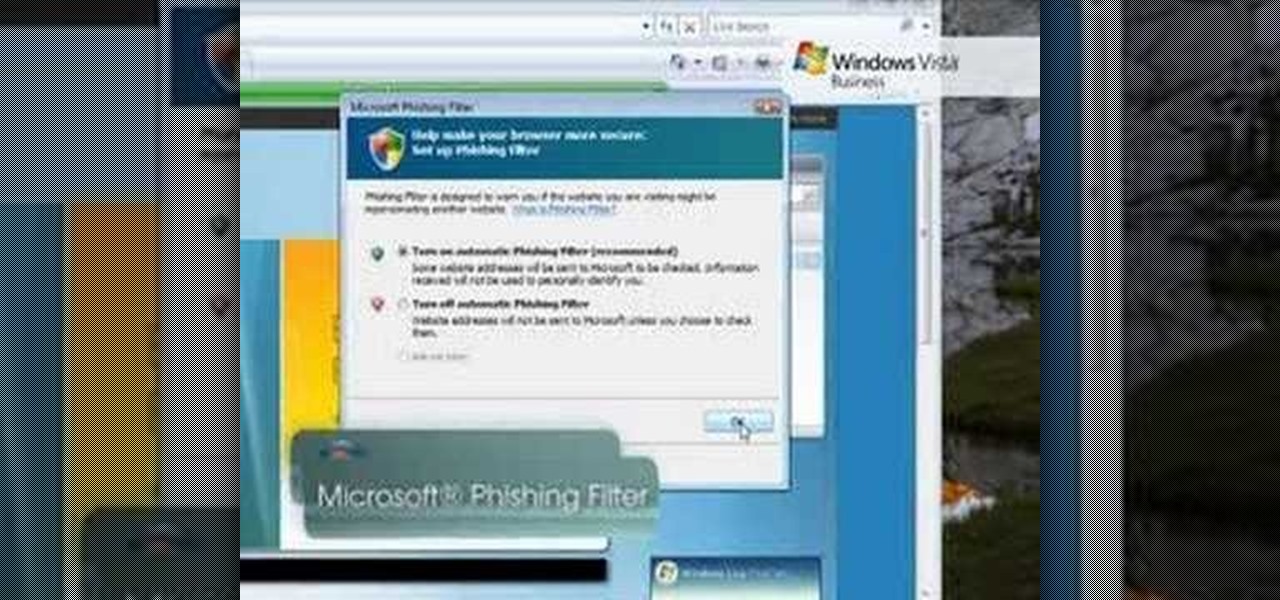
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

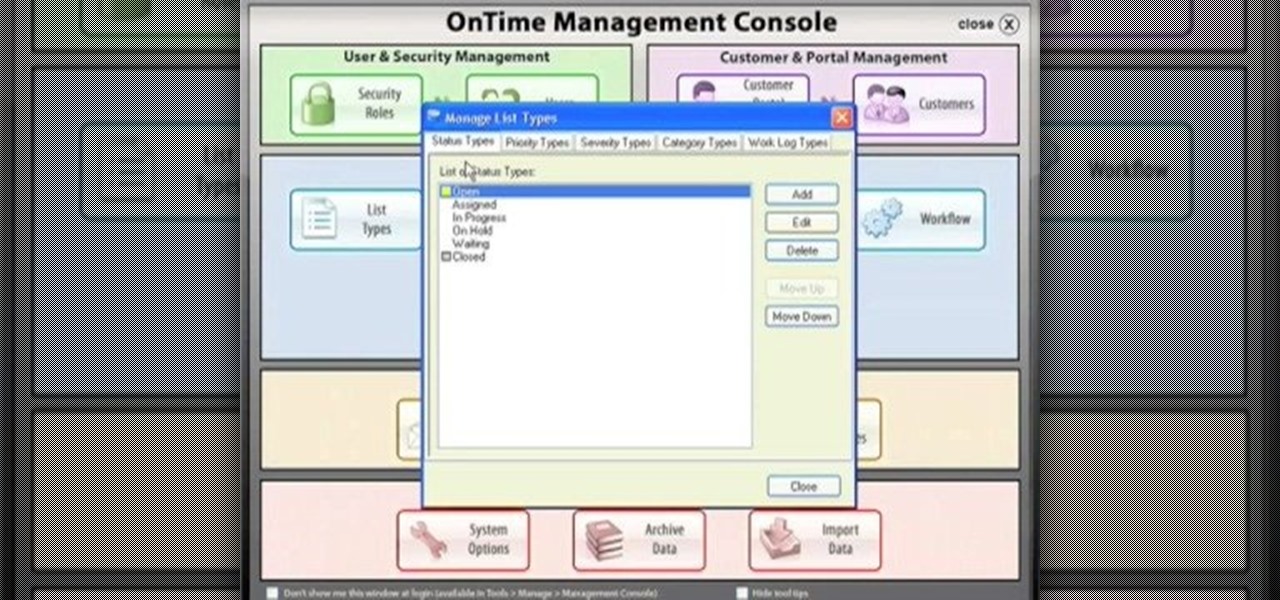
One great feature of OnTime 8.1 is the ability to add color schemes to the main grids of OnTime Windows and OnTime Web. This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers how to activate this functionality to allow color changes for items based on their Priority, Status, Severity, and Workflow.

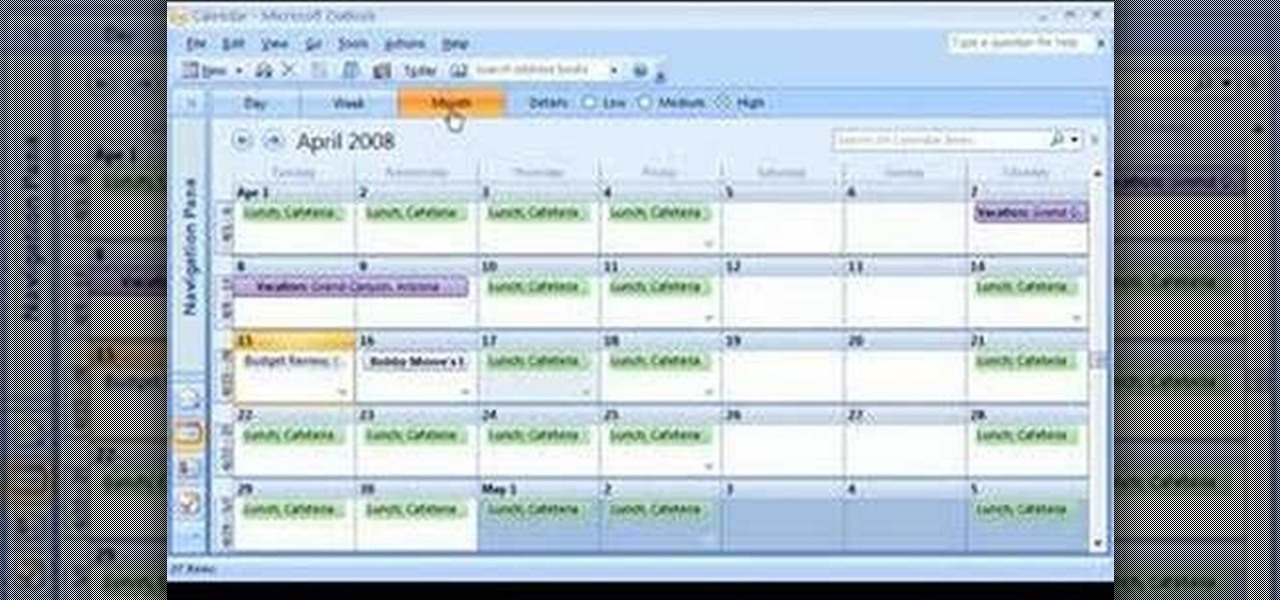
Did you know the views in your Microsoft Office Outlook calendar are fully customizable? View days and weeks in increments of 5 minutes, 60 minutes, or periods in between. Take a look into instructional video and learn how to adjust the view according to your work week and work day -- you can display Sunday-Thursday and show a normal day as 11 a.m.-7 p.m. Use different color schemes, and show more or less detail.

Kuler is a beta Adobe application at labs.adobe.com. It allows you to choose color schemes using rules or completely at random, then export the colors as an Adobe Swatch Exchange file for use in all of the Creative Suite applications. In this video tutorial you will learn how to create color schemes using Kuler.

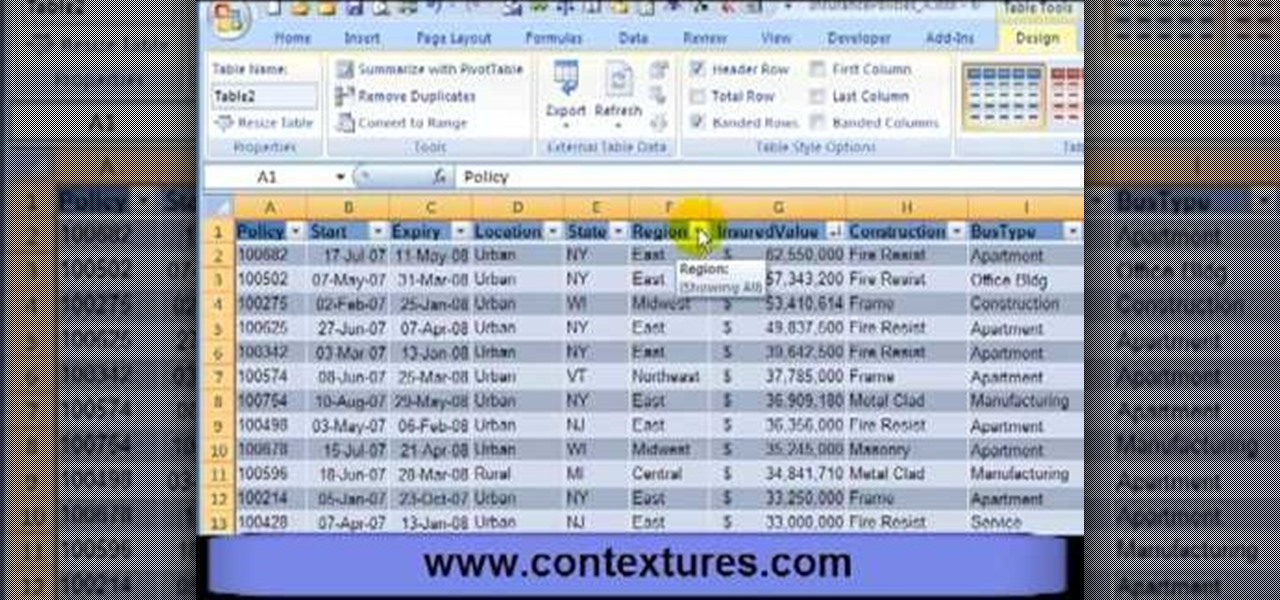
First, open the Excel worksheet you have previously created that you would like to create a table for. Click on any of the cell that contains data for your table. On the menu found on the upper portion of the application, go to the Insert Tab. Find and click Table. Your entire worksheet will now be selected. When a prompt window appears, click OK. Your table should now be created automatically.

This is another HelpVids video on technology. In this segment we will learn how to set appearances and themes in the Microsoft Windows XP operating system. The videos starts by right-clicking on a blank area of the desktop, then selecting ‘Properties’. The presenter then clicks on the ‘Appearance’ tab. Clicking on ‘Advance’ will open some very detailed options such as changing the font in a title bar window. You can also change the size of the fonts in this window. The options are truly endle...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

There are many things your iPhone or iPad can do, and Apple does an excellent job of documenting everything on its website. But there are some features that won't show up in any Apple manuals or help pages.

Our gardening expert will explain how to set up your perfect perennial plant business. Learn which plants go together, how to position the plants for just the right amount of sun, and how to determine if your adjustment has been successful. Are the flowers, shrubs and grasses happy after all of the work you have put in to meet their needs? Once you have mastered the basic care and maintenance of your garden, then you can concentrate on working toward exactly the look you want. Martha Cycz dis...

Like most new things, the Start Screen in Windows 8 has its adorers and detractors, but either way you slice it—it's here to stay. I'm still getting used to the Start Screen, so I'm not sure if it's a love or hate feeling yet, but I do know one thing—I want my own background!

Making use of Bar Chords in your guitar-playing can save you tons of effort and even allow you to achieve chords not possible using basic fingering schemes. Bar Chords can speed up your playing-time greatly; Peter Vogl provides excellent instruction in this video.

Widgets can display essential information from an app right on your iPhone's Lock Screen, but there's an even bigger reason you should be using them: fast access to your most-used apps.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

There are many things Apple doesn't tell you about its products, and that's definitely the case when it comes to its Messages app. Hidden features lurk in your SMS and iMessage conversations just waiting to be found, and we've unearthed some of the most secret ones.

Whether you're wielding an iPhone, iPad, Mac, Android phone or tablet, or even a Windows PC, this little-known secret holds the key to effortless assistance and unwavering obedience. Intrigued? I thought so.

Apple just released its biggest update to iOS 17 yet, and there are 60 exciting new changes for your iPhone. With iOS 17.2, you get a brand new app, more Apple Music enhancements, upgrades in Messages, and a new security feature that was announced last year, as well as changes for Weather, notifications, Apple TV, Books, and more.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

If you're looking for a new Reddit client on your iPhone, look no further than Apollo. Launched with iOS in mind, Apollo is a free app that offers an exceptional Reddit experience, but some of its excellent features — as well as some necessary ones — are hidden behind its "Pro" paywall. Are these extras worth your money?

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

Steganography is the art of hiding information in plain sight, and in this tutorial, I'll show you how to use Steghide — a very simple command line tool to do just that. In addition, I'll go over a bit of conceptual background to help you understand what's going on behind the scenes. This is a tool that's simple, configurable, and only takes a few seconds to hide information in many file types.

The story of the Essential Phone isn't one for the faint of heart. The company was founded by Andy Rubin, and their first phone was supposed to have only the "essential" qualities. Unfortunately, it lacked a decent camera, and still cost as much as most flagships. Since that rough start, however, things have taken a turn for the better. Now, Eseential's doubling down with a new set of colorways for the PH-1.

Believe it or not, there are legitimate iOS apps beyond the App Store that you can install on your iPhone. Some of them even work for iPad, Apple TV, and Mac, and there are also benefits to using them over apps found in the App Store.

It's a strange time for us iOS beta testers. While Apple prepares for the general release of iOS 13 on Thursday, it's also beta testing that software's successor, iOS 13.1. An iPhone updated to iOS 13 on Sept. 19 will only have 11 days before seeing 13.1 in its Software Update page on Sept. 30. To prepare for this release, Apple released the fourth iOS 13.1 public beta, just about the same time as its developer counterpart.

Apple's iOS 13 is nearly here. After four months of beta testing, the latest iPhone software update promises over 200 brand new features, like system-wide dark mode and an overhauled Reminders app. That said, it'll be shortlived, as Apple plans to release iOS 13.1 as a supplemental update just 11 days later. In fact, the company just seeded developers the fourth beta for iOS 13.1 today, Sept. 18.

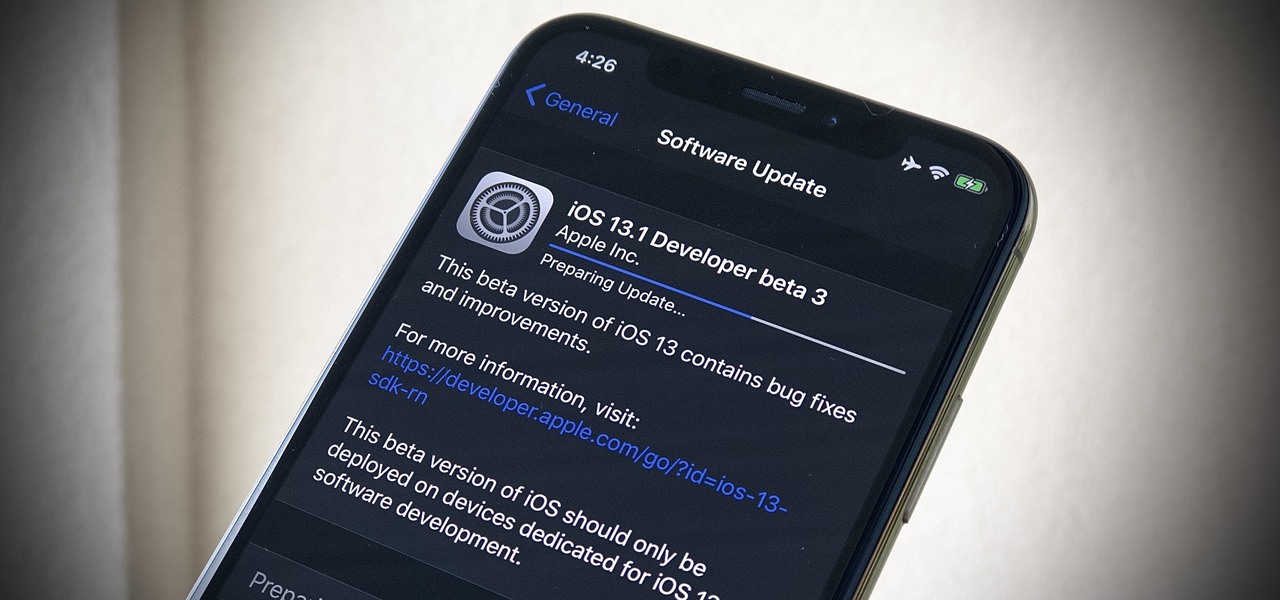
Yesterday showed us our first look at the iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. But it wasn't all about hardware. Apple also released the iOS 13 Golden Master, making iOS 13.1 the main focus for us beta testers. Now, Apple just seeded the third public beta, following yesterday's release of 13.1 dev beta 3.

It's a big day for Apple. First, the company announced its new suite of phones: iPhone 11, iPhone 11 Pro, and iPhone 11 Pro Max. Then, we get the iOS 13 Golden Master, the beta version of iOS 13 that will eventually release to the general public on Sept. 19. Now, it seems the company has dropped the third developer beta for iOS 13.1, set to release to all compatible iPhones on Sept. 30.

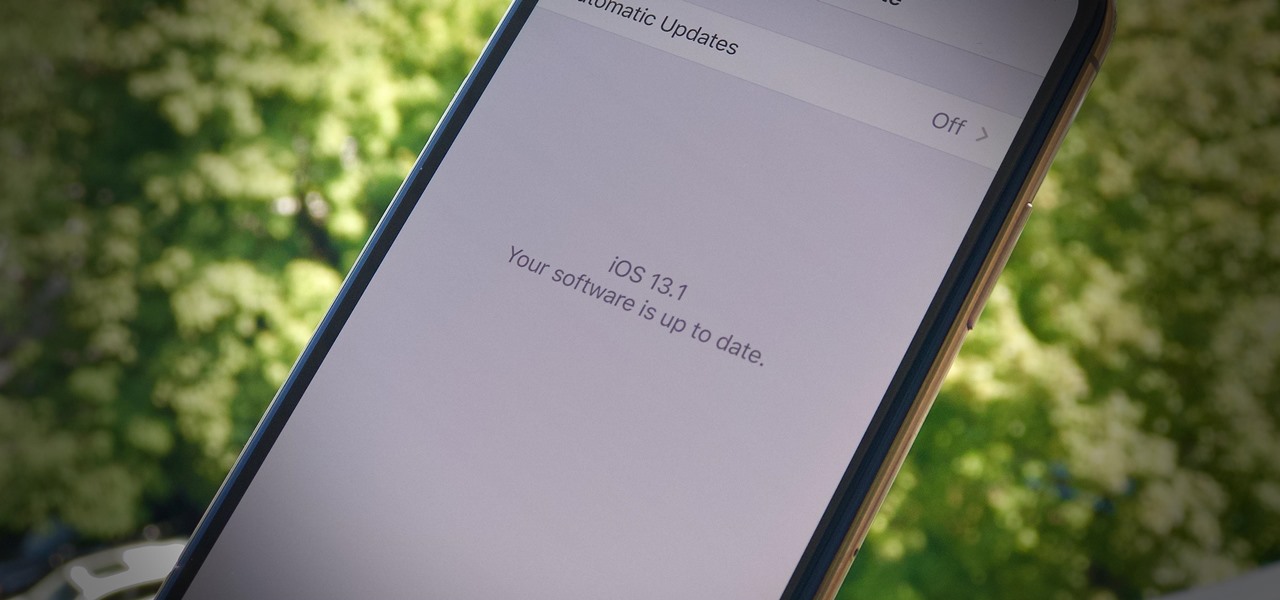
Apple has pulled quite the headscratcher in anticipation of its big iPhone unveiling next week. Its latest iPhone update, iOS 13.0, is just on the horizon, going through eight beta versions so far. And yet, before that software's official release, the company has started beta testing iOS 13.1, with no explanation why. And the second public beta for iOS 13.1 is now out, so let's see what's new.

When Apple takes the stage next week, we have no idea what version of iOS it will release. For months it seemed like a given that we would, of course, see iOS 13 seeded to our iPhones. Now, we aren't sure if Apple will tout iOS 13 or iOS 13.1, since the latter is now the focus of its beta testing. In fact, 13.1's second developer beta is now available to download and install.