In this video series, expert Karen Weissman will show you how to make your own stuffed animal, a reversible Teddy bear. This little toy has a long history in American homes, switching from a little bear in a dress to a sleeping bear under a blanket.

In this video series, watch as professional dart player Richard Buccola teaches how to play darts. Learn the history of darts, the different parts of the dart, how to throw darts, how to play the games cricket, 301.501, baseball, dead presidents, killer, and secret killer, and how to maintain darts.

In this series of expert videos, you will learn more about the history and function of the hammered dulcimer. Watch as our expert plays this beautiful instrument and demonstrates the function of the damper pedal. Get tips on playing the hammered dulcimer including tips on accompanying lead instruments or voice with the hammered dulcimer. Learn how to play different tunes, songs, and jigs on this instrument. Watch these videos and learn how to tune the hammered dulcimer and play muted notes. T...

Learn about the history and the benefits of Indian club training in this series of expert videos. Get tips on proper training techniques that will maximize your fitness with the use of Indian clubs. Watch as our expert demonstrates the basic moves, snatch, and squatted snatch of this technique. See different and more complicated maneuvers such as the full pendulum, forearm swing circles, stirring and the clean and press. Challenge yourself with these moves and other moves including forearm sw...

First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

Election Day is today, and Apple News is making it easy for you to stay informed with real-time results for the 2024 presidential election through a new Live Activity feature on your iPhone, iPad, or Apple Watch.

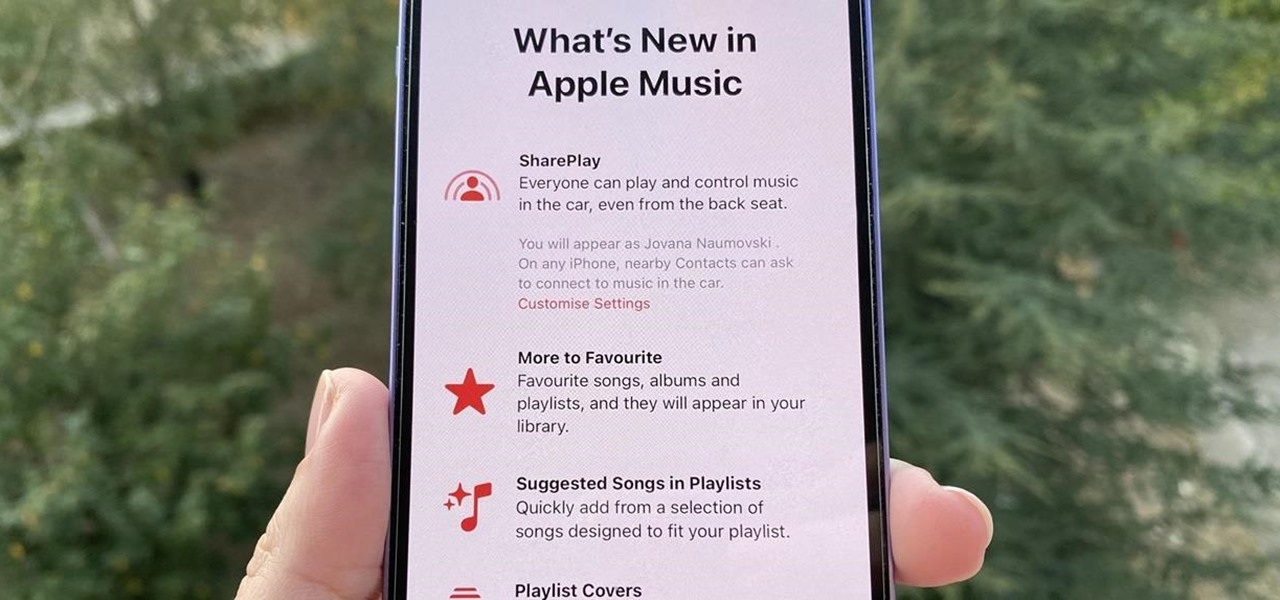
In case you missed it, Apple has added a lot of new features and enhancements to the Music app on your iPhone, changes that benefit both Apple Music subscribers and non-subscribers. Chances are, you haven't seen all the changes yet, especially since many of them weren't released when iOS 17 first came out, but we'll go over them all with you.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

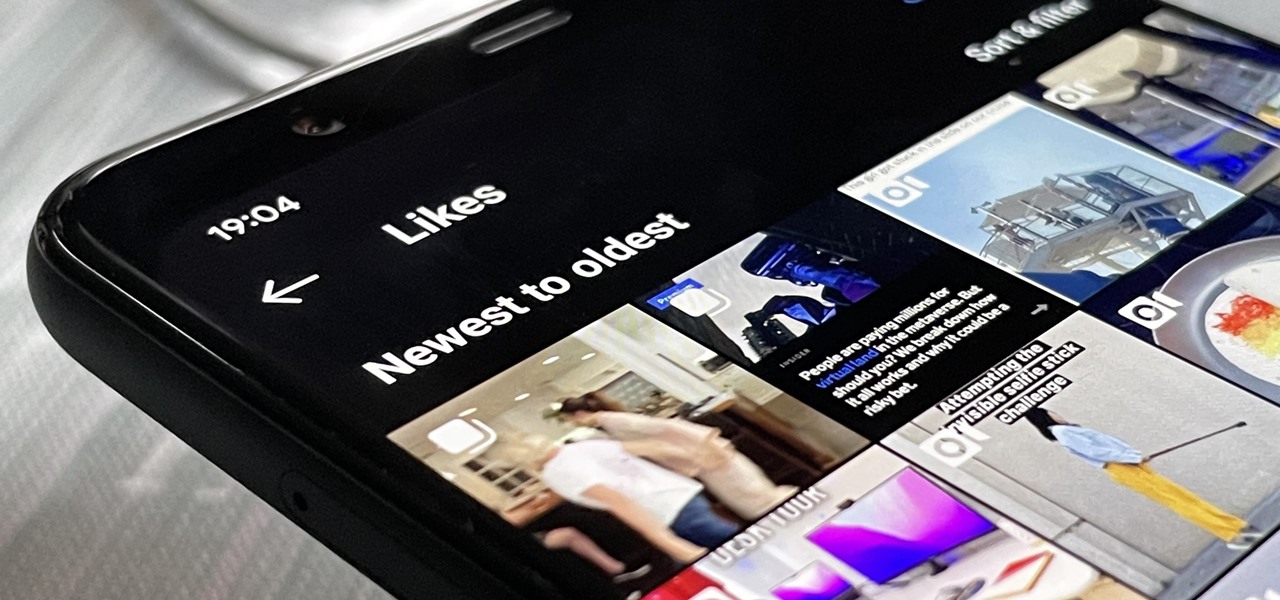
Unlike TikTok, there isn't a convenient "Likes" tab directly on your Instagram profile page to see all the posts you've ever loved. That's too easy. Instead, you have to dig a bit deeper if you want to take a trip down IG memory lane.

The beginning of autumn has delivered a number of new augmented reality developments, and we're on top of it.

Although the enterprise use cases for the Microsoft HoloLens 2 continue to impress, the arts community just can't stay away from the best augmented reality headset on the market.

Like its predecessors WandaVision and Falcon and the Winter Soldier, Marvel's latest series for Disney Plus, Loki, has its own augmented reality experience.

If you've ever wanted to start learning to code but haven't known where to start, then one of the best places is with Python. It's great for introductory programmers, and it's also a must-have addition to the repertoire of anyone experienced in the industry. As of 2019, over eight million programmers have used Python, and the industry has only grown since then, so the best time to start practicing is today!

The NFT space is moving so fast that if you're not already engaged, you've probably already missed several history-making events.

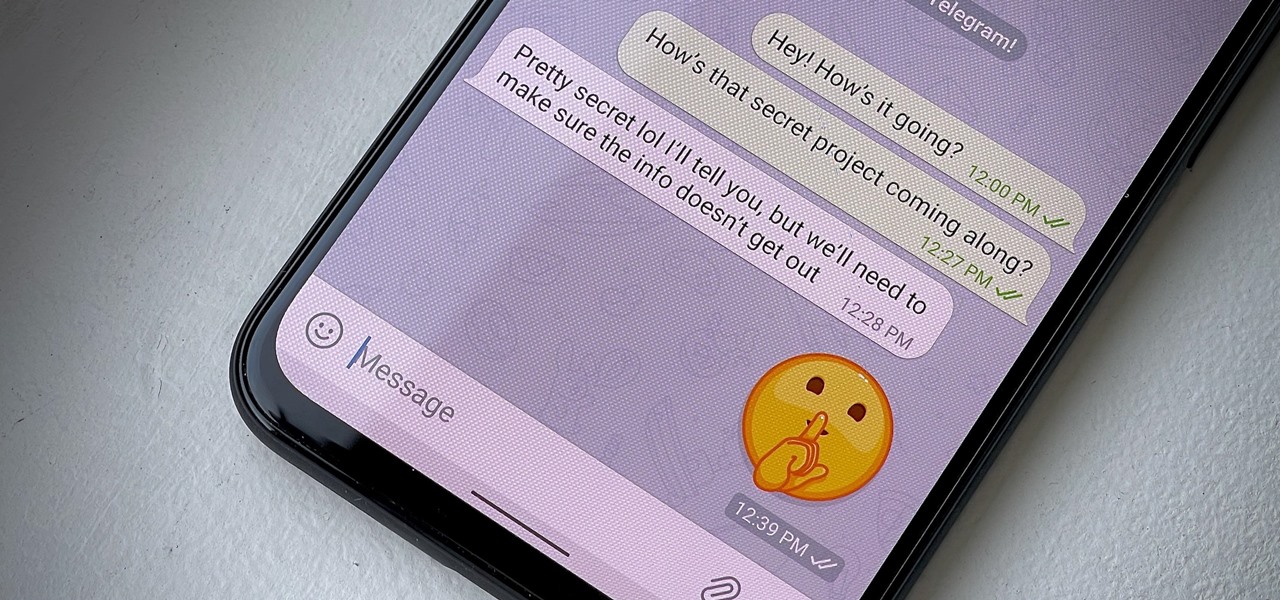
Have some sensitive information you need to share with somebody on Telegram but are worried it might fall into the wrong hands? You don't have to worry anymore because Telegram now sports a way to automatically delete all new messages in any chat of your choosing, not just end-to-end encrypted ones.

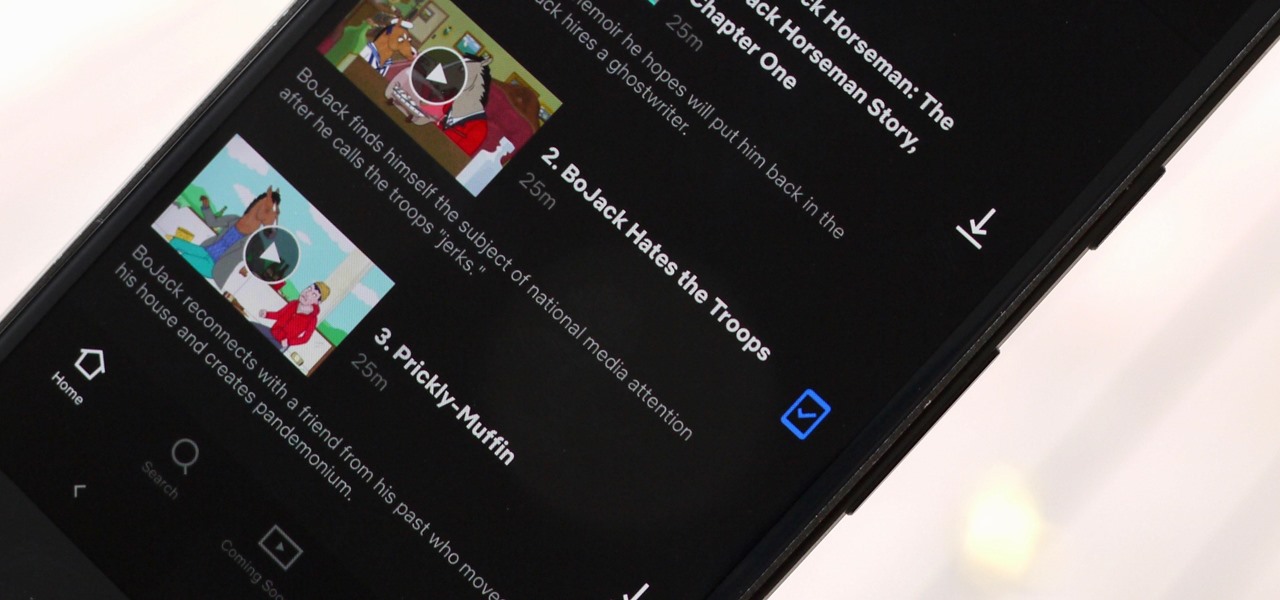
One of the most convenient features in the Netflix app is the ability to download movies and TV shows to your device, which lets you avoid potential streaming issues and watch content offline whenever you want. To make downloading even more convenient, you can automatically download new episodes of your favorite TV shows once you've finished the ones already stored on your phone.

The realm of science fiction isn't all lasers and cute green toddlers, sometimes alternate science history is sci-fi, too, as exampled by the Apple TV Plus series For All Mankind.

You only 'thought' the HoloLens 2 was the most expensive augmented reality device on the market. As with many things tech, Japan is here to up the ante with what may indeed be the most expensive AR-dedicated wearable we've seen—the Canon MREAL S1.

Most iPhones are more than capable of shooting crispy, high-quality video, perfect for any TikTok account to use. But if you're serious about the platform, especially in the long-run, you don't want just any iPhone. Instead, you'll want to pick up an iPhone 12 Pro or 12 Pro Max.

To kick off 2021, the Apple rumor mill is spinning yet again. This time a familiar item is on the menu: an augmented reality device.

With the new season of The Mandalorian underway, Google has launched a new AR app that enables some Star Wars fans to connect with virtual characters in between new episodes.

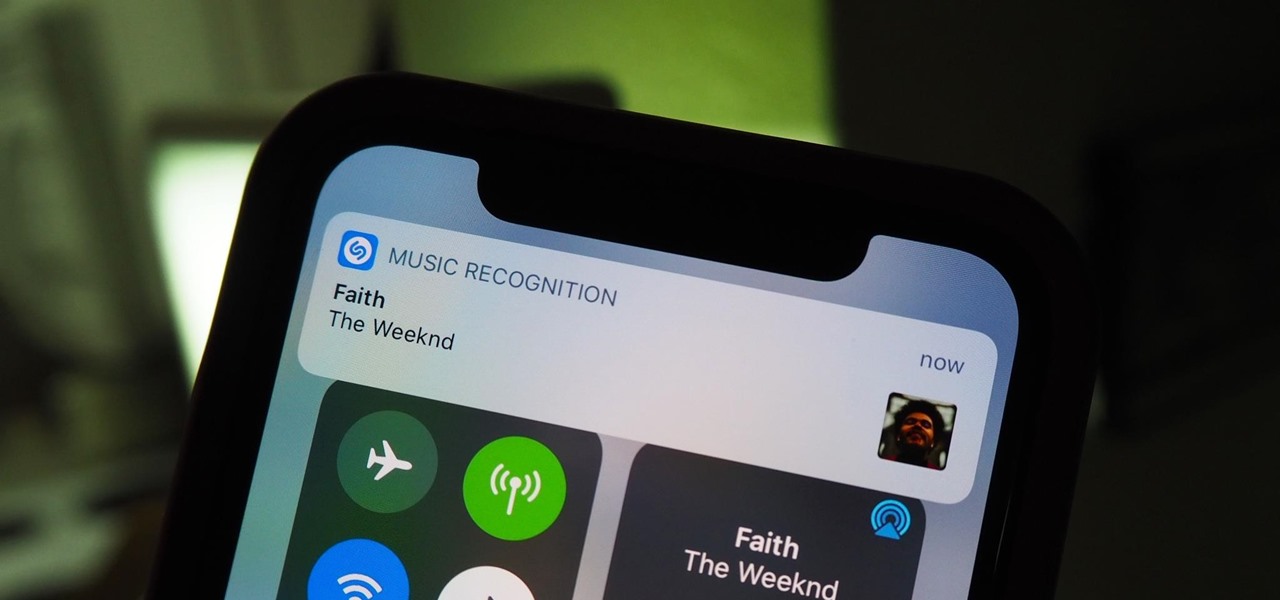
With or without the Shazam app, which Apple acquired in 2017, you can use Siri on your iPhone to identify music playing around you that you want to know more about. In the iOS 14.2 update, there's another way to name songs on your iPhone.

The iPhone 12 Pro and 12 Pro Max have one huge thing that sets them apart from their iPhone 12 and 12 mini siblings: a lidar scanner. Thanks to this new technology, Measure, an Apple app that's just over two years old, has gotten even better.

After a few months and a couple of beta versions, Android 11 is now ready not only for Pixel devices, but also handsets from OnePlus, Xiaomi, Oppo, and Realme.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

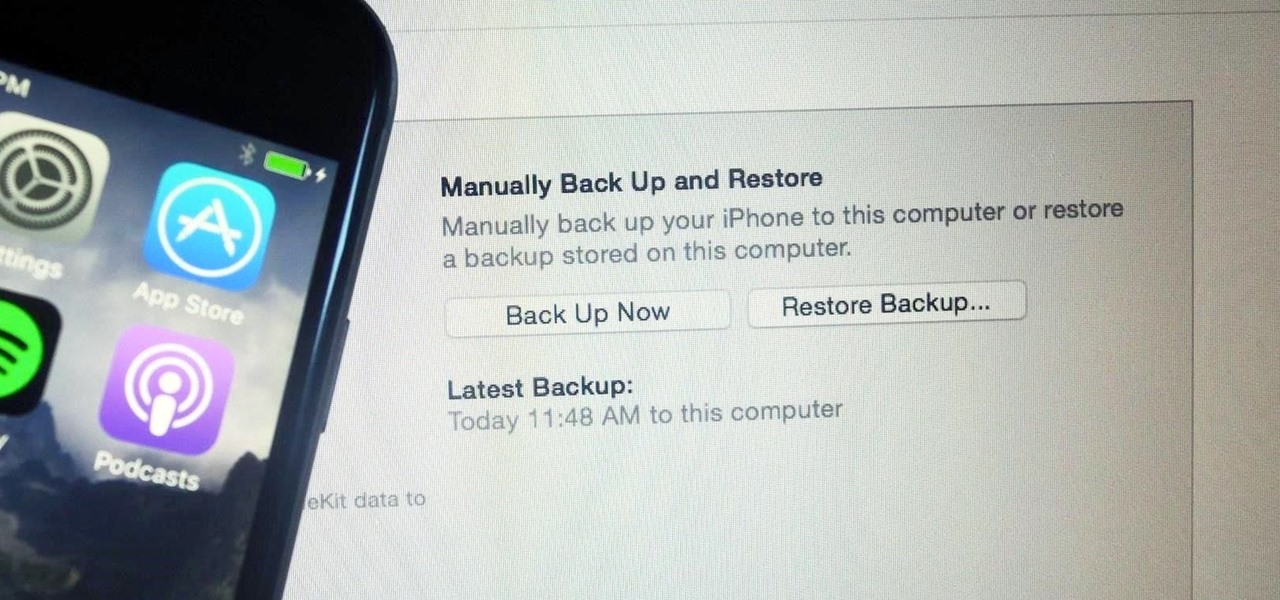
It's easy to back up and restore your iOS devices using iCloud, but there are a few downsides to encrypted iCloud backups. For one, Apple holds the key to decrypt all the data. Plus, you're limited to only 5 GB of data for free before you have to upgrade your storage to 50 GB, 200 GB, or 2 TB.

It's a myth that regular users only need the protection of a virtual private network when on a public Wi-Fi connection. First, almost all network connections can be accessed without the proper permissions. Second, ethical hackers also need to think about using a VPN as one step to encrypting and protecting their activity and identity during pentests, phishing, and other actions.

Google Photos is one of the most useful apps for storing, sorting, searching, and sharing all of the photos and videos you capture on your smartphone — but if you travel, it just got a lot more useful.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.