Just because you are using Linux, doesn't mean you have to be cut off from file sharing with those using a regular Windows PC. In this tutorial, learn how to share files between Ubuntu and Windows using a Samba local network. Samba is simple to use and can be obtained through your Synaptic package manager.
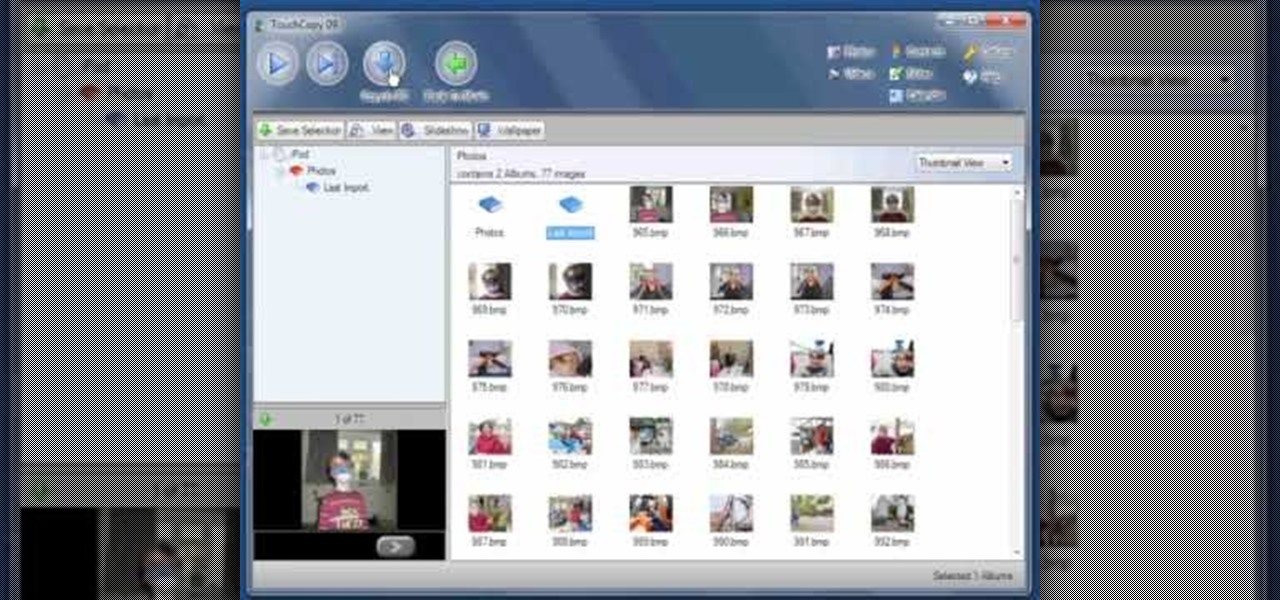
What if your computer just crashed and you've suddenly lost of your personal photos? Those are memories you can never get back in the digital world, unless...

This video is some real basic stuff about boat tying and anchoring. Watch to see the right way to tie and anchor your boat.

The Double Bowline has the same strength as a figure eight knot but is simpler to tie. As the rope wraps around twice, the double bowline knot is more secure than a regular bowline knot. Watch this video knot-tying tutorial and learn how to tie a double bowline knot.

As the clove hitch knot is adjustable and slipper, it can be useful attached to a carabiner, allowing the load to move fluidly up and down the rope. However, the clove hitch is not particularly useful or advisable as a securing knot. Watch this video survival training tutorial and learn how to tie a clove hitch knot on a carabiner.

With this how-to, you'll learn how to mount an SSH server on your Mac as part of the file system. The key is a third-party program called MacFuse, which is available, free of charge, through Google Code. To get started running SSHFS, or the secure shell filesystem, on your own Mac, take a look!

While the clove hitch is not a particularly secure knot, it's useful in situations when the knot requires a little bit of give. The steps to tying this knot are demonstrated in this how-to video, and are shown at a fast pace so you can see how quick and easy it is to do. Watch this video knot-tying tutorial and learn how to tie a clove hitch knot quickly.

The Improved Half Blood Knot is basically a half blood knot with a little improvement. To make the knot more secure the end tag is locked in the final step when tying the knot. The Improved Half Blood Knot is a popular knot for attaching hooks, swivels and lures to the the fishing line. Watch this video fishing tutorial and learn how to tie and improved half blood knot on a fishing line.

RC Car Action Magazine Editor Matt Higgins explains how to modify your antenna cap for better wire protection. Make sure that antenna cap doesn't go flying off. Watch this video tutorial and learn how to secure the antenna cap on an RC vehicle.

In this roofing video Bob Schmidt shows you how to use the foam padding from a sofa cushion to say secure and not fall while doing roof repairs.

This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

Check out this video to learn what kinds of tools to use to secure your furniture during an earthquake. You may want to use straps and stud finders.

Ori Livney shows you how to secure your newly inflated balloon with a simple knot at the tip.

Are you a Gmail user? Listen up, cause here's a snazzy tip from Tekzilla to help protect your emails.

Install acoustical wall panels using adhesive to secure the panel to the wall.

Check out this video to learn how to install acoustical wall panels using pins to secure the panel to the wall.

Check out this video to learn how to install acoustical wall panels using impale clips to secure the panels to the wall.

Motorcycle expert Chris Kelly is here to show you how to transport a motorcycle. As long as your bike fits, the vehicle won't matter but pay attention to how to tie down and secure the bike.

In order to set up a secure wireless router, you will need to use the security that is available with your wireless routing. You will need to change the default ID names and password on your computer. Try to make sure that your passwords are difficult. Also, turn on the encryption: e.g. WEP.

For this hijab style, start with hair completely covered and a large rectangular pashmina scarf. Pull the scarf over the head with one side hanging longer than the other. Pull the scarf tightly over the forehead to the nape of the neck and pin it together at the nape. Take the shorter end of the scarf and tuck it back toward the nape of the neck. Then pull the long end under the chin and up around the head until it is tight. Secure the end with a pin. Earrings can be worn through the scarf as...

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

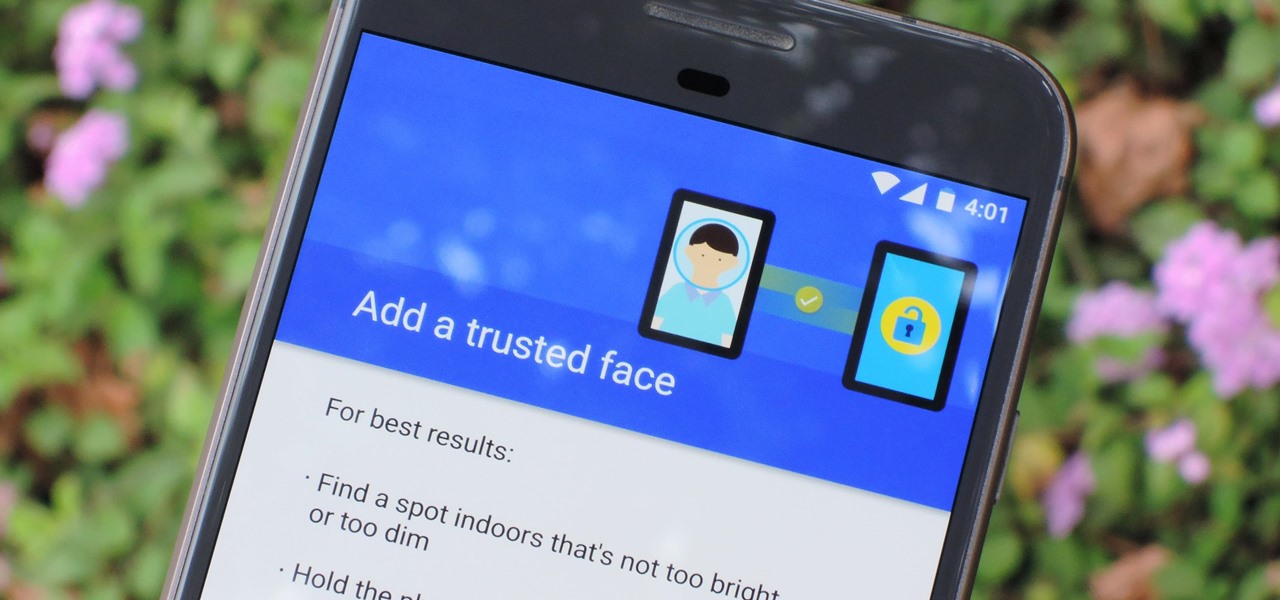
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

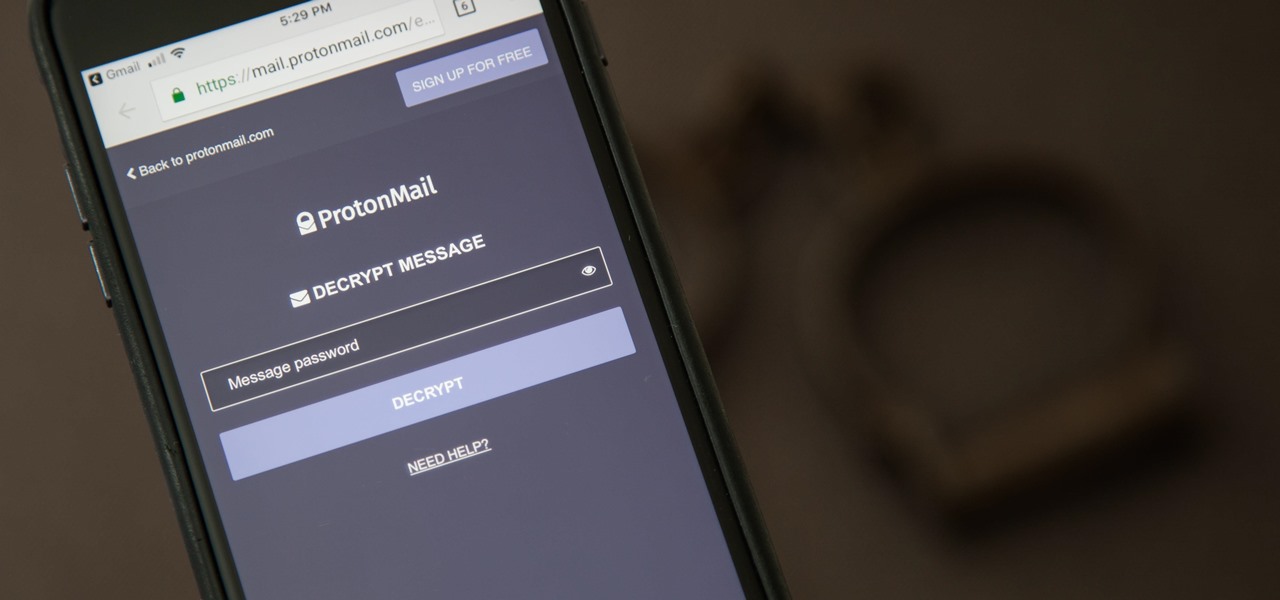
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

This video will guide you how to make digital signature in MS Word. The digital signature will allow to secure your document from tampering. When you set digital signature in your word text then you can't insert anything in the document anymore. You could add your image of signature with text.

If you want to protect your word doc from other, you can give it a password. When anybody wants to open, it will ask a password. This way your valuable document will be secured from unauthorized access.

I was kinda disappointed with last year's James Bond movie, Skyfall. Don't get me wrong, it was a solid flick, but only made me jealous with all its super spy hacker stuff.

Make sure your private documents are completely secure. This episode by Tinkernut deals with not only encrypting your files, but also hiding them in a hidden volume.

I know, "Steamdown" conjures images of a hoedown, but "Steampunk prop breakdown" is a bit of a mouthful, I thought.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

Have you ever screwed up a painting before? Beyond repair? Well, it might be able to be saved after all, at least, thanks to these tips from Merrill Kazanjian.

The narrator starts by explaining what a squash book is. A squash is designed to keep photos, journalling or what ever you like. To start we require a 4x4 pattern paper and 3x3 chipboard. We then glue the chipboard onto the pattern paper. We then cut the corners of the pattern paper. We then fold the flap in and glue down. We repeat this to form another cover. Next we grab a 6x6 pattern paper, we then complete a series of folds. One diagonal, half horizontal and half vertical folds. We repeat...

To create almost any headband look, start by using a real human hair headband with extensions. Mostly, the extensions will come with an interchangeable headband for different colors. Now, start by pinning back the front crown area of your hair, if you have bangs you can leave them out of the hair that you are pinning back. Secure the crown of your hair with bobby pins. The headband with extensions should have three little combs. These will help secure the extension and the headband onto your ...

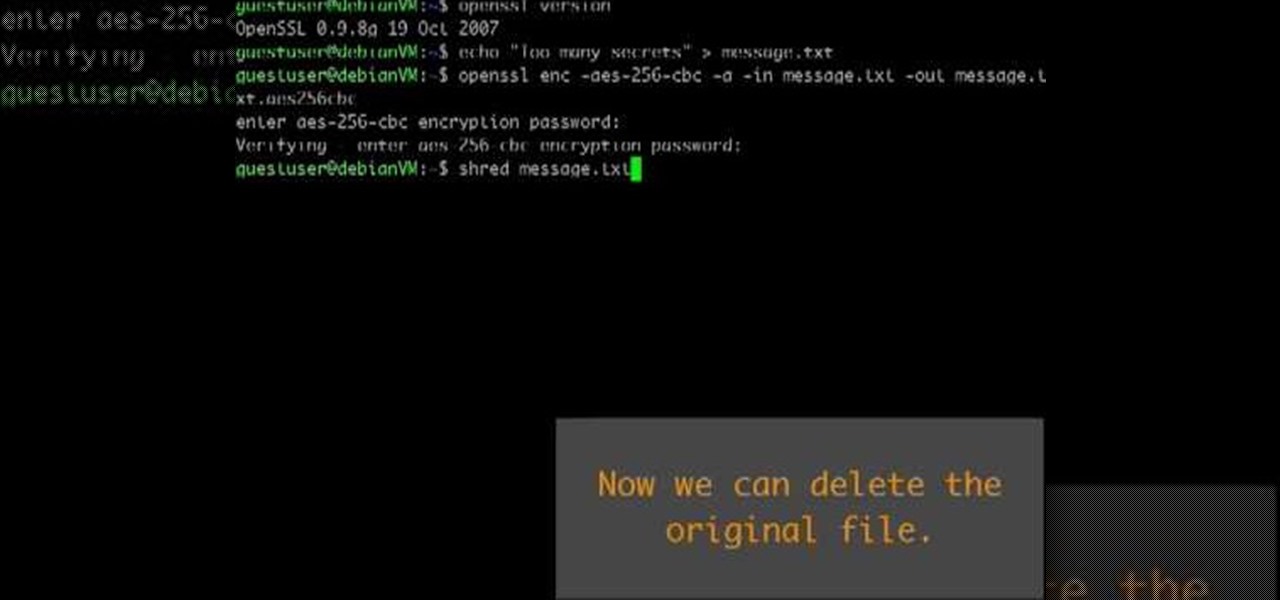
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...

Debra Hardy provides detailed instructions on how to make darling decorative Santa soy votive candles in this video. She first cuts the red felt into 6 3/4 inch by 2 inch strips for the Santa suit, wraps it around and adheres it to the bottom of the glass votive. Next, she secures a smaller strip of the white faux fur on top of the red felt also towards the bottom of the candle to create the bottom of Santa's jacket. Debra then instructs the viewer to cut a 6 3/4 inch by 1/4 inch black felt s...

Cocorais shows you how to style your hair into a Selena Gomez style up-do with short hair. Start by curling your hair, which is optional but it gives the hair shape and volume. Take your curled hair and sweep it to one side (opposite side of side-part if you have one), leaving a little hair on the other side to frame your face. Ignore any hanging hairs. Comb your hair into a ponytail, and tie it to one side. Gather your hair and tie it into a bun, using bobby-pins to secure it. For the rest o...

Crimp can be made easily and covered to the jewelry by using the following instructions. First purchase the proper supplies of crimping tool. This tool acts like pliers and is used by placing the bead in the appropriate slot at the tip and then squeeze the handle together. The multiple slotted tips are the key to the tool, and are needed to create a proper crimp. Then, select the proper crimp bead. The thin metal crimp beads come in a variety of materials and sizes. This will be used to secur...

Learn how to tie a perfect bow. To do a basic pony bow, place the gathered hair in the center of the ribbon and tie a single knot to secure it. Making two loops, cross one loop over the other and pull the loop on top through the hole you've created. Straighten out the ends and tighten so the two loops are on top and the two tails on bottom. Make a headband bow. Run the ribbon along the hairline, drawing the ends up on top of your head. Secure a knot and tie a bow. By tweaking the loops out a ...

This video teaches the viewer how to make a memo book with a paper bag. For this craft you will need two paper bags, memo paper, adhesive, ribbon, and scissors. To begin, you'll need to cut off the bottom of the bag and discard it. She explains where to make decorative edges on the bags before sewing them together or using hot glue. Fold and crease the open end down about one third of the way. Open and then fold a little farther down to allow room for the spine of your memo book. Repeat this ...