In this video, we learn how to delete hidden driver viruses. First, scan your computer with anti-virus and try to delete the virus that is harming your computer. If you have done this and your anti-virus can't delete it, download HijackThis from Trend Secure. Go through the download stages and install the new software. Now, open up HijackThis on your desktop. Once it's opened, open up the "misc tools" section. After this, click on "delete a file on reboot". Now, write the virus location name ...

This is a sped-up video of the FlowerGod showing how to make a beautiful feather anklet. The video is sped up to four times its normal speed. He begins by putting a basic feather anklet around a girl's ankle. Then he gets a piece of paper, to have a safe place to use some glue. He deposits a small amount of glue from a bottle of glue, and then uses this glue to secure several more decorations onto the anklet. These include some pink and white flowers, as well as a green feather. In the end, t...

Follow this video to view suggestions on how you can decorate a Christmas tree. It is best to start placing the lights first. Try to space them evenly and you can secure them in place by means of crafting wire. When you finish with the lights start decorating the Christmas tree with garlands and tinsel. Apart from giving a nice effect they will also serve to hide the wires of the lights. The next step is to start hanging the baubles and trinkets. Instead of including several colors try decora...

Learn to steal Kim Kardashian's pin curls and bangs with this video tutorial! Items needed: curling iron, straightener, blow dryer, hair spray, mousse, dual prong clips or bobby pins, comb and medium length bangs.

Learn how to wrap a short electrical cord. Treat your power cords right, and make them last longer, by learning how to store them correctly.

This is just a short climbing tutorial that demos what happens just after you go into the crevasse. Ditching the pack is easy if you have pre-hooked the pack to harness. The nest step is securing yourself with a prussik and getting it ready to use as a stirrup. But as we see, practice practice practice. Check out this instructional climbing video that offers some self rescue tips from a crevasse while climbing. These are good safety tips and procedures to learn.

Air horns are extremely loud. That's why they're used by truck drivers, fire trucks and ambulances to clear the way in a hurry. This video will show you how to make your own air horn, using stuff you've probably already got in a junk drawer.

F for FAKE. This video has been labeled a "Faux-To". Commonly contested as bogus science, we believe this video to be a hoax. What's your opinion? Comment below.

While sheltering at home orders are lifting, companies are still conducting most business online. Case in point, hackers have been having a field day over the last few months. Securing your identity has always been important, but never as much as it is at this moment.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

If you have friends who aren't privacy-conscious, you've surely heard the old "What do I have to hide?" excuse. Despite the fact that billions of people are using the internet each day, many of them don't know the dangers that can find them. And many don't know the tools to combat them.

The iPhone X introduced the world to Face ID in 2017, and now, every new iPhone uses Apple's biometric security system instead of the old Touch ID. It's more secure than fingerprint scanners and it's even more user-friendly. True, it's not without its faults, but at least one of the biggest problems can be fixed.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

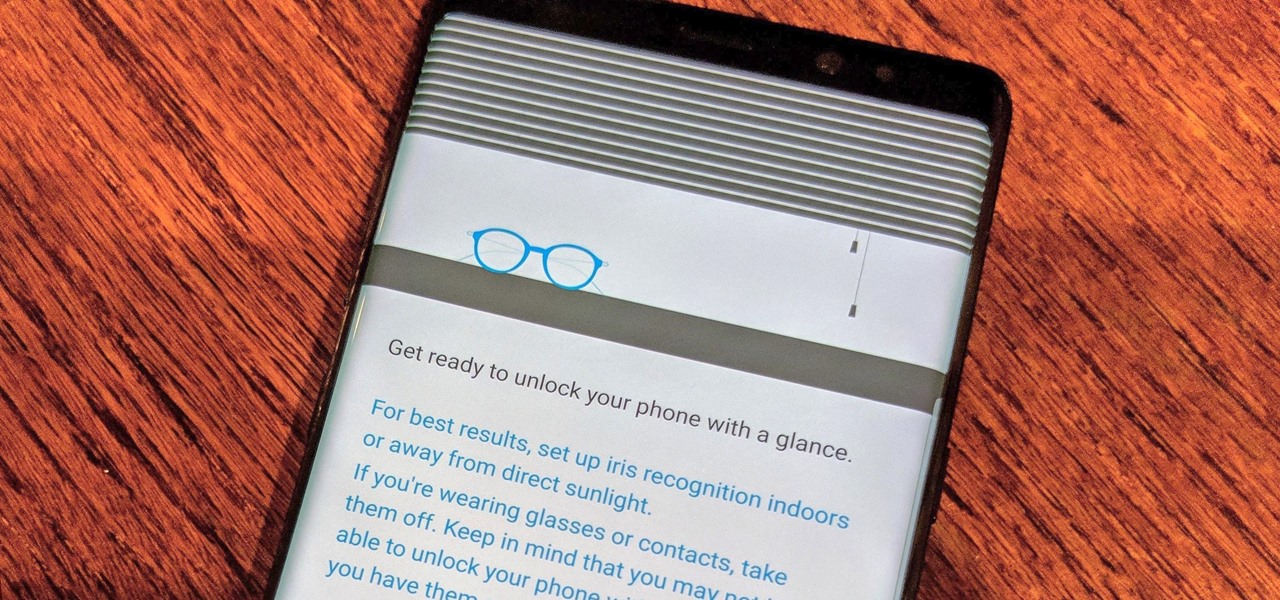
As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

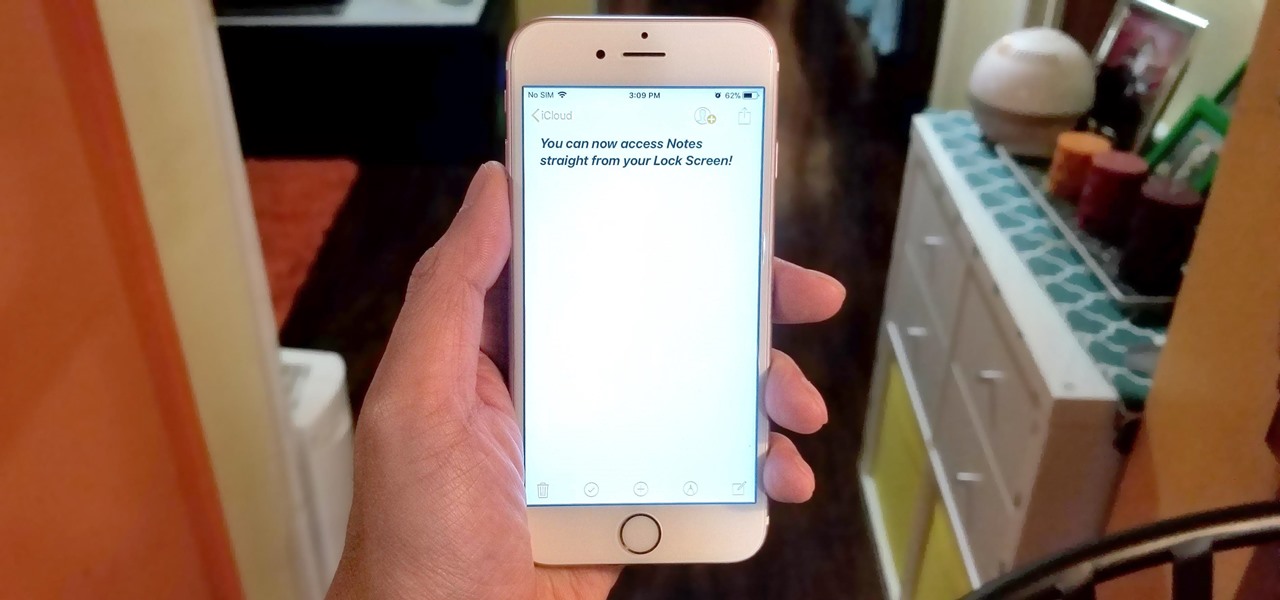
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

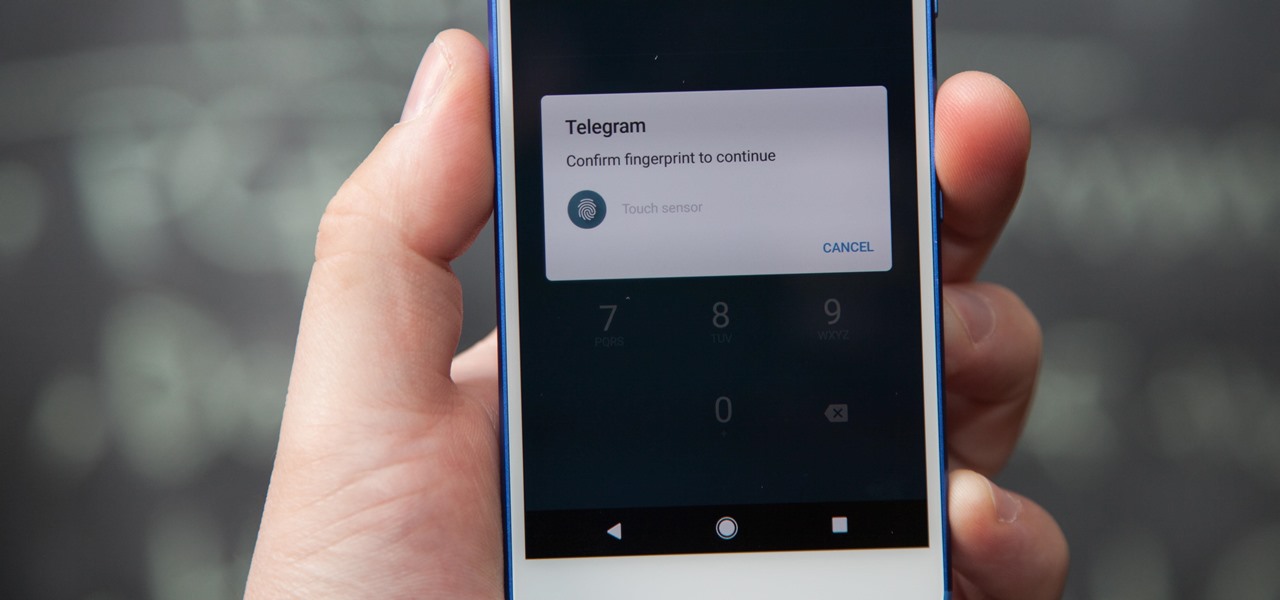
If you're using Telegram for its "Secret Chats" feature, which provides end-to-end encryption for your messages, then I'd highly recommend locking down the app itself with a passcode, PIN, or password. While your phone itself may have a secure lock screen already, if that gets compromised, you'll at least have an extra layer of security on your important conversations.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

When it comes to security, Android generally takes an all-or-nothing approach—once someone has your PIN, they're free to do just about anything, up to and including wiping your device. This is why you have to be extra careful to ensure that neither strangers nor friends are looking over your shoulder while you're entering your PIN.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Losing your phone is a much bigger ordeal today than it was just 10 years ago. Our smartphones carry with them lots of sensitive data that, in the wrong hands, is capable of being used for identity theft and fraud.

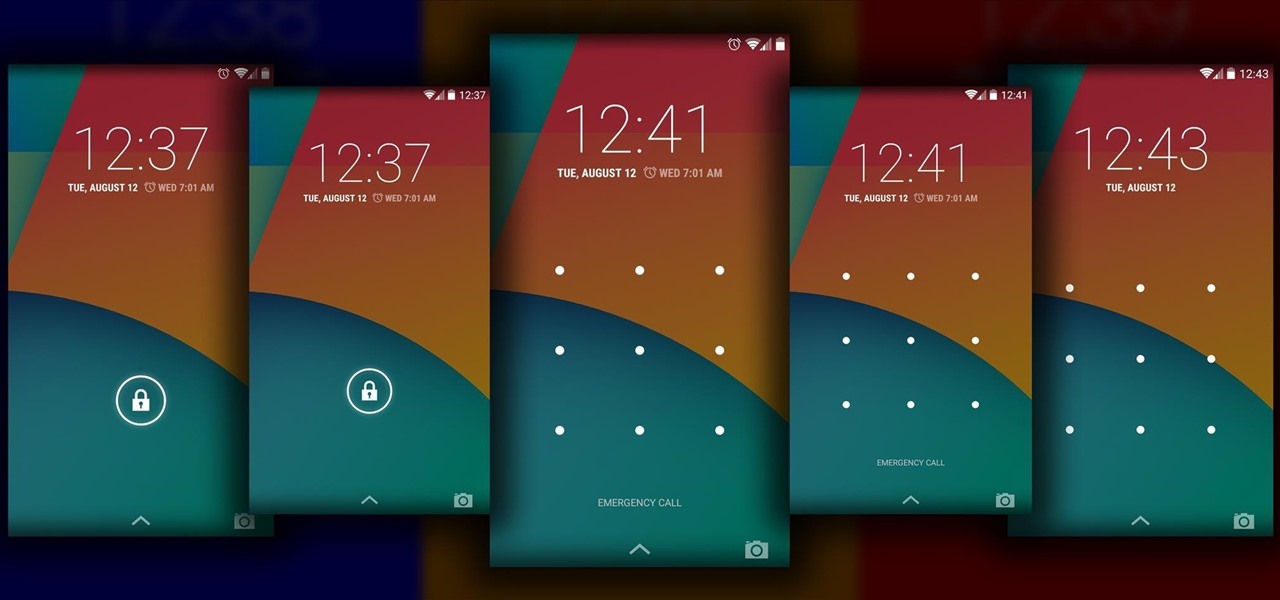
The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.

Welcome back, my greenhorn hackers!

Fashionably cool and awesome, this marvelous French Twist hair Style is as simple to make as it is elegant and stylish to flaunt. Just in few easy and accessible steps, this urbane style makes your appearance special and any outing memorable. Step 1: Comb Your Hair Neatly to Remove Any Tangles and Make Them Smooth. Step 2: Hold the Hair Together Like a Pony and Twist Them Till the Middle of the Pony and Make a Roll as Shown. Step 3: Once You Have Secured the Roll, Cover It with Surrounding Ha...

Being in your twenties is tough. You're not a child anymore, but also not quite a full-fledged "adult" yet. Sure, you do adult things like cook asparagus sometimes, but you're also sweating about securing enough likes on your social media posts.

Costume parties are in full effect this weekend, so with that said, how cool would this look at your Halloween party? Instructables user castor009 made two holes in the head (one for inserting the PVC tube, the other where the liquid will spew out) and insert the pipe and tubing, then stuffed it to secure everything. He then fit the bottom tubing through a pencil holder and attached it to a water pump. Then just add whatever you want to serve at the party (I would suggest anything red or blac...

In this tutorial, we learn how to take apart an Xbox 360 wireless controller for repair. First, grab your controller and grab a few different sizes of screwdrivers. After this, turn your controller over and start to remove all the different screws from their spots and place them onto a table where they won't fall. now, take the bar code off and take off the final screw that is on the inside. After this, you will be able to take apart your controller and fix whatever issue you are having with ...

Bleeding out your brakes is an important maintenance step, allowing you to flush out air bubbles and replace old brake fluid. There are several methods of doing this: a.) a two-person pump and hold; b.) a one-person pump and hold; c.) vacuum method; d.) pressure method; e.) reverse pressure method.

This is a video tutorial on how to take apart an XBox 360 gaming console. First, take off the face plate and the bottom as well as the top of the console. Then unclip the console from the front and back. Undo all the screws to open up the main console processor. To unscrew the screws, you need a 10 torx screwdriver. After unscrewing the screws, turn the console upside down and remove the top part. This will reveal the inside of your XBox 360. The video will show you how to take apart the cons...

A lot of the English you hear in the real world isn't taught in the classroom. This ESL tutorial gives examples of how people use "messed up", "screwed up" and "f*d up". This is real life and you need to know how to respond if someone says these things to you. Watch this how to video and you will be speaking and understanding English in no time.

A lesson in how to create screw type threads in the Mechanical CAD design application Autodesk Inventor.

Have you ever thought of building your own social networking site? Before you get to making websites like Facebook, you need to start off smaller, and this 29-part video series is where to begin with developing a social networking community website . Before you start with these lessons though, make sure you have all the following:

Check out this Do It Yourself (DIY) RV maintenance and repair video to learn how about RV battery maintenance. Know how to do it to keep your batteries running strong in your recreational vehicle with this RV tutorial video.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Over the past few days, we've learned a lot about Samsung's upcoming Galaxy S9 and S9+ smartphones. In addition to a full list of hardware specs, we have complete renders direct from renowned leaker Evan Blass. Of course, Samsung always has a few surprises up their sleeve, and today, we have some new information about the facial unlock method arriving on the S8.