
News: Official Android Oreo Update Already Hit Some Galaxy Note 8s
As the Samsung world anxiously awaits an official Android Oreo update, some Galaxy Note 8 users are waking up to find their devices have jumped the line. Are you one of them?


As the Samsung world anxiously awaits an official Android Oreo update, some Galaxy Note 8 users are waking up to find their devices have jumped the line. Are you one of them?
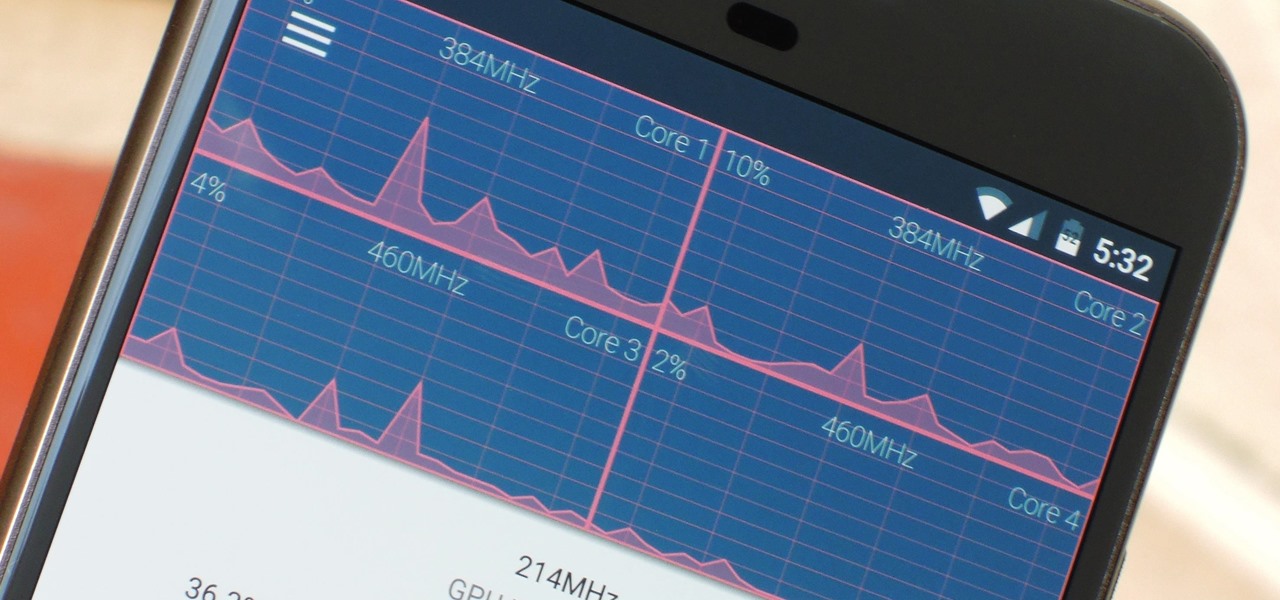
The Google Chrome browser does mostly everything well and integrates nicely with other Google services, but it's not exactly renowned for speed. With a rooted device and the aid of an app called Kernel Adiutor, however, you can make Chrome as nimble as some of the fastest browsers on the market.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.
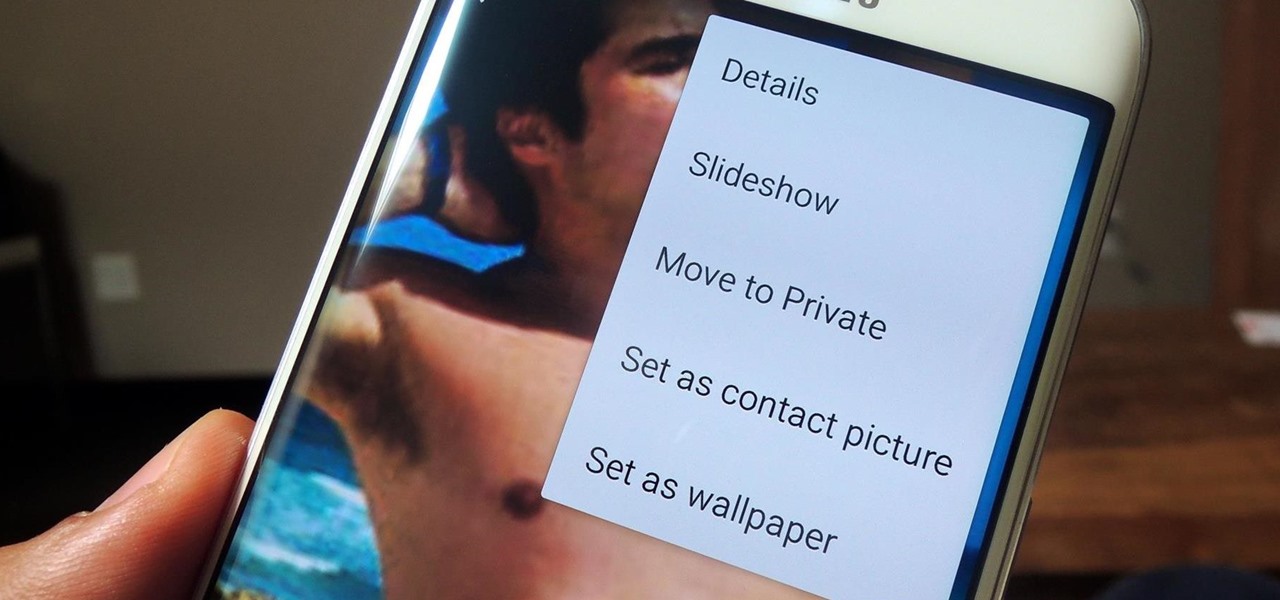
If you have a smartphone, chances are you have something on it you don't want others seeing. Whether it be photos, videos, or documents, some things are best left private. Not everyone is a saint, after all.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.
No matter how many PSAs are published on the topic, studies continue to show that we are generally terrible at creating secure passwords and PINs. Using the same password (or variations of it) for multiple sites is another huge no-no that the majority of people ignore, and even though you should change your passwords frequently, most of us don't.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

Even though we all know it's a bad idea, a lot of people still use their browser's store password function to keep up with all their accounts. While convenient, this shortcut also makes their passwords very easy to find if you have access to the computer they're stored on.

Everyone knows that using your phone and driving is illegal, and rightfully so. Tons of people die on the road everyday due to careless people texting or calling someone. Everybody knows that it's wrong, yet everyone still does it anyway.

In these days of mobile technology, losing your iPhone or iPod Touch is almost worse than losing your car keys. It becomes one of the most frantic searches you've ever had to endure. But you can relax now, because you can use Apple's Find My iPhone, iPad or iPod Touch service to locate your lost device.

In this video from Betty's Kitchen, learn how to make a delicious low-calorie vinaigrette for your salads. This tangy dressing has just a hint of raspberry sweetness and contains no oil so you can avoid all the fat and calories that oils bring. It tastes great and will keep for weeks, possibly even months, in your fridge. Enjoy!

In Obstetrics and Gynecology (OB/GYN), doctors deal specifically with the female reproductive organs, which means a lot of visual inspection of the vaginal area. Whether you're a doctor, surgeon, nurse, or nursing assistant, knowing how to properly drape a patient is detrimental to the patient feeling protected and secure with the hospital staff, along with having some privacy. This video will cover different types of draping techniques.
It’s called Urophagia—the art of consuming urine. There could be any number of reasons for having the desire to drink your own urine (or somebody else’s). There’s the so-called term “urine therapy,” which uses human urine as an alternative medicine. In urine therapy, or uropathy, it’s used therapeutically for various health, healing, and cosmetic purposes. There’s also those people who drink urine as sexual stimulation, where they want to share every part of each other. And then there’s the o...

Instead of paying to have someone else do it, learn how to flush your auto transmission fluid in less than 10 minutes by following this tutorial. Unknown to most people, is the fact that draining your transmission from the bottom, only removes about half of the fluid, while the rest remains. This tutorial shows how to do a complete flush. First, find out how much transmission fluid your vehicle needs by reading the owner's manual. You will also find out what type of product you need to use. R...

Tired of always having to ask tall folks to help you get stuff down from the top shelf? In this tutorial from Make Magazine, Kipkay teaches you how to build your own stilts. But while these stilts will make you taller, we don't suggest wearing them on the basketball court.
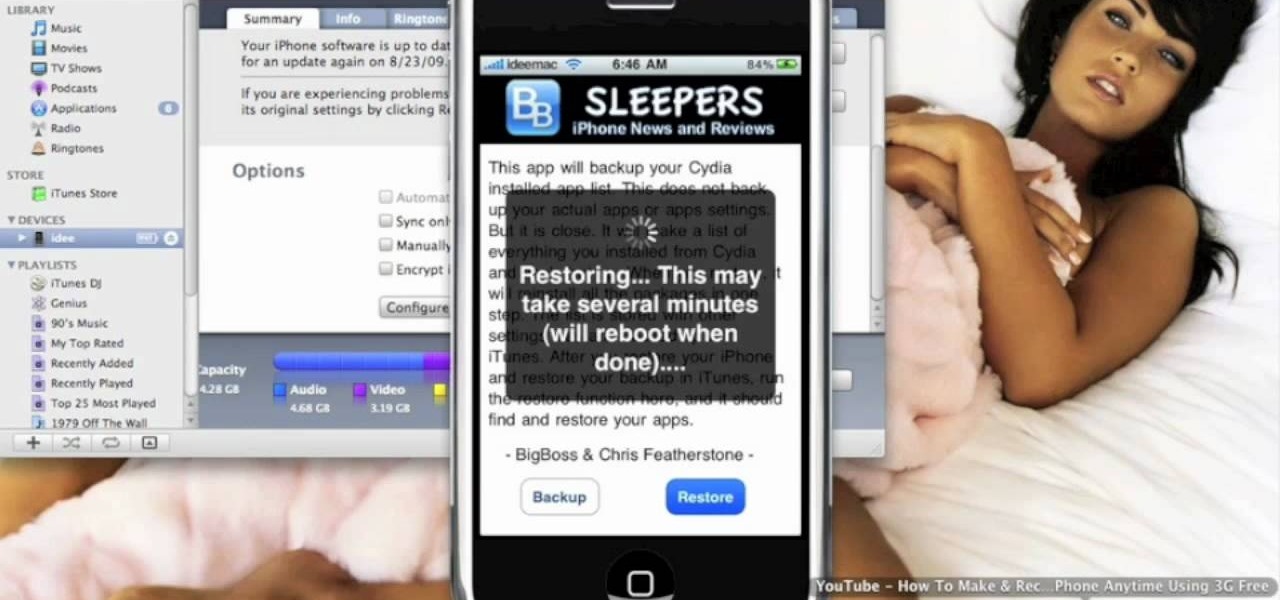
What happens if your jailbroken iPhone or iPod Touch gets destroyed? What happens if it merely malfunctions and poof—all of your applications are gone? You're screwed—unless you backed up your apps.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to create an old rusty control panel in Photoshop.

Check out this DIY video tutorial from Curbly, the best place to share pictures of your home, find design ideas, and get expert home-improvement advice.

A good way to install a window in a metal frame construction is to use some light gauge angle and screw it onto the sides of the window leaving a 10mm space for plaster. A flat head, self tapping screw is used to fix the window to the frame. Watch this video tutorial for a demonstration on how to install a window in a metal frame.

Watch this video to learn how to tie off an ice screw when rock climbing.

Repairs Universe demonstrates how to replace the LCD screen on the BlackBerry Curve 8900 phone. First, remove the SIM card, the battery and the back cover of the phone. Run a safe pry tool between the gap in the phone and the small back cover to remove the cover. Use a T-6 screwdriver, remove the six screws from the back of the phone. Then, pull up to remove the back layer from the phone. Flip the phone over and remove the front layer. Release the four clips with a safe pry tool and release t...

How to change the outdrive gear fluid on your boat.

Install a pond skimmerThe most critical steps to installing a skimmer are the water level and attaching the liner to the face plate with a water tight seal. The pond should be rocked in. The skimmer needs to be level from front to back and side to side. That's critical. Optimum water level is approximately 3/4 inch down from the top of the steel face. Use the level (tool) to determine the water level on the face plate. It's important to have the weir door work effectively. Prepare the area fo...

Josh Copp and Madeline Donahue show us how to build a light table from pine wood and plywood utilizing two fluorescent light fixtures as the light source inside the box. The frame of the box is fashioned out of two 1X8 planks cut into four pieces so that two sides are 30 inches and two sides are 22 3/8 inches. The base of the box is made of plywood or OSB and is 30X22 3/8. Once the pieces are cut and assembled using a pocket hole jig and wood screws, the inside of the box is painted with whit...

This is a great way to turn your treadmill into a walk station quickly and cost effectively. You only need a few things for this project: a tape measure, four shelf mounting brackets, screws, a drill, and a shelf.

First of all put a bucket under the trap. Now use your hand to loosen the handle of the PVC type trap. Loosen both the two plastic nuts on the ends. Remove the nuts that are holding to the drain pipe. Now when you remove this trap from the drain pipe a little dirty water comes out of it which gets collected in the bucket. Now check the trap for some hair and other clogs. This you have to remove and clean it out completely. Also check the drain pipe outlet for removing any hair or other clog. ...

Circuit bending an audio device typically involves removing the rear panel of the device and connecting any two circuit locations with a "jumper" wire, sending current from one part of the circuit into another. Results are monitored through either the device's internal speaker or by connecting an amplifier to the speaker output. If an interesting effect is achieved, this connection would be marked for future reference or kept active by either soldering a new connection or bridging it with cro...

Chef Jason Hill tells us how to open a champagne bottle without much noise safely. Before opening the bottle make sure it is chilled to about 45 to 50 degrees. You can fill a bucket with half ice cubes and half chilled water and chill it for 30 minutes or you can refrigerate the bottle for 3 hours .When the bottle is chill remove it and dry it with a towel and carefully remove the foil with the wired wood intact. Grab the neck of the bottle with your left hand and place your thumb over the co...

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...