Chances are, you just point, shoot, and share photos and videos on your iPhone without a second thought about how your privacy is affected. It's fairly easy to do so since the Camera and Photos apps that Apple provides seem so innocent. But there are a few things you need to know when it comes to shooting media, sharing it, and even deleting it.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

Mobile wallet Curve just released a new feature that lets you correct past mistakes. Sounds incredible, right? Unfortunately, the mistakes you can erase aren't things like forgetting to do an assignment in school, screwing up a job interview, or, well, your ex. However, you can switch the card you want to use to pay even after you've paid with Curve, and that's still pretty cool.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

Late last year, two surgeons from the Instituto de Ortopedia e Traumatologia de Jaraguá do Sul in Brazil started using a combination of 3D printing and the Microsoft HoloLens to help plan spinal surgeries. And now, with the rest of their team, they've successfully performed a surgical procedure on their first international patient using their 3D impression planning and augmented reality process.

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

Autodesk offers some of the most popular software for computer-aided design (CAD) projects, which involve all sorts of 3D rendering. Their tools are clearly suited for use with the Microsoft HoloLens, but so far very little supports HoloLens development outside of Unity. Why is that?

You're better than a can of Reddi-wip, which is why you should always make fresh whipped cream at home. It's extremely easy to make, won't have all those nasty preservatives, is thicker and creamier in consistency (like cream should be), and tastes much richer.

Video: . The following are 5 Simple household pranks you can pull off on friends and family this upcoming April Fools' Day! All the material needed you already have at home so lets get started! Check out the video tutorial for further instruction.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

The horizontal dotted icon in your iPhone's status bar serves as an indicator of your device's network strength. And while it does help provide an approximation of how strong your signal is, swapping it out to display an actual numeric value is a lot more precise and can change up the look of your iPhone (or at least the status bar). The process is quick, painless, and you don't even need to jailbreak your phone.

There are few kitchen tools as elusive as the oyster knife. Many people—even seafood lovers—don't own one. If you do own one, it probably gets used so infrequently that it gets sent to the very back of the shelf where it proceeds to get lost. Then you accidentally find the knife once a month when you don't need it, but can't for the life of you find the sneaky little thing when you do need it.

When it comes to security, there are usually only a handful of things that you want protected from prying eyes on your iPhone—private photos, scandalous videos, and important text, such as credit card and social security numbers.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

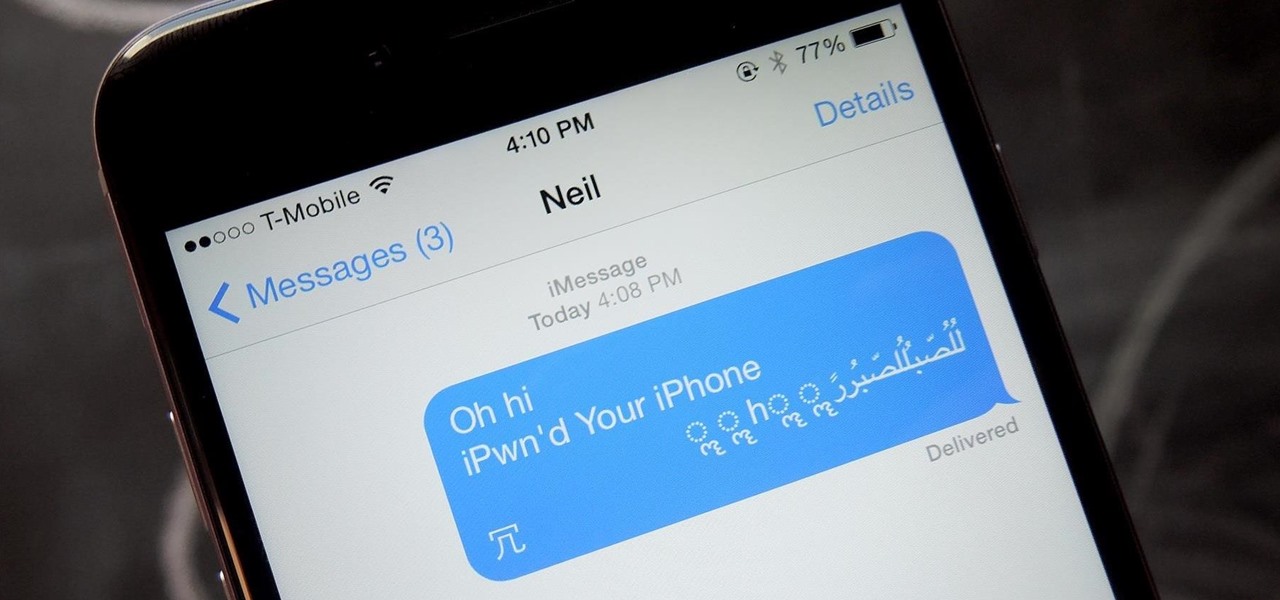
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

You know how when you finish a bag of potato chips, Cheetos, or some other glorious savory junk food snack, there's always some bits and crumbs in the bottom of the bag? And you know how you pour those into your mouth, making sure to get every last speck of dust, because it's the most delicious part?

No, your Apple Watch isn't totally hacker-proof, despite what some have claimed.

Bringing lunch to work or school is a win-win situation. You save money, you eat better, and you create less waste. But while the virtues of brown-bagging it are undeniable, it also gets kind of boring after a while. How many times can you shove a container of salad or noodles into an insulated sack before you say screw it and buy a $12 burrito for lunch instead?

With over 2 million uploaded videos and over 28 million people who had talked about it online by the end of August, the ALS Ice Bucket Challenge was the most viral social media event of 2014. Its popularity provided the ALS Association with $115 million in donations to date, with everyone from students to veterans to celebrities contributing.

The official release of iOS 8 was highly anticipated, but the truth is it may have been a little premature on Apple's part. Since its debut only a week ago, plenty of bugs and issues have been reported across the various compatible iPhone models.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.

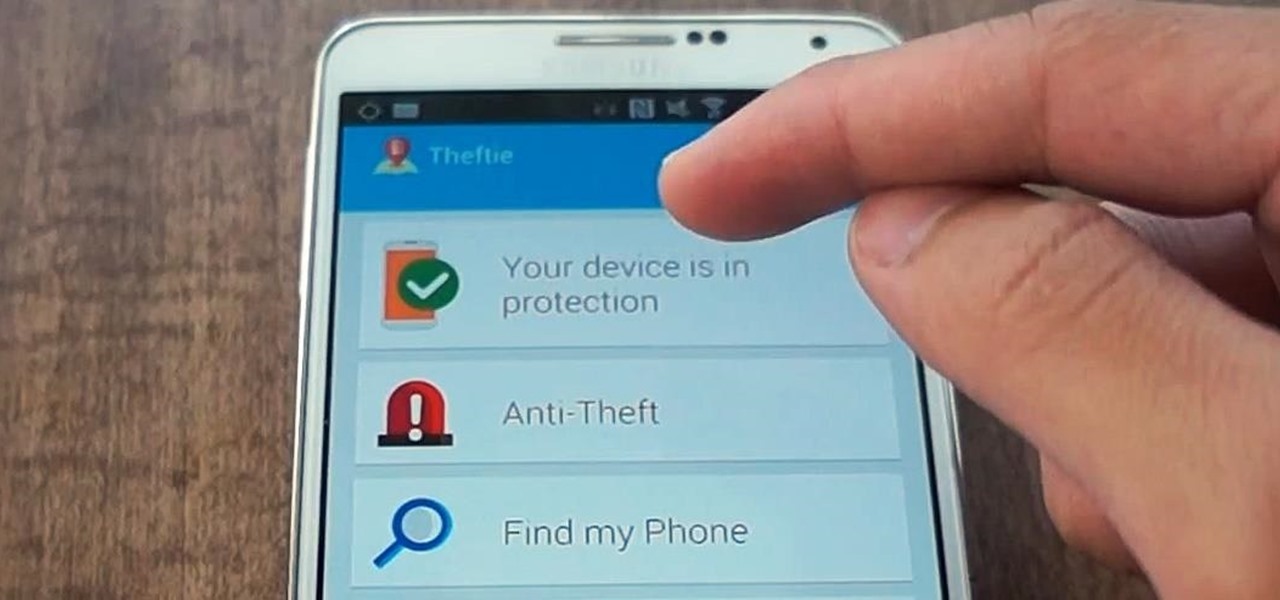
When you misplace your Android device, finding it with the Android Device Manager, or even better, Whistle Me, can help you find it no problem. But what about when your phone is not just hiding under the couch cushions? Your worst nightmare just came true. It's officially gone.

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

How to build a set of strong, stackable sturdy sawhorses. Let's face it, one of the most useful pieces of carpentry equipment would have to be a set of sawhorses. Every worksite, garage or workshop needs a set of sawhorses. They have numerous uses from stacking timber on, using as painting racks, to using as a temporary workbench by laying a door or some ply across two sawhorses. You can even use them as trestles for a dining table!

Today I'm going to show you 7 easy ways to organize your room. They are really simple and cheap so I hope you find them useful!

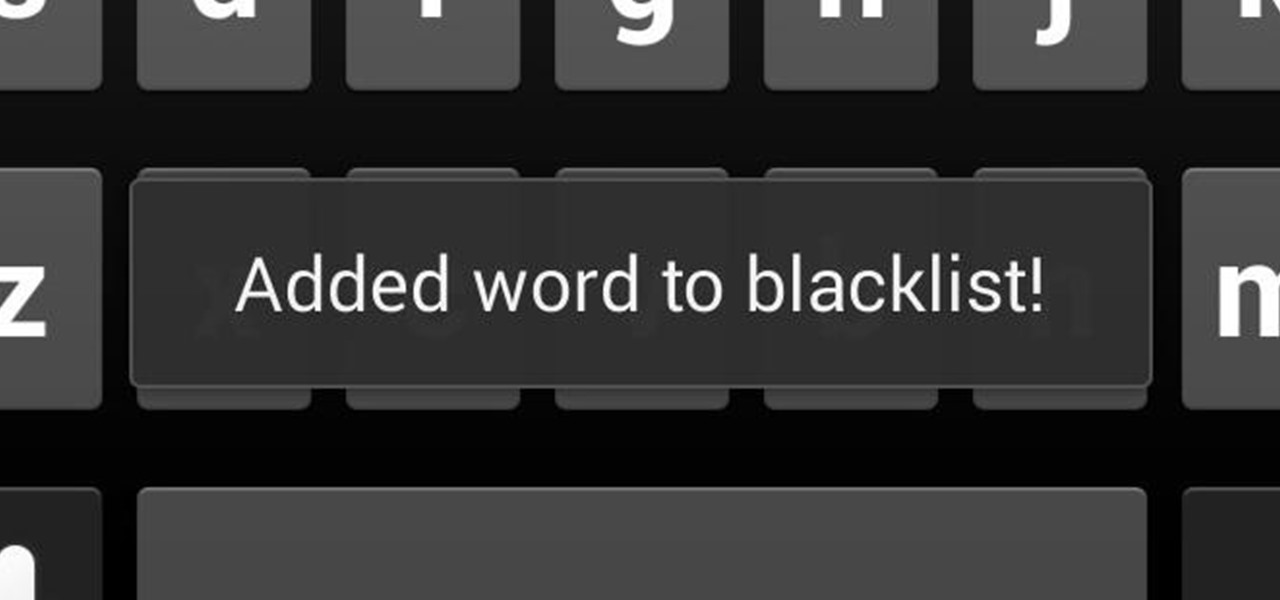
In the midst of furious finger typing on a small non-tactile screen, you're sure to make mistakes—so the majority of keyboards have autocorrect. Generally it works pretty well and is a welcomed feature.

If you're like me, then you were a little disappointed after updating your Nexus 7 to KitKat and realizing that not much has changed. The old Jelly Bean look still occupied your home screen, and there wasn't really anything noticeably new overall. All of that waiting and anticipation only to be left high and dry.

Making your own alcohol at home sounds like fun, but it's a long, complicated, and sometimes expensive process. You need all sorts of equipment, and by the time you're finished, it's been a few weeks—even months.

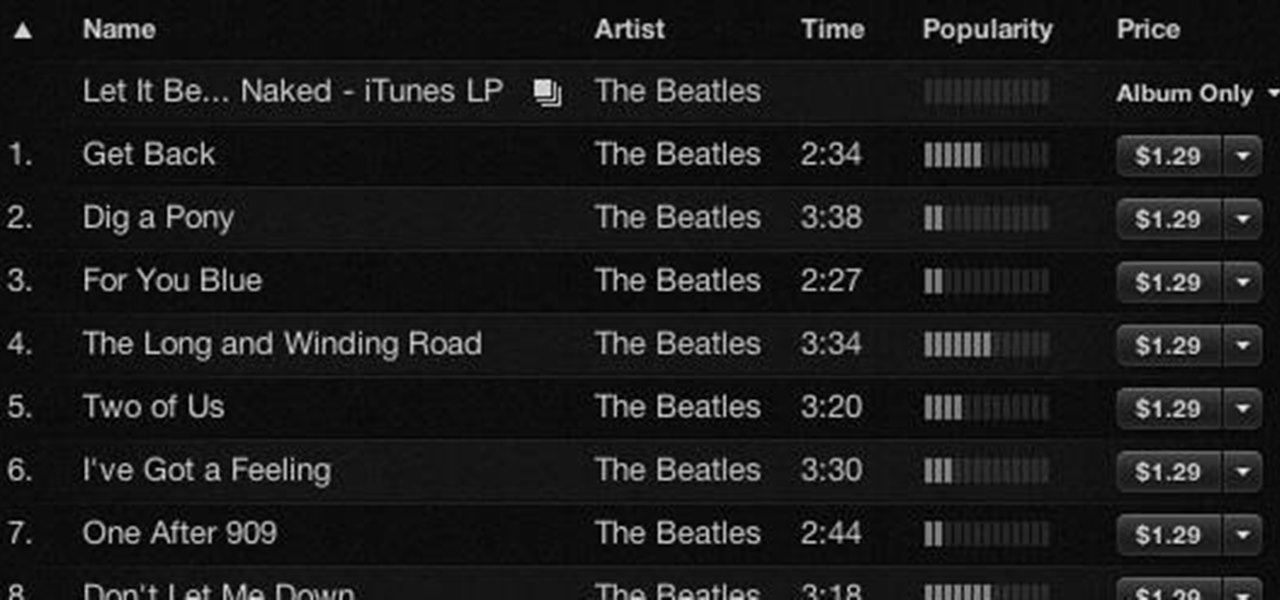
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

The Rubik's Cube is probably one of the most well-known puzzles, but if the number of articles about how to solve them is any indication, it's also one of the least understood. How many people do you know who actually know how to solve one?