
TypoGuy Explaining Anonymity: A Hackers Mindset
CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.


CEO's of IT companies doesn't know this because they are not a hacker. Only a true hacker can become a successful Security head officer.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.
Are you tired of uploading videos to different sites separately? It's really time consuming and difficult. Finally, there is a way to upload and distribute your videos to YouTube, Facebook, Dailymotion, and many more video-hosting websites in one go. No need to upload to every site separately and one by one.
This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.
I'm often reluctant to use a home screen launcher other than the stock one on my Android. Once you're well acclimated with something, complacency sets in, welcoming change with much resistance. Well, my friends, I have seen the error of my ways...

Raw fruit "cakes" are all the rage these days, and this stacked watermelon cake is easy to put together and is perfect for people of all ages. It's also perfect for every diet, as it's low-calorie, low-fat, gluten-free, and full of "good" carbs.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

bObsweep Standard and Pethair are made to easily transition between a variety of floor types, so they function efficiently in most spaces.

Presented by Apartments.com When looking for a new apartment, it's hard not to notice the improvements (on large and small scale) needed prior to moving in. While your landlord may be taking care of new carpeting, cleaning the central air vents, and fresh paint on the walls, there may be some additional improvements on your list that you can take care of on your own. Here are five quick improvements you can check off your list before the big move.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.
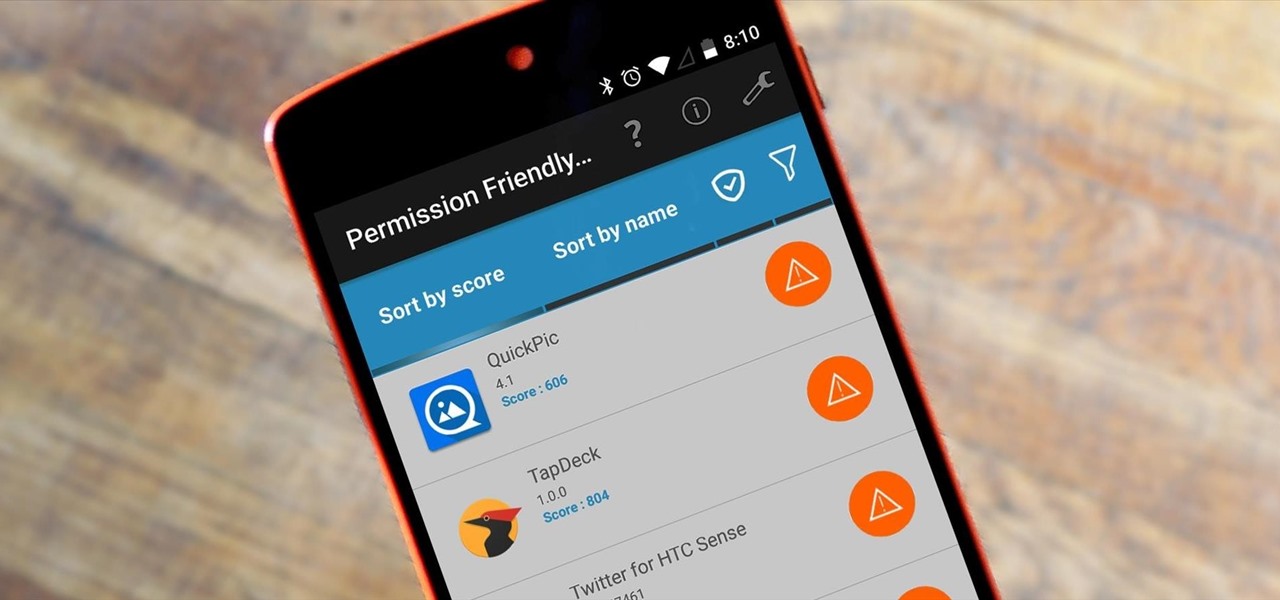
Android's permission system doles out access to certain system-level functions. Without it, our favorite apps wouldn't be able to perform their most basic operations. Picture a camera app that didn't have permission to access your camera sensor—now that wouldn't be much fun at all.

Before phones became mobile-gaming, music-playing, app-downloading devices, they were used simply to make convenient, cordless phone calls. There's so much on phones these days that a passcode is needed to keep everything secure, and making calls is now more complicated.

Yes, "Safer Internet Day" is a real thing, and it's actually been around for 12 years. This year, Google again will be commemorating the event by giving away a 2-gigabyte storage bump for their Google Drive cloud service if you simply run through a security checkup.
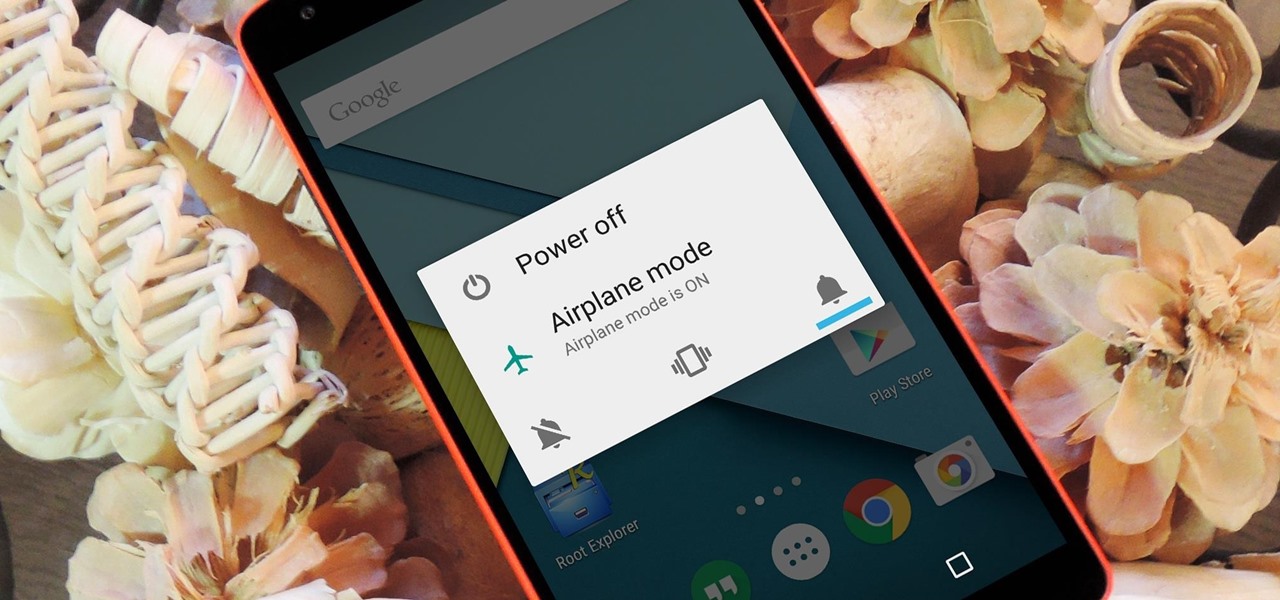
In an effort to make things simple and more secure, Google decided to slim down the power menu in Android 5.0. What once provided a quick link to shut your device down, turn on Airplane mode, and toggle volume states, has now been relegated to a simple power switch. Lucky for us, developer Gar Ynych has created a flashable ZIP that will revert these changes and restore functionality to the Nexus 5's power menu. In a few simple steps, you can add the volume toggles and Airplane mode switch rig...
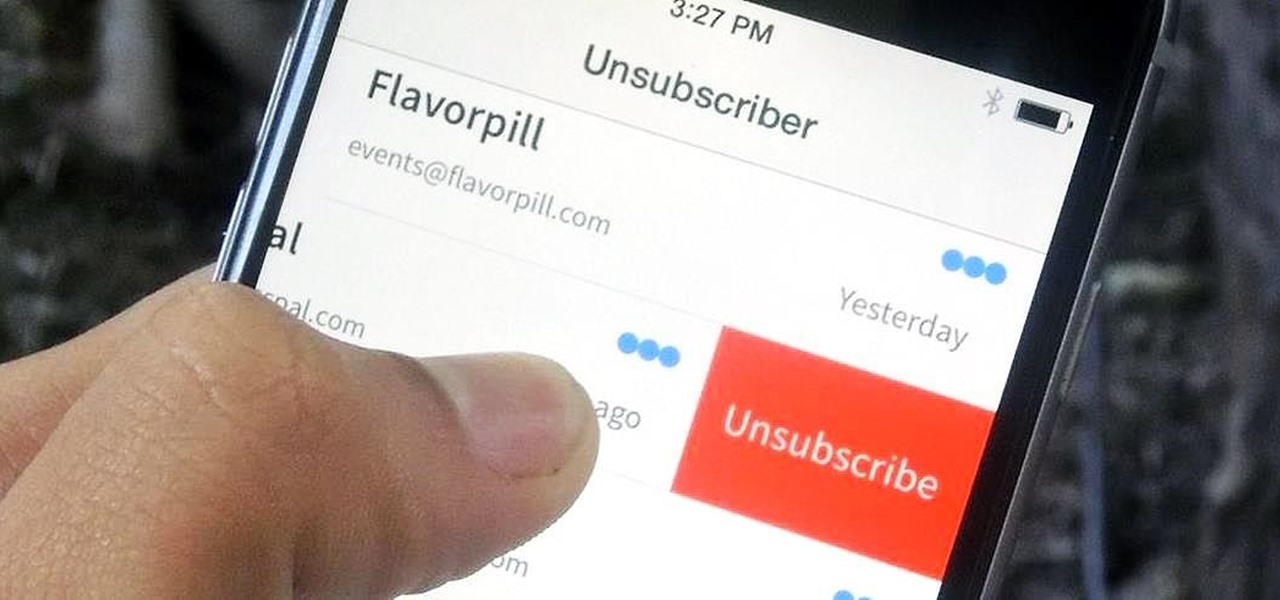
You've undoubtedly used your email address to sign up for a chance to win something online or to purchase something on sale. Often, these offers are too enticing to pass up, and you reason that you'll live with the consequences of handing out your information for the chance at making out big.

Whether you use a third-party keyboard or the stock offering, your Samsung device keeps a history of the last 20 words you copied on its clipboard. Samsung added this feature to Android to help make multitasking a bit easier, but if you use a password manager like LastPass, this feature quickly becomes a gaping hole in security. While you're copying and pasting your various passwords, the last 20 of them become freely available to anyone that gets their hands on your device.
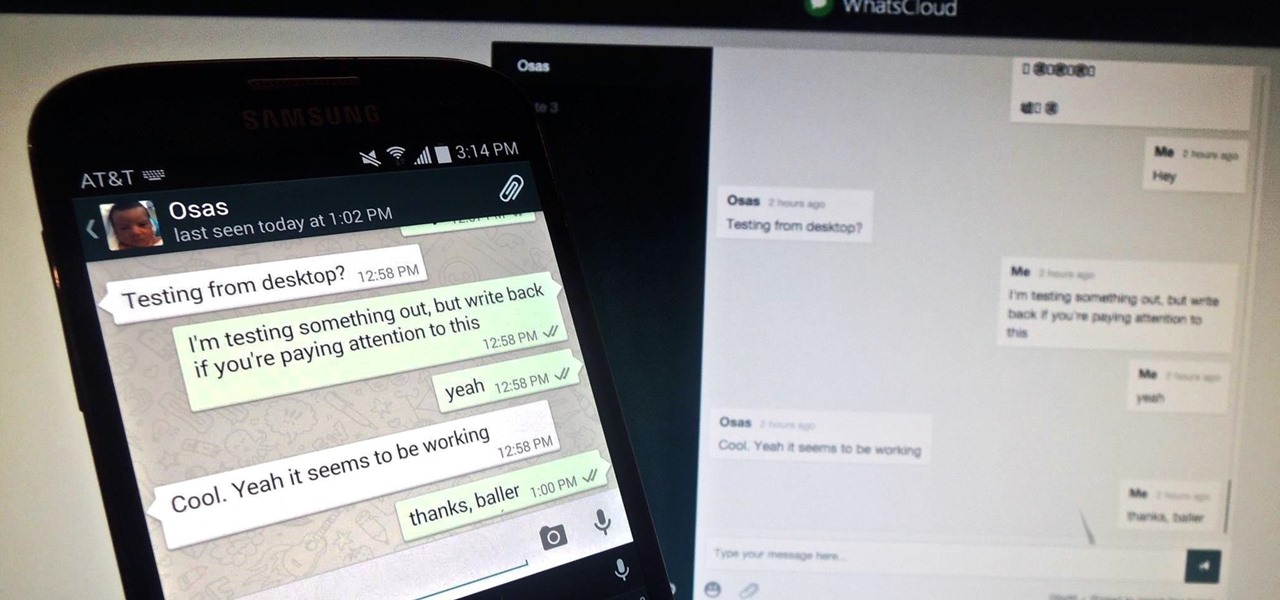
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.
A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Since the days of Friendster and MySpace, social media platforms have taken leaps forward, revolutionizing how we live our lives by changing the way we communicate with others. Not only has social media become a catalyst for major uprisings around the world, but on a personal level, it connects people together in ways that were unimaginable even 10 year ago—no one was taking pictures of their brunch to share with the world in 2004.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.
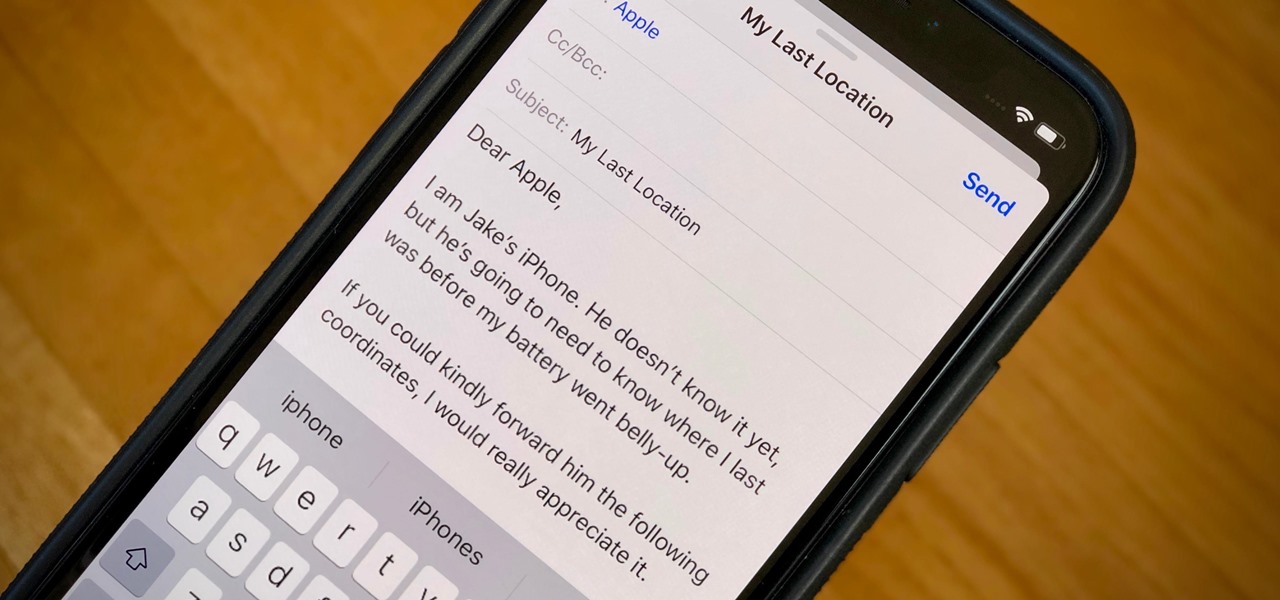
When your iPhone can't be found, Find My iPhone is a true lifesaver. When you use the feature, you can ping your iPhone and even see its current location on a real-time map. But what happens when your iPhone runs out of battery? Find My iPhone can't locate a dead iPhone, can it? You might be surprised to know it can, to a certain degree.
Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Being healthy and active will help you live longer, but finding the strength to work out? That's hard. What does it do for me right now? I mean, here I sit, writing this article, thinking about going for a run, and I feel good just for thinking about running. But will I do it? Nah, I'm too lazy.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

Lock screen apps are a dime a dozen, but every now and then one pops up that defies expectations. We've already covered some good ones for the Samsung Galaxy S4, including Picture Password Lockscreen (which gives you secret unlock gestures), SlideLock (which improves notifications), and TimePIN (which gives you a more clever PIN).

Back in August, Google introduced Android Device Manager. This new service allowed you to locate, lock, or wipe a lost or stolen Android device from either a companion app or a web interface. Effectively, this is the "kill switch" that legislators are clamoring for.
In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!
If you're as bad at locking your Nexus up as I am, you have the "slide" option set for your screen lock. It may not be the most secure option, but it's definitely the easiest way to unlock your device while being able to utilize lock screen widgets.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.
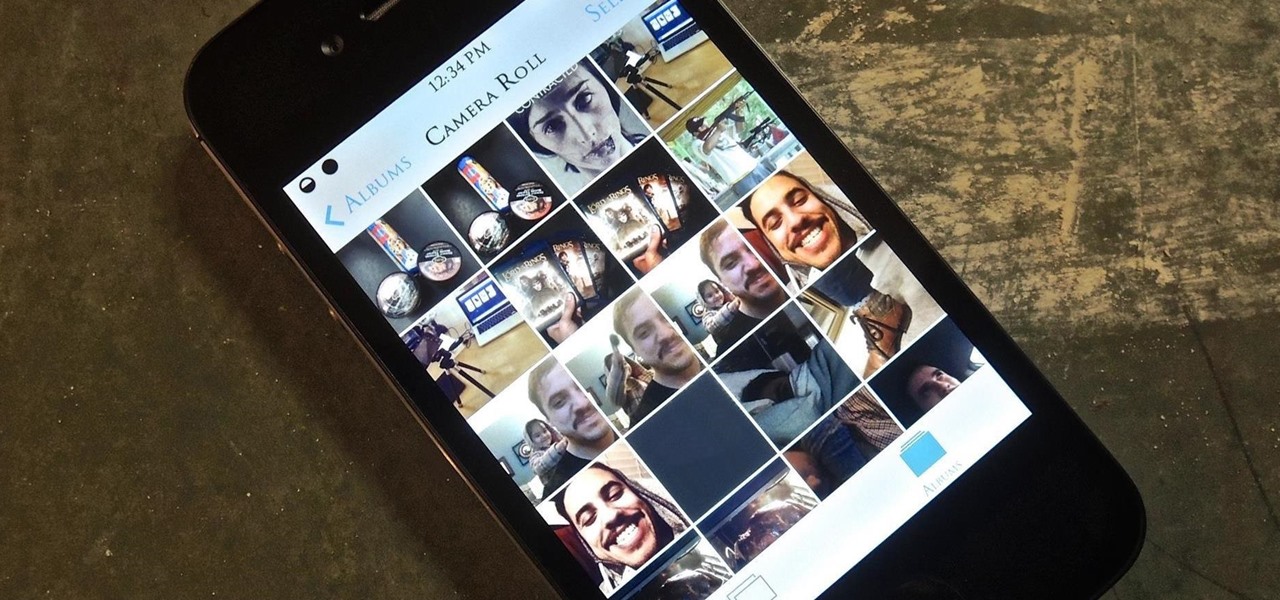
I have over 400 photos on my iPhone, and I don't even know where half of them came from. Scrolling through all of those pictures is a pain in the ass, but it's not nearly as bad as trying to actually find an old image. Organization is not my strong suit, so I'm definitely not the type to create new albums to sort through my 400+ photos.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.