Using your iPhone for a smart home remote just keeps getting better and better. Apple has consistently improved its HomeKit platform since the Home app came out, adding new features, tweaks, and refinements to the system with each update. And iOS 14 continues this trend with a few changes to help make your home even smarter and easier to use.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

If you're one who enjoys a good DIY project, or if you're just tired of paying exorbitant labor fees to have your vehicle serviced every 5,000 miles, changing your own oil can be a rewarding endeavor. Even though cars and trucks are becoming increasingly over-engineered these days, manufacturers generally see to it that the basic maintenance items can still be taken care of in your driveway with a few common tools.

As I said in this earlier post, there's no easy way to explain or define the Steampunk aesthetic. There are a large number of Steampunk tropes or "cues", as I call them, that bring to mind the feeling of Steampunk. These cues combine to push past the "not-Steampunk" threshold into firmly "Steampunk" territory.

Water is an important resource and it needs preservation. Older toilets suck up way more water than necessary, causing both high water bills and pain for the environment. Follow this tutorial, and learn how turn your old toilet into a newer low-flow model.

You can help keep your laptop cool by fixing a malfunctioning laptop fan. With a screwdriver and some compressed air you can clear away any obstructions. Think about where you are setting down your laptop as soft surfaces can block air intake.

In this online video series learn from expert professional mechanic Nathan McCullough who graduated from Nashville Auto-Diesel College with a Grade Point Average of 3.5 and received their craftsmanship award and honor seal. Learn important automotive Serpentine belt topics including: what is a Serpentine belt, locating the Serpentine belt, replacing the Serpentine belt, when to check the Serpentine belt, types of wear to look for, Jacking Screw Tensioner, Serpentine belt removal, checking the...

Ready to try and sew-in your own weave? It's a big decision. As with everything that concerns our hair, we struggle with the pros and cons and often dwell on what could go wrong. Pixie cut. Perm or not? New shade (of pink, purple, or blue). These are all major decisions because ... well, it's our hair, and hair is such a big part of our style. To get a weave or not calls for careful consideration, and to sew one in yourself, that's an even bigger internal debate.

The warmth of a fire is great while camping or on a cold winter’s night but it can be difficult to get those log roaring. Use materials you have at home to create some easy, fool-proof fire starters that you can use the next time you need to get some logs burning.

Here is a fun afternoon project that will add a little fare to your dogs wardrobe. Instead of buying your next dog collar, try making one out of an old belt. Some say dogs look like their owners and now they can dress like them too.

Love the beauty and fresh fruit of trees but have limited space? Try your hand at dwarfing a tree. You can enjoy all the benefits of a tree without any worry of the tree outgrowing the area or roots damaging side walks and property. Plus, they just look adorable.

Dawn your flannel and grow out your beard, it’s time to do some log cutting. Put good use to unwanted trees or extra lumber by making proper logs. It may seem self explanatory but the correct form will create uniform, crack free logs and keep you with all your fingers.

Show up the other kids at school and bring your teacher a super-sized apple, well, paper-bag apple that is. Great project to do with the family or in the classroom. Create a festive apple using just paper-bag and some newspaper.

A bouquet of fresh roses is wonderful but real roses soon fade and die. Make a rose that will last forever, or at least a lot longer that a freshly cut one. Give your rose to someone special or use it as a decoration.

In this video demonstration you will see the work done on a GM 3.1 Liter V6; your instructor is replacing the cam cover seal. First raise the car into the air, remove the tire wheel assembly and place a jack stand underneath the car or vehicle on the side where you have removed the tire wheel assembly. Now remove the serpentine belt from the engine by using a 3/8ths breaker bar. Place it on the tensioner and lift up while removing the belt from the alternator. Keep lifting the belt out from t...

Vacuum the floor and make sure that the surface is clean and free from anything sticking up out of the floor. This is important so that there are no uneven areas when you start laying the laminate flooring.

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

With every new Galaxy flagship release comes the age-old dilemma: do I choose great hardware or great software? For years, Samsung has given users the best components available on any smartphone. The problem is the software is an acquired taste. But there is something you can do about it.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

You watched the live stream, pored over the specs, and are now super excited for the Google Pixel 4. But specs don't tell you everything. After using the Pixel 4 XL for over a week now, we've found several things you wouldn't know without getting your hands on the phone.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

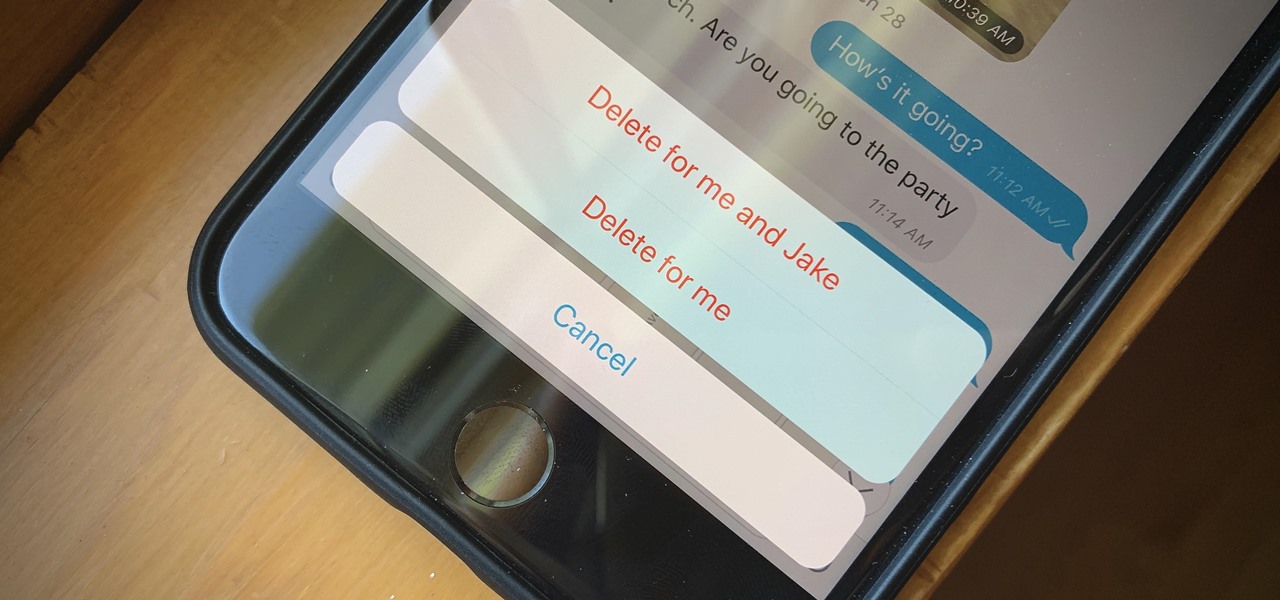
If you're looking to keep your conversations private, look no further than Telegram. Its cloud-based chats are secure and its optional end-to-end encrypted chats even more so, but you can't really prevent someone in the conversation from sharing your messages. However, you can lessen that chance by taking back your messages, deleting them for both you and the other end of the discussion.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

With Apple releasing the iPhone XR, it appears Samsung is looking to challenge this "budget flagship" option head-on. They brought their usual two phone releases this year, but also threw in another three for a total of five phones, including the Samsung Galaxy S10e. And for many, this might be the option to look at.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

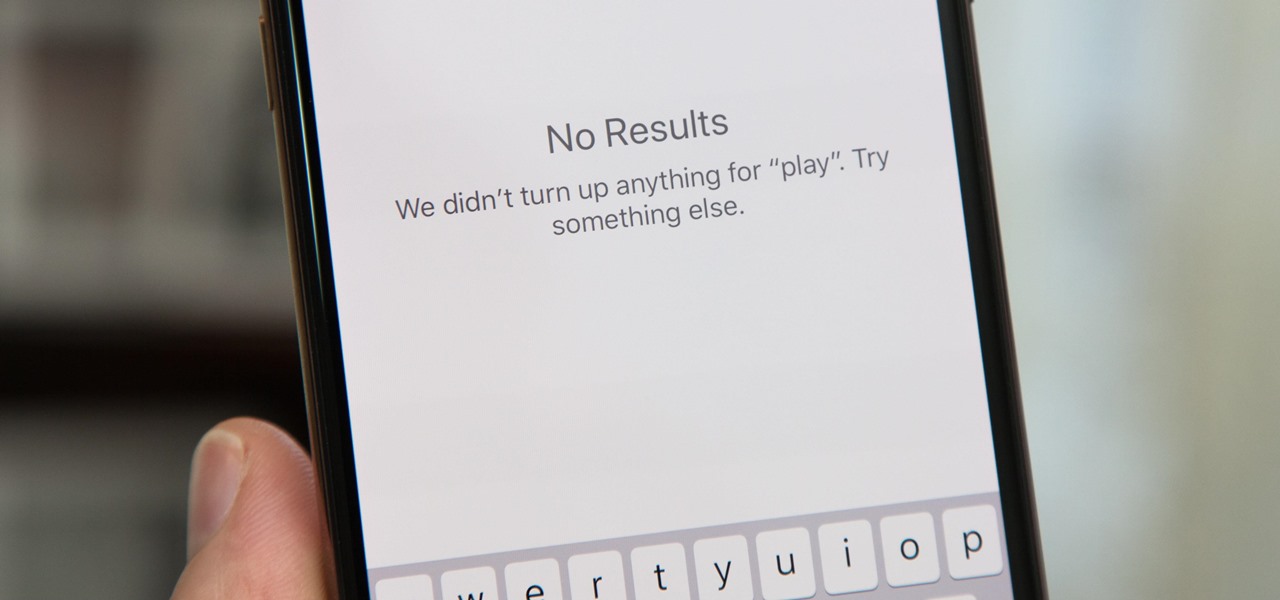
There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The rumors are still hot that Apple might include an 18-watt USB Type-C power adapter with the upcoming iPhone lineup so that there's fast-charging capability right out of the box. Leaked photos have surfaced that substantiate this rumor, though, they could also be fake. But how would ditching the old-style 5-watt USB Type-A power cube affect you if it's true?

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.