In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Making a custom location on Instagram is one of the best ways to generate traffic to your account. It gives you that extra uniqueness when it comes to standing out amongst other companies. It also allows people to check in at the same location, further promoting your account across other platforms.

Maybe you decided to make your own pumpkin pureé because of all the buzz about canned pumpkin actually being squash (which, by the way, is a load of bull: it's made with ugly pumpkins, but pumpkins nonetheless). Or maybe you just wanted to be that person that proudly proclaims that they made everything from scratch for their Thanksgiving feast this year (ahem, me).

Wheat toast. White toast. Sweet potato toast. Okay, one of these things is not like the others... Don't Miss:

Mochi seems to be everywhere these days: as a topping at your local frozen yogurt shop, in ice cream balls (the green tea ones are heaven), and as colorful treats all over Instagram. It seems like mocha mania is in full force!

There are two kinds of people standing in the international section of the grocery store: the kind who love Pocky and the kind who don't yet know that they love Pocky because they've never had it.

If you're here, you're probably one of the seven people dedicated to making Mac n' Cheetos a permanent part of the Burger King menu.

Grilled meat may be a staple of summer barbecues, but grilled cheese should have a place at your outdoor feast as well. I don't mean taking a slice or two of cheese, slapping it between two pieces of bread, and putting it in a pan to create a grilled cheese sandwich. No, I mean literally grilled cheese.

In many places, May has given way to a surplus of strawberries cluttering the produce aisle. These sweet berries are great in a wide variety of delicious baked goods, from pies to cakes and everything in between.

There are countless recipes for mug cakes (and breads) on the internet, but not all of them are good. Mug cakes promise a warm, moist, and fluffy cake after a few minutes and with minimal work... but sometimes, all you end up with is a chewy, rubbery mess.

Desserts always taste better when they are sugar-coated—and even more so when they're coated in powdered sugar. In particular, crinkle cookies—cake-y cookies that are chewy on the inside and crispy on the outside—are famous for the powdered sugar that creates their cracked appearance.

I am officially breaking up with my daily breakfast of avocado toast and embarking on a promising new relationship with savory oatmeal. Yes, you read that right—savory oatmeal.

Local cafés and food bloggers are catching onto a gourmet toast trend that makes bread and butter look like movies before color TV was invented.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

Almost every bread recipe will tell you to look for a golden brown crust or to tap on the bottom of your loaf and listen for a hollow sound. That visual and sound technique will work most of the time, but it can still come up short, leaving you with a soft and gooey spot in the middle of your loaf.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

I was bored when I found this piece of literature: ==Phrack Inc.==

Beer isn't just for drinking anymore. There are many useful and surprising things that an ice-cold brewski can help you accomplish, from household chores to better-tasting food. It can even help you look and feel healthier.

Why did I write this when they're tons of scanning tools available.

Dulce de leche is a beautiful, caramel-like spread that you can slather onto bread or use to flavor cakes, cookies, or flan. You can also use it as a drizzle for ice cream, chocolate candies, and pastries. It tastes like heavenly toffee, translates roughly to "milk candy," and is popular all over Latin and South America. A version of the confection is also popular in the Philippines, in Russia, and is known in France as "confiture de lait." The traditional way to make dulce de leche is to slo...

While most people build collections of things with intrinsic value such as coins, stamps, or rare post cards, I collect wine corks—the natural ones, not the plastic kind. Corks are a natural product harvested from the cork oak tree. It takes the better part of 10 to 12 years before a tree can have its bark manually removed for the production of cork. Thankfully, no tree is harmed in the process and in 12 years, the tree bark can be harvested yet again.

In recent years, Hollywood has taken a shine to hackers, with hackers appearing in almost every heist or mystery movie now. This can be both good and bad for our profession. As we know, whichever way Hollywood decides to depict our profession is how most people will perceive it.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.

If you've ever had issues charging your iPad, iPhone, or iPod touch, like most other Apple products, the culprit to blame is usually a frayed or damaged cable. It's a common design flaw due to the thinness of the cords and the weak sheath surrounding them — but that's not always the problem.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

As someone who's dependent on glasses to see on an everyday basis, losing or misplacing them is obviously a bad thing. I can't even see clearly enough to find the glasses that I just lost, so I'm pretty much blind now.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

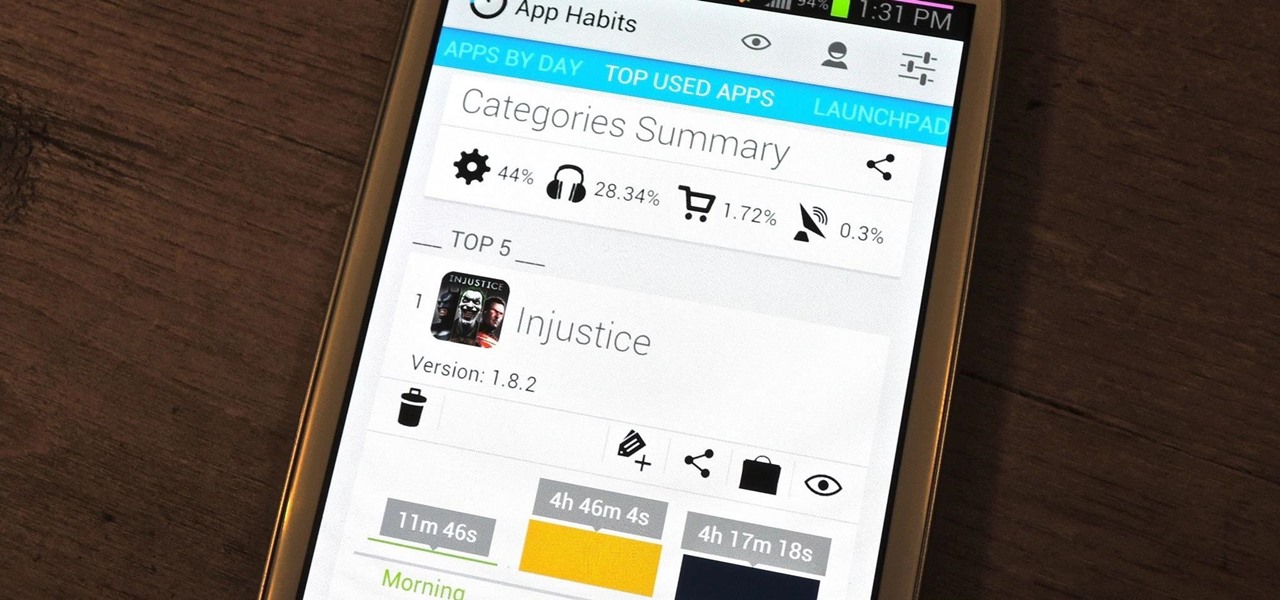
In today's dog-eat-dog world, every minute matters. Whether you're in school or working for the Man, a huge amount of your day is consumed by tasks, assignments, and other kinds of work. Then there's the time you spend playing video games, watching TV, or screwing around on your Samsung Galaxy S3.

It seems nowadays the word "easy" has taken on an alternate meaning. When I see "easy," I expect a quick and painless process, but when it comes to flashing or installing a custom ROM, easy means anything but.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

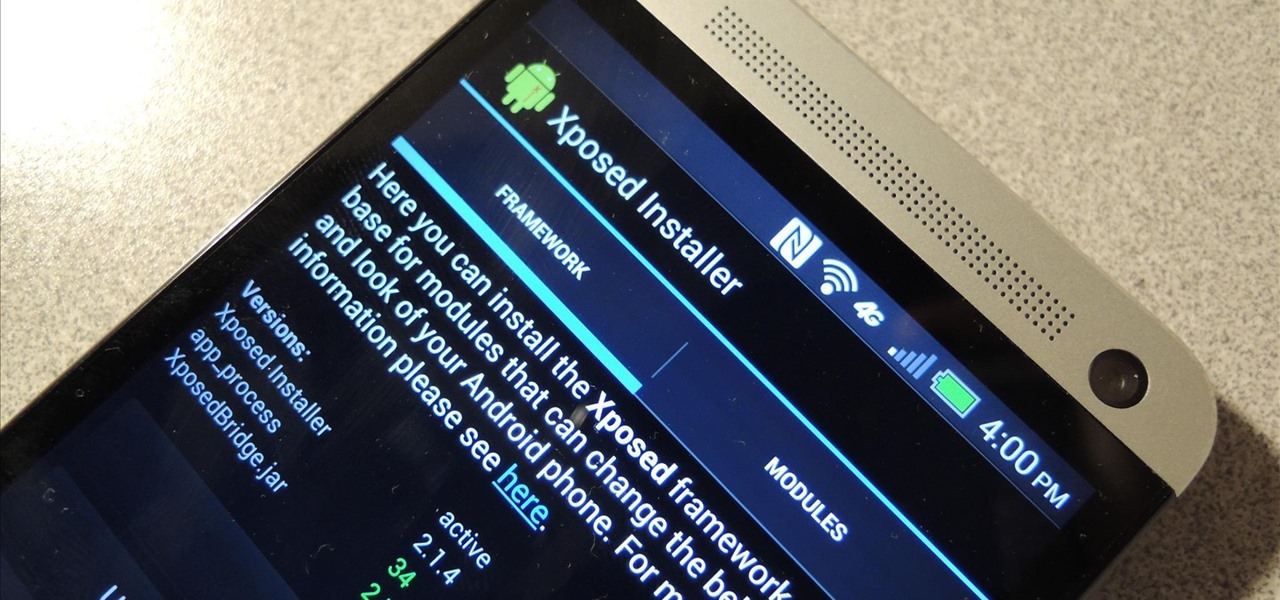
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

This summer's going to be a hot one, so skip the water pistol this year and break out the big guns! In this project, I'll be showing you how to build a water balloon shotgun—a high-powered water balloon launcher that's capable of firing 17 water balloons at the same time!