Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Welcome back, my greenhorn hackers!

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

And we meet again Crackers! Welcome to my 7th post (Part-2), this tutorial will explain about some more basics of Batch Scripting, with C00L Scripts, which in turn will help you learn and understand better

A friend of mine has a crazy amount of Reddit karma and gold, and yesterday he let me in on his secret. This person, who will remain unnamed for obvious reasons, created a Python script called Reddit Karma Crawler that finds rising posts before they get too popular.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

AppleScript is quite an easy scripting language to use. In this guide, I will be showing you several commands. Near the end, I will show how these can be used to create a fake virus that actually does no harm.

Automation has been a buzz word for quite some time now, but the principles behind it are as strong as ever. For a hacker or pentester, Bash scripting is one form of automation that cannot be ignored. Virtually any command that can be run from the terminal can be scripted — and should be, in many cases — to save valuable time and effort. And a Bash script just happens to be great for recon.

In this video series, watch as screenwriter and producer Chris Cobb teaches you how to turn a script into a production board. learn how to break the pages down, how to transfer the scripts onto the breakdown page, how to color code the script, and how to put together the production board.

Mike and Rajo from the SubStream's "Film Lab" have some tips regarding pre-production and development for proper script format.

Bash (Shell) Scripting for Beginners Intro

Mike from the SubStream's "Film Lab" has some tips regarding screenwriting, specifically... documentary scripts.

Greasemonkey scripts allow Mozilla Firefox and Google Chrome to be augmented in powerful ways. Take these two Greasemonkey scripts will help add information to your favicons when using Google Calendar and Gmail - now you can see the current date and unread message counts on their respective favicons.

Support and improve your stereo work by using Stereoscopic Scripts in Adobe After Effects. With After Effects, it's easy. Whether you're new to Adobe's popular motion graphics and compositing software or a seasoned video professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Whether you're new to Adobe After Effects or a seasoned digital film professional after a general overview of CS5's most vital new features, you're sure to be well served by this official video tutorial from the folks at Adobe TV. In it, you'll learn how to turn spoken dialogue into searchable text either by synchronizing content with your Adobe Story script, or by using reference scripts that are optimized for your content. Also see how to accelerate editing by marking in and out points in t...

Block Facebook scripts on sites that you visit with Safari, Chrome and Firefox by installing an add-on called Facebook Blocker. This removes the "Like" buttons, "Recommended" lists and prevents Facebook scripts from tracking your browsing history. Veronica from Tekzilla Daily demonstrates the features of this new add-on.

Tinkernut presents the Bluetooth headset hack! This video shows one of the vulnerabilities of some bluetooth headsets. To prevent this vulnerability, it's best to invest a little more money into a more secure headset and making sure your headset is turned off when not in use. You can find all of the links and scripts used in this video, as well as find answers to questions you may have at the link below:

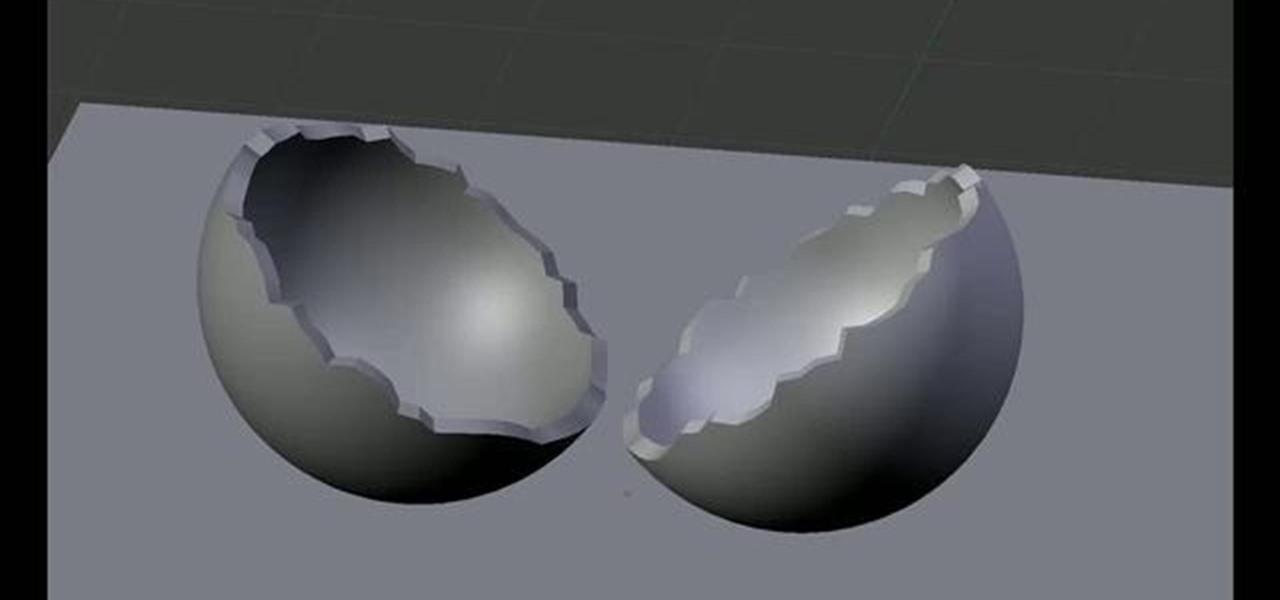
Learn how to create a crack in a 3D object in two minute or less with this video guide. The technique involves no scripts, just a powerful tool that has been right under your nose for years! Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial. For more information, including step-by-step instructions,...

The Wedge ROP is a render output driver, which can be used to change variables on the fly while rendering. This can be very useful when simulating, in that you can test out different parameters to see the different results. It's a relatively new feature in Houdini 9.5.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

In this tutorial, we learn how to install themes for Google Chrome. First, enable user scripts by visiting the website Chrome user scripts. Install the Chrome 4.0 onto your computer, then type in "chrome.exe --enable-user-scripts" into your run menu. After this, scripts will show up on your page. Scroll through the different types of themes until you find one that you like the best. To use these, you simply just click on the image and then download which one you like. You can install differen...

On mobile devices, the Notification Center received a huge facelift when iOS 8 was released, but it wasn't until Yosemite that its Mac OS X counterpart received the same amount of love—especially the much needed ability to add custom widgets, like a FaceTime dialer.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

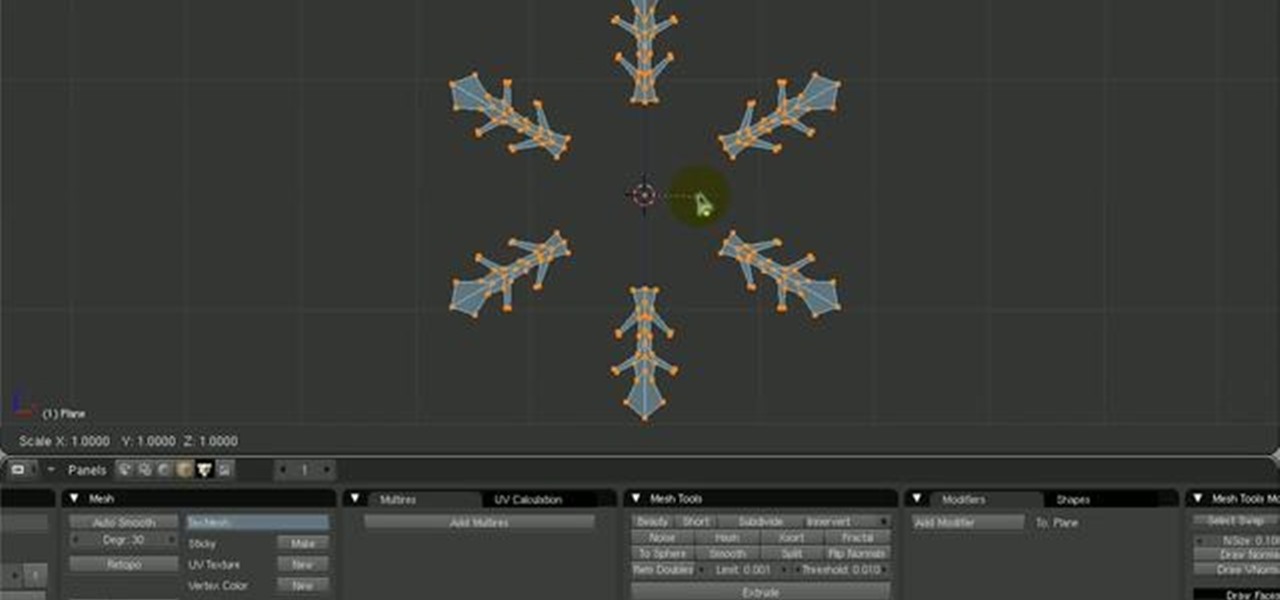
Learn how to create layered snow flake patterns in this tutorial by using scripts and nodes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or are a seasoned digital artist merely on the lookout for new tips and tricks, you're sure to be well served by this free video software tutorial from the folks at CG Cookie. For more information, including step-by-step instructions, take a look!

Writing a script is easy, but writing a script that the Hollywood elite would actually like to pick up is a totally different story. Any aspiring screenwriter will find this information about action in scripts helpful.