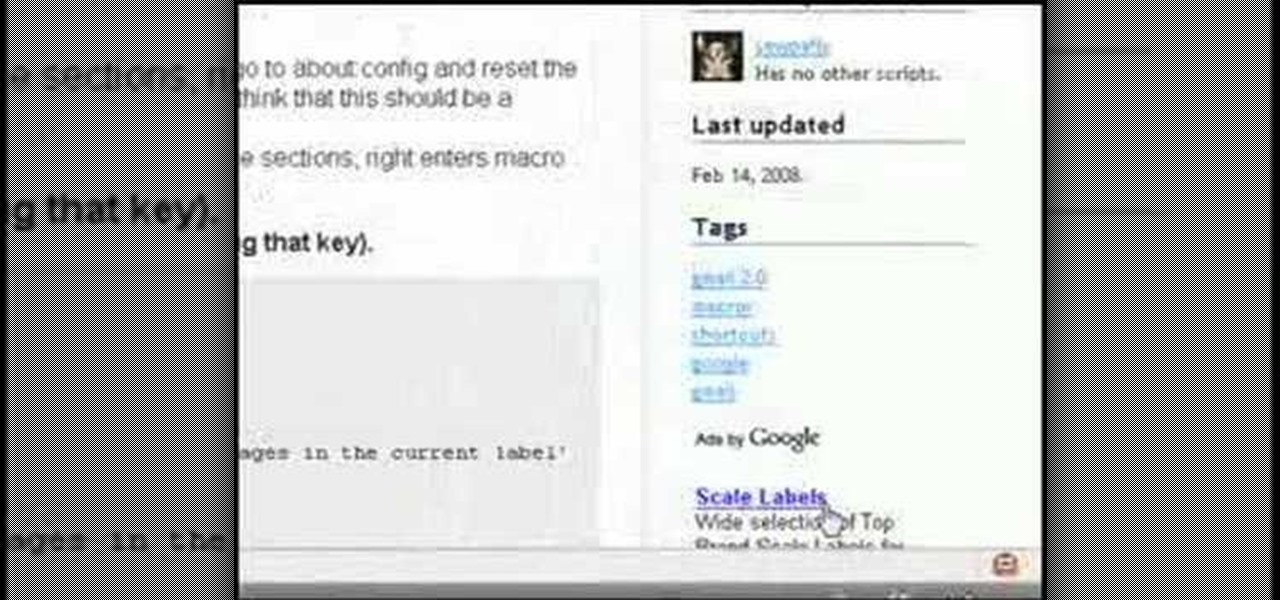
Greasemonkey is a Firefox add-on which works as a script manager for the collection of scripts available on the userscripts.org website. It can be used to manipulate the view and functionality of websites which has a user script. Greasemonkey only works in Firefox and not on any other web browser.
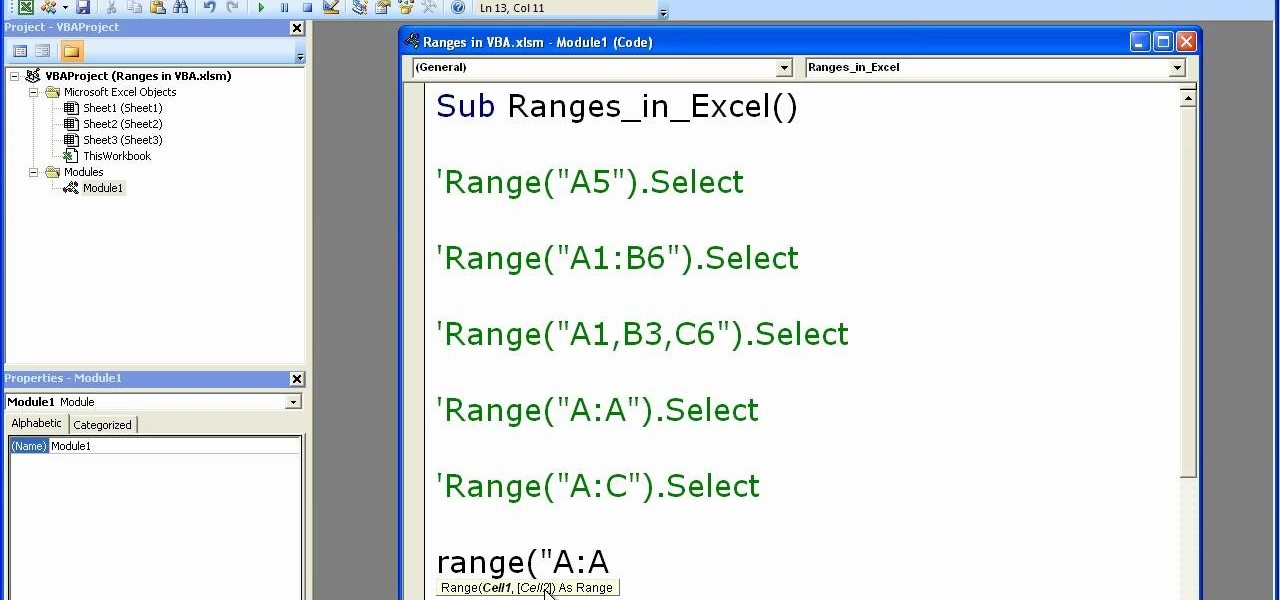
Microsoft excel is a powerful tool used to work with numbers and data by filling them down in rows and columns of a table. Excels also supports macros, which are small scripts to automate certain functions. In Microsoft Excel you can select entire rows and columns using the range property. You can also use macros to select individual rows and columns as well as multiple variations of rows, columns, and individual cells all at once. In Excel a horizontal line of data is called as row and a ver...
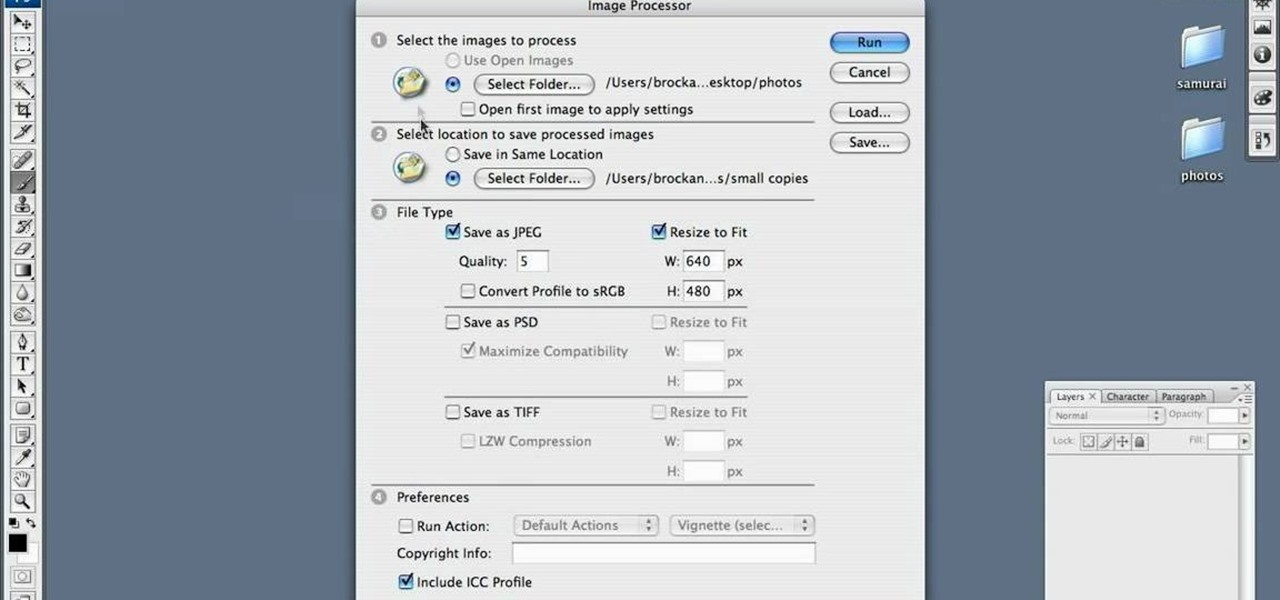
Are your high resolution photos taking too much space on your hard drive? Tired of getting file too large error when emailing photos? Don't worry Photoshop Samurai will help you batch resize your photos as fast as a ninja! You will need: Photoshop (Not Elements version), photos that need to be resized Go to file, then scripts and select image processor. Select the source folder (where your pictures are stored on your computer). Then select a destination location (where you would like the proc...

In this flash tutorial the instructor shows how to create a custom cursor. This is created using shapes and simple Action Scripts. First open the flash tool and create a simple shape. Then convert the shape in to a movie clip and add simple animation to it where it switches colors. Now create a new layer and add Action Script code as shown in the video. This Action Script code is a command to make the shape follow the cursor. Now the shape follows the cursor as the cursor moves and appears as...

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.
In this tutorial, Mike Lively of Northern Kentucky University gets you started in getting the Adobe Air Content Management System up and going.

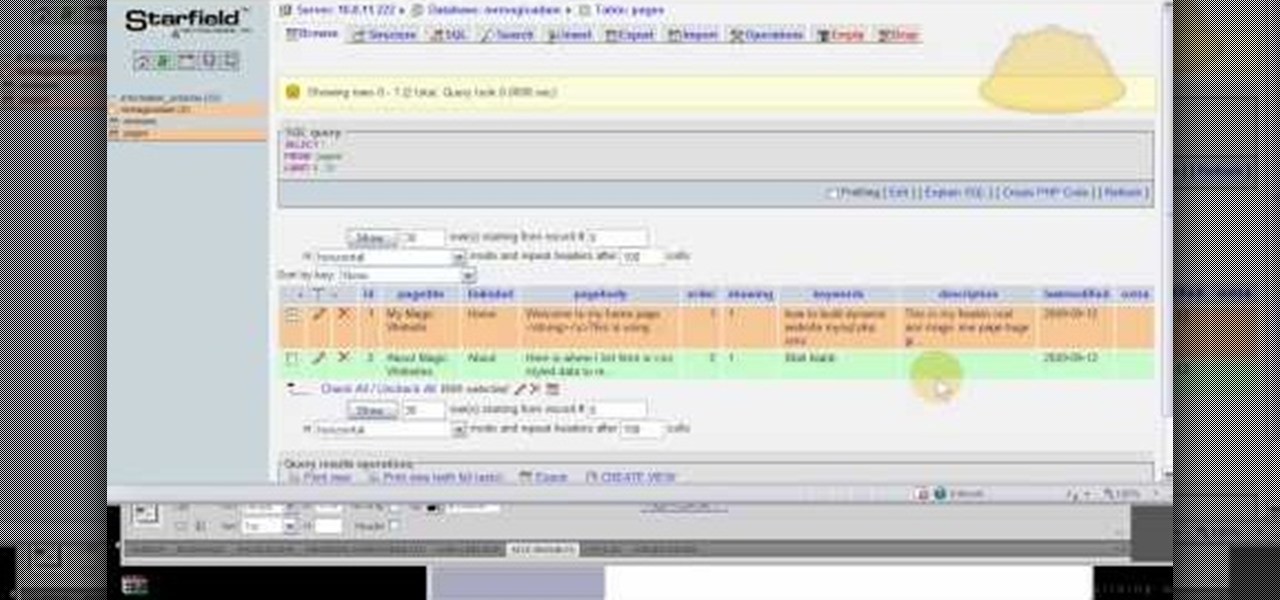
PHPMyAdmin is a tool for website creators who may not yet be comfortable writing custom database scripts using straight PHP. This tutorial shows you how you might use PHPMyAdmin for your own website and display all the information contained on your website in just one file.

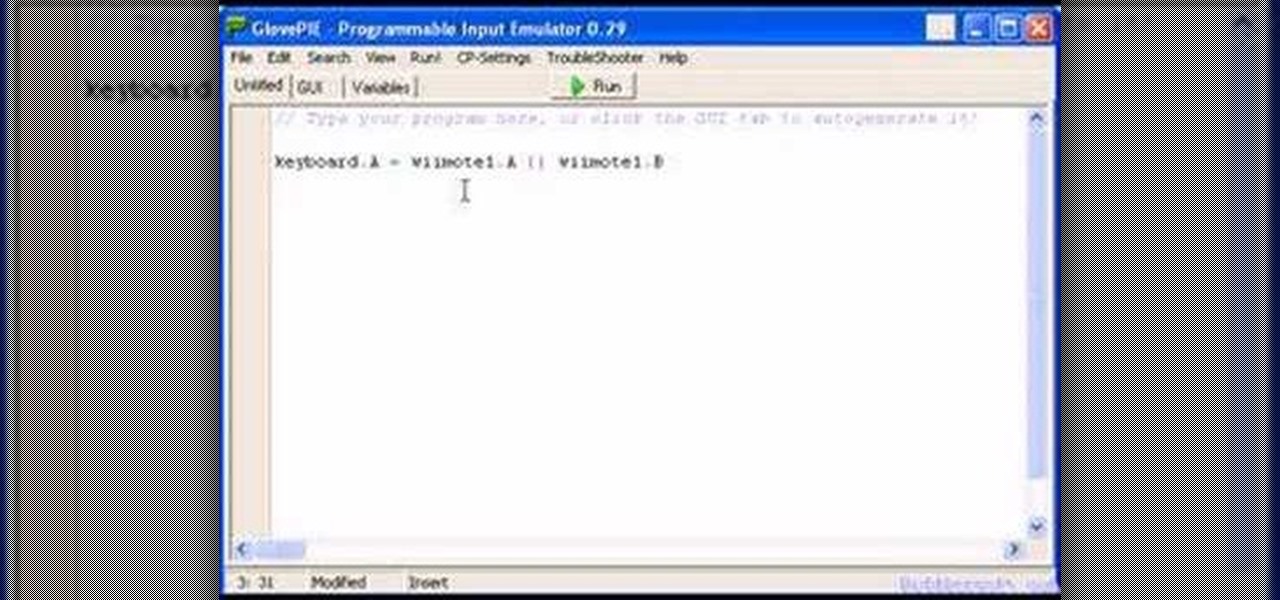
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to create scripts in GlovePie to program your PC to respond to simultaneous button presses and button combinations from a Wiimote.

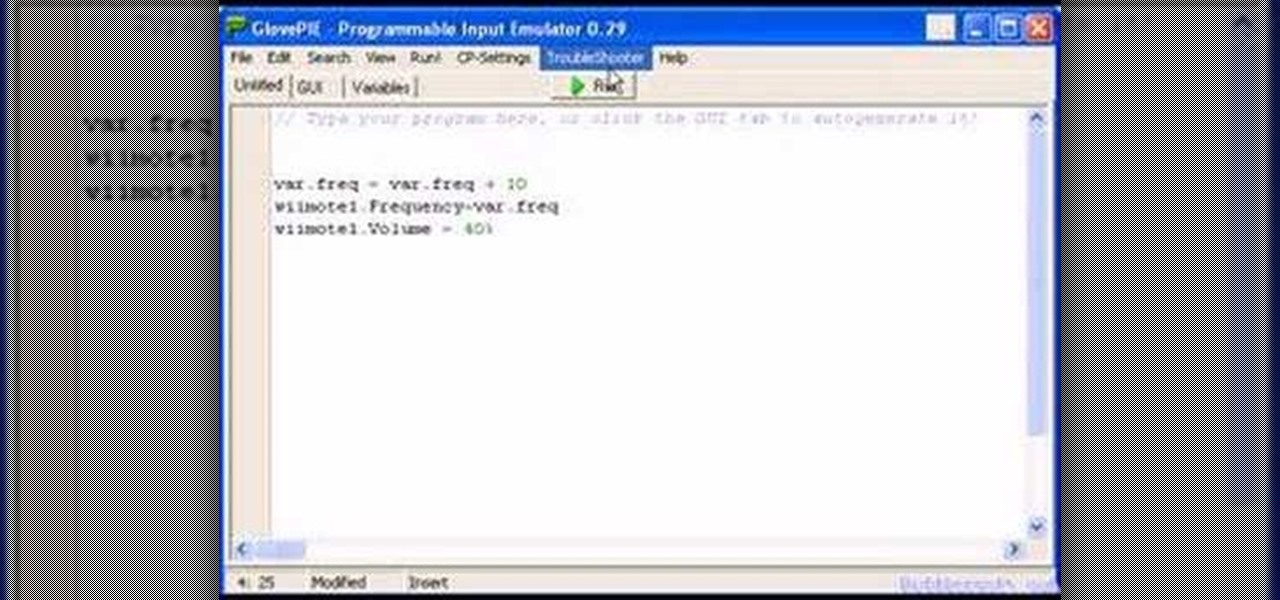
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how you can program GlovePie scripts that will emit sounds from the Wiimote's built in speaker.

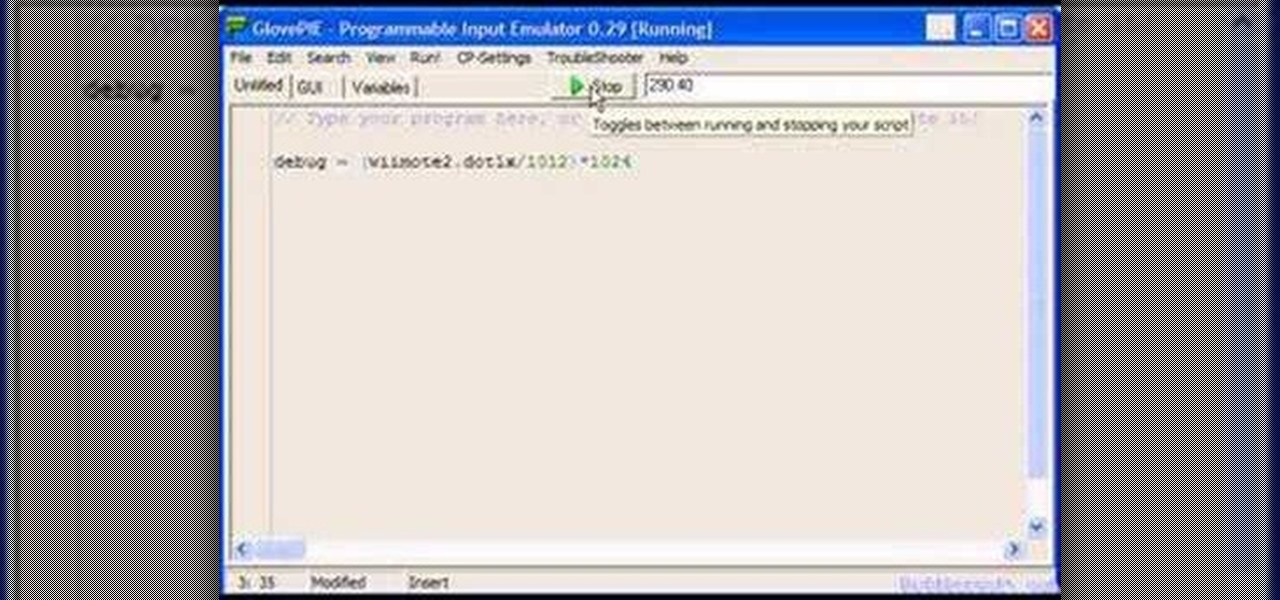
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. See how to program scripts in Glovepie to use the infra-red sensor on the Wiimote to move the mouse cursor.

Learn how to install PHP and some of the basics of PHP programming including some basic commands including conditionals and booleans for creating scripts and command line interfaces.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

In this tutorial, we learn how to create interactive shortcuts in Gmail:Greasemonkey. Start off by searching for "Greasemonkey", then click on the very first result. Click to install this, then once you have it you need to restart Firefox. Now, on the bottom of the screen you will see a little monkey icon. After this, type in "Greasemonkey scripts" into Google, then search for "modified Gmail macros" and install this. After this is installed correctly, go to your Gmail account. First, type in...

To remove the DRM from a Kindle, you will need the following: Kindle for PC software program and Python scripting program.

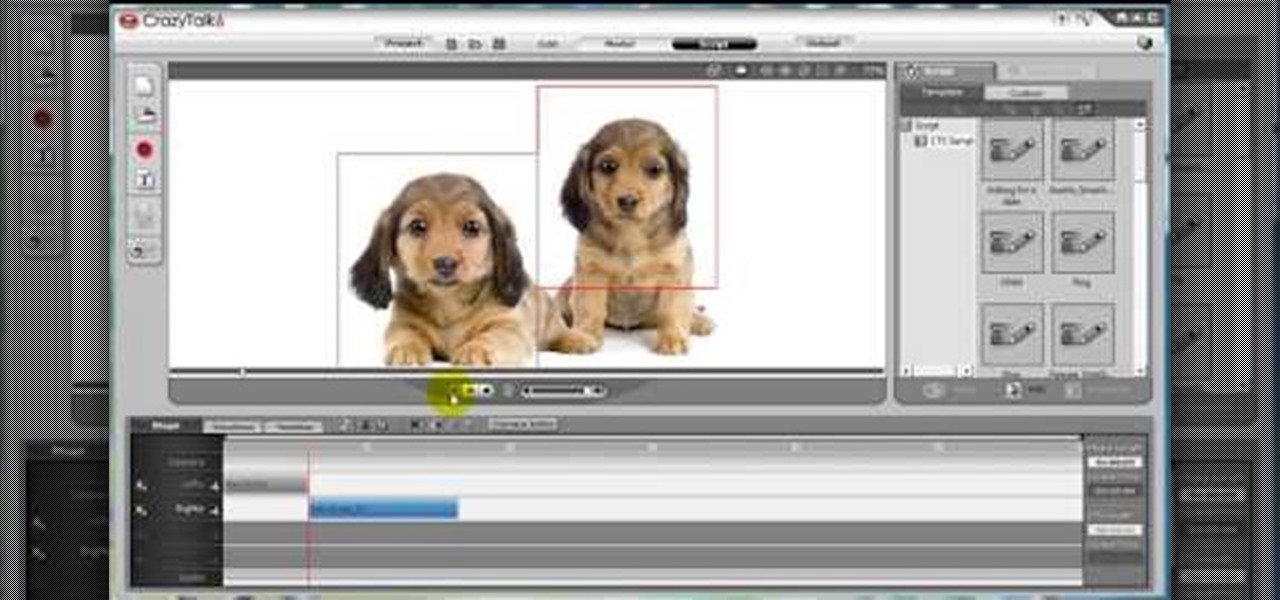
In this video, we learn how to make an animated dialogue in CrazyTalk6. Once you are in CrazyTalk6, face fit your character then click on "script". You can re-name your characters as you wish. Once you have their names picked out, you can create a script for them. Press the red record button and record what you want the character to say and press "load". Then, choose what you want the facial features to look like. Load another script for the other animal and once you press play, you can see b...

http://mange03.mybrute.com Here Link To Download Grease Monkey: https://addons.mozilla.org/en-US/firefox/addon/748

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

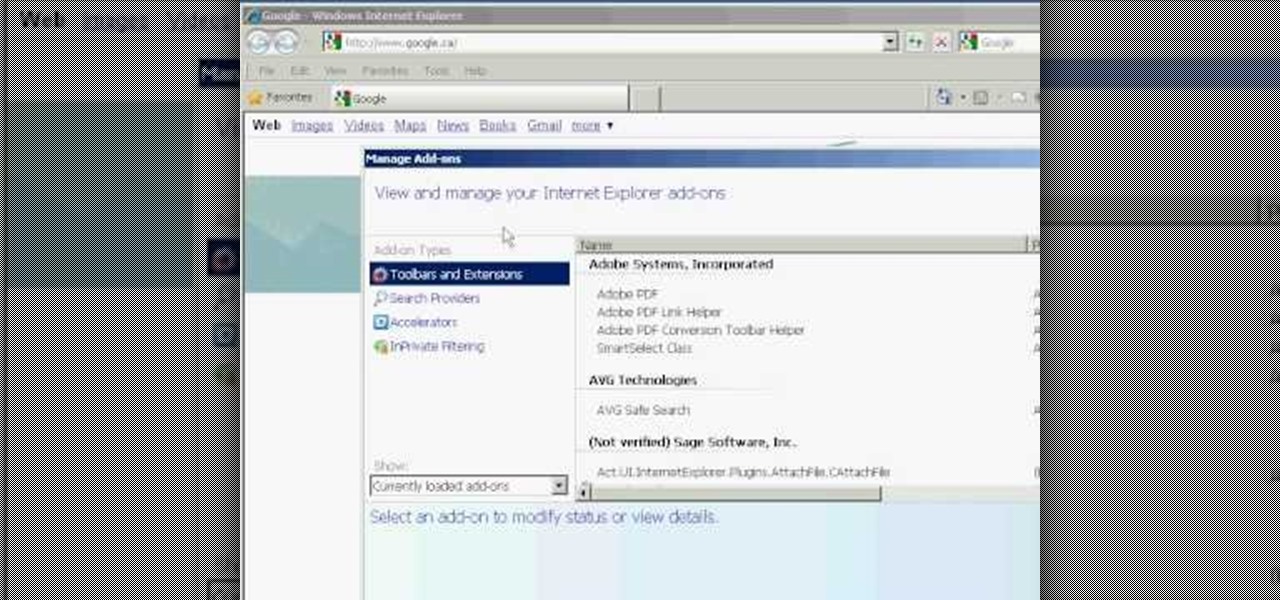
Whethamsolution’s Quick tip walks us through some of the issues caused by use of add-ons in Internet explorer 8 web browser. The video also shows how to manage the add-ons installed in IE8. Add-ons are software’s which enhance the functionality of a web browser. Though most add-ons enhance the browser functionality to a great extent they often tend to slow down the browser drastically. Moreover unwanted add-ons like toolbar's and malicious scripts may cause nuisance to browsing experience...

Whether you use shadow puppets or marionettes, put on a fanciful puppet show with these tips. Step 1: Decide on script

In this video series, our expert John Carstarphen will show you how to create boolean scripts, create the first light, streetlights, mood, and depth. He will also show you how to edit colors, do a graduated background, add illumination, and how to use volumetric light and shadows.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

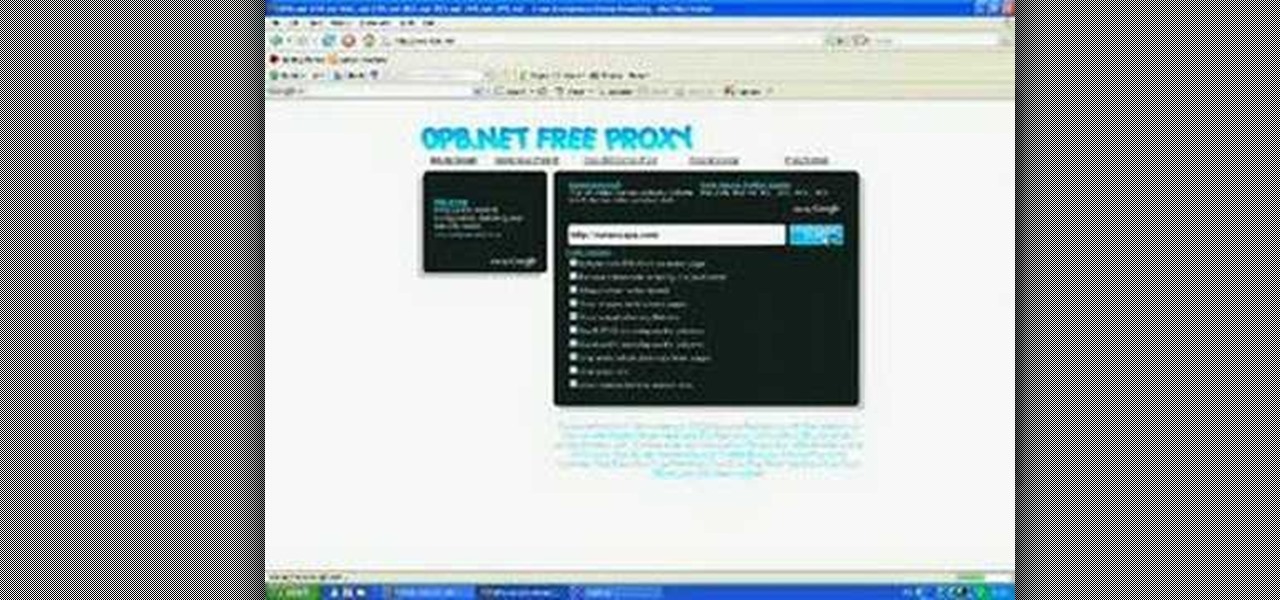
This video tutorial belongs to the Computers & Programming category which is going to show you how to view blocked sites with a free proxy website. Open up a browser and go to a free proxy such as SneakyRascal or opb.net. Type in your website, say for example http://runescape.com/ and click on 'surf' or 'go'. If the website has flash, go to options and make sure 'remove side scripts' isn't ticked or 'activate side scripts' is ticked. And you are on the blocked site. But, be aware! The proxy s...

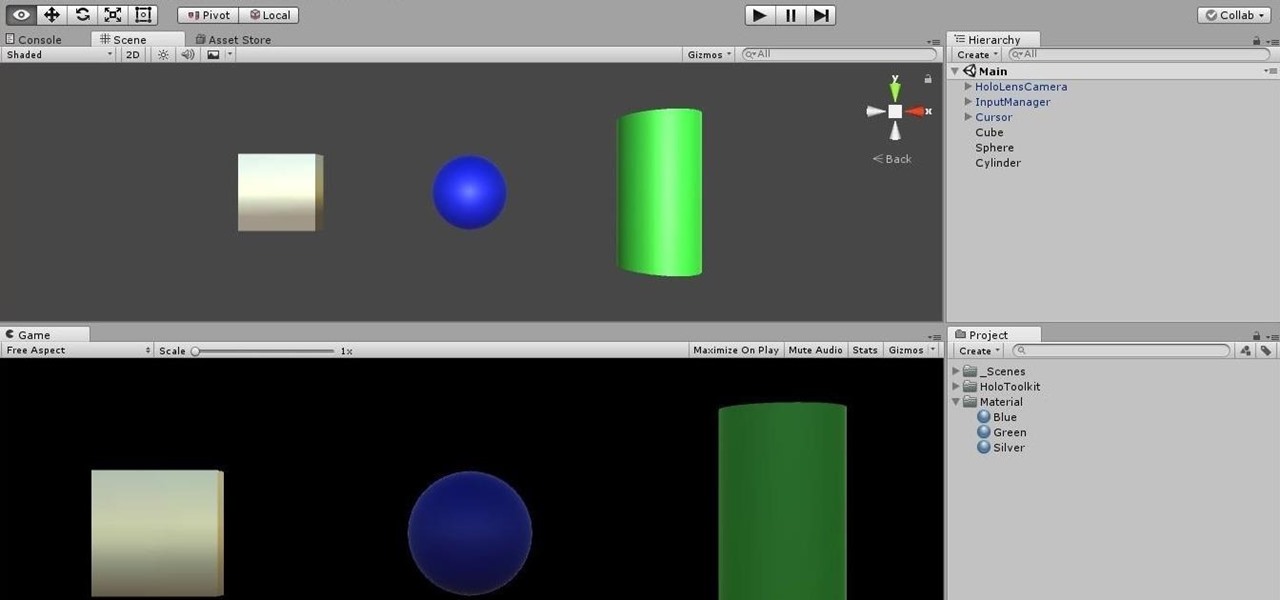
Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

The Bridge has great integration with the other CS2 apps. One of the ways the Bridge integrates is via Bridge scripts. In this video you will see how to use Keywords in the Bridge to easily find your images as well as how to create an InDesign Contact Sheet.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

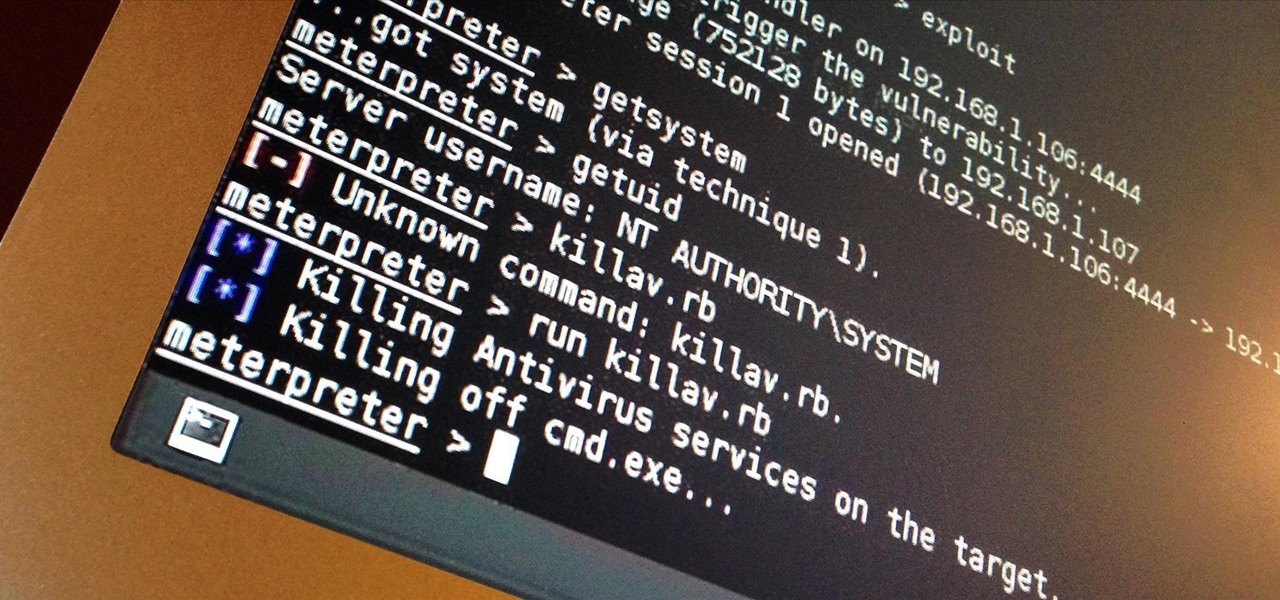
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.