
How To: Adopt a child
The adoption process can be long and taxing. Start off right by learning the basic procedure. Step 1: Learn the requirements


The adoption process can be long and taxing. Start off right by learning the basic procedure. Step 1: Learn the requirements

Do it yourself closet organization can be quite a journey, even with the best advice. Meghan Carter discovered first-hand the trials and tribulations of closet organization as she put herself under the scrutiny of professional organizer Cynthia Ivie. But in the end, Meghan not only organized her closet, but found a great excuse to go shopping.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.
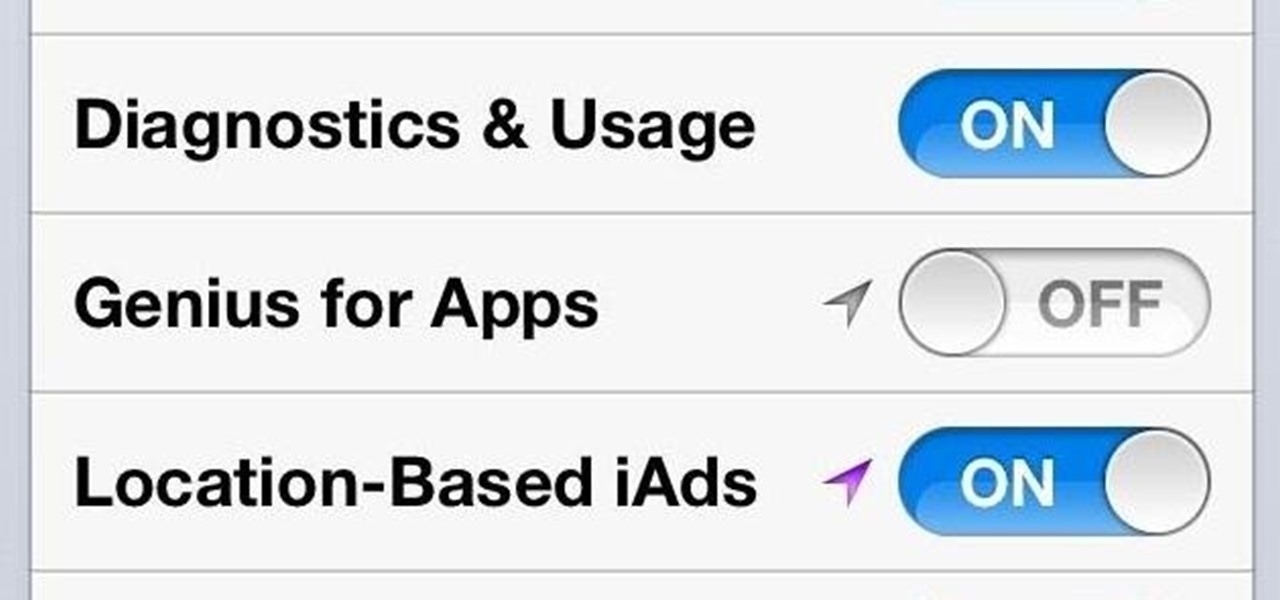
As if iOS 6 wasn't under enough scrutiny, a new issue has surfaced regarding the App Store for iOS 6 on the iPhone and iPad. According to users, the application store is very sluggish and doesn't load properly. Below is a video of just how slow the application store is.
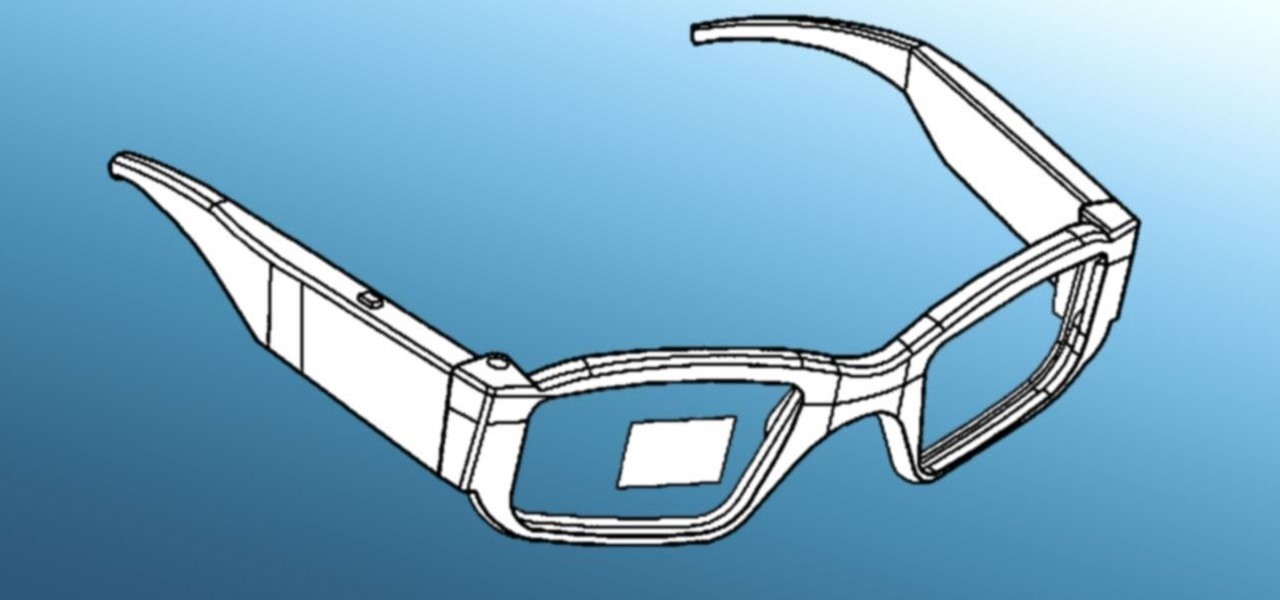
Historically, patents have never been a rock-solid source for uncovering the future of a company's product pipeline. However, sometimes, the images you find in the patent application search archives are so convincing you have to pay attention.

Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.

How many times have you heard someone utter the phrase, "Now, let's break into groups"? From classroom discussions to workplace think tanks, gathering into groups to generate ideas is common practice. These forced get-togethers are intended to encourage creativity and unique thought, but they can actually do the opposite. More often than not, group brainstorming is annoying rather than encouraging, and these group sessions can actually be detrimental to your productivity. Getting together har...
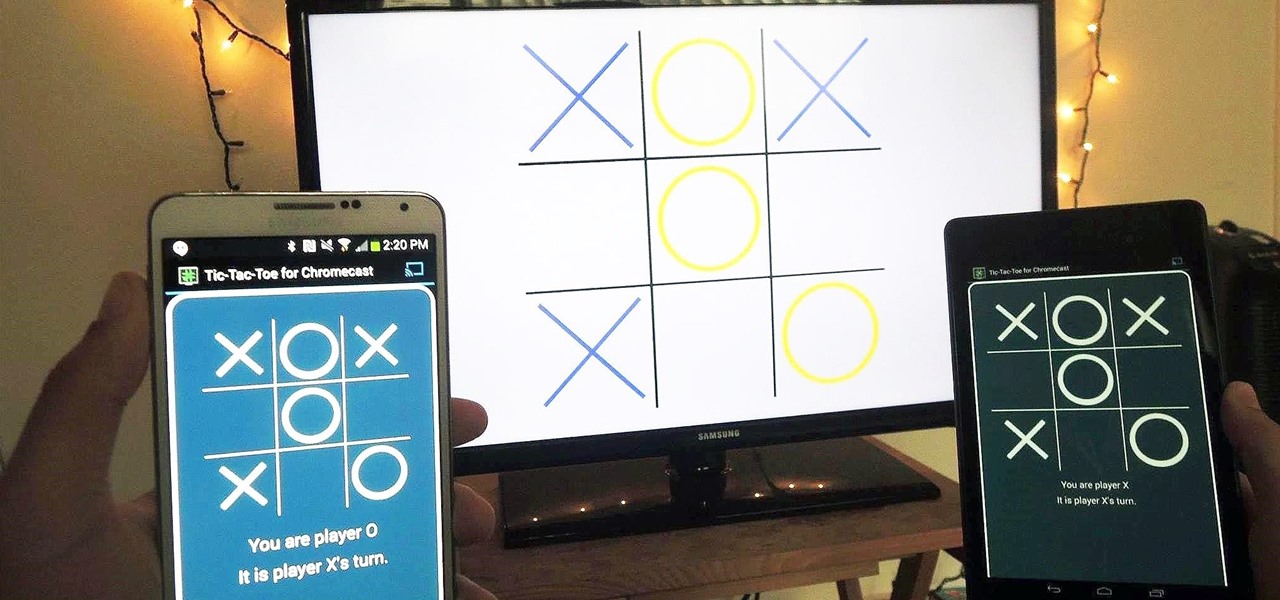
With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Some women see Halloween as a once-a-year opportunity to dress in something skimpy without dealing with as much scrutiny as usual. That can be fun, but not everyone is comfortable enough wearing so little, and the costumes are so boring and repetitive. Some of us just don't feel like freezing.

The fight to wrest control of apps from Apple's revenue-focused grip just took a major turn in favor of Epic Games.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

As we move toward the end of the year, the wheels of the augmented reality space continue to shift in major ways.

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Do you wanna be that person who stands out in a crowd? Our society dictates our fashion sense. We believe we all must look like who ever is the "most popular" in the media (TV, film, magazines etc.). Our choice to express our self is very limited because of the stigma of what patterns, styles and colors belong to which gender. I have found by adding just a hint of feminine flair to my person that I am able to catch peoples eye's faster than a supermodel walking onto a runway.
Just in the nick of time. The TSA has come under a lot of scrutiny lately as outrage grows around the country over goons in gloves touching the junk of everybody from toddlers to grandmas. Then there was a suspicious if not improbable al-Qaeda underwear bomber threat to get things back on track. Now we have a French woman with a “surgically implanted device” on transatlantic flight.

In the wealthy oil man's world of Arabian camel racing, the tradition of using child jockeys has been replaced with the use of small robo-jockeys in recent years. But after finally ridding the game of the mistreatment of children, the sport is now under scrutiny again. The Dubai police have discovered a new feature illegally added to the torturous, whip-endowed robots: hidden stun guns.

Children under the age of 13 possess insight that can blow the minds of their elders, but not the wherewithal to make important life choices for themselves. This is exactly why there are strict rules against marketing cigarettes to them. In 2000, a law went into effect called the Children's Online Privacy Protection Act that institutes similar consumer protections for our youth's online identities, prohibiting companies from soliciting personal information from children under 13 years of age ...