If you're all out of prank ideas for April Fool's Day, we've got a few that your Apple-loving friends will enjoy (or hate?). You can have a little bit of fun if you don't have access to their iOS device or Mac, but for the best pranks, you will need access to their devices, even if it's just for a few seconds.
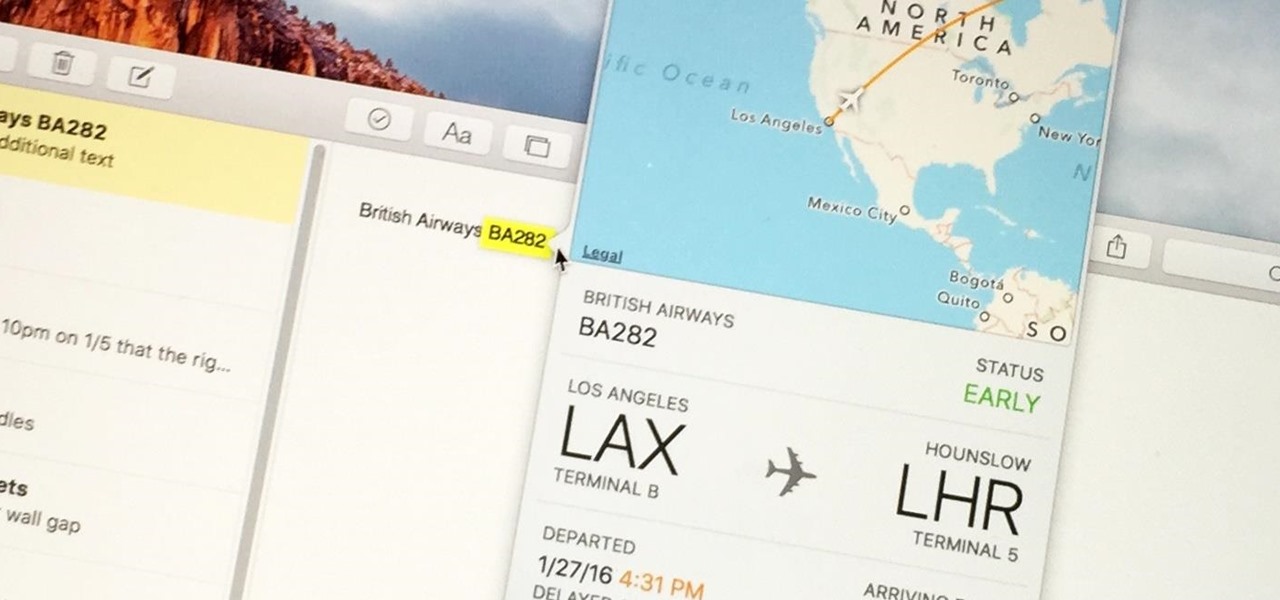
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

Google Maps, in conjunction with the Android operating system, is a powerful tool for navigation that is often underutilized. While it's no secret that it can get you to wherever you're going and back, some of you might not know that you can use Google Maps without even having to touch the screen. Not having to touch your display means you can concentrate on other things, you know, like driving or eating that jelly-filled donut.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

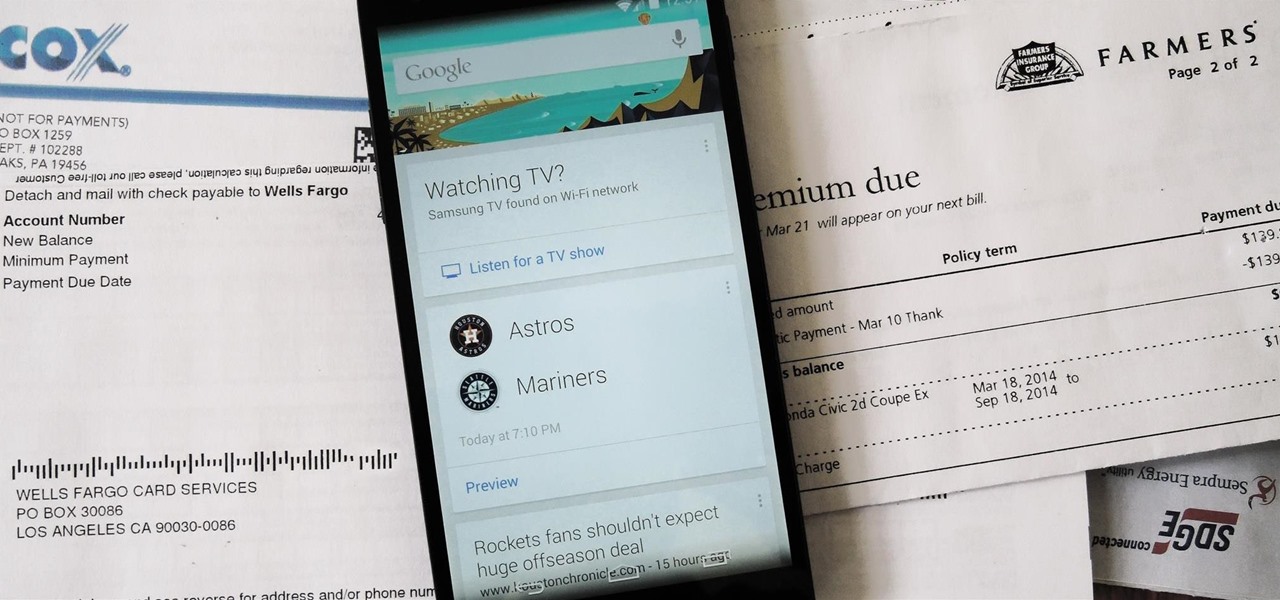
One of the biggest new features in the soon-to-be-released Android 6.0 Marshmallow is something Google is calling "Now on Tap." Essentially, this service will be able to scan the contents of any screen on your Android device, then after you long-press the home button, it will provide you with relevant information about anything—from movie times to directions or dinner reservations.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

hello my dear colleagues, I made a visit to nullbyte and found that there is not a complete tutorial about the google dorks, so I felt the need for this tutorial, and seeing that there are many newbies around, so here's a tutorial that will teach you how to use google to hack.

Apple's latest mobile operating system, iOS 9, may not be the huge overhaul that iOS 8 was, but that doesn't mean there aren't plenty of new features. In fact, there are a ton of subtle changes that you may not notice right away. Here's a rundown of all the coolest new features you need to know about on the new iOS 9 for iPad, iPhone, and iPod touch.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

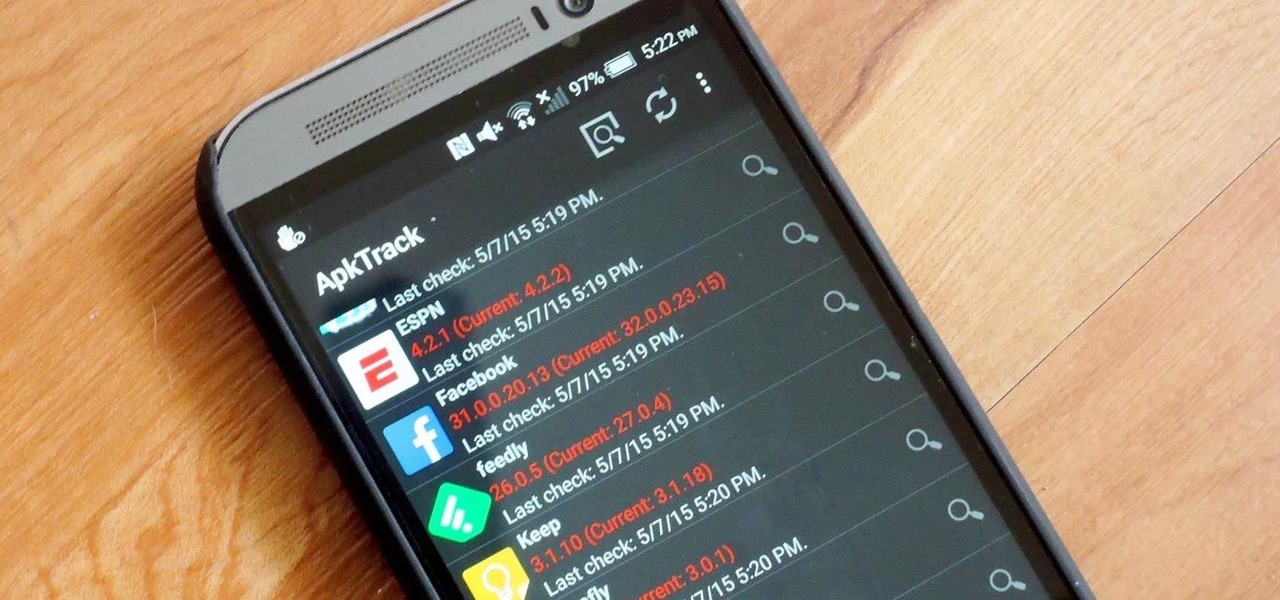
The Google Play Store may have fewer restrictions that its iOS counterpart, but that doesn't mean that all apps make the cut. Ad blockers and Xposed modules that bypass paywalls have never had a place on the Google Play Store, which makes tracking their app-updates a painful process.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

With the release of the Nexus 5 back in 2013 came the Google Now Launcher, which has become the go-to choice for many Android users, especially those who prefer the Nexus line. With its integration of the Google Now page and the always-listening hotword detection, you'd be hard-pressed to find a more complete and useful launcher.

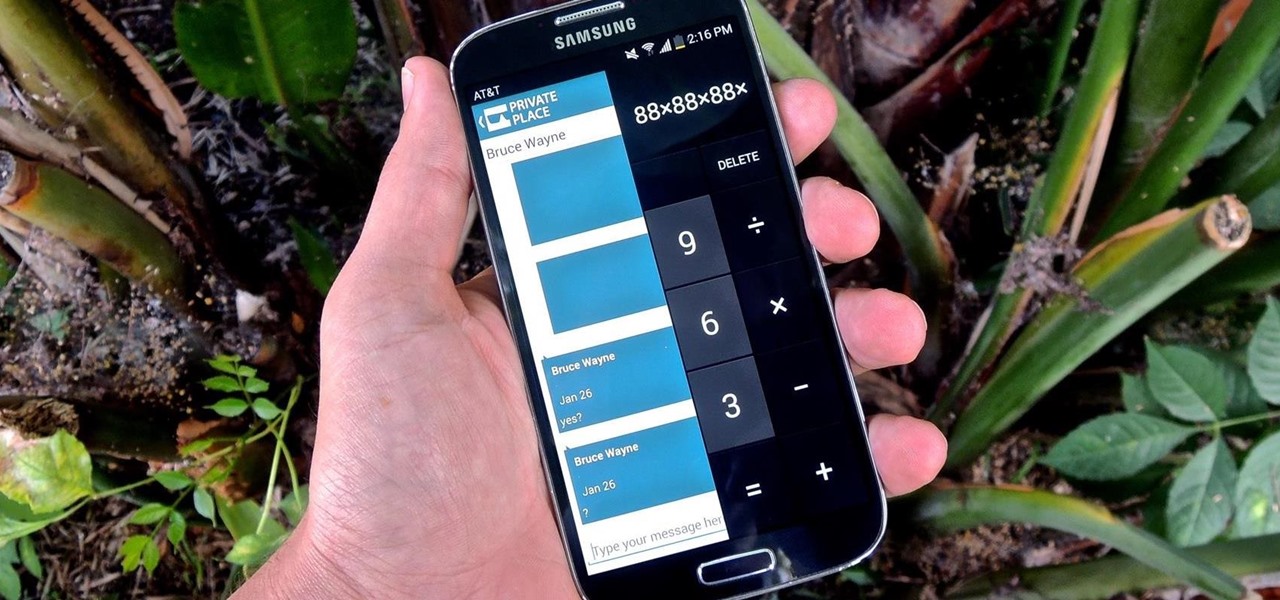
Whether you're a secret spy or just a regular person with a few secrets, you may want to keep certain information on your smartphone private, and it's totally possible on Android to do so.

Those of us with girlfriends understand that in order for the relationship to run smoothly, you have to keep your woman happy and let her know that you're thinking of her—even when you're not.

Apple scrubbed the floor clean of all existing text-bombing apps in the iOS App Store, and even though there were once a ton of these apps in Cydia, the go-to store for jailbroken devices, there few and far between these days. If they do exist, they either cost money or don't work as advertised.

Ever wanted to communicate with another driver on the road, but just didn't know how? Sure, you could flag them down by waving or honking at them, but that assumes that they're in close proximity, that you have a unobscured path, and that they're paying attention. And if you're in a fit of road rage, flagging them down probably isn't the best idea for either of you.

Now that Apple has added support for third-party keyboards in iOS 8, the ways we can communicate with our "peeps" has expanded beyond emojis and standard text messages to GIFs and even rap lyrics now. RapKey takes some of the best and most popular rap lyrics, then lets you choose and send them straight from their easy-to-use keyboard.

This video will show you how to block or unblock someone from calling and sending your messages in your iPhone or iPad. So please watch the video and follow all the steps carefully. Employ the technique in your iPhone or iPad.

The San Diego Film Community and the families of Down Syndrome individuals band together to make this great feel good PSA with a positive message.

It's been a long-rumored feature, but today, VoIP calling has finally started rolling out to users of Google's Hangouts service. Essentially integrating Google Voice into the popular messaging platform, Google has given Android (as well as iOS) users an easy way to make calls without eating up their plan's minutes.

Only scumbags hide their call and message history, right? Wrong. While it may seem like a tactic for the unfaithful, it's still a good thing to do for certain contacts on your phone that you don't want to block outright.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Texting just got a whole lot better for your iPhone. In iOS 8, you can send an in-the-moment picture or video without exiting the conversation you're in, and you can also send voice messages! Plus, they'll self-destruct, similar to Snapchat.

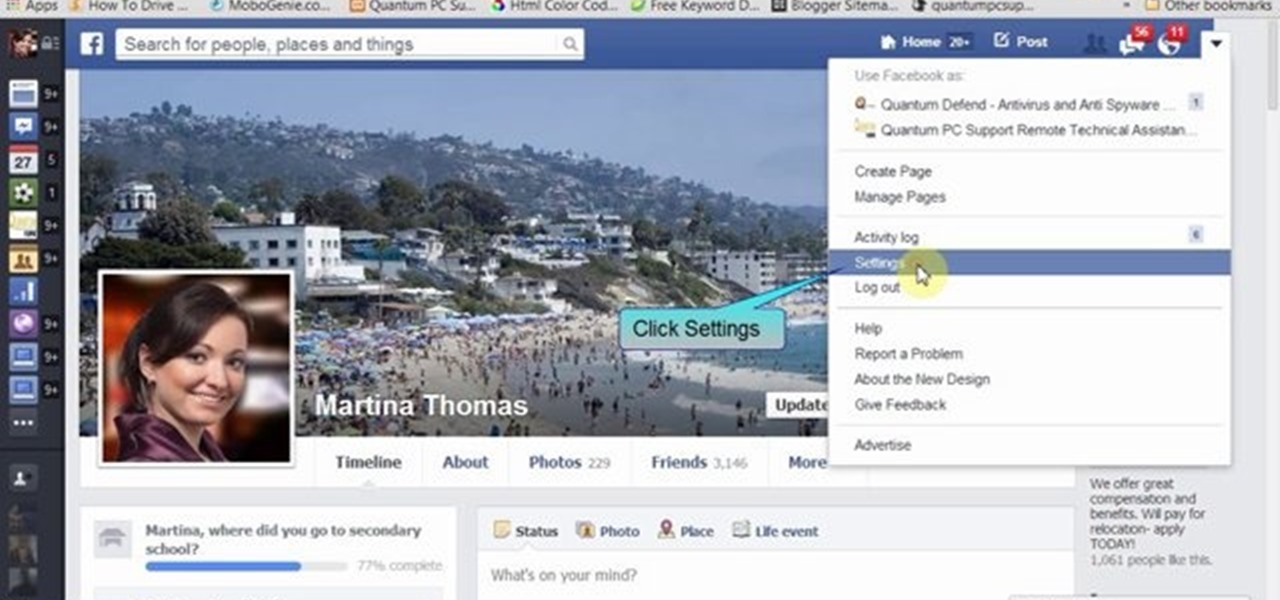
Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

Accessing your recent contacts just became a hell of a lot quicker with iOS 8. In addition to accessing recent apps, double-pressing your Home button now shows off recent contacts at the top of your screen.

Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

If you are not interested about the huge amount of messages contain app and playing game invitation in Facebook, then you could stop those messages from coming to your end. This video shows how to block friends from sending apps and game requests o

A while back, Facebook released a killer feature called "Chat Heads" to its Facebook Messenger app. Messages from users would "pop up" in small bubbles that floated on the screen that could be seen, accessed, and moved around from within most apps.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

You want to find a message that you've sent two years ago, but scrolling is taking too long? I have a solution for this! :)

Spam emails are emails that are sent to you without your permission. They can quickly fill up your email account if you don't do anything about it. Each email server deals with spam in a different way. Gmail is good at separating the spam for you so that you can get rid of it more quickly. It is easy to delete the spam and if you want to take it a little farther, you can get some of the spam to stop coming all together.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

We've all been there. Your phone is on your nightstand, but you're on the couch in the living room browsing the web on your Nexus 7. Then you hear it—a faint sound for a new text message notification from the bedroom.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Trying to get rid of an ex or clingy friend? Just want to keep telemarketers from calling you all the time? You can use the iPhone app iBlacklist (for jailbroken iPhones) to create a list of blocked calls for your iPhone. Blacklisted phone numbers will not be able to send you either phone calls or SMS text messages, so you can continue to use your iPhone in peace. Customize your phone's reaction to blacklisted numbers and adjust the filters for your blacklist, as well.

In this video, we learn how to access Casio G'zOne Brigade QWERTYShortcut. From your idle mode with the flip open, press the middle button. Then, press '9', which is settings and tools. After this, press '7' or scroll down to 'phone settings'. Then, press '2' for shortcuts and then press '3'. After this, go up to text message and select the center key to set. Now, from the main screen you will be able to start composing a message just by selecting any key. This makes it easy to write a text q...

Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...

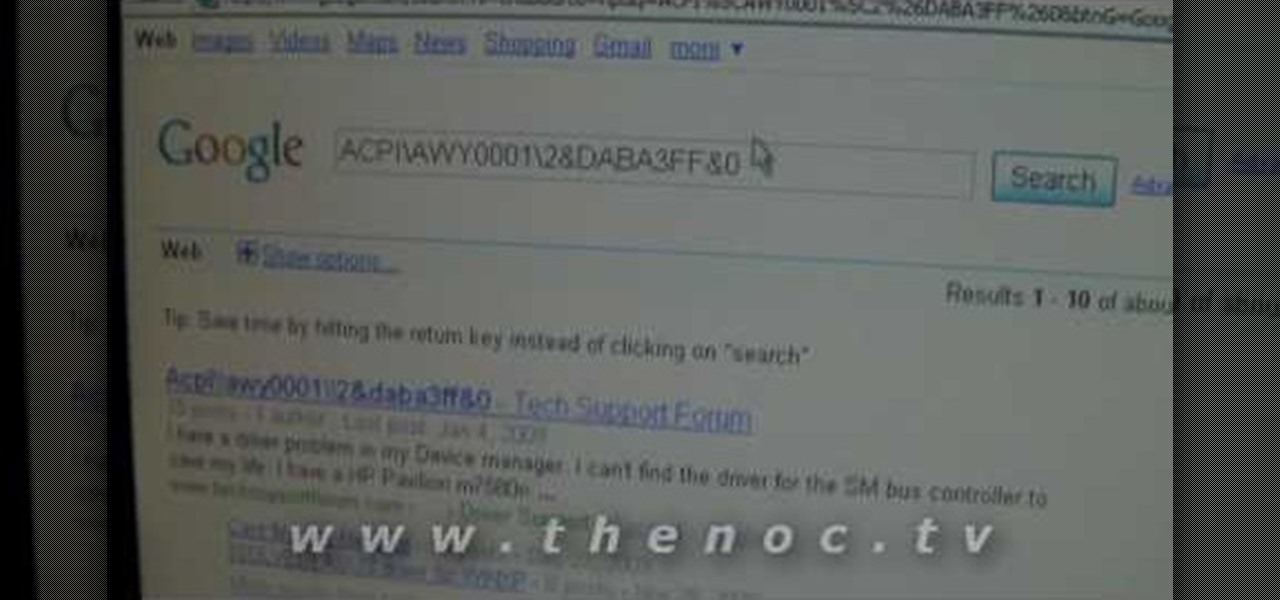
This video narrates and explains how to figure out how to install an unknown device using the device manager. The first step is to access the device manager through the control panel/system. Once in device manager you must select the show devices options. Once the device menu is visible you then find the unknown device section and copy the name of the device driver. The next step is to open Google search engine and paste the unknown device ID name. After the search is complete you will see ma...