Trevor4Ever595 teaches you how to hack mini tower defense using Cheat Engine. Start the game in your internet browser and then pause it. Start Cheat Engine and go to your process list - the little computer icon in the top left corner of the window. Select your browser and then change the value type to 4 bytes. Take the money you have, multiply it by 8 and then add 6. So for 300 you get 2406. Search for that in Cheat Engine. Build a tower and if you have 200 left, you will get 1606. Search for...

In this video from Extreme Bartending we learn how to make a B52 shooter. This is the most popular layered shooter. Start with 1/3 oz of Kahlua, then using a bar spoon, pour very slowly Bailey's. Lastly is Grand Marnier. Use the spoon with this as well. If you're having a party, pour a bunch of them and put the in the fridge for an hour. That works great. This drink is all about the presentation of the layers. This video will teach you how to make a B52 shooter using the proper layering.

This do it yourself centerpiece is brought to you by A-Bnc parties and more. This starts of by making the bow, shown by painting a dowel and letting it dry. Then glue the 'frogs' at the ends of the dowel and glue fishing line to both frogs and trim to fit. Next take a polystyrene cut out of a violin and seal it. This helps paint stick to the surface of the cut out. The violin is painted brown to replicate an actual violin. Using black paint you detail the 'f' holes and allow to dry before pro...

Are you interested in parties and cocktails? Let's make a Jagermonster cocktail. Start with a rock splash and ice it up a little bit. Next, get another glass for an ice mixture, one ounce of Jagermeister, and a little bit of grenadine. Then, add 4 ounces of orange juice. Shake it up well for a good mixture, get rid of the previous ice in the glass, and pour it in. This will provide a variety in your list of cocktails.
When you need a website to showcase your product or service, it can be quite confusing. Follow these easy steps to gather everything you need to have a successful website. Start your search for a domain name in the domain name registrar. (Example: www.companyname.com) Rent space from a hosting company to hold the files for your website. Set up an email account for your company. Create the content for your website (example: products, prices, services, etc). Get internet security to protect sen...

So you want to party with celebrities. Whatever you do, don’t cry. You won’t just look silly—you’ll look unstable. Follow these steps to get you one step closer to hanging with the stars.

There's nothing more tedious, yet exciting, than watching surveillance cameras at work. They prey on the innocent and the unknowing. They protect businesses, workplaces, and homes. They catch criminals in the act, find hilarious anomalies, and are just darn cool when you're not the one that's supposed to be eavesdropping with them.

You Will Need * A fire extinguisher

Kids... it's dance time! Check out this dance video tutorial on how to do the Miley Cyrus Hoedown Throwdown dance. This dance is from the Hannah Montana movie from 2009 where Miley Cyrus performs the Hoedown Throwdown in Tennessee.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the Ubuntu Software Store on Ubuntu Linux.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

The ah sound. The jaw drops more on this sound than it does on any other vowel sound. Ah, ah. And as you can see, the tongue is laying there on the bottom of the mouth. Ah. So, the jaw drops here, make the sound, ah: pretty basic, simple, and straightforward. Ah. Sample words: father, collar, calm. Sample sentence: The party at the bar was a mob scene.

Lab Coat Cooking! Discover how to have fun with cheese. Surprise your friends with this new spin on a classic Caprese Salad. Learn how to make a Mozzarella Balloon. This how to video turns a boring Caprese Salad into a party hit with a little help from some fresh mozzarella cheese, roasted garlic, and a little nitrous oxide. This is a lesson in Molecular Gastronomy.

Bethany's back and she has a pretty amazing tutorial for us this time! Learn how to create X-Men Wolverine inspired eye makeup. This is a pretty awesome interpretation. Nothing's cooler than X-Men, so try out this Wolverine look for a costume party, next Halloween, or just a crazy night out on the town.

They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

Bethany's back and she has a pretty amazing tutorial for us this time! Learn how to create X-Men Storm inspired eye makeup. This is a pretty awesome interpretation. Nothing's cooler than X-Men, so try out this Storm look for a costume party, next Halloween, or just a crazy night out on the town.

The most popular rum drinks liven up any party. Be the life of the party by learning to mix eight rum cocktails in this free drink mixing video series.

Need a new way to impress your friends? Well, when you're out partying, show them how to break a beer bottle with you bare hands. This bar trick is sure to amaze anyone, and it relies simply on air pressure. Just keep in mind that this could be dangerous... glass will fly.

Learn how to hack Google with this amazing video. This video will teach you how to hack Google by using advanced search operators and esoteric search terms to find “hidden” files and mp3s quickly and easily; you'll also learn how to use Google to hack unprotected Internet-controlled devices like webcams and security cameras. For more information on Google hacking, and how to get started using these hacks yourself, take a look at this instructional video!

What's the perfect Christmas drink for this holiday season... a candy cane martini. This festive winter drink is perfect for all of your holiday parties, even if it's Christmas in July that you're celebrating, or even Hanukkah. Watch as Art of the Drink's Anthony Caporale as he teaches you how to make this Candy Cane Christmas Martini.

In this how-to video, you will learn how to find the IP address you are using on your computer without using any third party sites. First, go to the start menu and click run. If you are using Vista, go to search in order to the run the file. Next, you should type in cmd.exe into the prompt. A window should now open up. In this window, type in ipconfig /all. From there, your IP address should be listed. This simple video shows you a very easy way to find your IP address without having to use a...

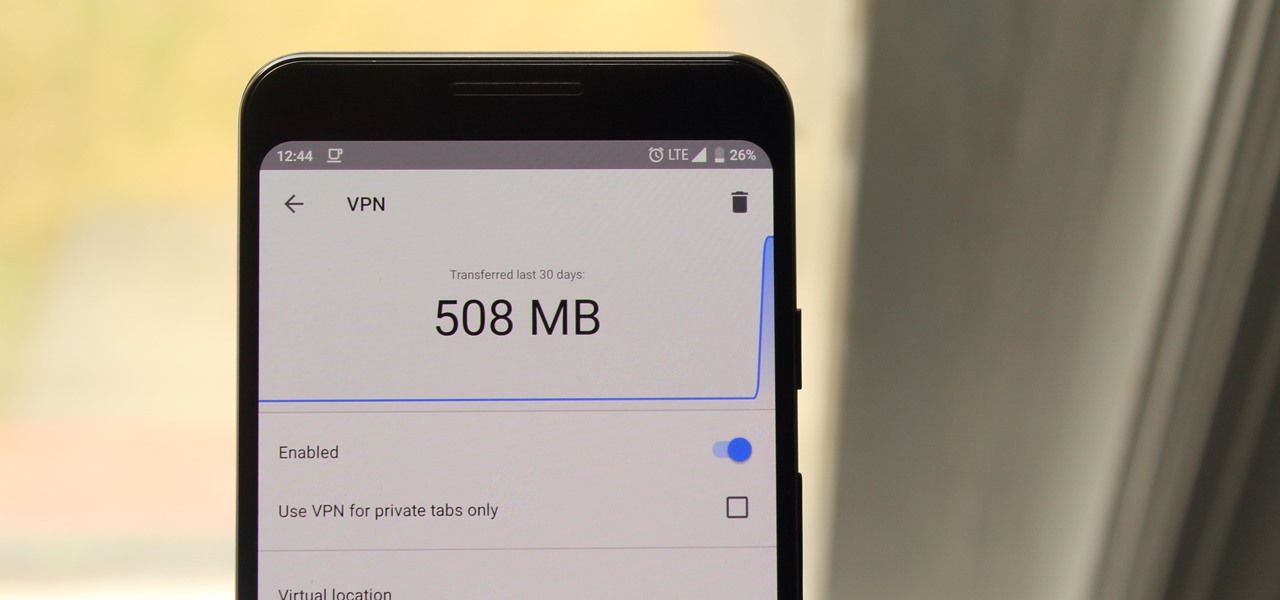
If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

Sure, your search history can be useful, but more often than not, it's a paper trail of privacy infringement. It's perfectly reasonable not to want to see a complete list of your YouTube queries every single time you search for a new video. Luckily, blocking YouTube from saving your search history takes only a few taps.

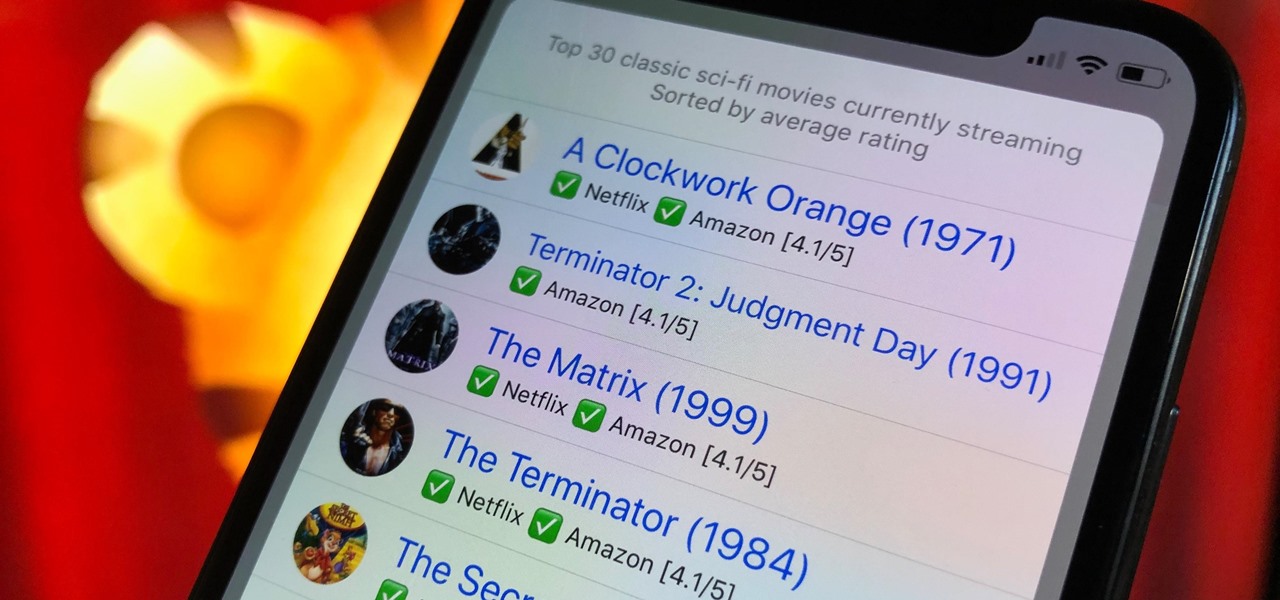
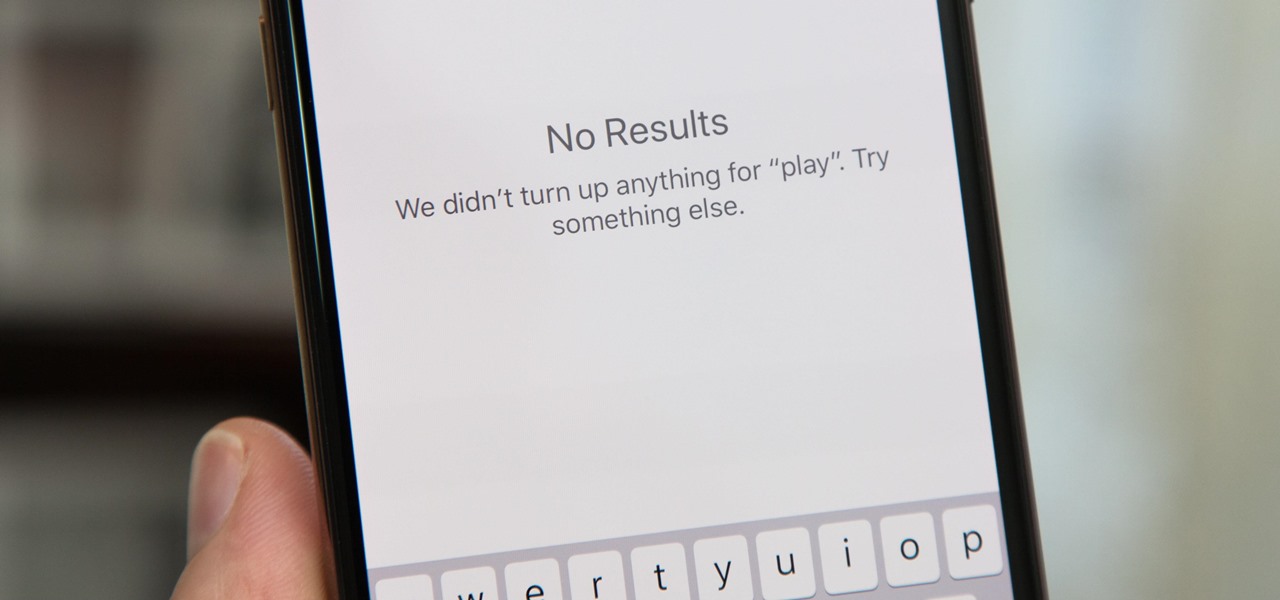
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

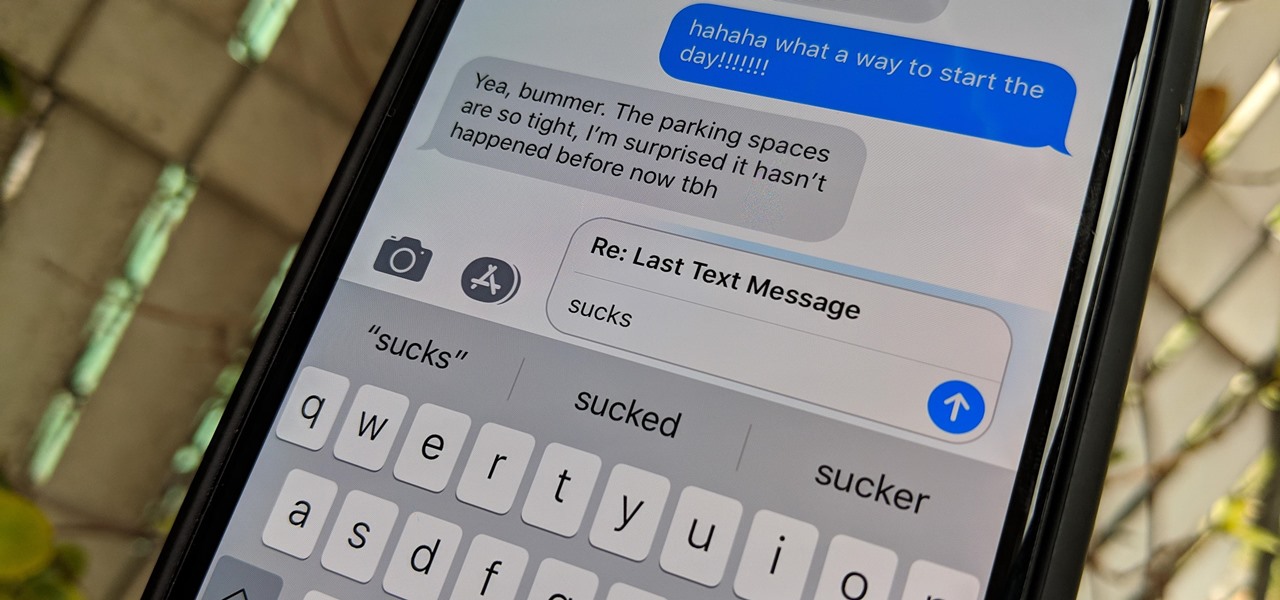
The subject line is a crucial part of an email, but you don't see it very often in texts. That's mostly because many people don't even know it can be done, and even if they do, why would they use it? Just like with emails, subject lines can make iMessages and SMS texts seem more important and more professional. Plus, they can help with organization and searching past messages, as well as make text bold.

Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

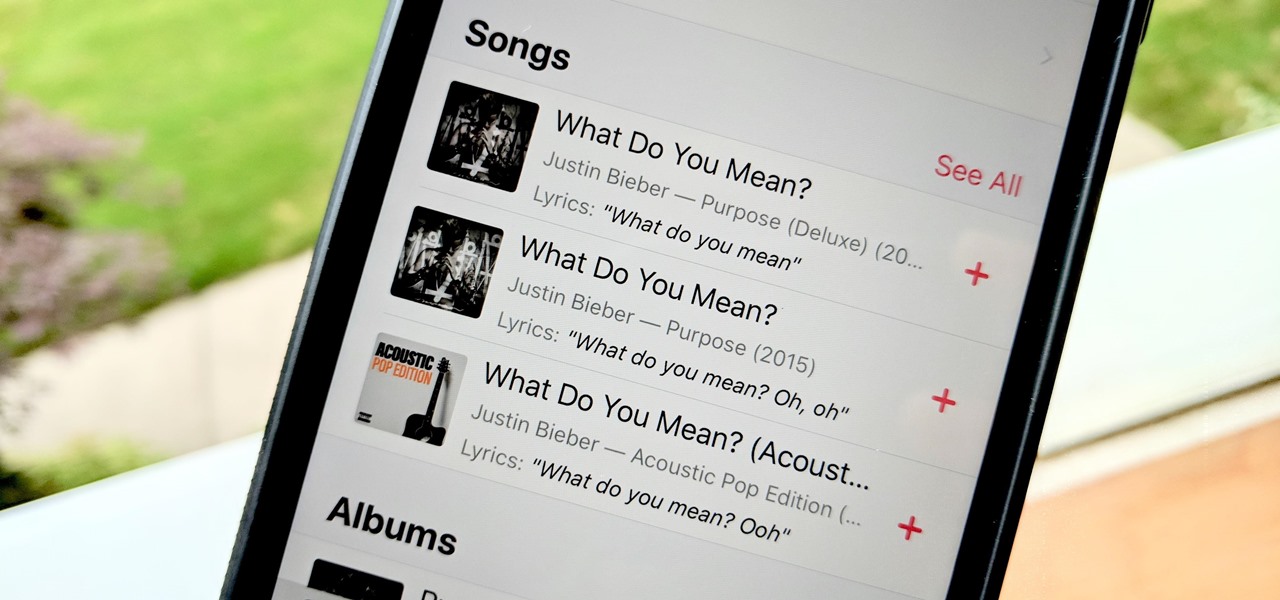
Has this ever happened to you: You're singing a song in your head and want to look it up on Apple Music but you just can't think of its name or even who recorded it? In iOS 12, if you can sing it, you can search for it, as the update lets you find songs in Apple Music by lyrics alone. It's like Shazam, only instead of identifying music by sound, it uses the lyrics in your head.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Google just unveiled it's biggest search product in recent memory, except this time the search giant is looking to take over the world of virtual objects.

The Pixel 2 has finally arrived. Google unveiled their newest flagship phones on October 4th, and there's quite a few changes in store. For one thing, most of Google's official renders have already showed us something new: The Pixel 2 and Pixel 2 XL will have a Google Search bar at the bottom of their home screens.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Most of us don't get the opportunity to see election coverage first hand, but with virtual reality, we're not as restricted. AltspaceVR has teamed up with NBC News to let you log in on your computer or VR headset and actually take part in the action—just not physically.

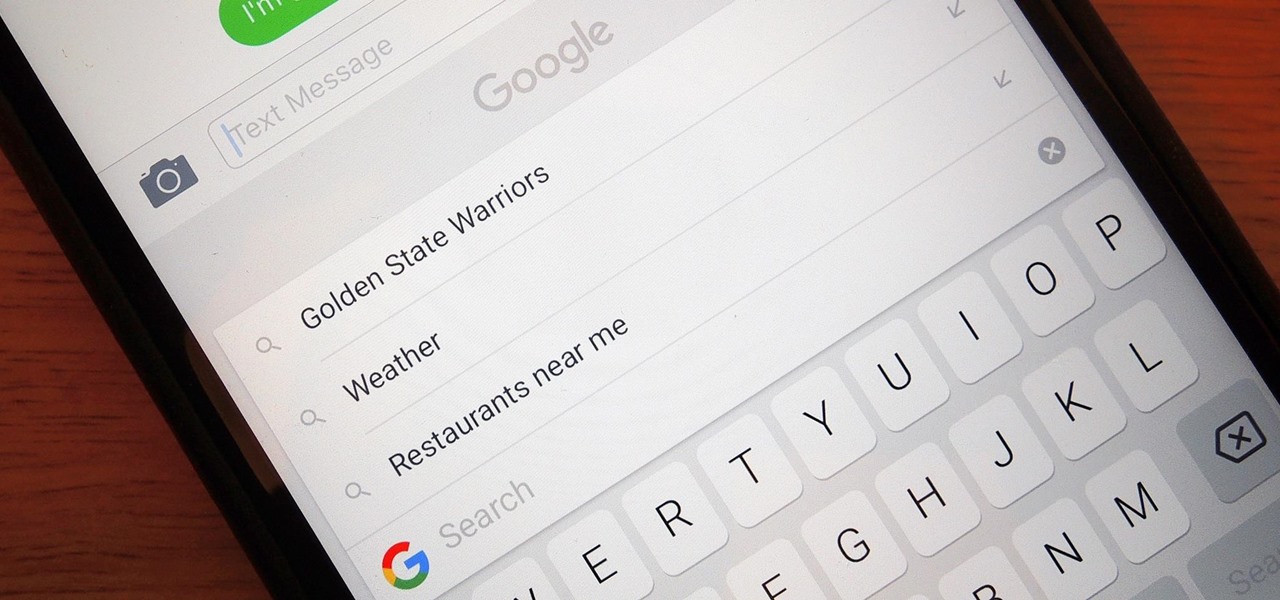
Google just made searching the web on your iPhone a whole lot easier with its new GBoard keyboard for iOS. It has a built-in Google icon so that you can search directly from whatever app you're in, making it a cinch to add images, GIFs, directions, videos, and more.

The big day is nearly here... Super Bowl 50 kicks off this Sunday, February 7, at 3:30 p.m. PST (6:30 p.m. EST). And whether you're having a giant party or watching the game on your big-screen TV by yourself, there's one thing you probably won't be doing: cooking food in your kitchen.

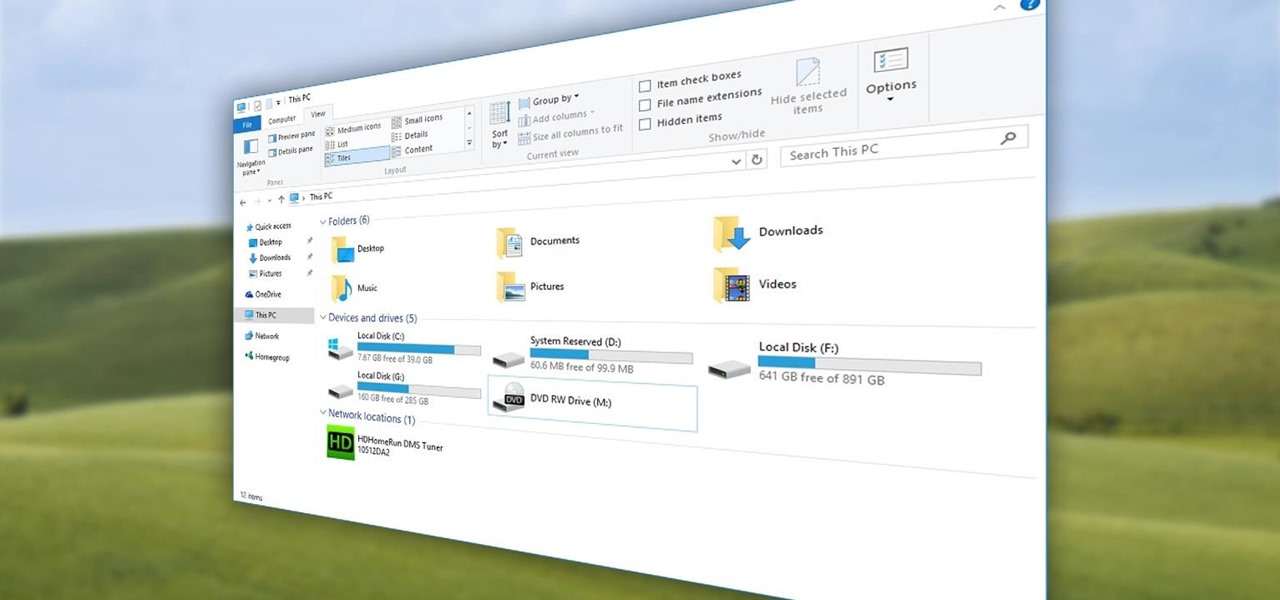
Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

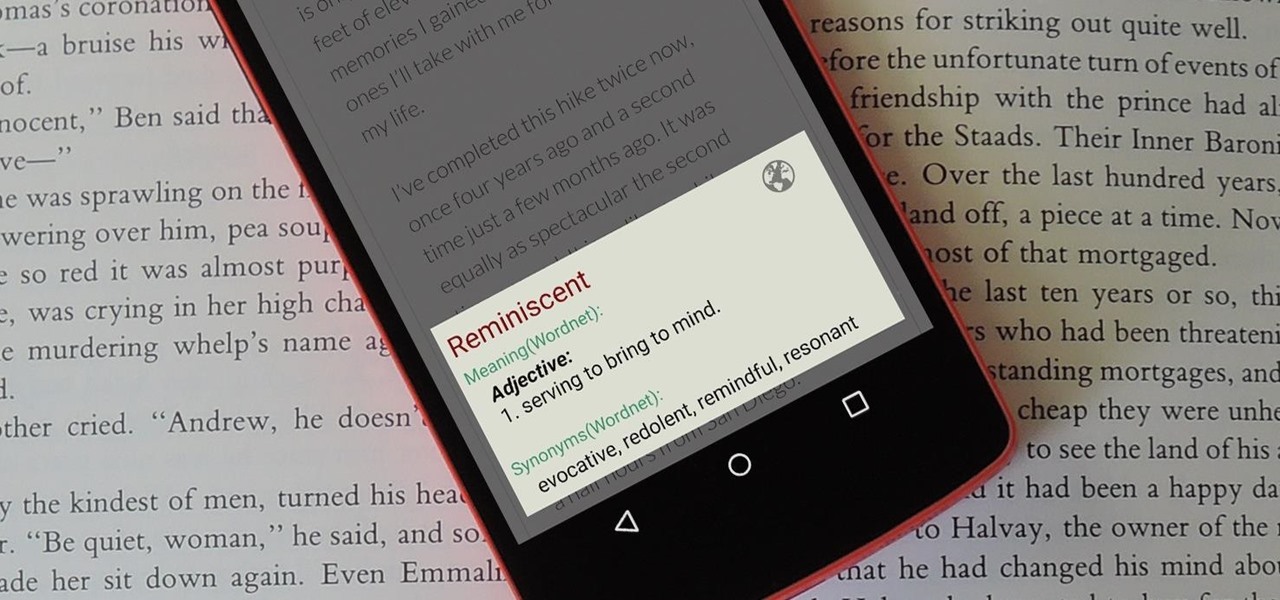
When you're browsing the web, going through emails, or reading a book or magazine, you'll occasionally come across a word or phrase that you haven't seen before. This would be a perfect time to have some sort of built-in dictionary lookup service, but most Android apps lack such a feature.