
How To: Bypass web filters with a web proxy
How to bypass web filter with a web-based proxy server. Bypass web filters with a web proxy.


How to bypass web filter with a web-based proxy server. Bypass web filters with a web proxy.

In this Illustrator CS2 video tutorial you will learn to import and place images into a document. A placed image does not exist within a document; it is linked like a web page image and updates instantly if there are any changes to the original image. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Import and place images in Illustrator CS2.

As it ships, Dreamweaver typically has more built-in behaviors for ASP and Cold Fusion than it does for PHP. Still, developers are quickly writing PHP extensions to make Dreamweaver quite a robust tool for developing PHP/MySQL Web Applications. In this Dreamweaver 9 video tutorial you will learn how to define a site to use PHP pages. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Define...

Well this law was passed... Our privacy is slowly being pulled away from us. But I'm certainly not going to let it stop me. We'll just have to take more secure measures. If You Use Tor Browser, The FBI Just Labeled You a Criminal.

Not every tweak or theme is automatically available once you jailbreak your iOS device and install the Cydia application. For certain tweaks, you'll need to manually add its source, which is simply a web address linked to repository where the tweaks are hosted.
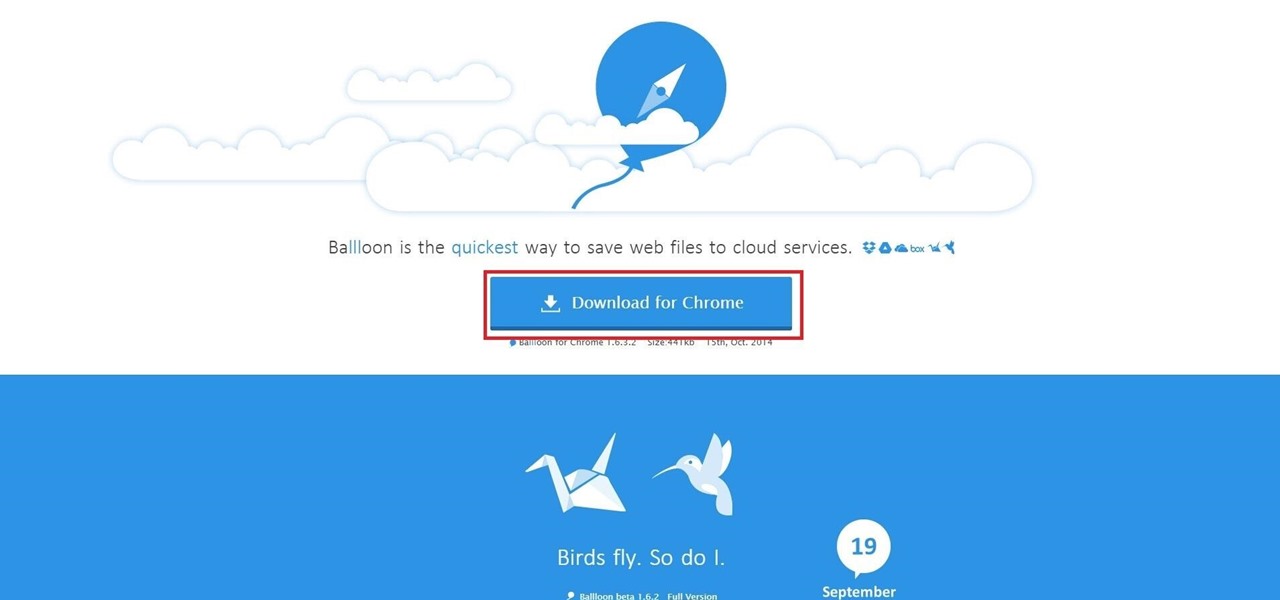
Step 1: First in first, you have to install a Chrome browser, and download Ballloon from official site You can also download it at Chrome Web Store

There are many advantages to knowing how to speak in foreign languages, whether it's for traveling, business, or simply for the pleasure of getting to know a culture that is completely different from your own.
Welcome back my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on us all, all the time.

Often someone who is bone-tired will lay down in bed and flip on the TV or his laptop thinking that it would be nice to relax for a few minutes before going to sleep.

It seems like Apple is always releasing something new, so there must be a lot of lonely iDevices out there going unused, right? With Seedio, you can make the most of your Apple products by connecting them to make one synchronized loudspeaker. As long as all the devices have the Seedio app installed, you can connect as many iPads, iPhones, and iPod touches as you want. All you need is a wireless connection. You can play music from anywhere: your library, YouTube, or the Web. It also works as a...

To Mario enthusiasts everywhere: Mario mania has been lovingly expressed all over the web for some time now (including How-To). The most recent accomplishment brings together two classic favorites: Mario plus LEGOs.

This technique was popularized on Japanese television and has since been widely imitated and posted everywhere. The original concept was shown on a primetime Japanese variety show. Many others produced (plagiarized) their own tutorials for the web. Even Martha made one.

In case anybody's been under a Beyoncé-proof rock for the last month, the (internet) world is forever changed by the Single Ladies... and in many ways, me.

Last week Amazon set their sights on the mobile app market, launching their Appstore for Android. This week they're attacking Android devices once again, but that's not all—they're getting into the online storage biz.

After years of false rumors and abandoned hopes, the day has finally come. Verizon Wireless is finally getting the Apple iPhone!
There's a whole lot of brouhaha going on right now about the hidden plug-ins being installed unknowingly in the Mozilla Firefox web browser, with companies like Apple, Microsoft and even Google being named top offenders.

Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi.
Microsoft's new mobile operating system is officially out on the market, and programmers are hard at work developing new mobile apps for Windows Phone 7 devices. But there's a lot going on in this new platform, which means there's a whole lot to be learned, and the only man in the world with a Windows tattoo is here to help— Charles Petzold.
Ink & Paint was originally intended to provide a place for the sharing of graffiti and street art related news and the spreading of the street art culture. However in recent months I have noticed a distinct lack of "lowbrow" art in the WHT community. Don't get me wrong though, I'm a HUGE nerd. I love null byte, I love the Minecraft world, and all the tech posts that are becoming increasingly more common. It's awesome. However the nerd in me and the artist in me both want to see more comics, s...

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

As we all know, security is a big thing here in Null Byte. We've talked quite a bit about ways to encrypt traffic and become anonymous on the internet, some of which entail using proxies, VPNs, and SSH tunnels. We've also talked about preference using SSL pages in practice for safe logins. These are all great protocols and tools, but aren't without their flaws and inconveniences.
JavaScript is the language of the internet. It is what allows us to create dynamic, interesting webpages that are fast, web-based applications and so much more. The primary use of JavaScript is to write functions that are embedded in or included from HTML pages and that interact with the Document Object Model (DOM) of the page. This is the magic that allows all of what we see to happen, and for our browser to be manipulated.

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

In this Null Byte, I'm going to teach you about Null Byte Injections. Null Bytes are an older exploit. It works by injecting a "Null Character" into a URL to alter string termination and get information or undesirable output (which is desirable for the malicious user).

Like the recent XSS 0day exploit found in the Mac and Windows versions of Skype, a similar one has been found in the Skype app for iPhone. The vulnerability allows an attacker to send a message that contains malicious JavaScript code in the "Name" parameter. This code can steal your phonebook, crash the app, and potentially do a lot worse. The URI scheme is improperly identified for the web-kit browser. Instead of going to a blank browser page, it defaults to "file://". The code could steal a...

Big news from the world of game development engines. For several years, Unity3D has been the free 3D game development engine of choice for aspiring and indie game designers around the world. While it isn't as powerful as Unreal Engine 3 or CryEngine, it's free and much easier to use. Now, according to an announcement made by Unity yesterday, Unity 3D is about to unleash a huge weapon that neither of those other engines can claim: Flash compatibility.

G+Me is one of our favorite Chrome extensions here at Google+ Insider's Guide. We love it because it's one of the most comprehensive extensions out there. It attempts to address the "noisy streams" issue, with list mode, and collapsible posts and comments. The creator, +Huy Zing, is very responsive to feedback, and he's been quick to address any issues that arise, including privacy concerns. He's even created a G+Me (Paranoid Edition) extension, for the extra careful Google+ user. And if you ...

If you're like me, you don't do a lot of web browsing anymore. I subscribe to my favorite blogs' feeds and read them via Google Reader. It's one of my favorite Google products, for a lot of reasons. I can keep up with most of my web activities in one tab, and follow along with my favorite blogs, Flickr photos, and Twitter. I can share instantly with people who follow me, and see what other people have shared with me. I hope that Google+ will integrate well with Google Reader, because it alrea...

Over the weekend, Google made several updates to the Google+ profile. Here's how to make the most out of old and new features to make your profile page shine.

Mozilla is scheduled to release their updated Firefox browser on Tuesday, bringing the popular web browser up to version 6. Lately, the Mozilla team has been releasing newer versions of Firefox without a slew of new features, focusing on fixing bugs and getting the improved product out as quickly as possible, in order to compete more rapidly with other browsers like Google Chrome.

Google+ Hangouts are proving to be a proficient platform for teaching and communicating in real time with others. If you're someone who creates instructional content online, you may want to consider using the platform for your next project.

+Randall Munroe, the man behind the web's most popular web comic, XKCD, has always had a knack for getting to the heart of the larger social issues on the web. During the 1st 48 hours after Google+ started letting non-Googlers in, one of the most shared posts within its private walls was his latest comic about Google+:

Video games are the most prevalent type of interactive media, but certainly not the only one. The interactive music video for the song "3 Dreams of Black" by supergroup ROME and digital artist Chris Milk utilizes the latest web design technology, video game influenced art and interactivity, and large crowd-sourced elements to form a compelling work of art. ROME is composed of producer extraordinaire Danger Mouse, Italian film composer Daniele Luppi, Norah Jones, and Jack White. Their recent e...

The Free Art and Technology Lab (F.A.T.) has provided three different energetic and passionate methods for voicing support for Ai Weiwei, the famous Chinese artist and activist who has been detained without known reason by the Chinese government since March 31st.

At Google I/O this morning, Google finally announced the launch of its much awaited Google Music service. It's currently in invite-only beta mode, but they claim it will open up to the masses soon enough. To start syncing your music library with Google's Cloud now, you need make sure you're signed into your Google Account, then click here for a personal invite. It's currently free for a limited, undisclosed amount time.

Warning If you don't trust that these steps are safe or that they won't work, than have your computer/laptop backed up so you can restore it if necessary.
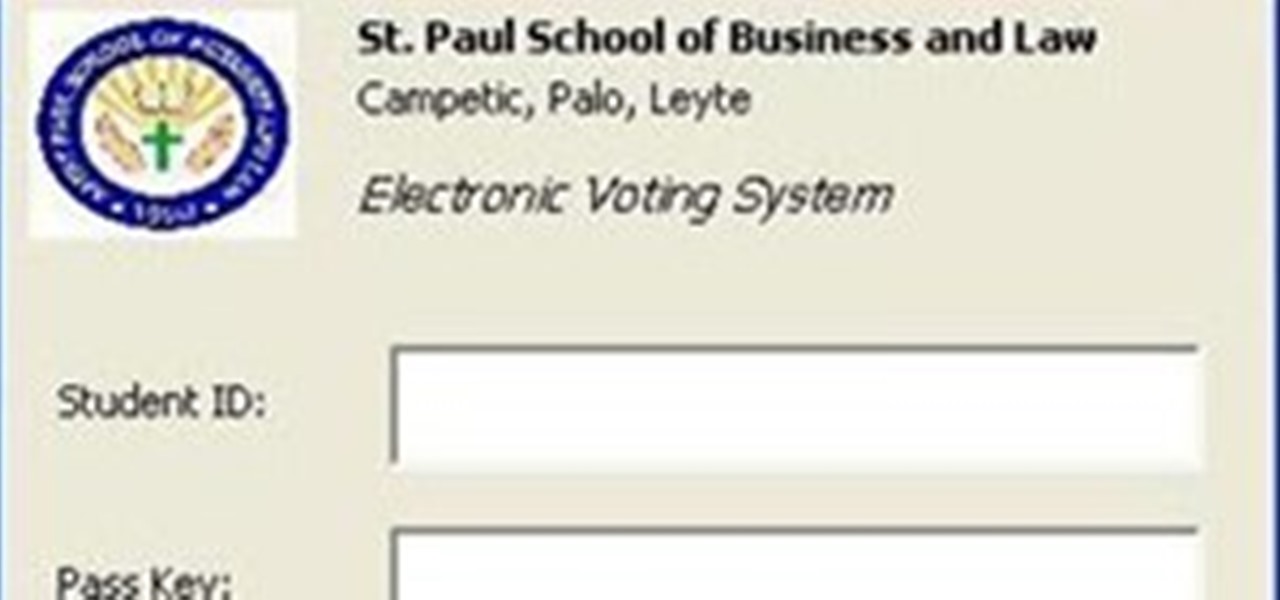
Tomorrow is another day of election (PSG). I have to wake up early to set up the computers on both computer rooms. The election process is computerized, making the counting of votes the responsibility of the computer. What makes this year's election special is that for the first time in 3 years (correct me if I'm wrong), there are competing parties. The result is something to look forward to especially for me who contributed in the creation of the system.

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...