While sliding doors is far from a new concept and will be obsoleted once we see wider support for multiple backgrounds (CSS3), it is still a good one for your bag-of-tricks. The theory is that if we have an extra hook in our markup, we can apply two overlapping background images to a single spot of text. When that text grows or shrinks, these overlapping images and reveal more of themselves creating the illusion it is a single expandable graphic. In this video screencast, we do a quickly exam...
This video covers creating and programming a a PHP-based web forum. Topics include basic layout, login and logout, Admin start, creating categories and subcategories, creating topics, and more...

There are some very powerful tools in CINEMA 4D that you can use very quickly to create some 3D graphic elements. Once you start practicing you'll find it may be easier to create your own reference than to find the "just right" one on the web. So, if you're in need of some barbed wire, for reference or otherwise, check this tutorial out. Of course, it takes quite a bit longer to actually SHOW you how to create the barbed wire (creating the barb, wrapping it around the wire, using MOGRAPH in o...
Hack the hex code in Bejeweled Blitz for a higher score! Everyone wants the top score in this popular web game, but it all comes down to how you get it. Do you have what it takes to come out on top? Check out this video tutorial to learn how to hack Bejeweled Blitz (07/24/10).
An easy way to view your CSS code of your website is through the Firefox plugin called Firebug. It's really helpful, especially if debugging your code. Just remember, you cannot save anything with Firebug, it's only for viewing code and adding codes for previewing webpages.
There's a new way to shop, and it's called your phone! On an Android mobile device, there'a handy shopping application called Shop Savvy, found in the Google Marketplace. Okay, so you can't actually buy things with it, but you can scan barcodes of products to get more information about them, making shopping in the mall so much easier. But how do use it to buy everything you want? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use the Shop Savvy app on your Android...

1. Open Web Browser and go to WWW.Google.com and type crucial memory mechanic and press enter. 2. Click the first result found on the search page( i.e., lolo memory mechanic)

Have an opinion and want the whole world to know it? You're not alone! There are many online outlets for you to type up your review, whether it be for a restaurant, play, movie, book or anything else you have recently experienced. Check out this video for tips on how and where to post your exciting review.

1. To start a blog pick a topic on which you want to create your blog. 2. Select a blog software or platform where you can work like word press.

This video is about downloading videos in Firefox. Firefox is a web browser, but it will be used rather than Internet Explorer because Firefox allows you to install plug ins. Go to the tools menu and click "add-ons". Download helper is the add on we will select. Click "get extension". A web page opens. In the search box, choose "search for add-ons". Add to Foxfire. Install now. Restart to complete installation. On the toolbar you will see three rotating bars which will let you know the add on...

Not all websites are created equal, and that's why Safari doesn't apply Dark Mode to each webpage you visit during your iPhone's system-wide dark appearance. But in Safari's latest update, Apple gives its web browser more power to automatically apply Dark Mode to specific website content without having to use extensions like Noir.

Currently, the COVID-19 pandemic is showing signs of winding down, nevertheless, Google will still hold its annual I/O developer conference as a virtual affair, with keynotes and sessions available as live streams and on-demand videos starting Tuesday, May 18 and concluding on Thursday, May 20.

Angry Birds, one of the first franchises to find success in mobile gaming, continues to shoot its shot at new life in augmented reality gaming.

Have you ever wondered where you'd come out if you drilled to the other side of the world? Now, if you have an Android device and Chrome web browser, you can find out.

There are many considerations to make when choosing a web hosting plan. Storage space, performance, security, and reliability all matter. The cheapest option isn't always the best idea.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Since its launch in 2009, Google Apps Script has given creative thinkers the ability to perform light-weight application development within GSuite. Based on JavaScript, you can build your own simple tools that will increase your efficiency and productivity.

The "Zoombombing" trend is still strong on the Zoom video meetings service, despite security measures Zoom put in place to stop it. That's why it's up to you, as either a host or co-host, to be proactive about preventing Zoombomber harassment, as well as stopping it whenever it slips through the cracks.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

While Modiface, YouCam, and others have been playing in the virtual make-up marketing pool for a while, here comes Google ready to splash down with a cannonball.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

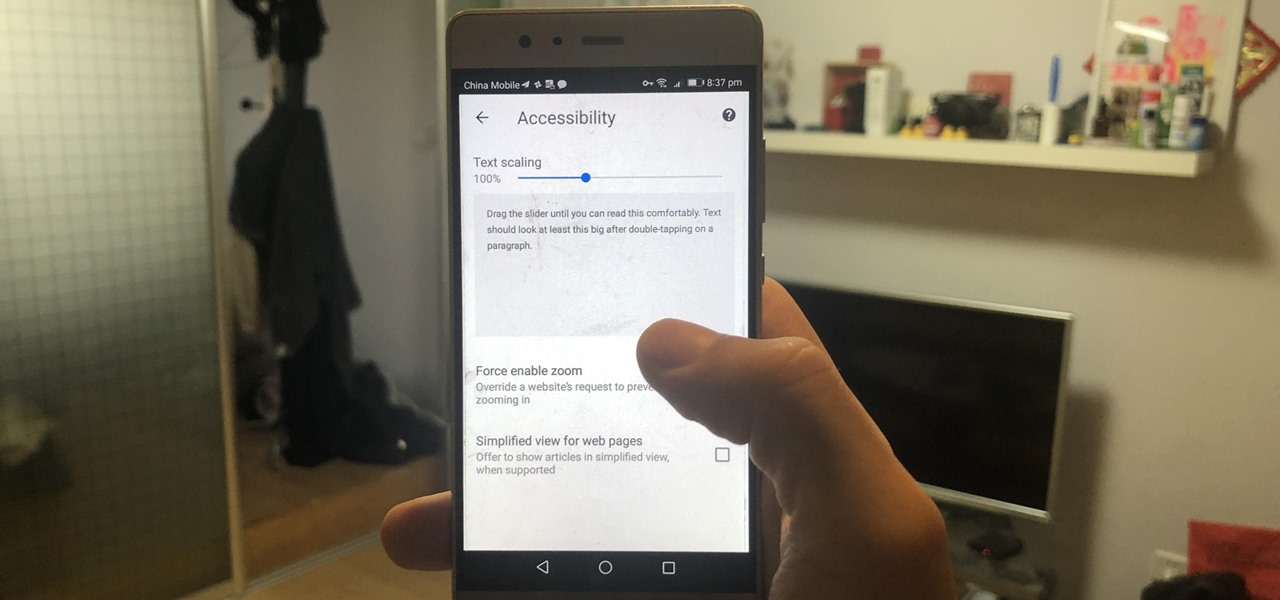
There are many reasons you might want to increase your text size in Google Chrome. The browser's accessibility options have a few tools to help the readability of text on websites. Changing the text scale, enabling zooming, and toggling the simplified view can customize Google Chrome to be perfect for you.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

It's no secret that Android has a messaging problem. iPhone users can turn to iMessage as a one-stop shop for all their messaging needs — features like read receipts and the ability to text from a computer have been standard with Apple products for quite some time. Android has no such solution, but Google's looking to fix that with a huge update to the Android Messages app.

Bookmarks and favorites are handy options for saving interesting websites you come across while surfing the web on Android but are far from ideal when it comes to instant access. Thankfully, Google Chrome gives you the added ability to save webpages and progressive web apps directly to your home screen for added convenience.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Instagram Direct is fast becoming the end-all-be-all messaging app, and it just added some incredibly convenient features that should make it a bit more practical. These new additions have a clear purpose: To help Instagram Direct grow its base and take on more feature-rich messengers like Snapchat or WhatsApp.

Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

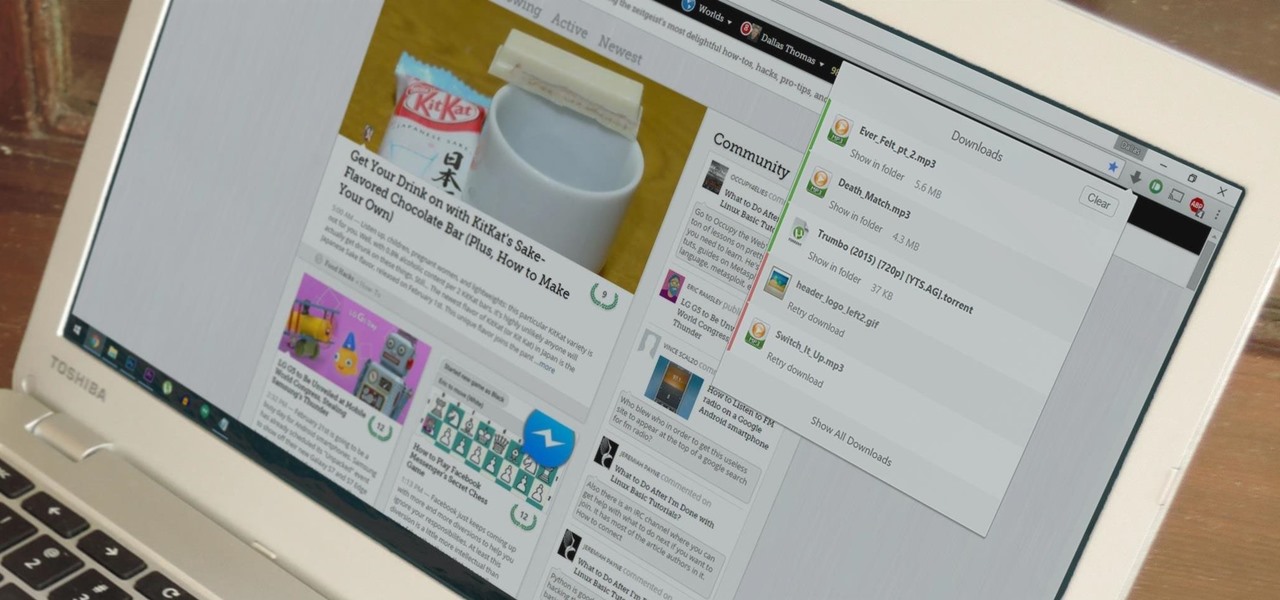
Chrome's download bar has looked pretty much exactly the same for years now—a simple horizontal menu that spans the entire bottom of the browser and displays buttons for each of your recent downloads. It's not exactly pretty, and when it comes to functionality, the space it occupies could certainly be put to better use.

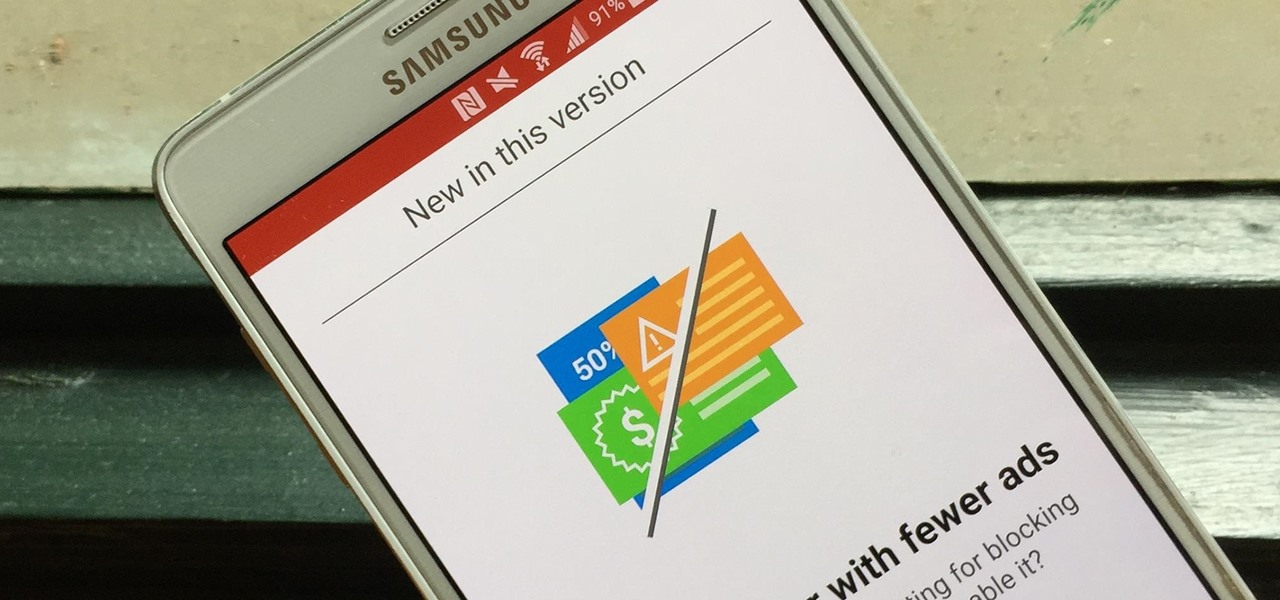
Although they're often times the primary source of income for websites, on-site advertisements can annoy even the most tolerable reader. That's why ad blockers have been some of the most popular downloads on Firefox and Chrome for some time now, demonstrating that when it comes down to it, most people just want nothing to do with ads shoved in their face.